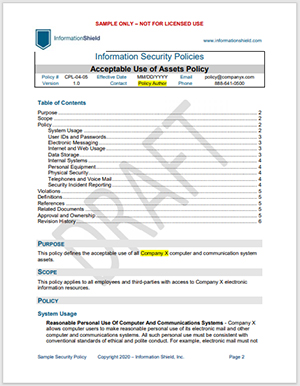
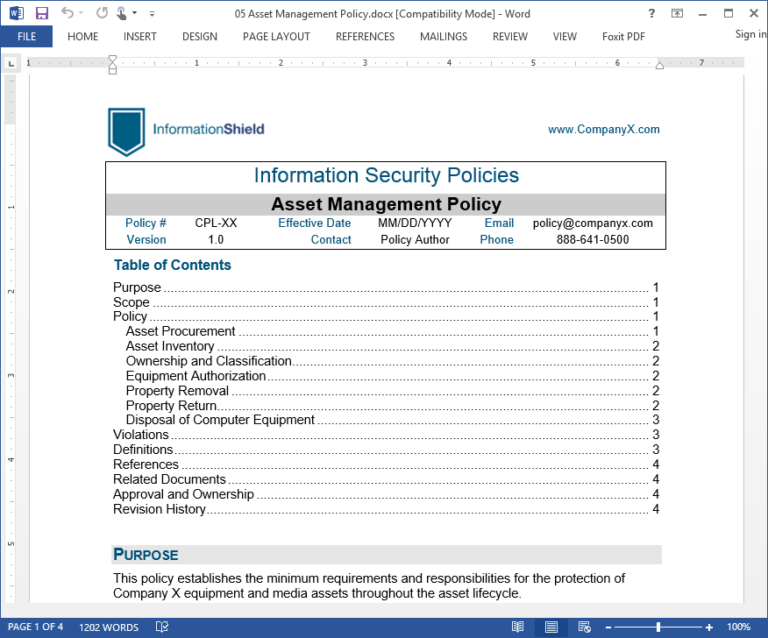
Outdated Policy Documents Insecurity Example
Experience the creative potential of Outdated Policy Documents Insecurity Example with our collection of vast arrays of artistic photographs. combining innovative composition with emotional depth and visual storytelling. transforming ordinary subjects into extraordinary visual experiences. Browse our premium Outdated Policy Documents Insecurity Example gallery featuring professionally curated photographs. Ideal for artistic projects, creative designs, digital art, and innovative visual expressions All Outdated Policy Documents Insecurity Example images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Artists and designers find inspiration in our diverse Outdated Policy Documents Insecurity Example gallery, featuring innovative visual approaches. Comprehensive tagging systems facilitate quick discovery of relevant Outdated Policy Documents Insecurity Example content. Time-saving browsing features help users locate ideal Outdated Policy Documents Insecurity Example images quickly. Reliable customer support ensures smooth experience throughout the Outdated Policy Documents Insecurity Example selection process. Professional licensing options accommodate both commercial and educational usage requirements. Instant download capabilities enable immediate access to chosen Outdated Policy Documents Insecurity Example images. The Outdated Policy Documents Insecurity Example collection represents years of careful curation and professional standards. Multiple resolution options ensure optimal performance across different platforms and applications.










![Free Printable Security Policy Templates [PDF, Word] Information ...](https://www.typecalendar.com/wp-content/uploads/2023/05/Empty-information-security-policy-template.jpg?gid=207)
![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-22.jpg)
![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-08.jpg)
![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-06.jpg)
![Free Printable Security Policy Templates [PDF, Word] Information ...](https://www.typecalendar.com/wp-content/uploads/2023/05/information-security-policy-document-template.jpg?gid=207)
![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-12.jpg)









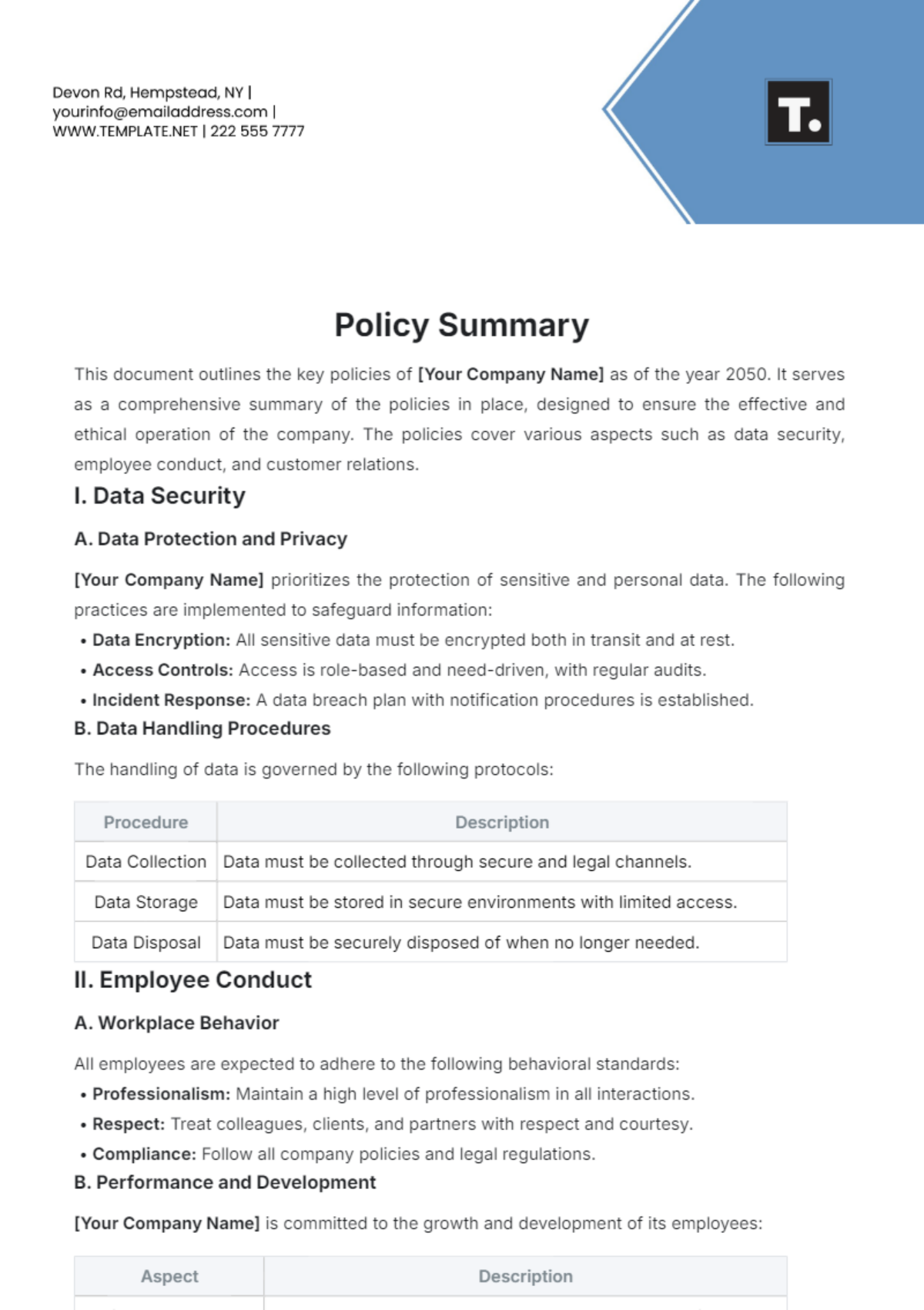








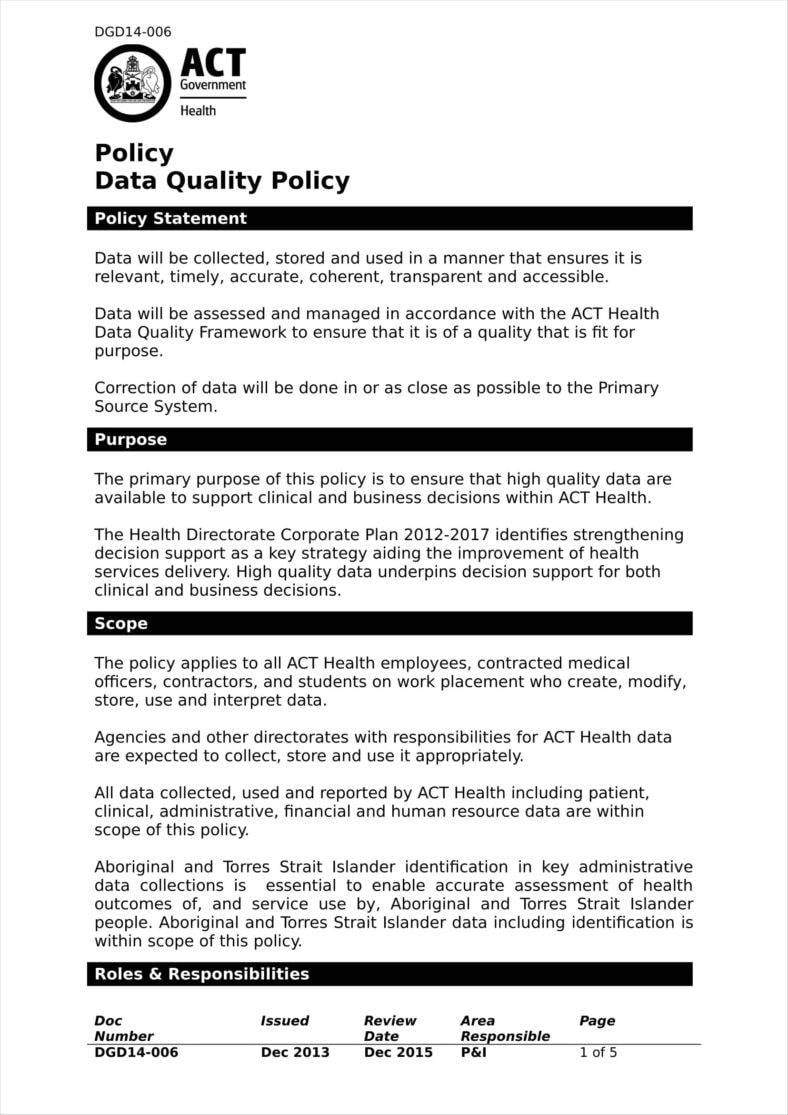
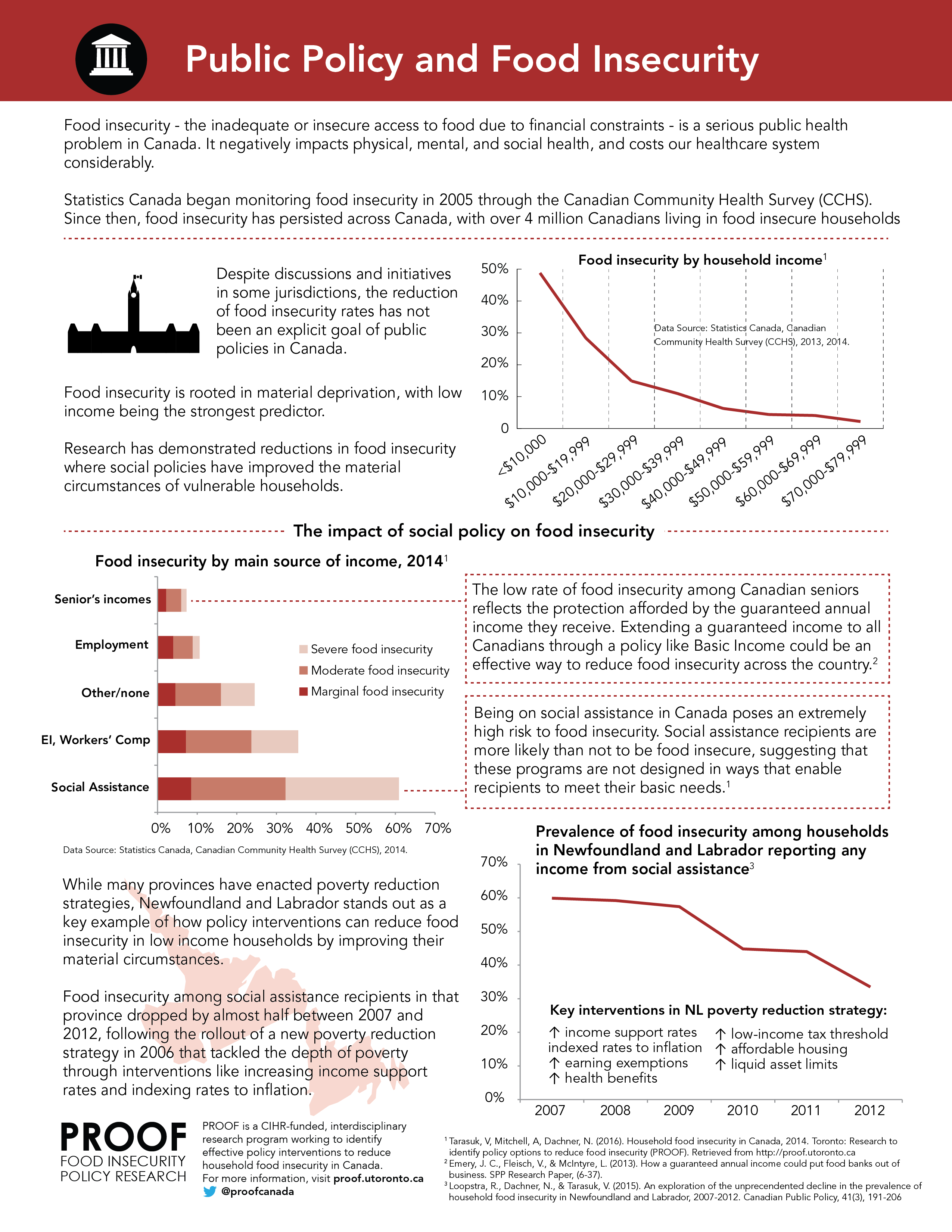








![Free Printable Security Policy Templates [PDF, Word] Information ...](https://www.typecalendar.com/wp-content/uploads/2023/05/Information-security-policy-examples.jpg?gid=207)



![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-03.jpg)




![20+ Free Information Security Policy Templates [Word, PDF] » TemplateData](https://templatedata.net/wp-content/uploads/2021/07/information-security-incident-management-policy-template.jpg)



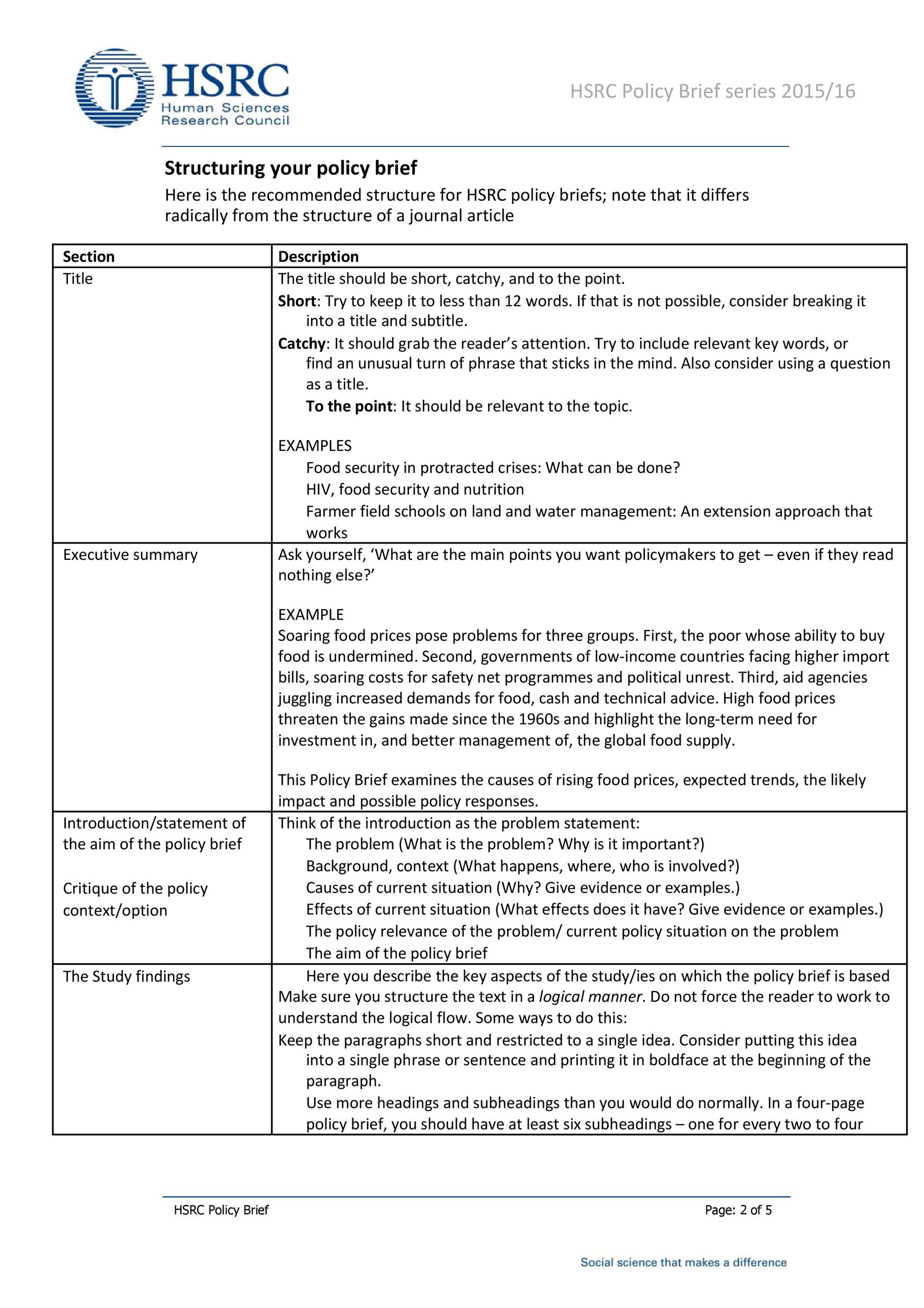









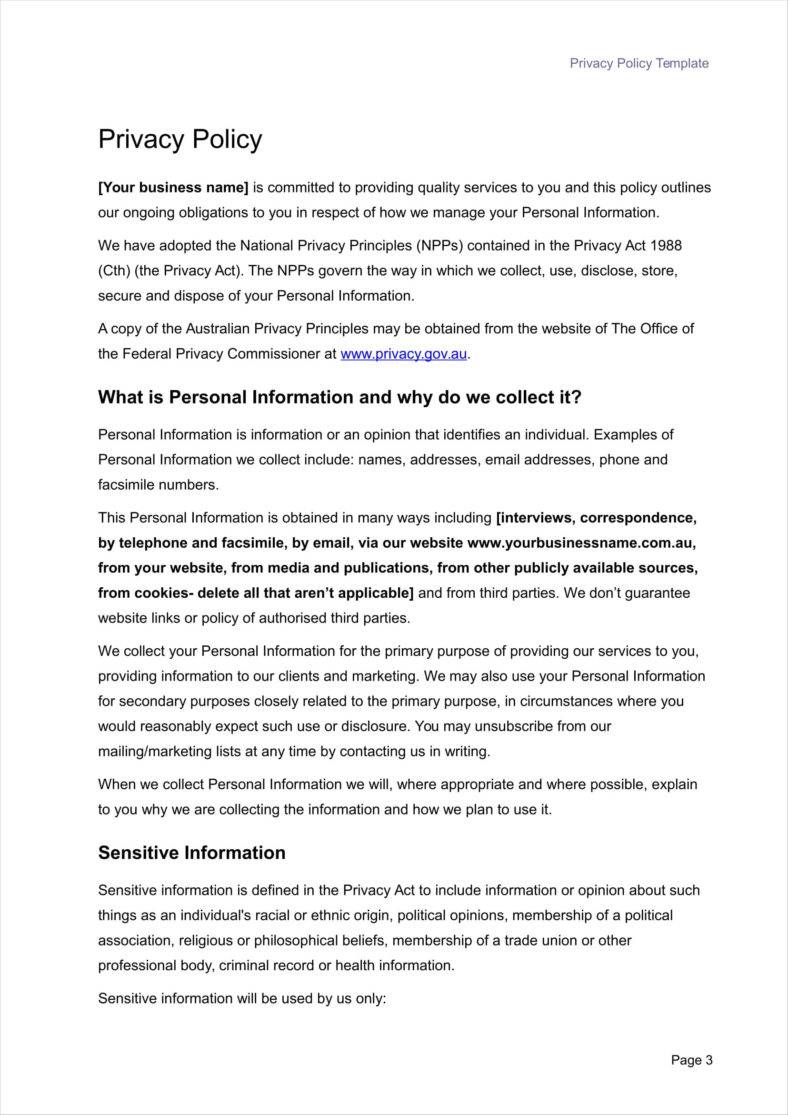


![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-17.jpg)


![Free Printable Policy And Procedure Templates [Word, PDF] Examples](https://www.typecalendar.com/wp-content/uploads/2023/05/policy-and-procedure-template-word.jpg?gid=298)
![Free Printable Policy And Procedure Templates [Word, PDF] Examples](https://www.typecalendar.com/wp-content/uploads/2023/05/Policy-and-Procedure-1-1536x864.jpg)



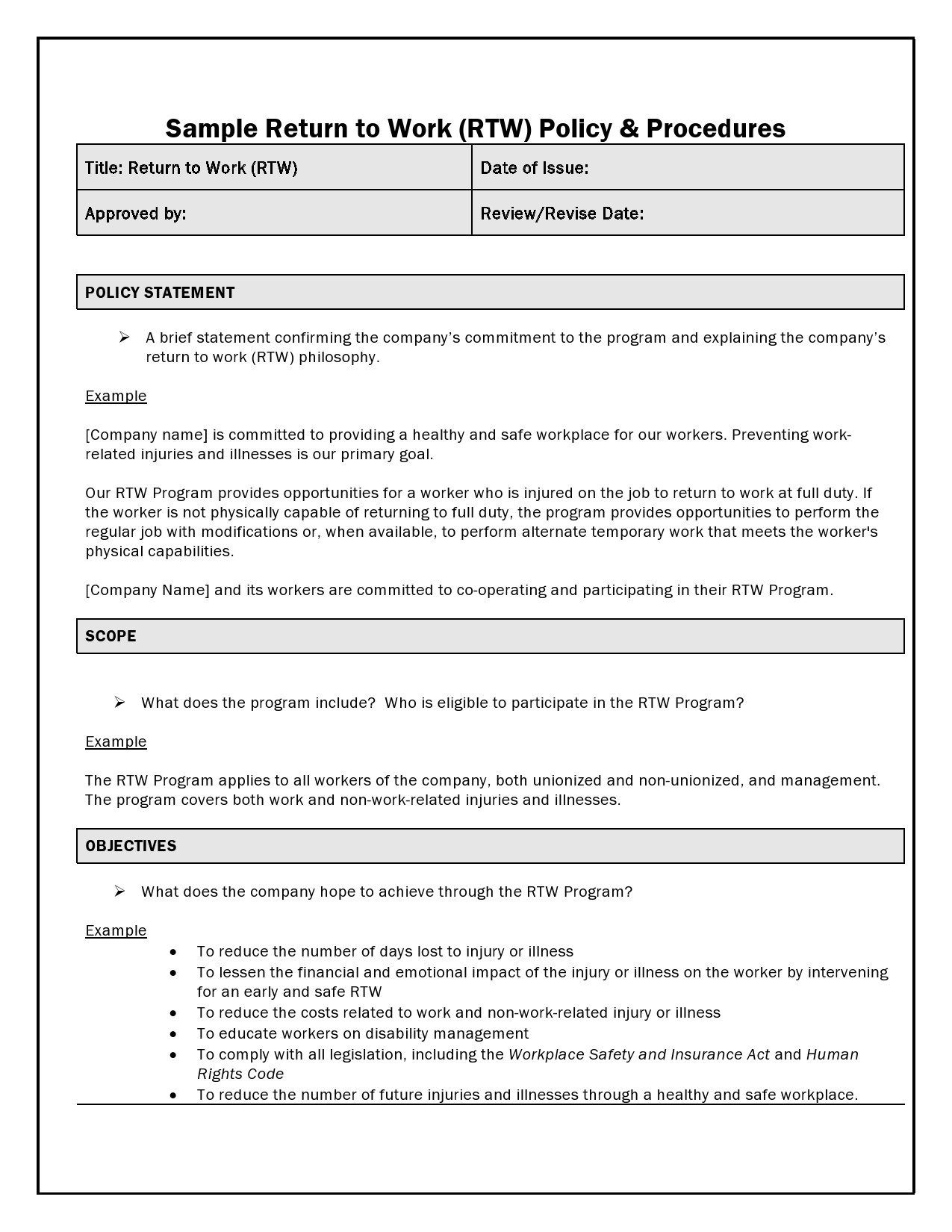





![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-10.jpg)


![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-19.jpg)