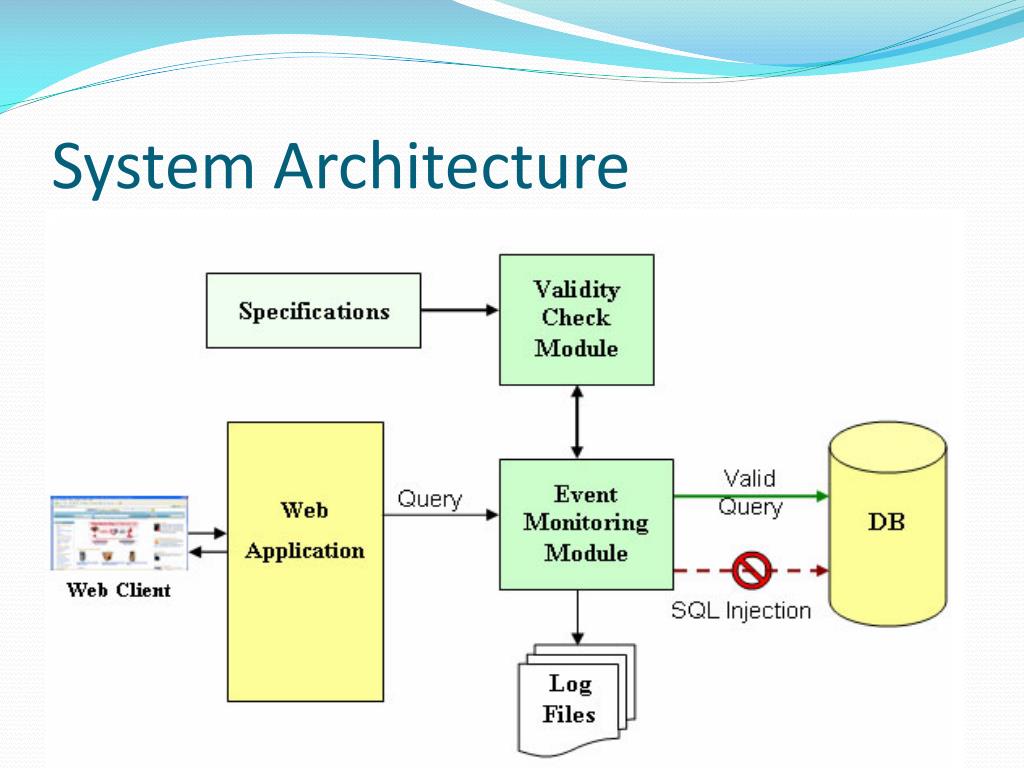
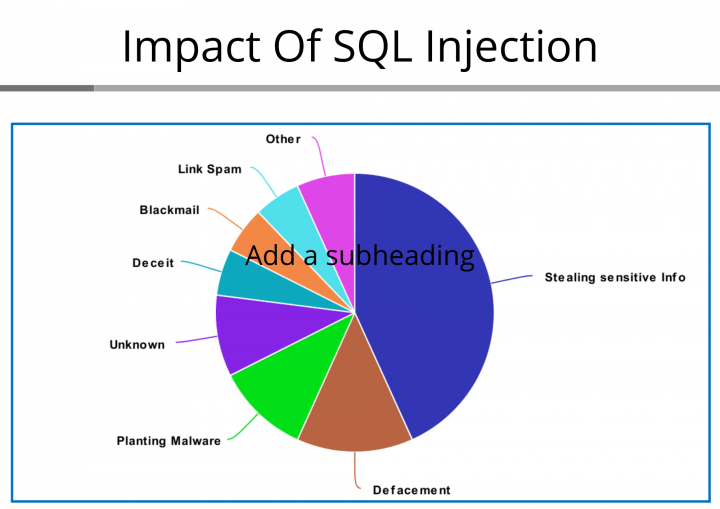
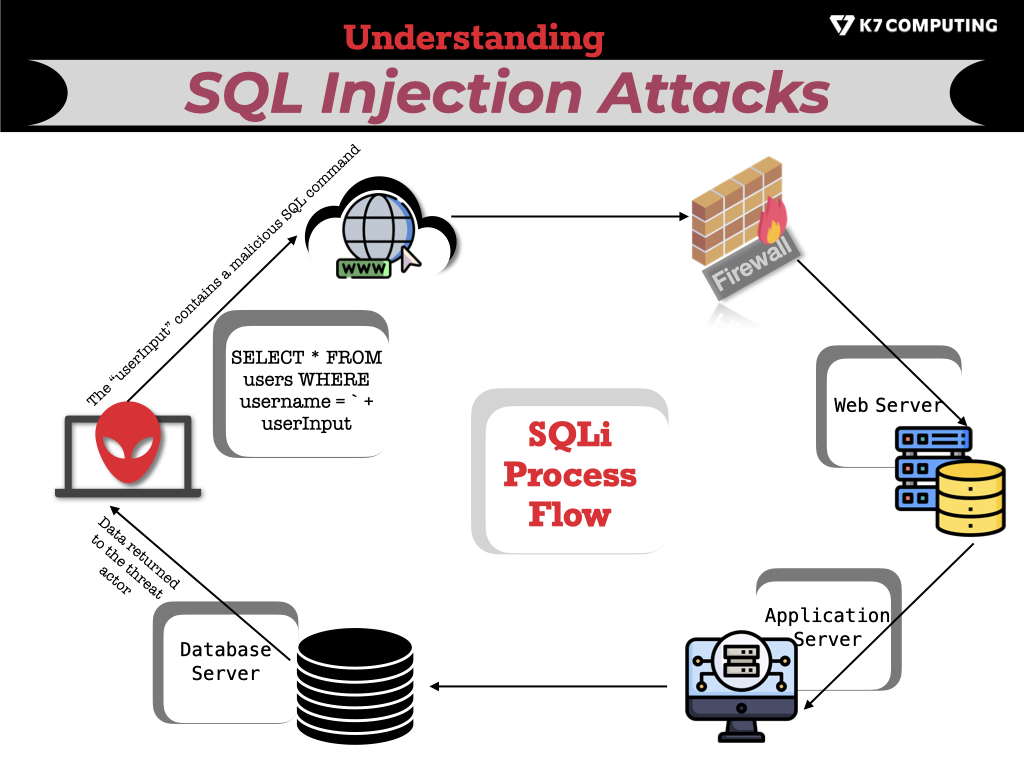
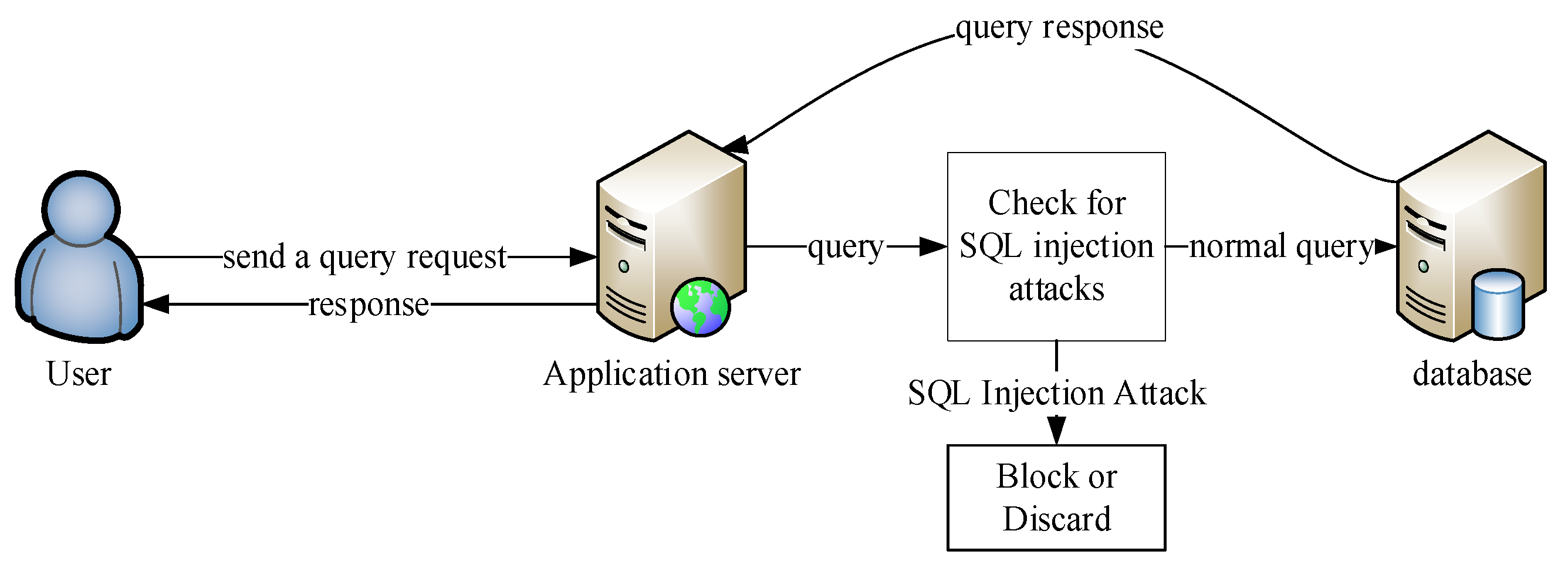
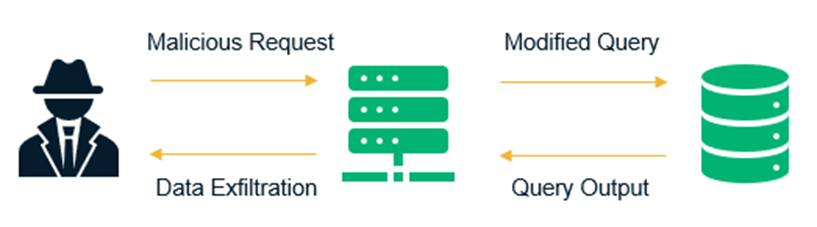
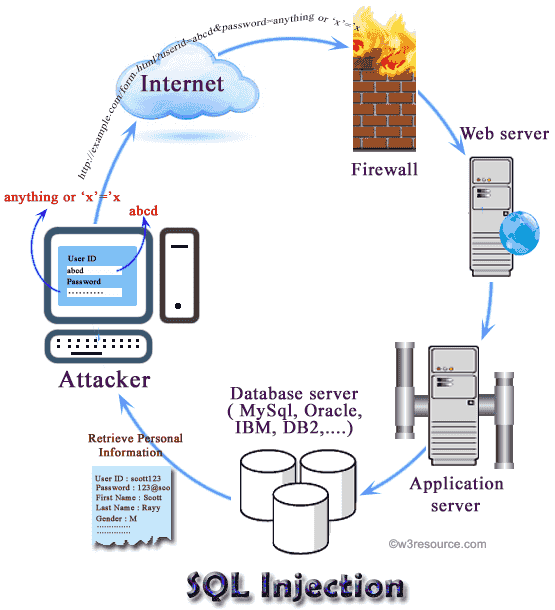
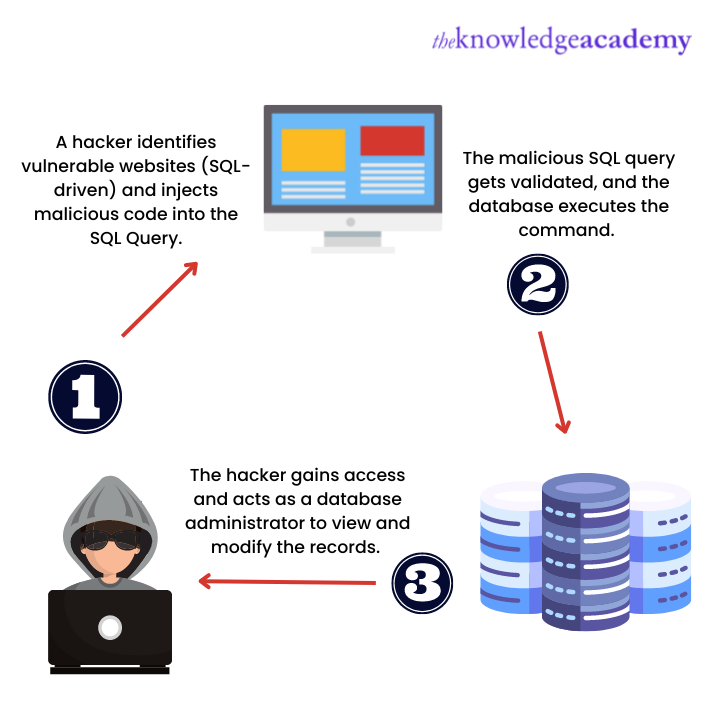
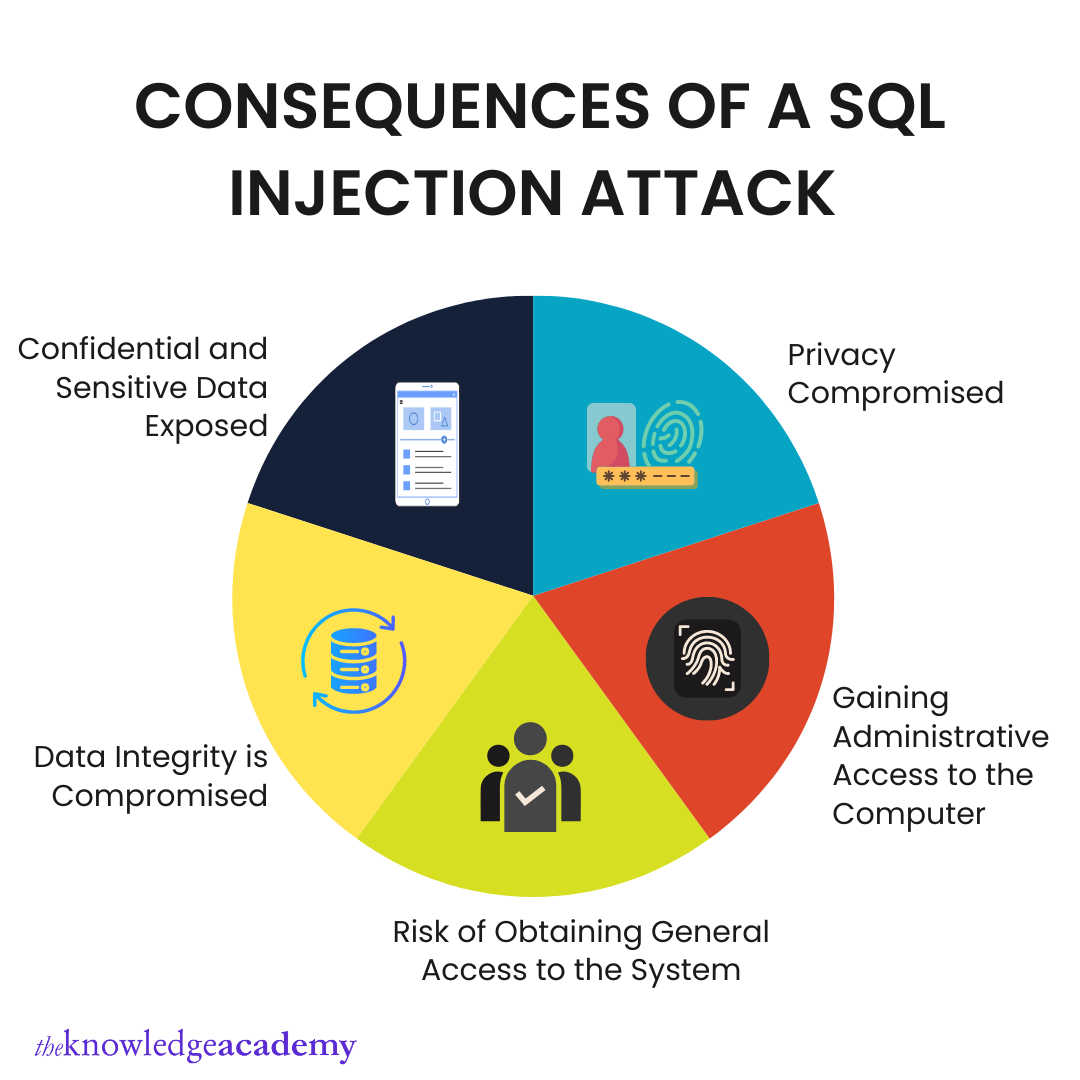
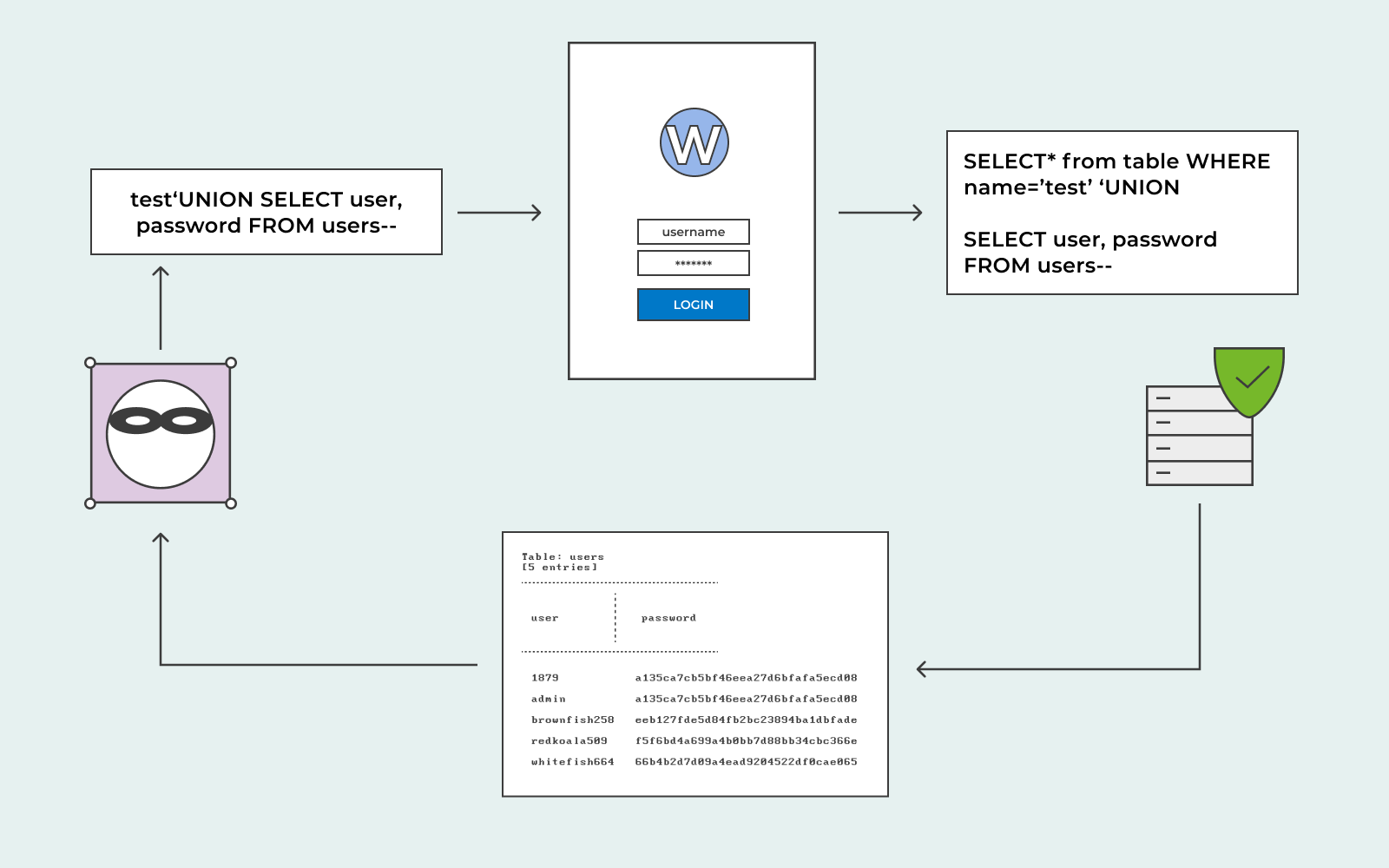
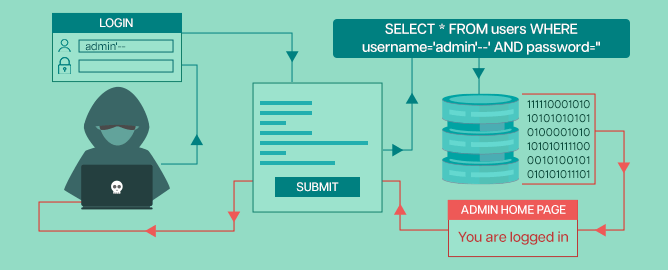
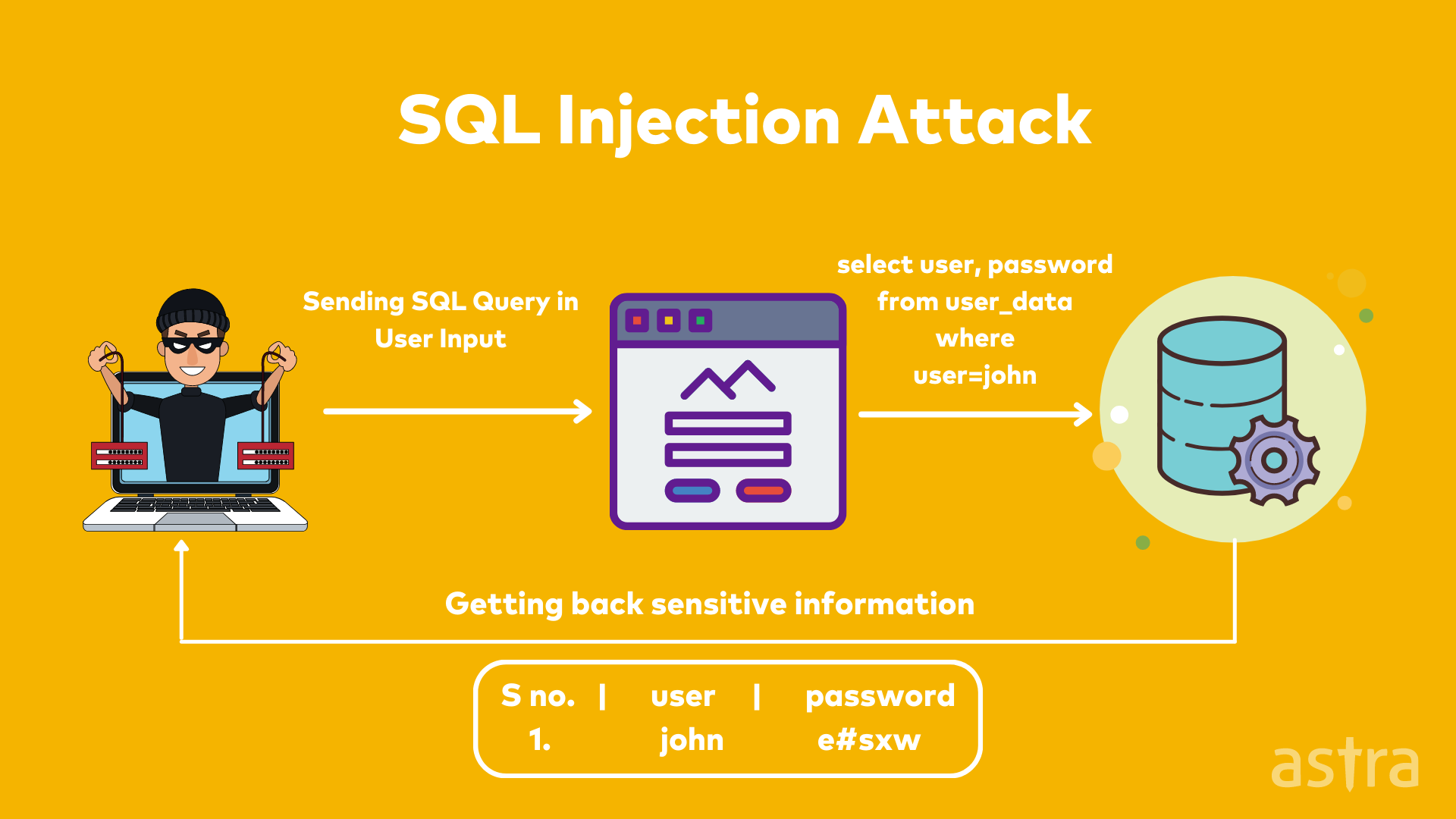
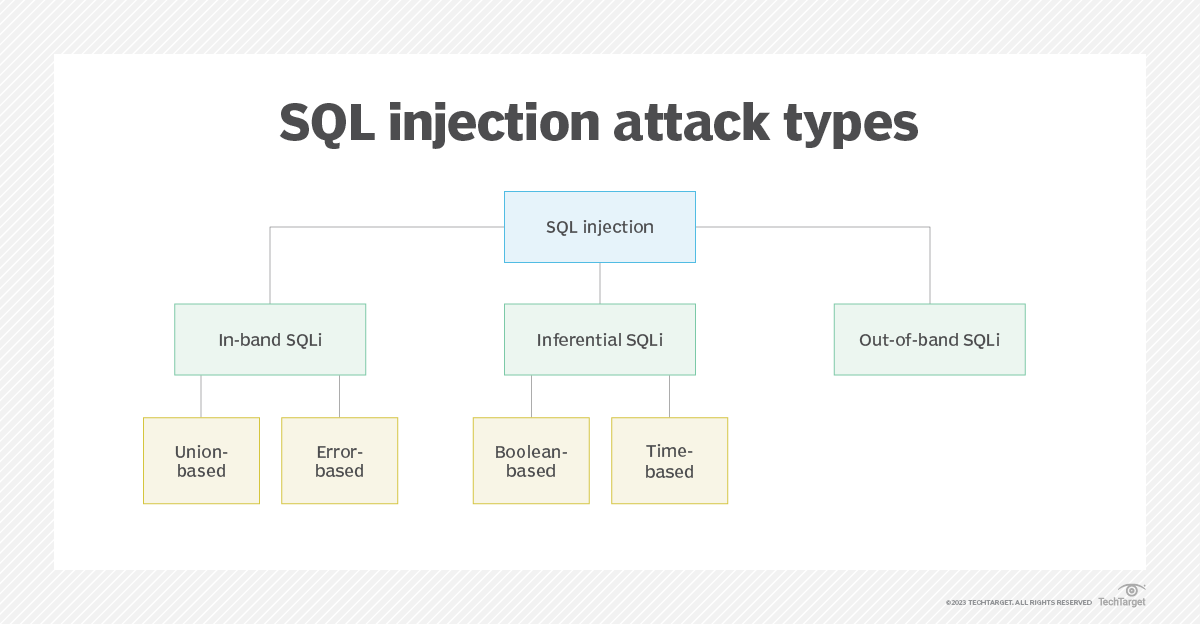
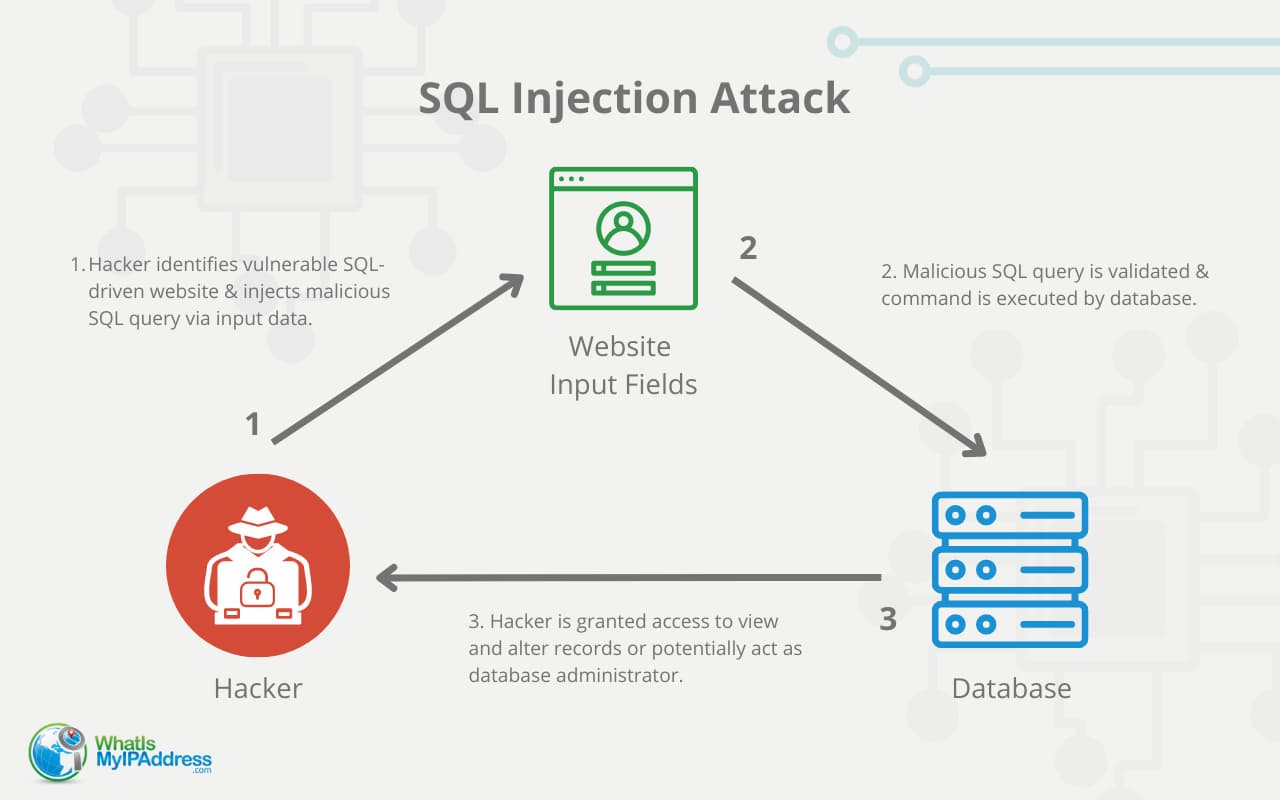
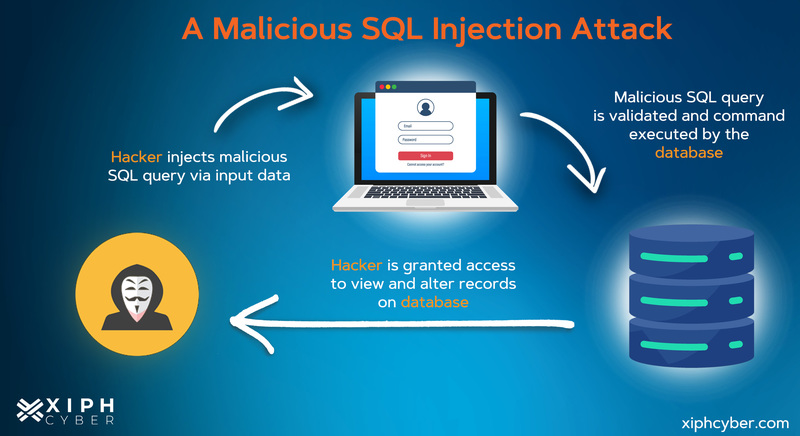
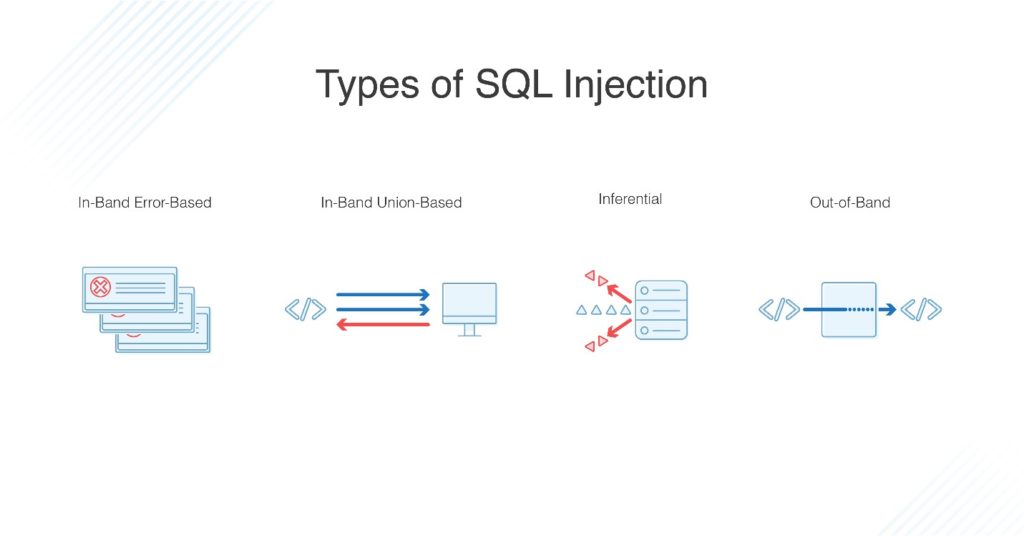
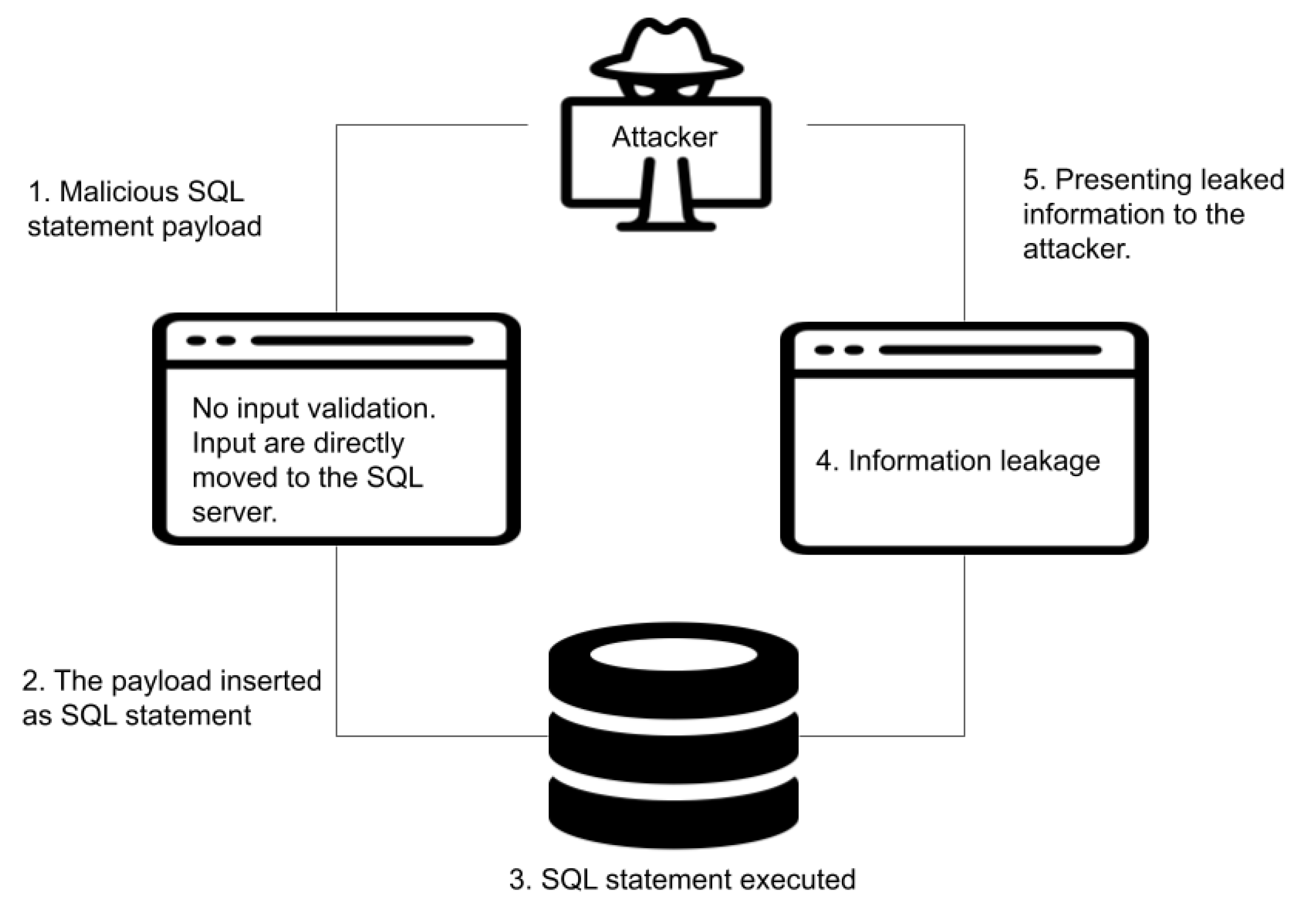
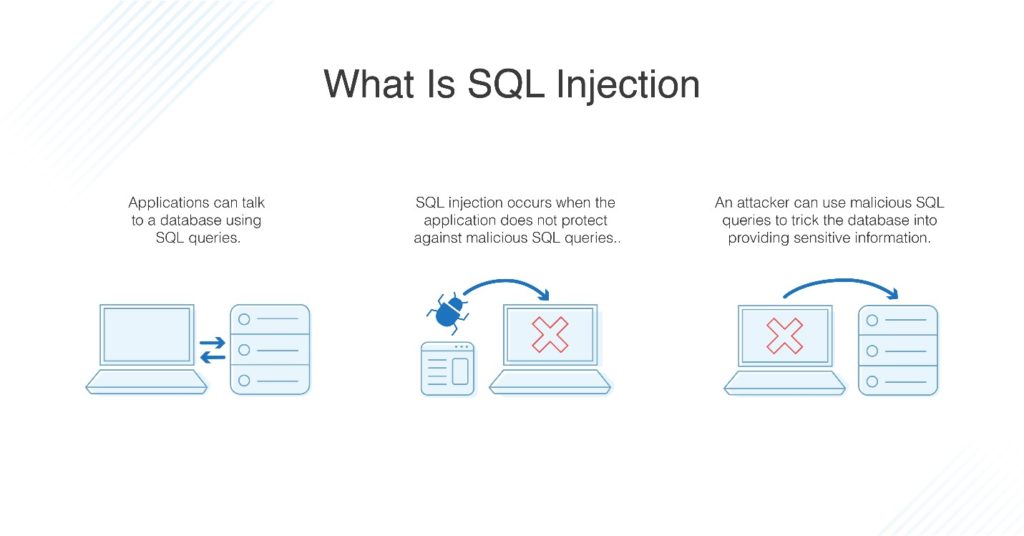
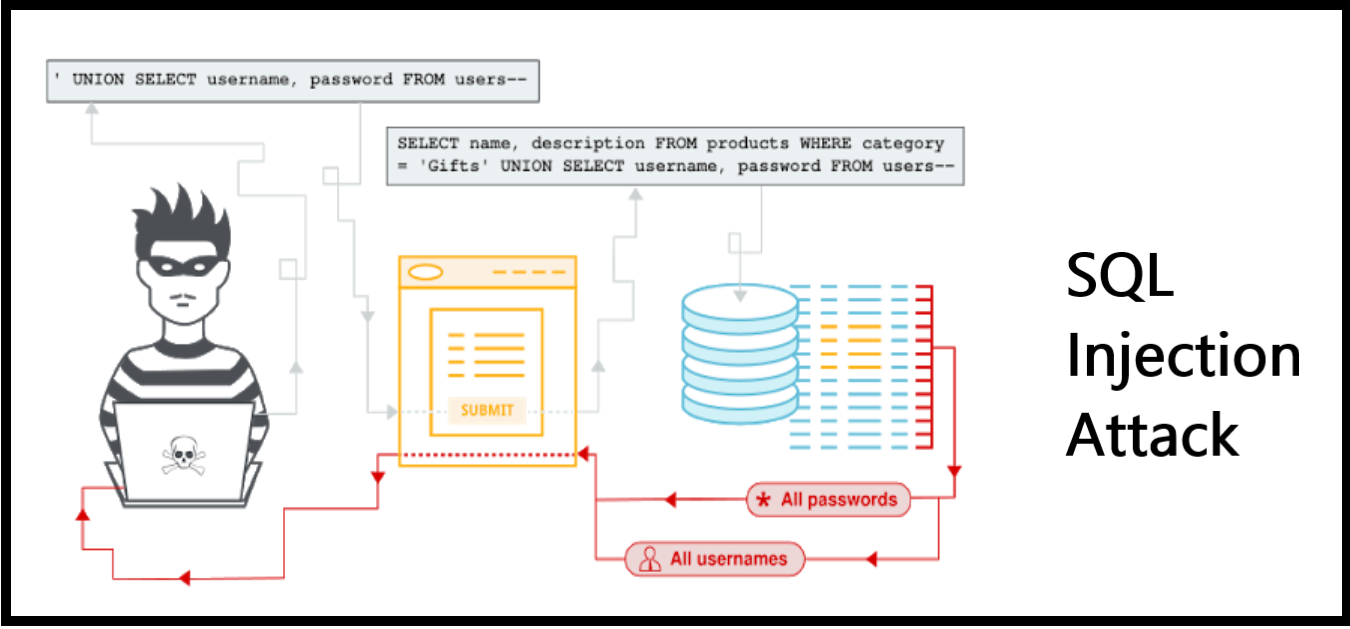
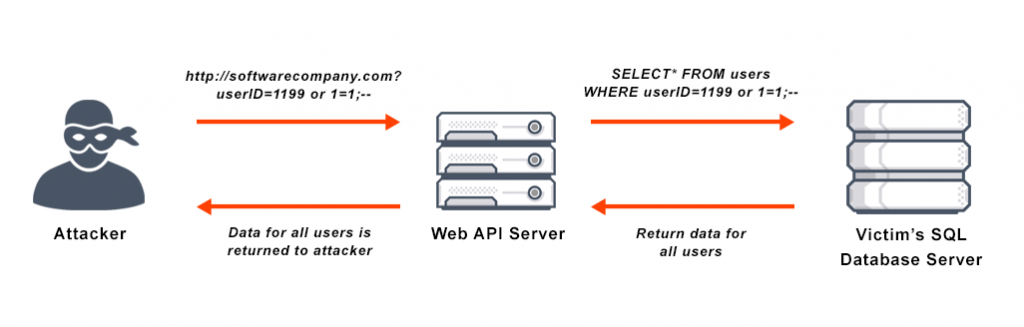
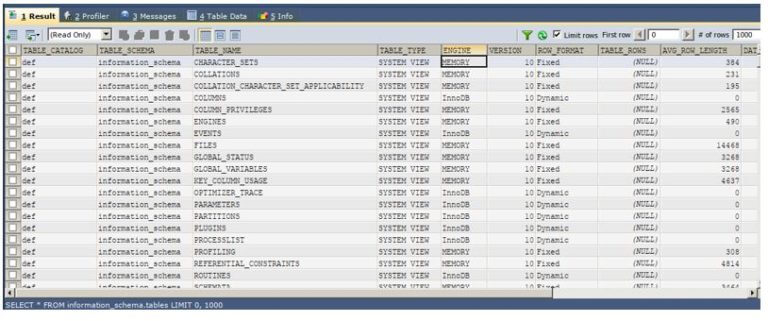
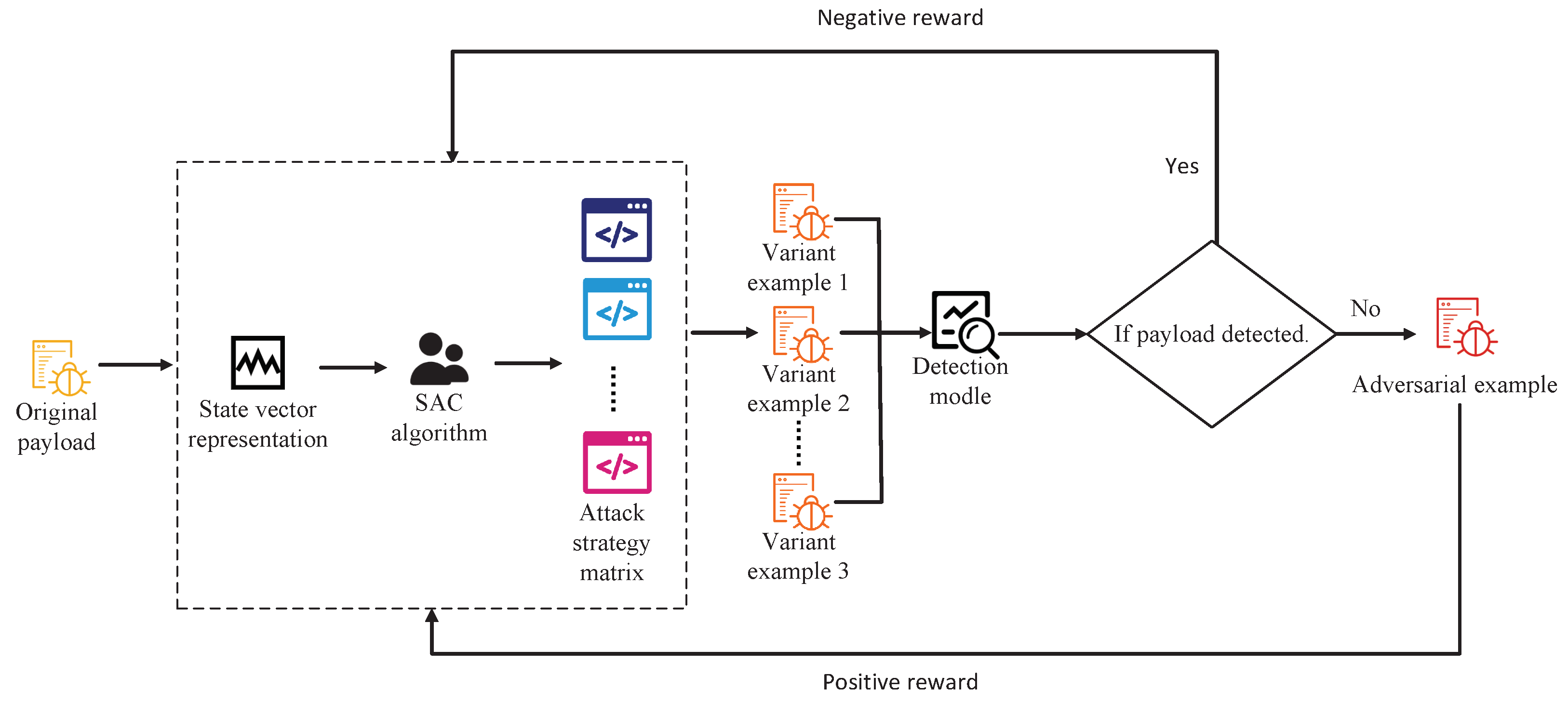
Sql Injection Attack System Diagram
Access our comprehensive Sql Injection Attack System Diagram database featuring comprehensive galleries of professionally captured photographs. optimized for both digital and print applications across multiple platforms. supporting commercial, educational, and research applications. Browse our premium Sql Injection Attack System Diagram gallery featuring professionally curated photographs. Perfect for marketing materials, corporate presentations, advertising campaigns, and professional publications All Sql Injection Attack System Diagram images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Each Sql Injection Attack System Diagram image meets rigorous quality standards for commercial applications. The Sql Injection Attack System Diagram collection represents years of careful curation and professional standards. Diverse style options within the Sql Injection Attack System Diagram collection suit various aesthetic preferences. Professional licensing options accommodate both commercial and educational usage requirements. Instant download capabilities enable immediate access to chosen Sql Injection Attack System Diagram images. Time-saving browsing features help users locate ideal Sql Injection Attack System Diagram images quickly. The Sql Injection Attack System Diagram archive serves professionals, educators, and creatives across diverse industries. Our Sql Injection Attack System Diagram database continuously expands with fresh, relevant content from skilled photographers.






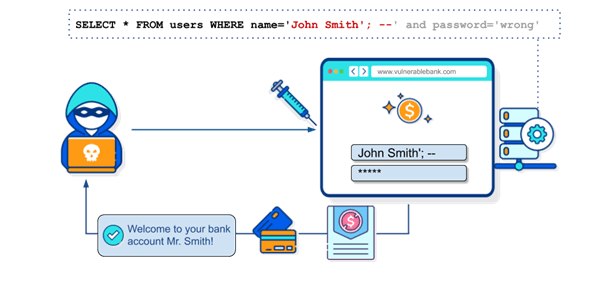
![SQL Injection Attack [9] | Download Scientific Diagram](https://www.researchgate.net/profile/Sneh-Bavarva/publication/375113483/figure/fig1/AS:11431281202238250@1698771915286/SQL-Injection-Attack-9.jpg)







![SQL Injection Attack [9] | Download Scientific Diagram](https://www.researchgate.net/profile/Sneh-Bavarva/publication/375113483/figure/fig1/AS:11431281202238250@1698771915286/SQL-Injection-Attack-9_Q640.jpg)













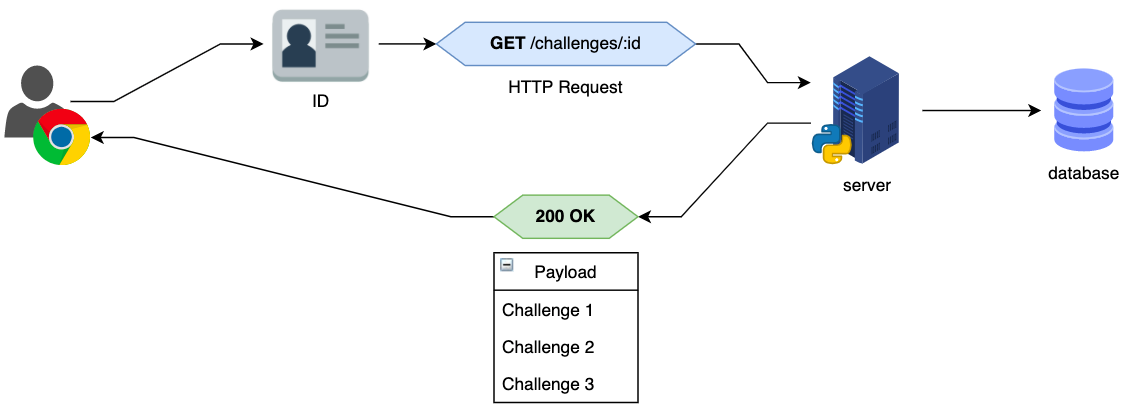

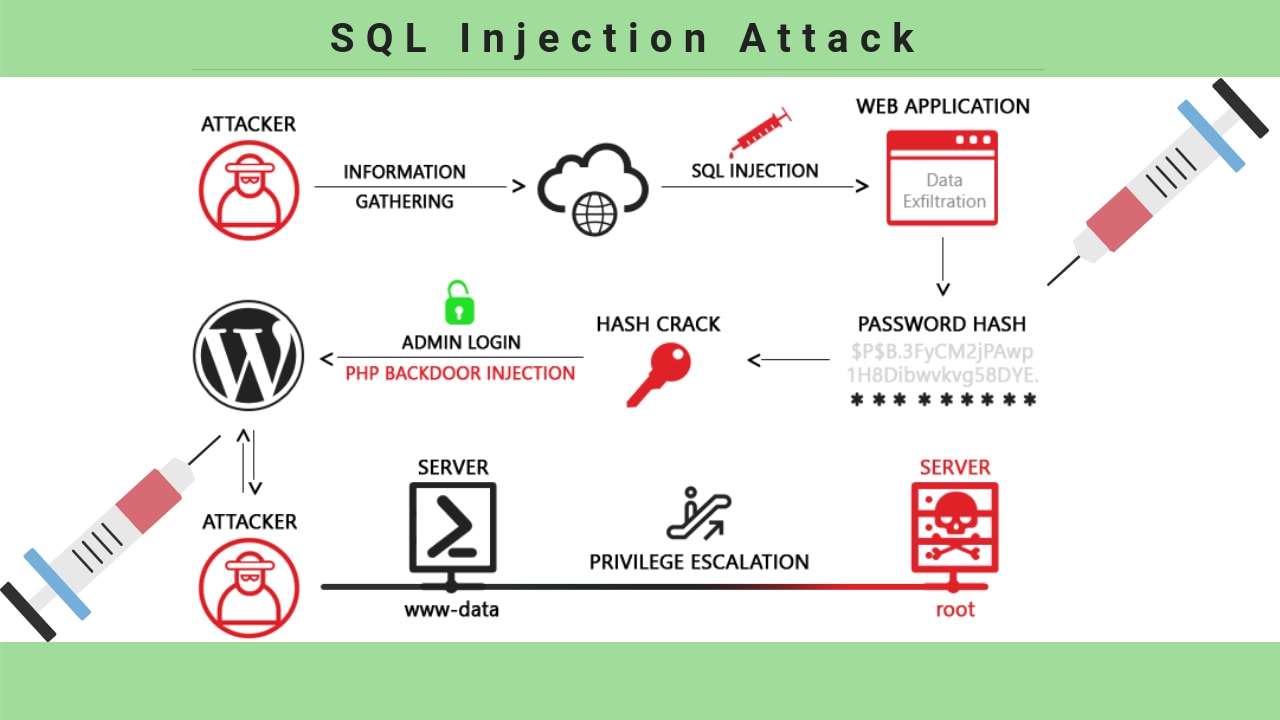
![SQL injection attack process adopted from [3]. | Download Scientific ...](https://www.researchgate.net/publication/372707406/figure/fig1/AS:11431281177634365@1690556711361/SQL-injection-attack-process-adopted-from-3.jpg)









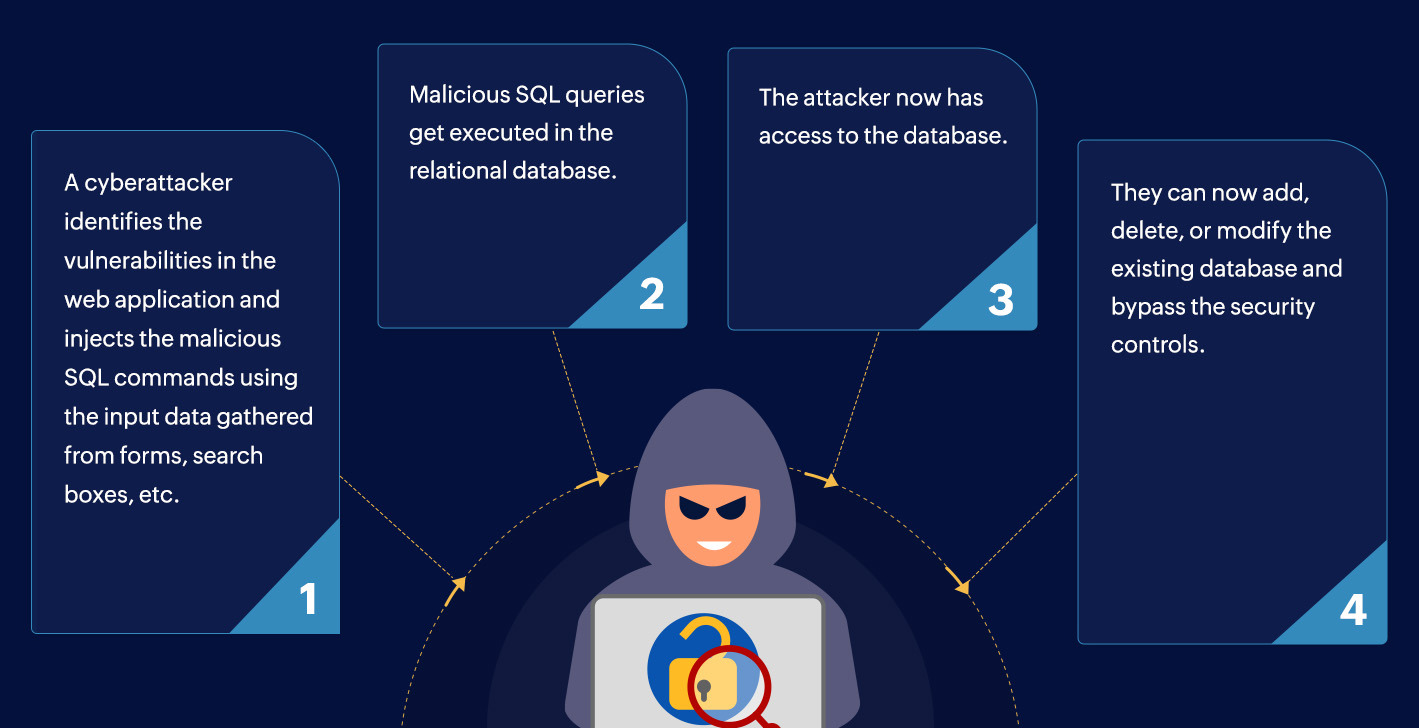





![SQL injection attack process, adopted from [2]. | Download Scientific ...](https://www.researchgate.net/publication/372290757/figure/fig1/AS:11431281174176797@1689163637287/SQL-injection-attack-process-adopted-from-2_Q320.jpg)