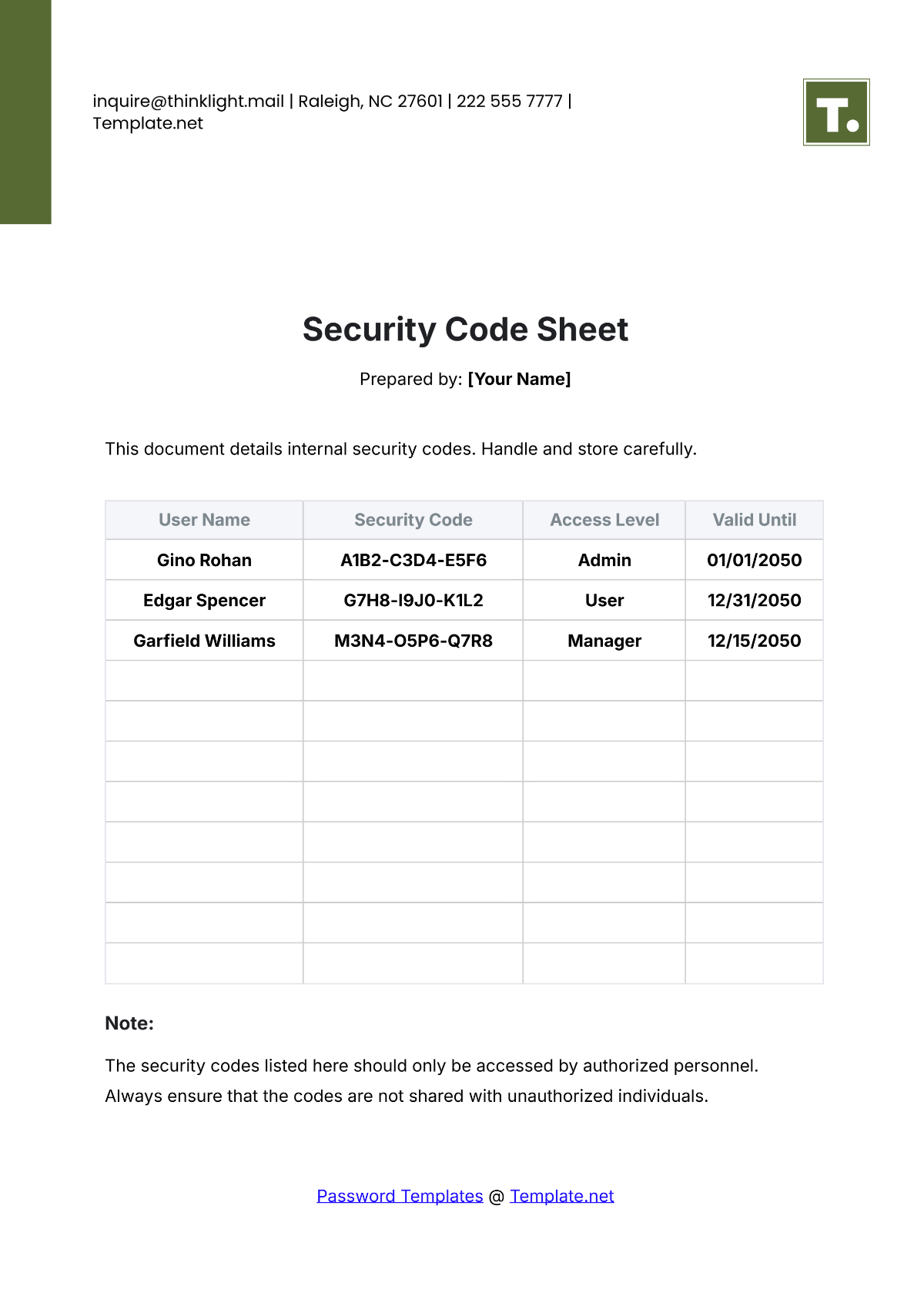
Security Code Hd
Indulge in the stunning luxury of our Security Code Hd collection with hundreds of exquisite images. highlighting the opulence of photography, images, and pictures. ideal for luxury lifestyle publications. Each Security Code Hd image is carefully selected for superior visual impact and professional quality. Suitable for various applications including web design, social media, personal projects, and digital content creation All Security Code Hd images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Explore the versatility of our Security Code Hd collection for various creative and professional projects. Time-saving browsing features help users locate ideal Security Code Hd images quickly. The Security Code Hd archive serves professionals, educators, and creatives across diverse industries. Diverse style options within the Security Code Hd collection suit various aesthetic preferences. Reliable customer support ensures smooth experience throughout the Security Code Hd selection process. Each image in our Security Code Hd gallery undergoes rigorous quality assessment before inclusion. The Security Code Hd collection represents years of careful curation and professional standards. Comprehensive tagging systems facilitate quick discovery of relevant Security Code Hd content. Cost-effective licensing makes professional Security Code Hd photography accessible to all budgets.


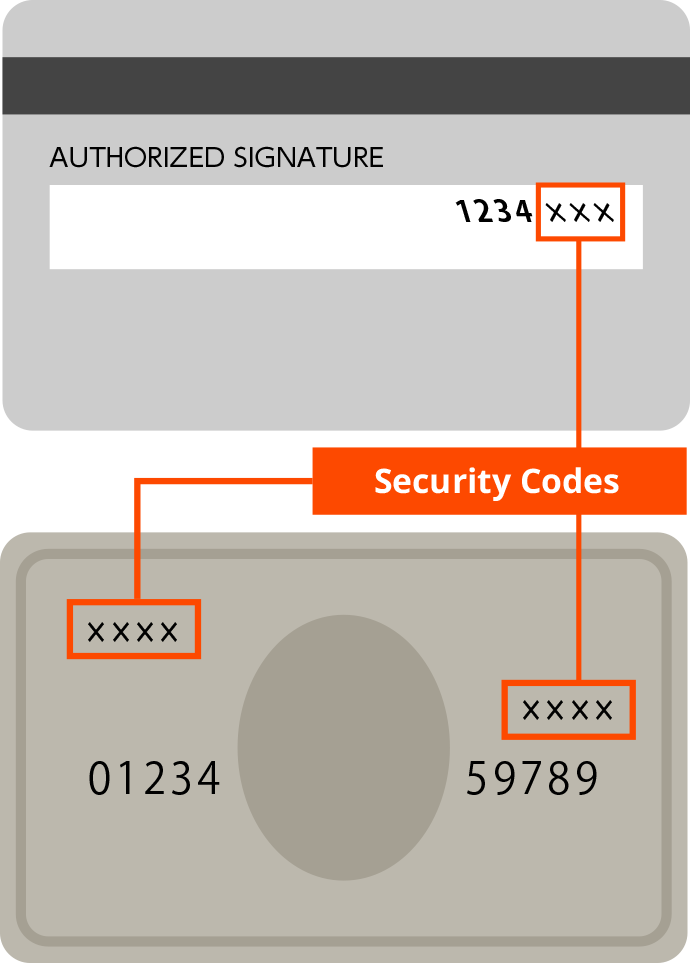






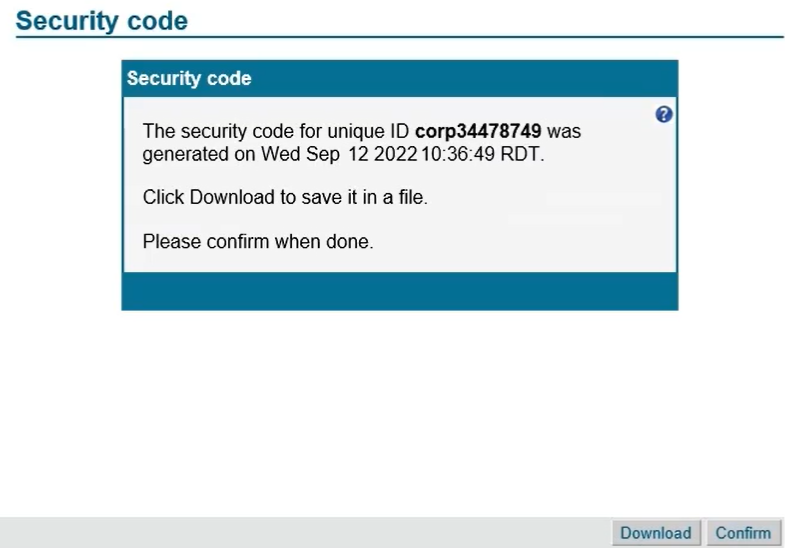






















![[100+] Cyber Security Wallpapers | Wallpapers.com](https://wallpapers.com/images/hd/cyber-security-codes-and-padlocks-louj44tbnhinx0e4.jpg)
![[100+] Security Wallpapers | Wallpapers.com](https://wallpapers.com/images/hd/cyber-security-interface-skjqyncmzs3h1jcr.jpg)



![[200+] Security Pictures | Wallpapers.com](https://wallpapers.com/images/hd/cyber-security-code-wall-h7zf5q8ot3xv0wz8.jpg)






![[100+] Security Wallpapers | Wallpapers.com](https://wallpapers.com/images/hd/cyber-security-protecting-information-4swch6shb5gcb54o.jpg)

![[100+] Security Wallpapers | Wallpapers.com](https://wallpapers.com/images/hd/cyber-security-shield-and-keyhole-zjn550kb1l2fpb66.jpg)
![[100+] Cyber Security Wallpapers | Wallpapers.com](https://wallpapers.com/images/hd/globe-and-padlock-cyber-security-g253vc7ko1gaakyh.jpg)










)


![[100+] Security Wallpapers | Wallpapers.com](https://wallpapers.com/images/hd/laptop-cyber-security-zxsxx9xj3x7ond3i.jpg)


![Secure Code Review: Finding XML vulnerabilities in Code [1/2] - mqst](https://www.muqsitbaig.com/wp-content/uploads/2024/01/Top_10_Secure_C_Coding_Practices_800x533_jpeg.jpeg)
![[100+] Security Wallpapers | Wallpapers.com](https://wallpapers.com/images/hd/honeycomb-cyber-security-de1nra84qghymwjm.jpg)

![[100+] Cybersecurity Backgrounds | Wallpapers.com](https://wallpapers.com/images/hd/cybersecurity-background-oab75v94oynalo3j.jpg)
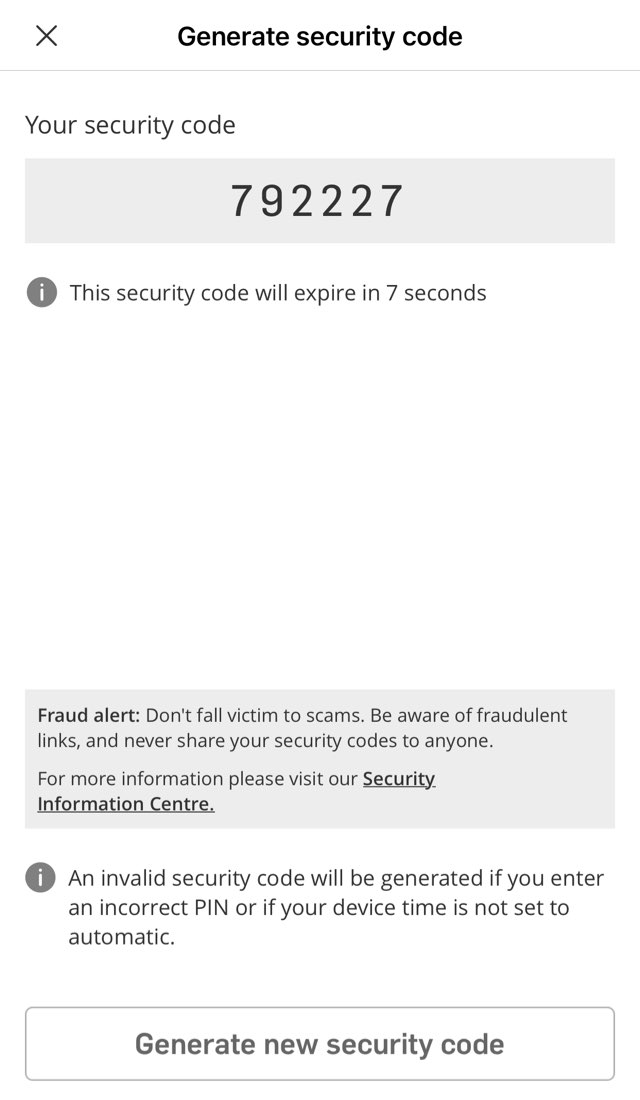
![How can I set up the [Security Code] for my computer? – Splashtop ...](https://mavink.com/images/loadingwhitetransparent.gif)

