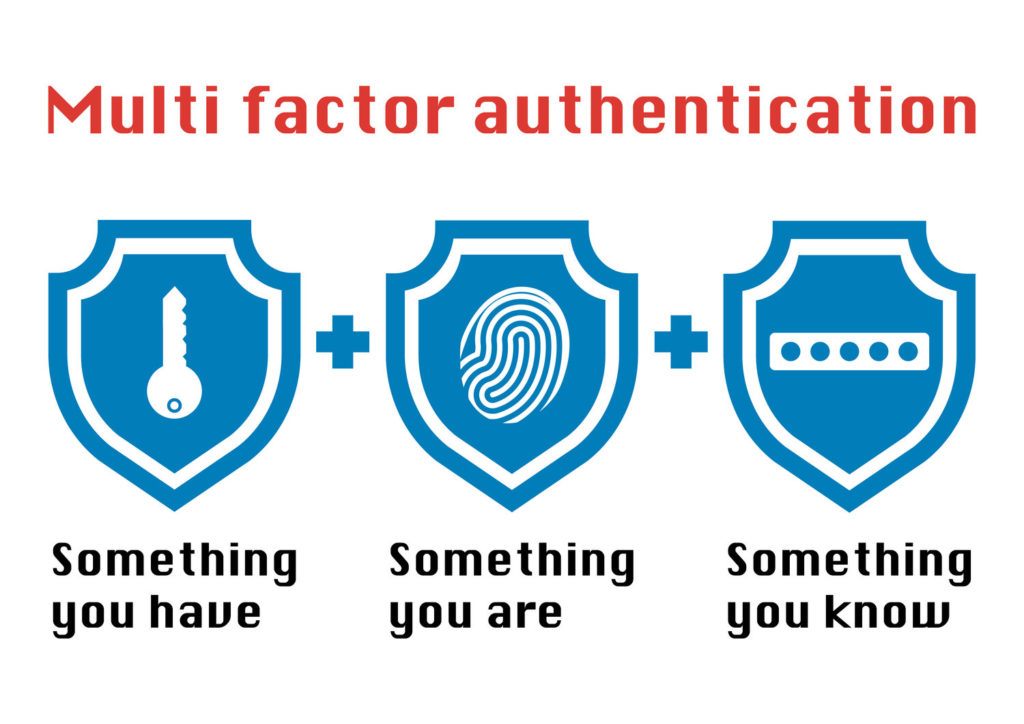
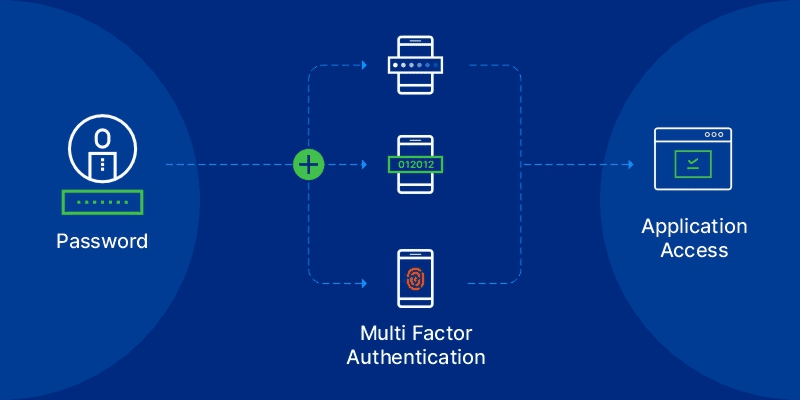
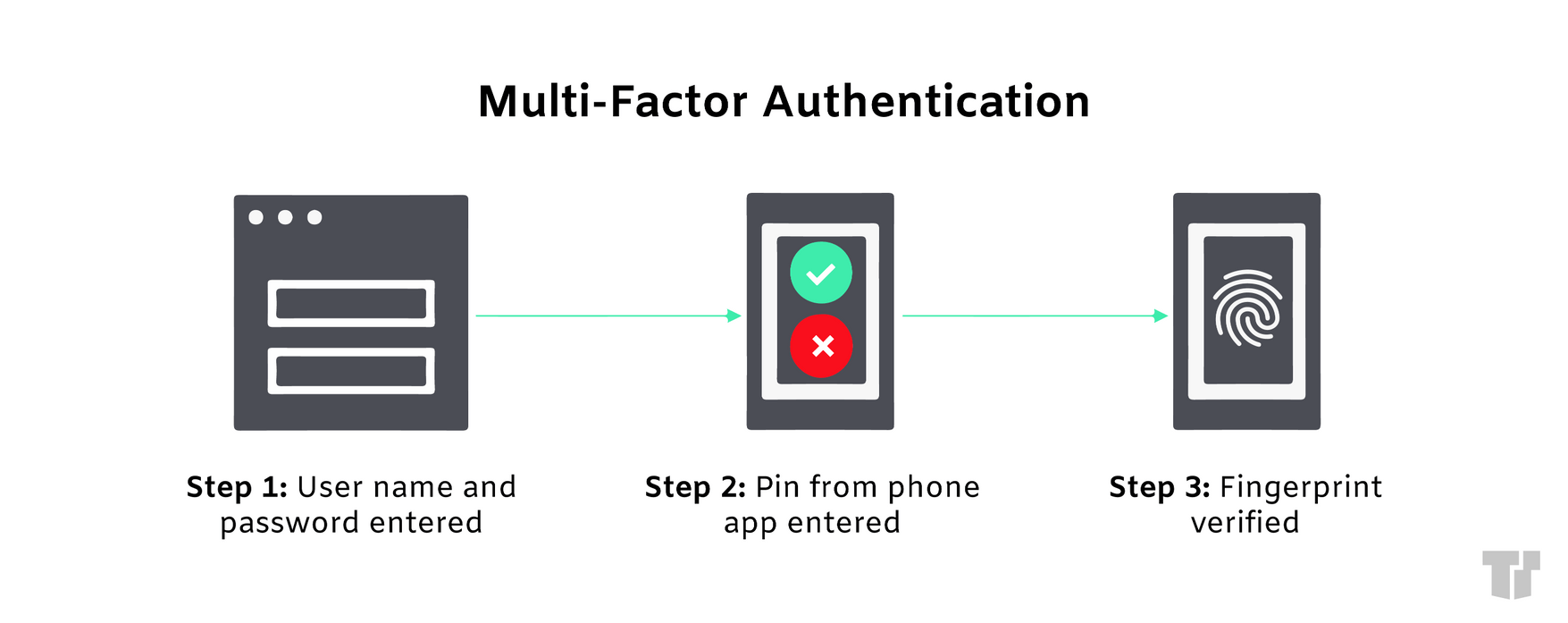
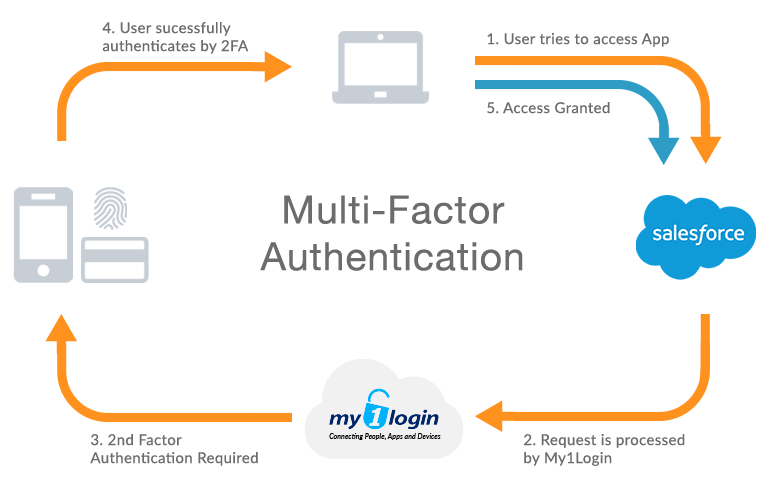
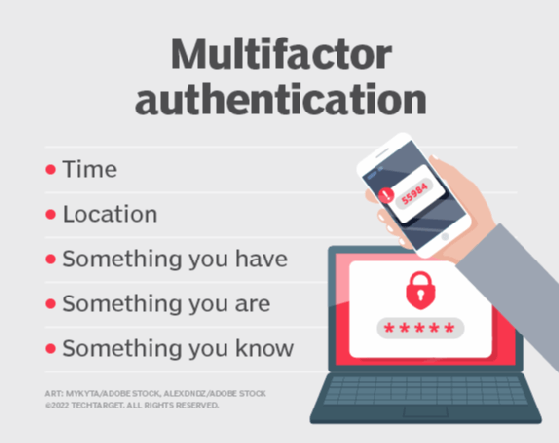
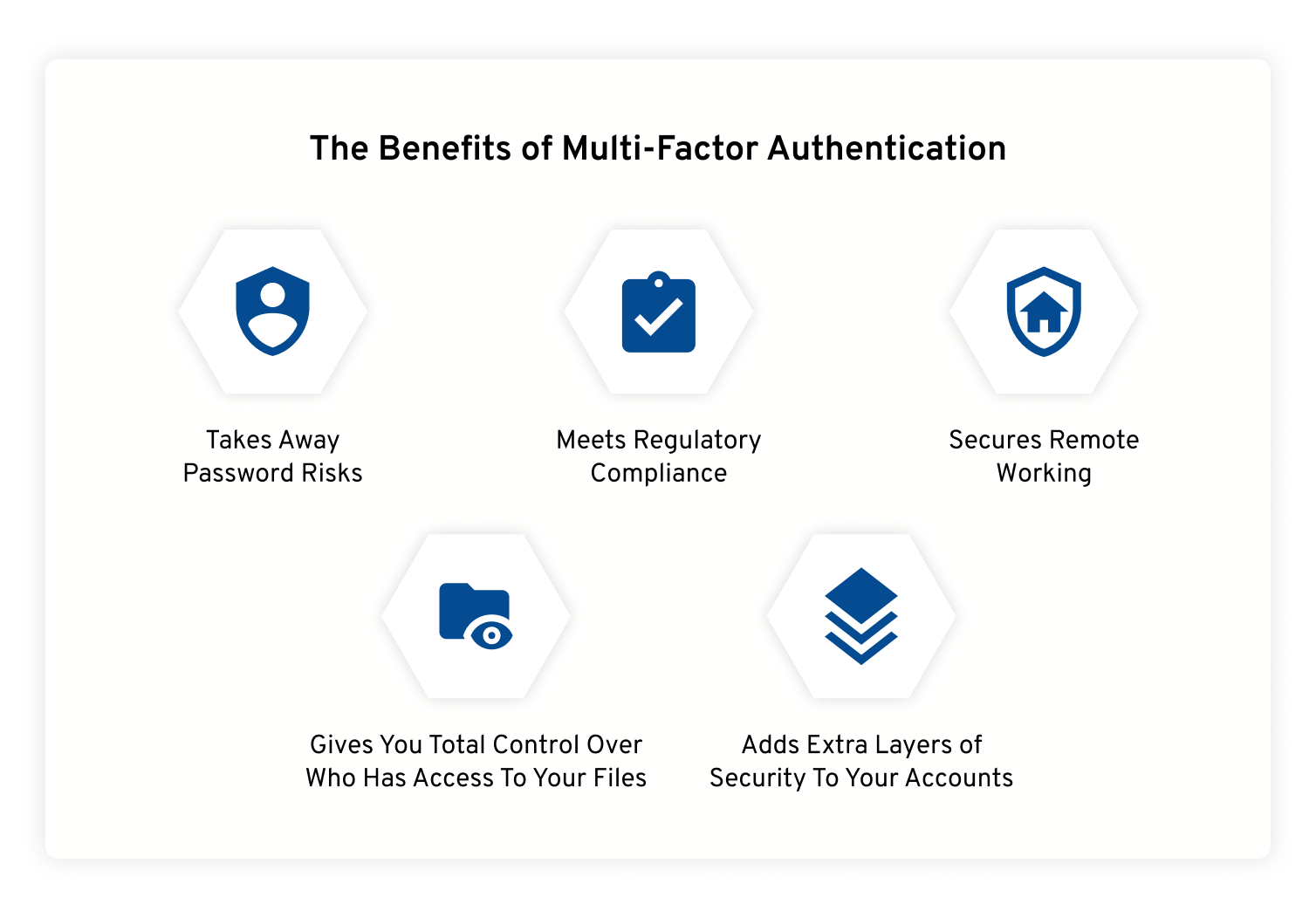
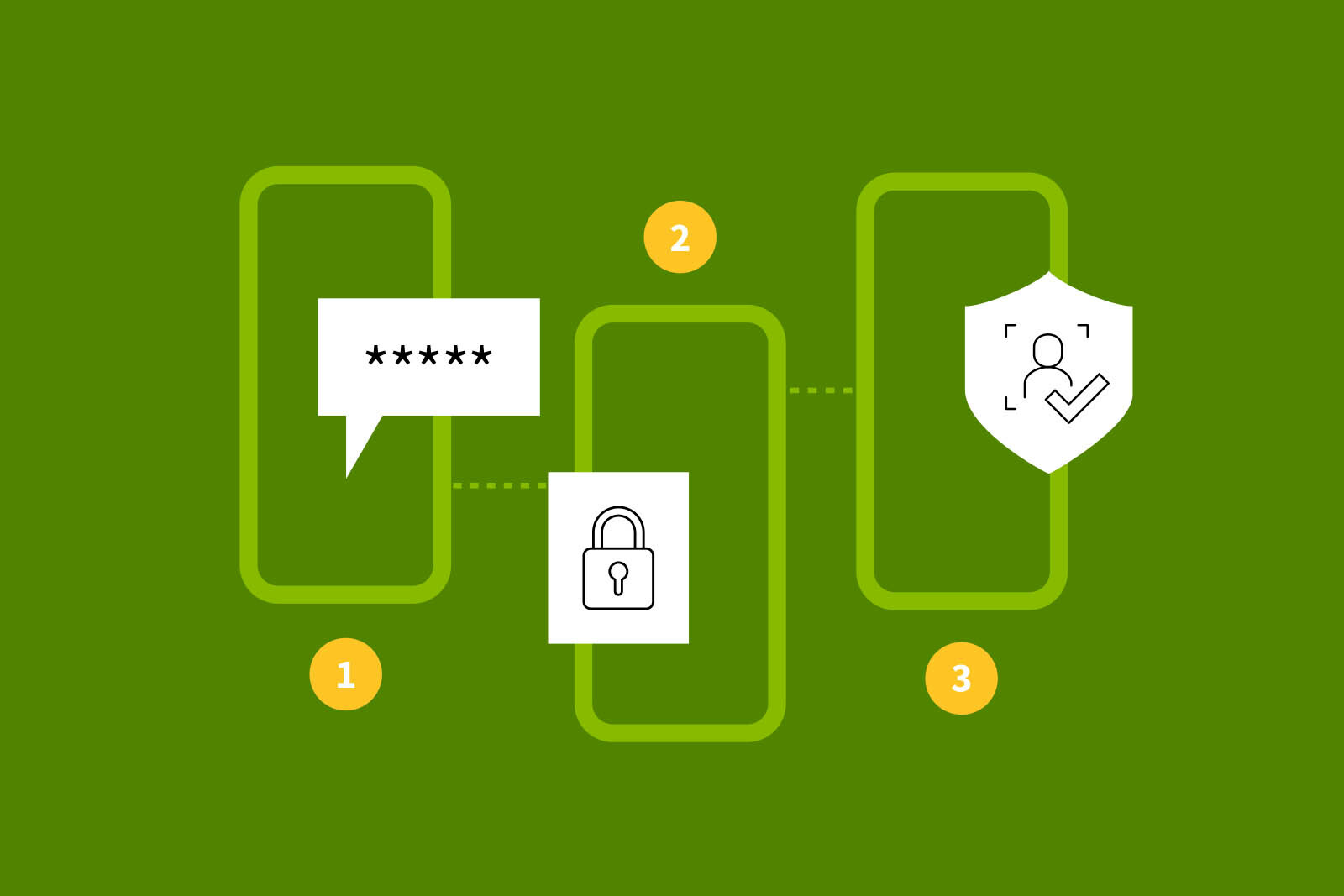
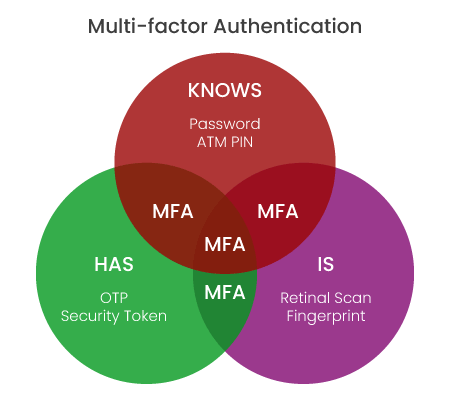
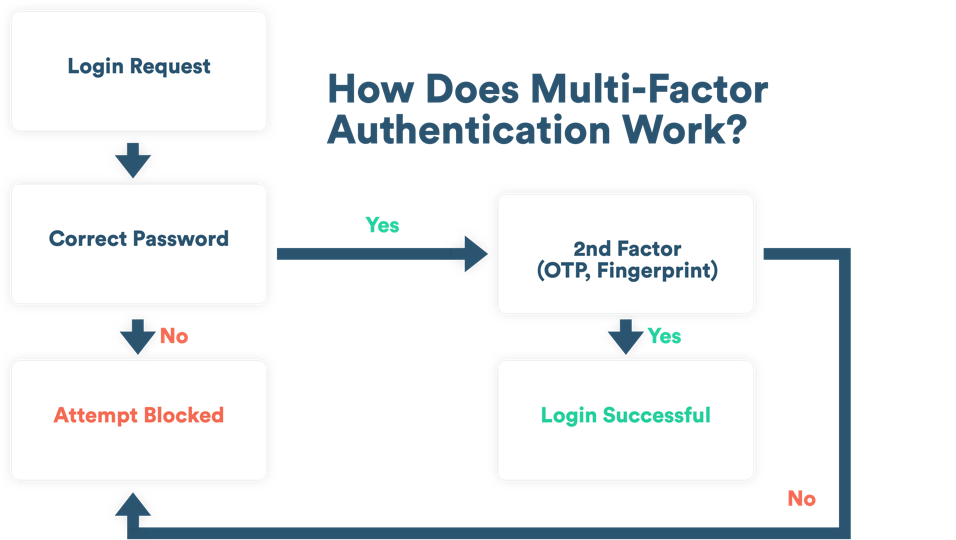
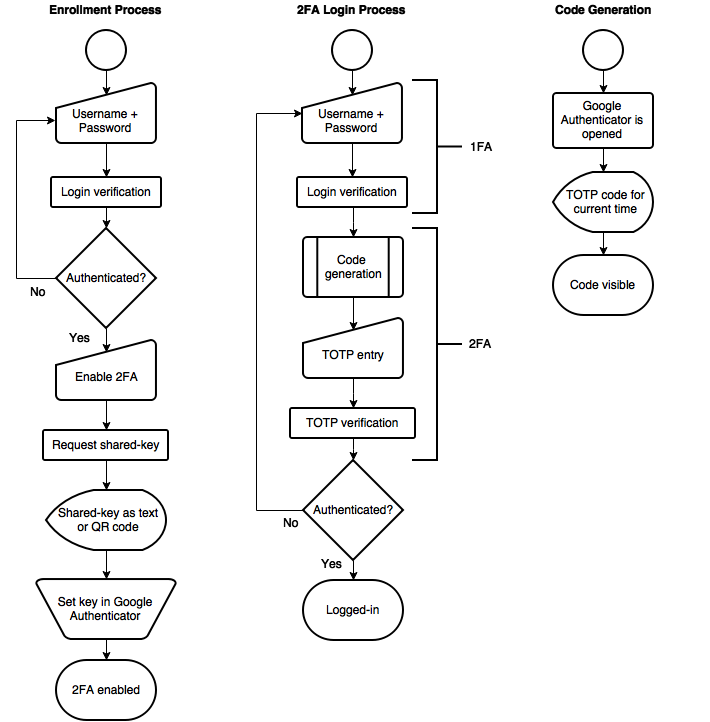
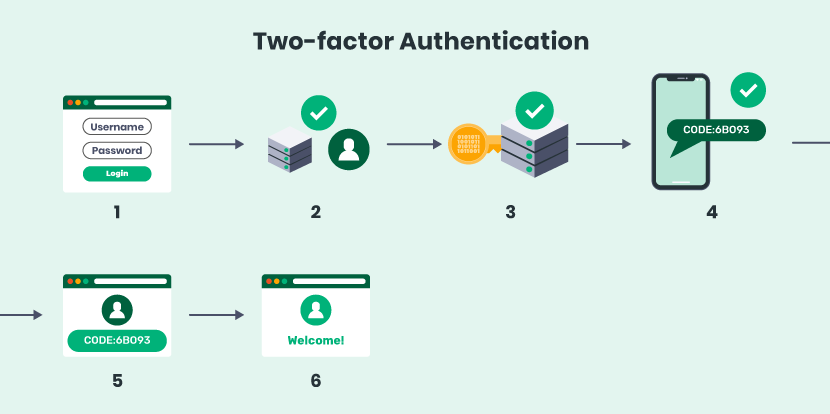
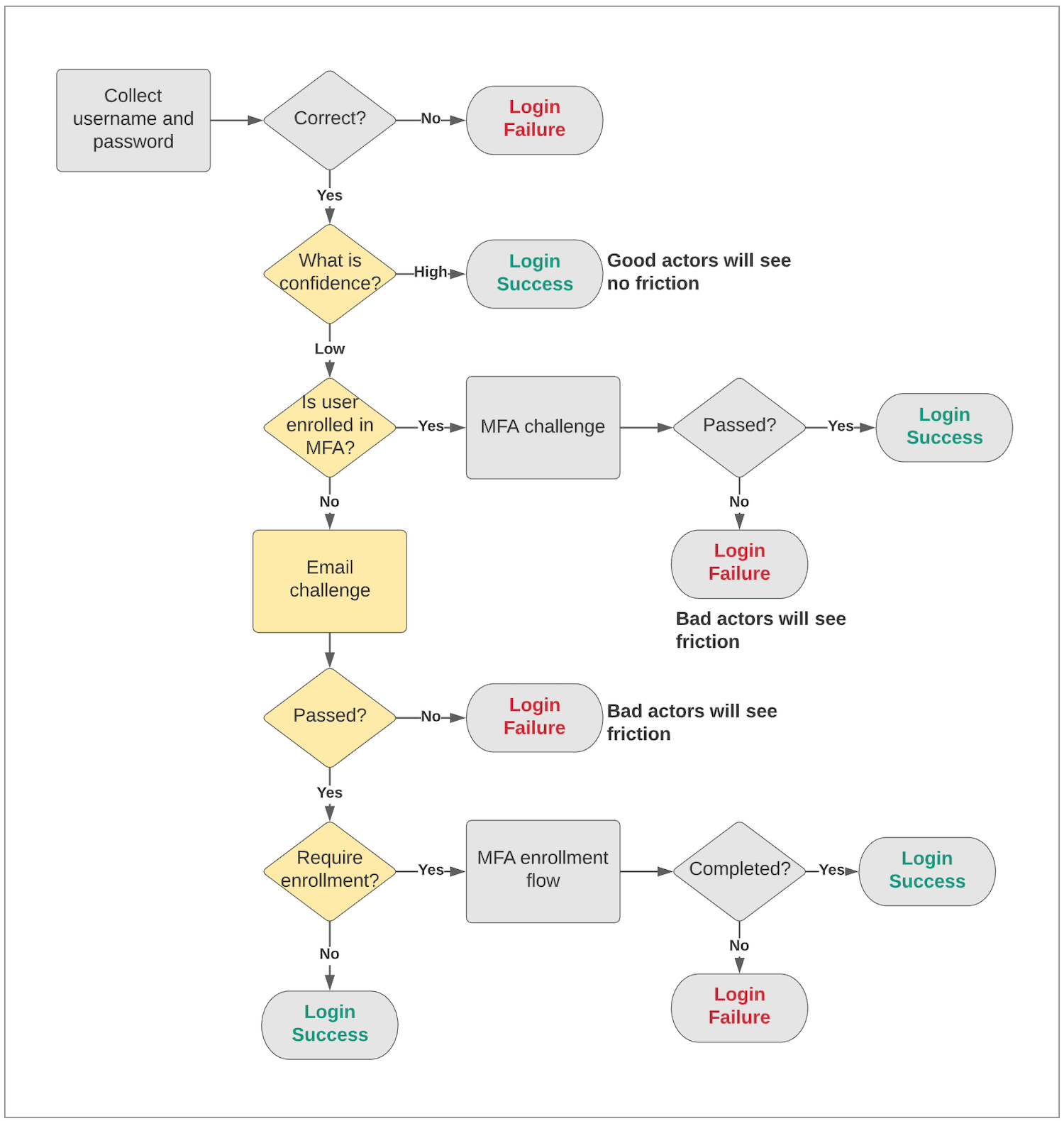
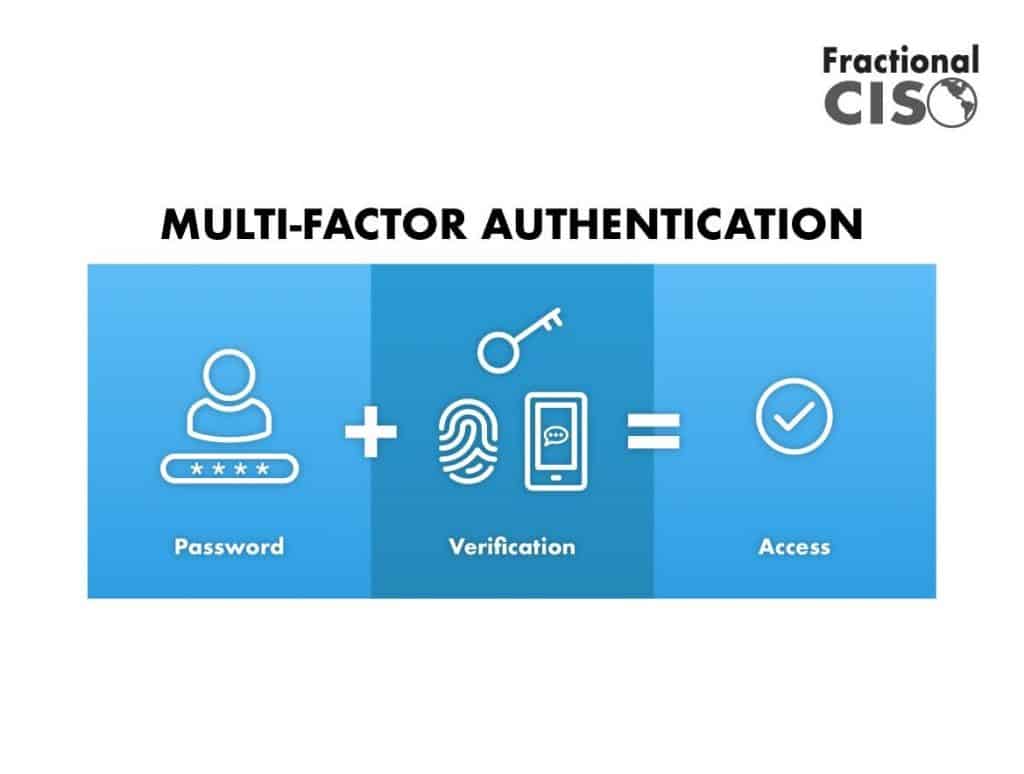
Multi Factor Authentication Diagram
Showcase trends with our fashion Multi Factor Authentication Diagram gallery of countless chic images. stylishly presenting photography, images, and pictures. ideal for style blogs and trend reporting. Each Multi Factor Authentication Diagram image is carefully selected for superior visual impact and professional quality. Suitable for various applications including web design, social media, personal projects, and digital content creation All Multi Factor Authentication Diagram images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Explore the versatility of our Multi Factor Authentication Diagram collection for various creative and professional projects. Time-saving browsing features help users locate ideal Multi Factor Authentication Diagram images quickly. Multiple resolution options ensure optimal performance across different platforms and applications. Our Multi Factor Authentication Diagram database continuously expands with fresh, relevant content from skilled photographers. Diverse style options within the Multi Factor Authentication Diagram collection suit various aesthetic preferences. Instant download capabilities enable immediate access to chosen Multi Factor Authentication Diagram images. Reliable customer support ensures smooth experience throughout the Multi Factor Authentication Diagram selection process. Professional licensing options accommodate both commercial and educational usage requirements. Each image in our Multi Factor Authentication Diagram gallery undergoes rigorous quality assessment before inclusion.




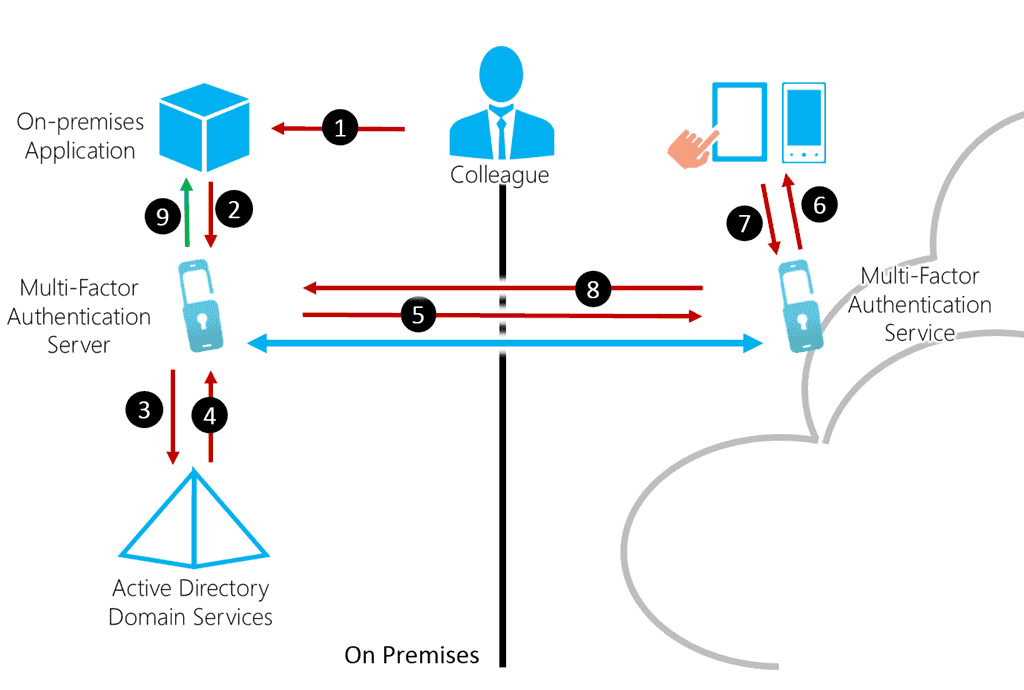
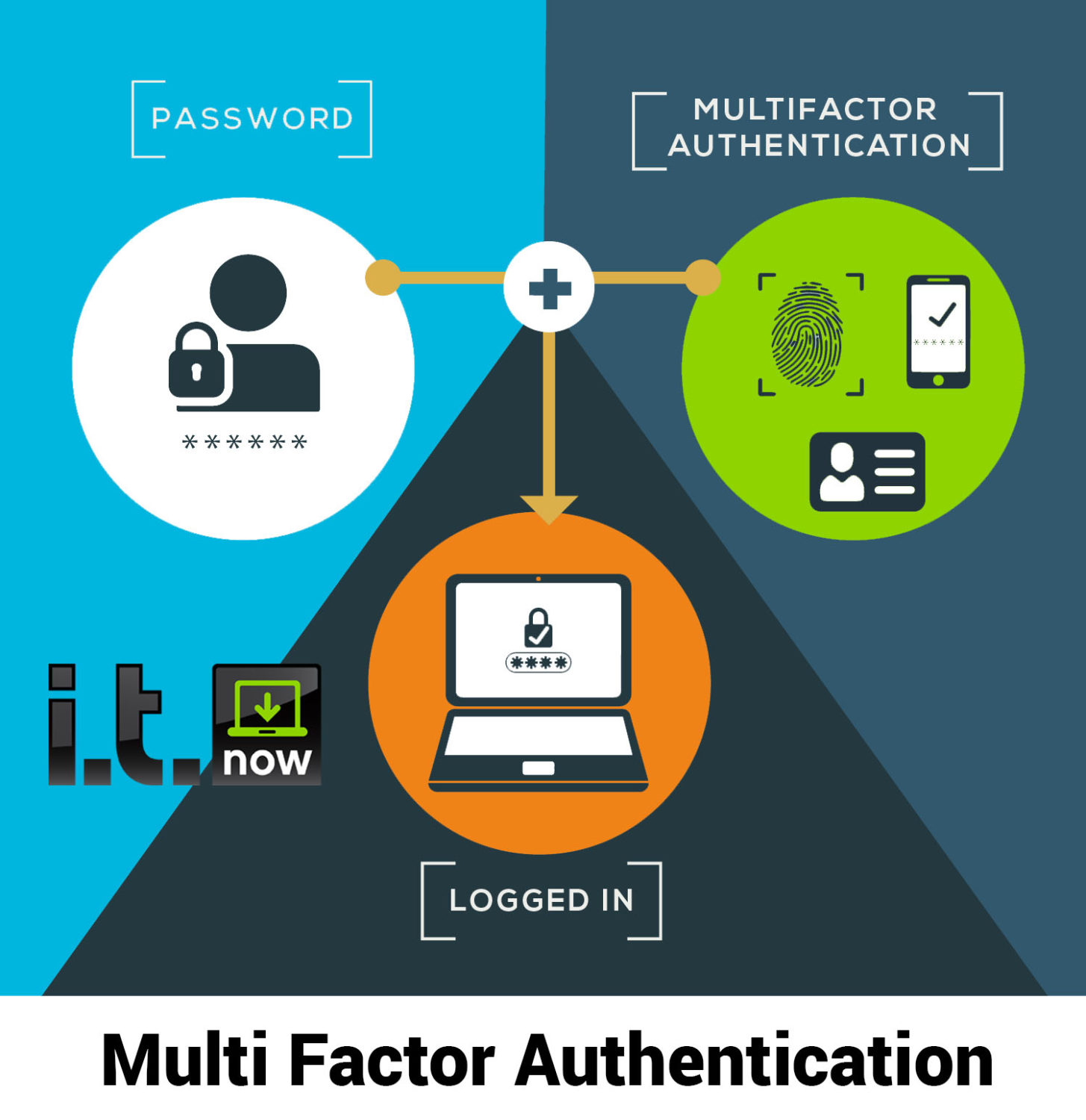
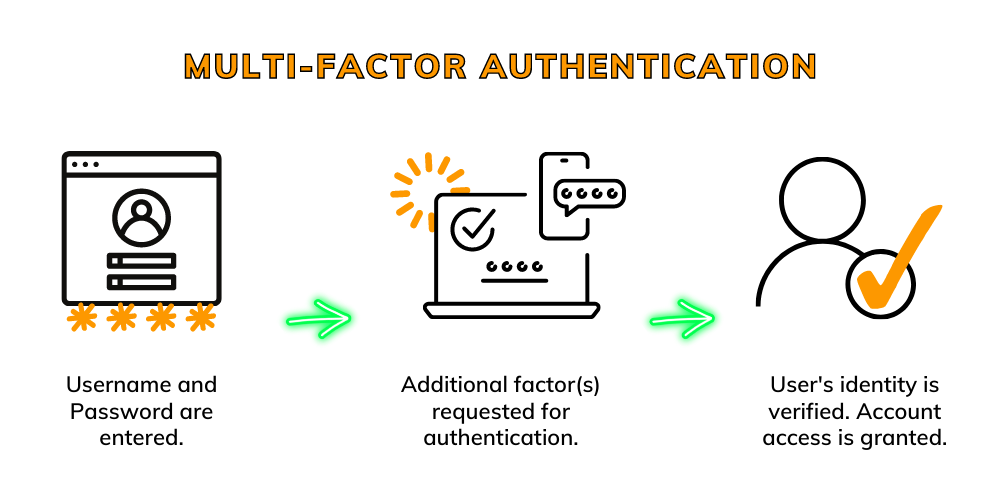
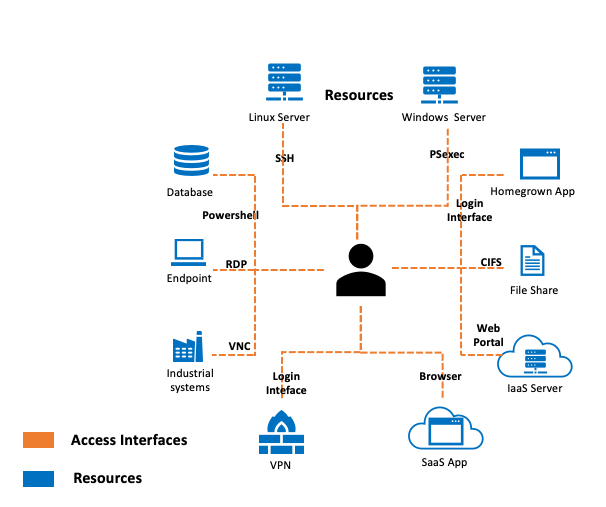
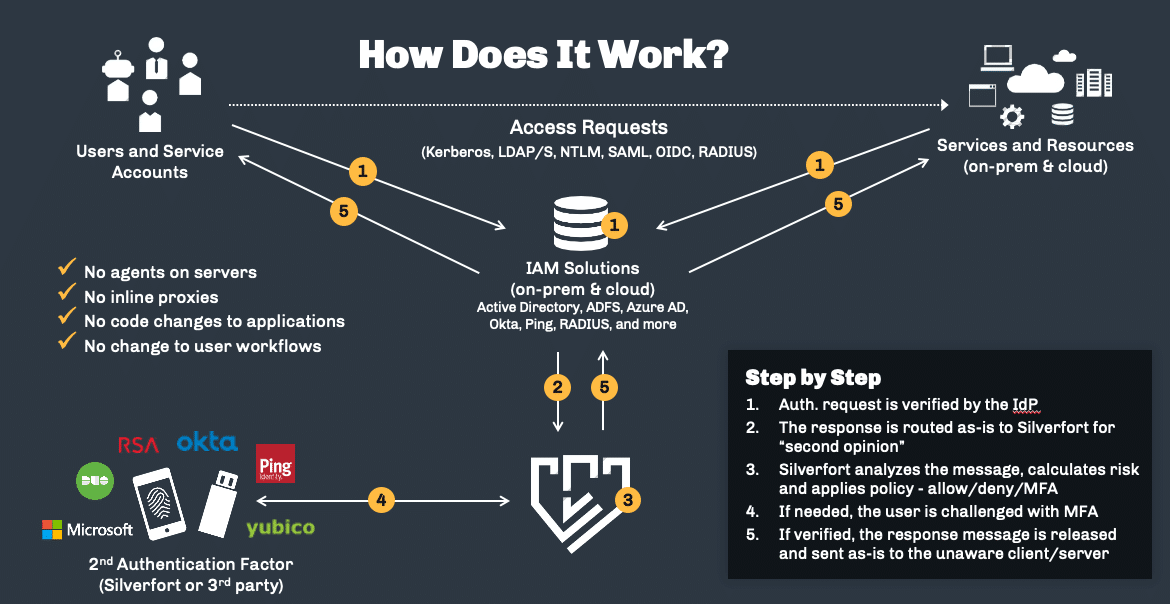


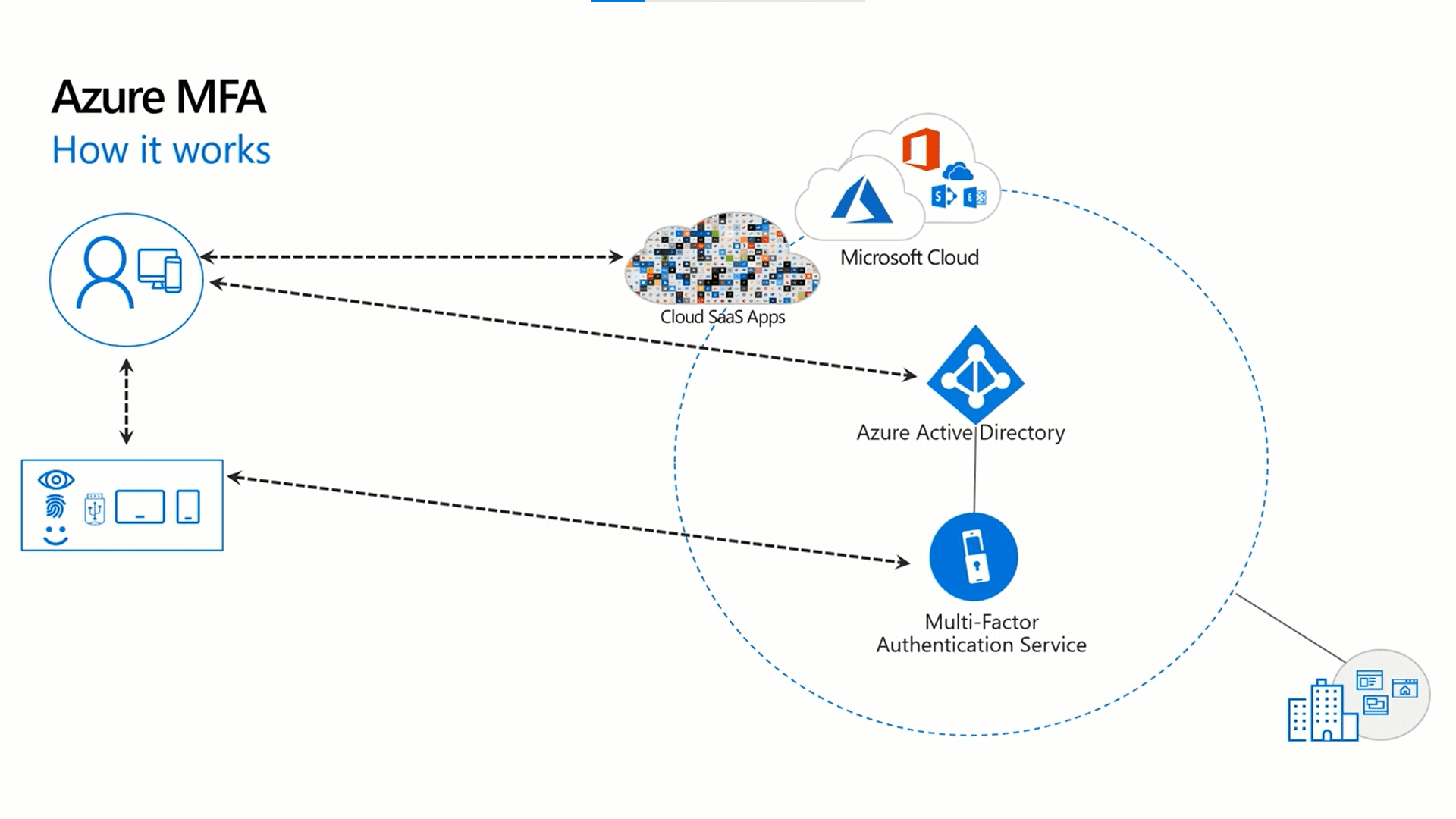


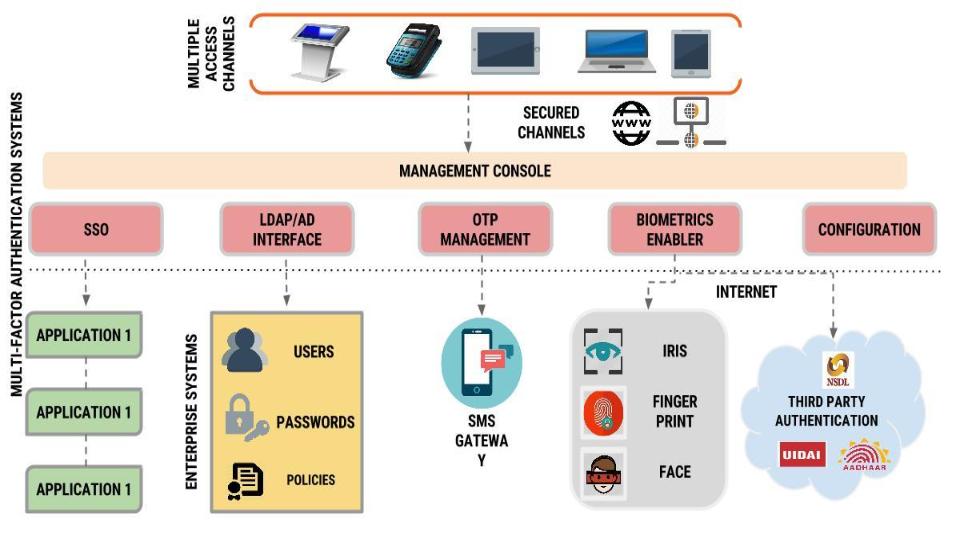
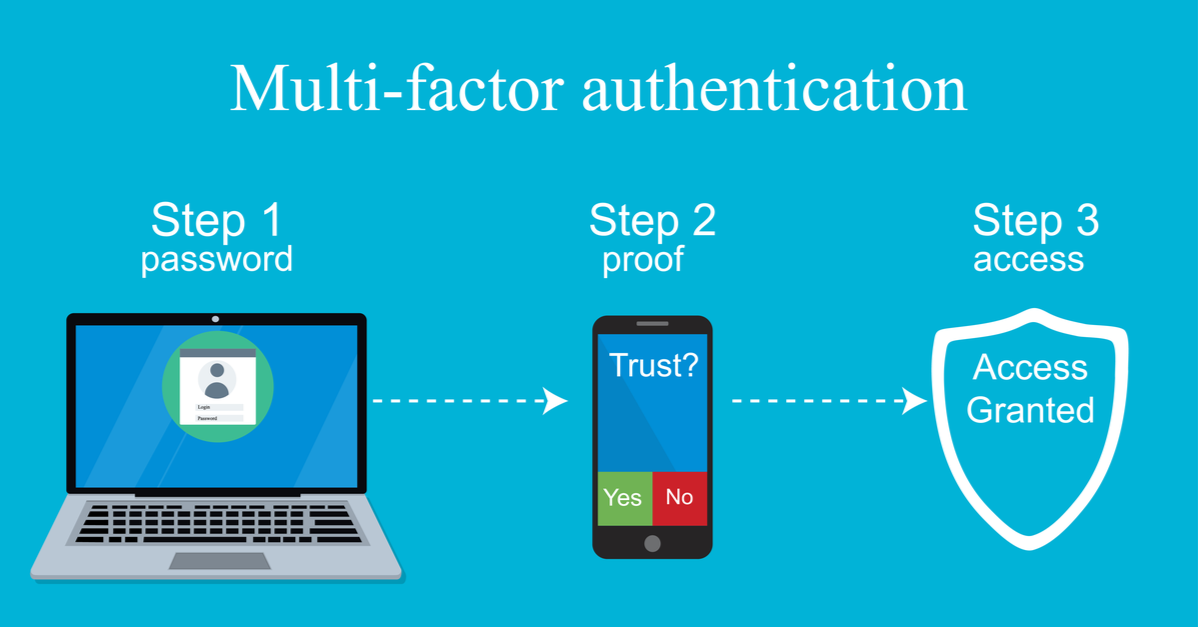
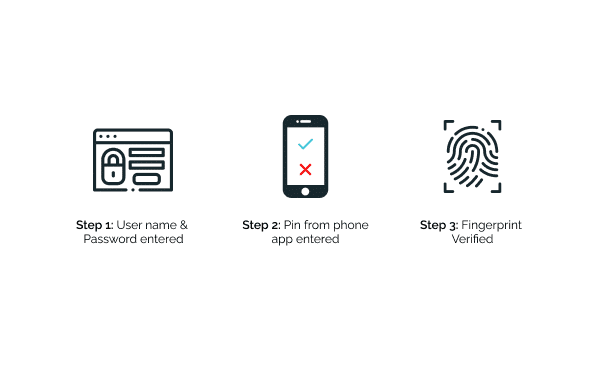




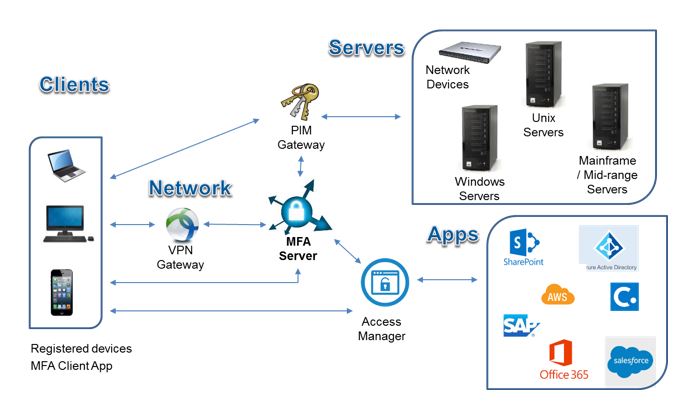
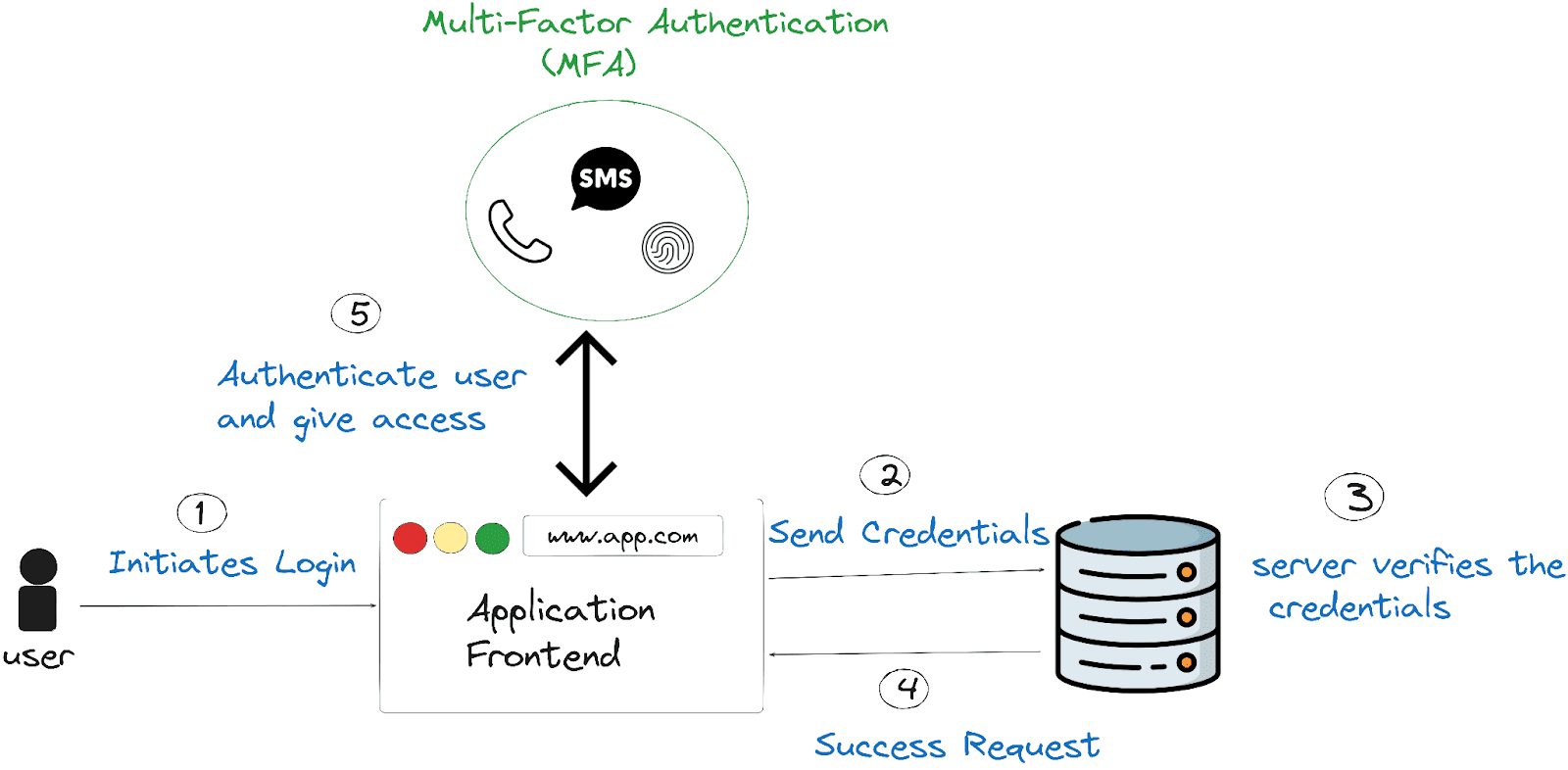
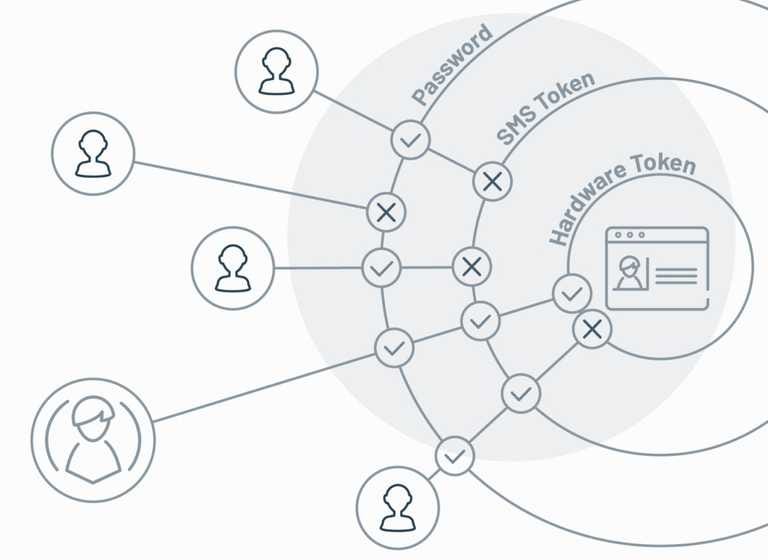
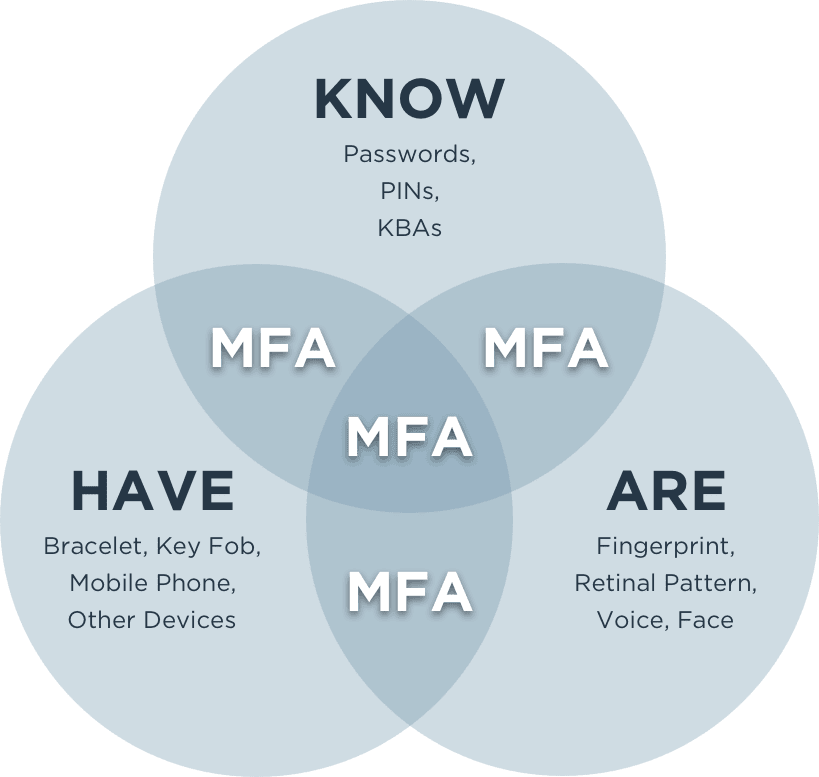
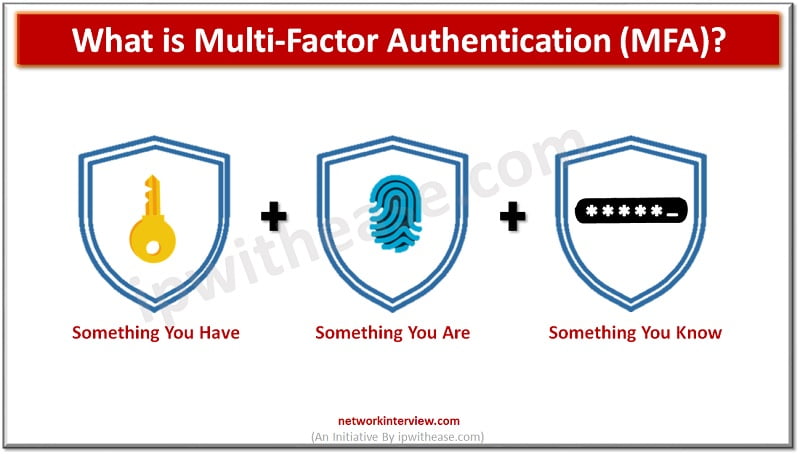
![2]: Multi-Factor Authentication | Download Scientific Diagram](https://www.researchgate.net/publication/331035134/figure/fig1/AS:725346743771137@1549947548708/Figure-12-Multi-Factor-Authentication.jpg)





















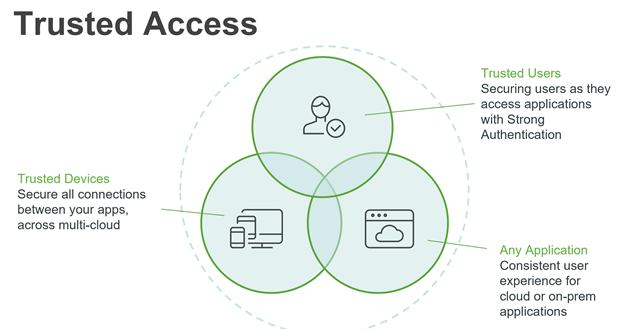


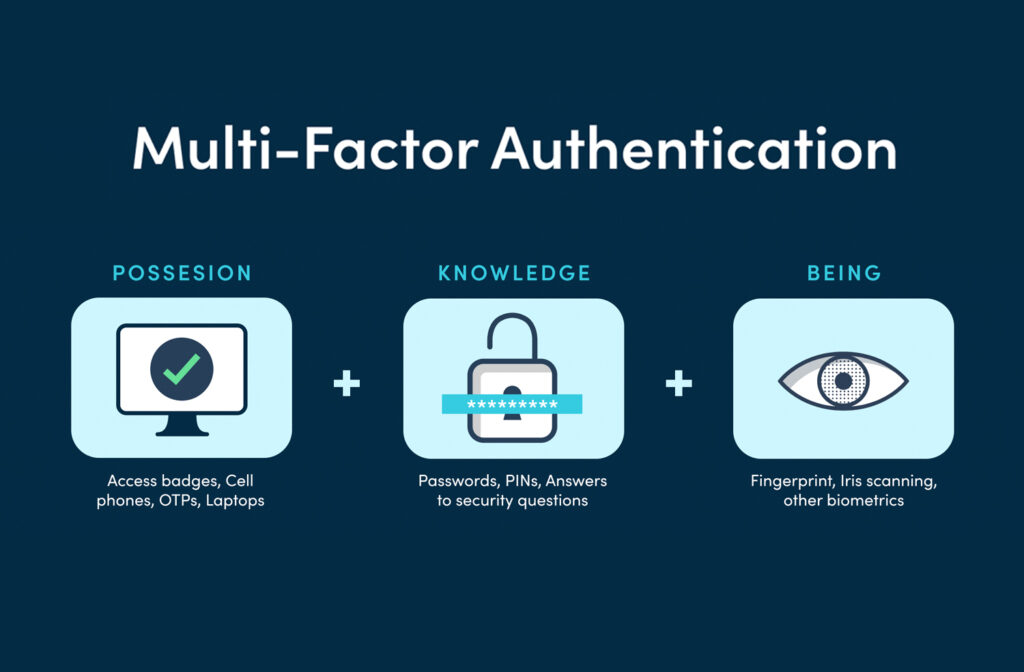


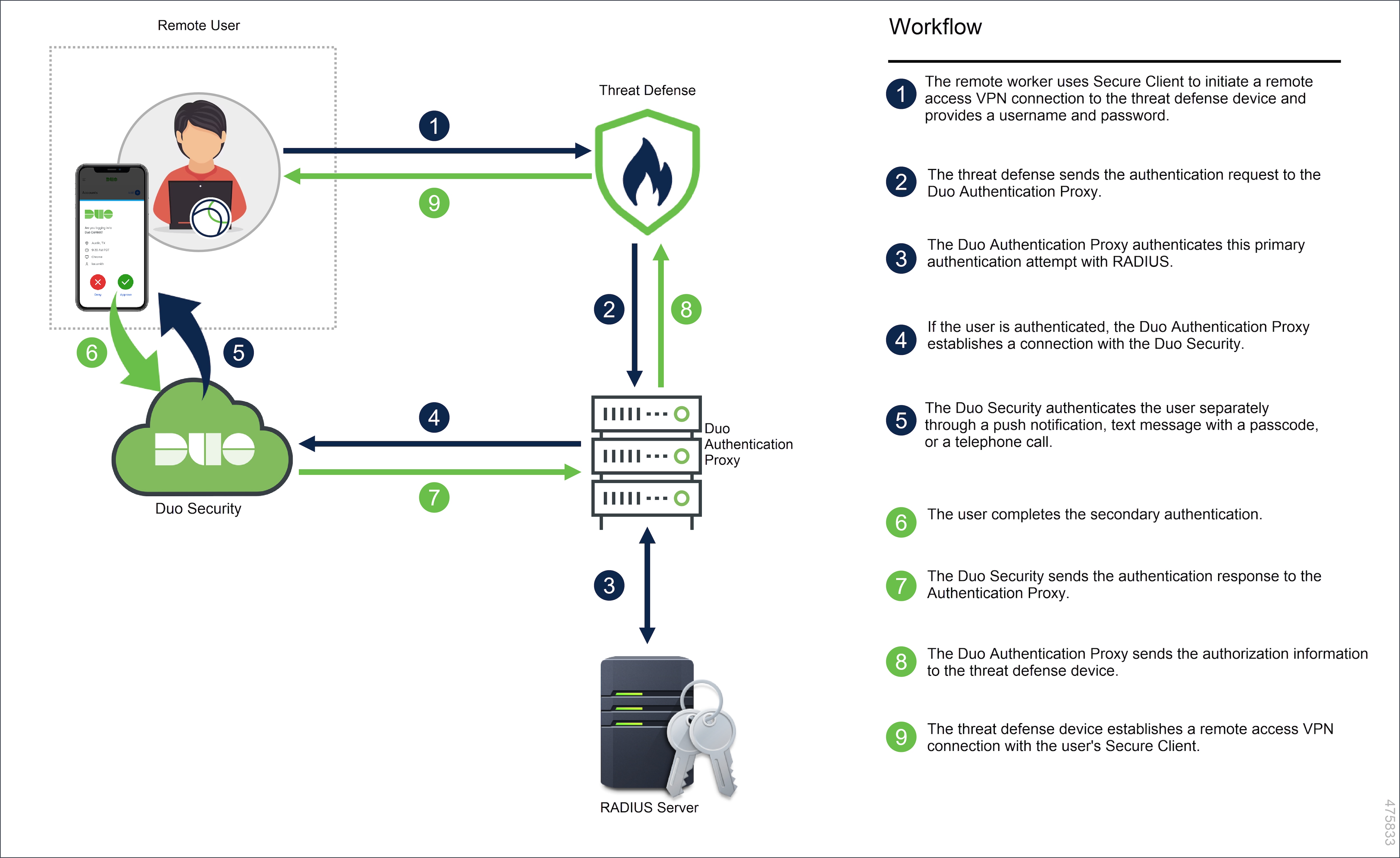

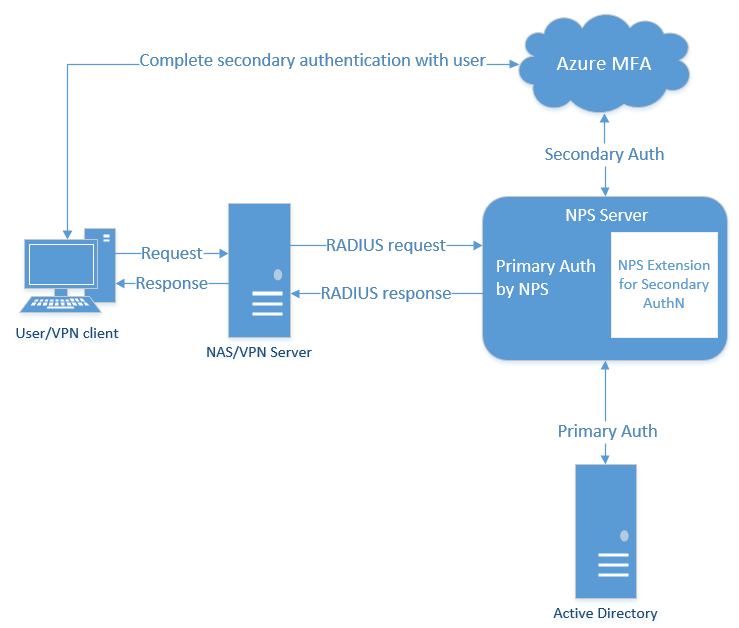





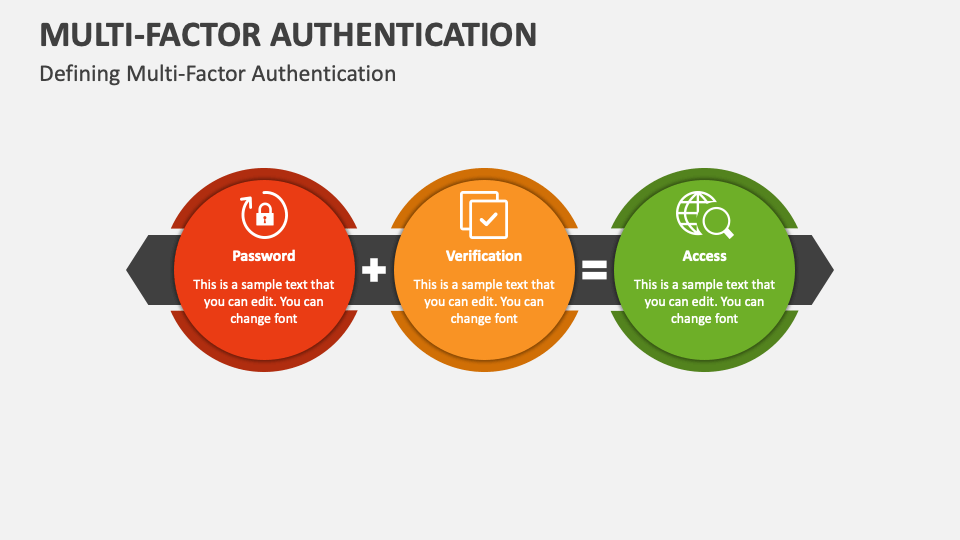



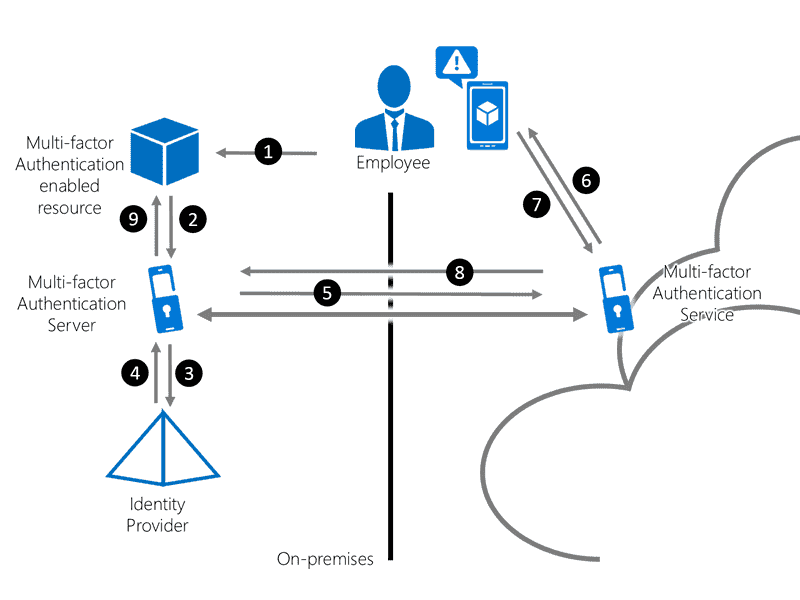
![[DIAGRAM] Microsoft Mfa Diagram - MYDIAGRAM.ONLINE](https://wyzguyscybersecurity.com/wp-content/uploads/2018/10/MFA-diagram.png)
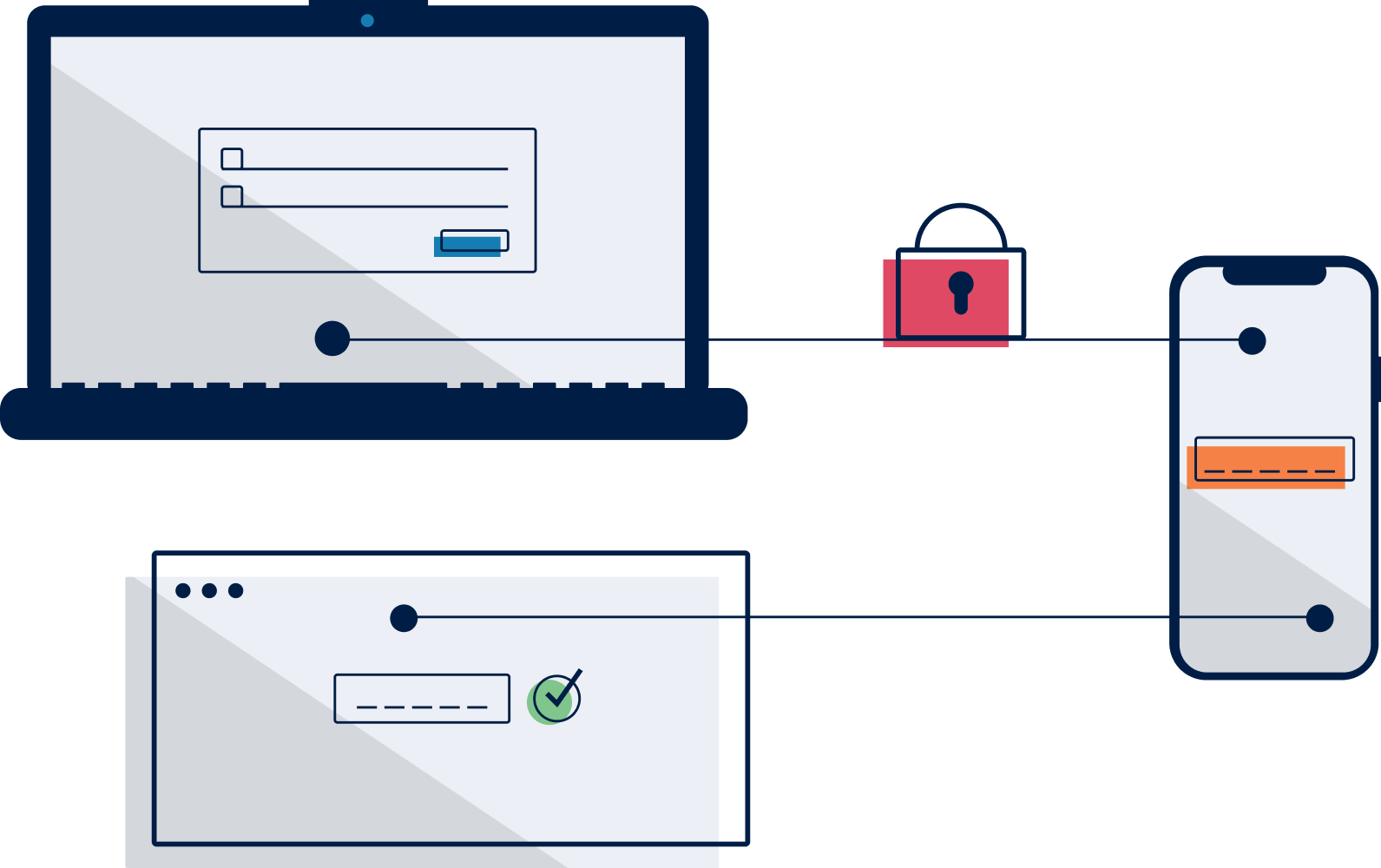


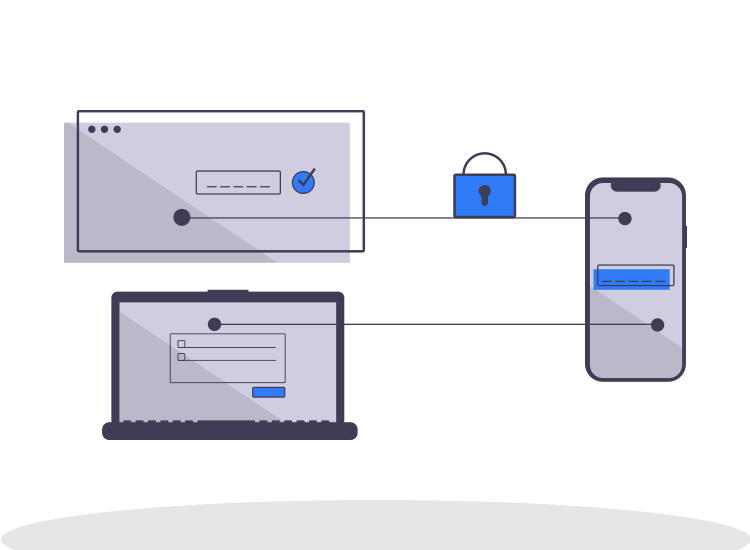











-768.png)



