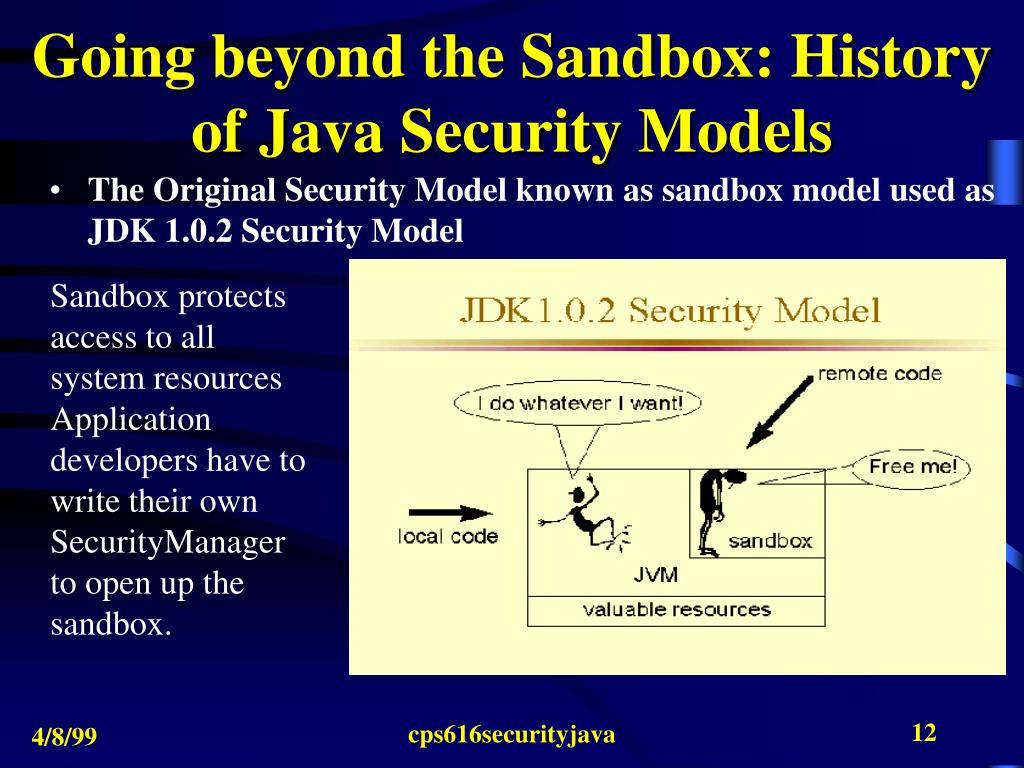
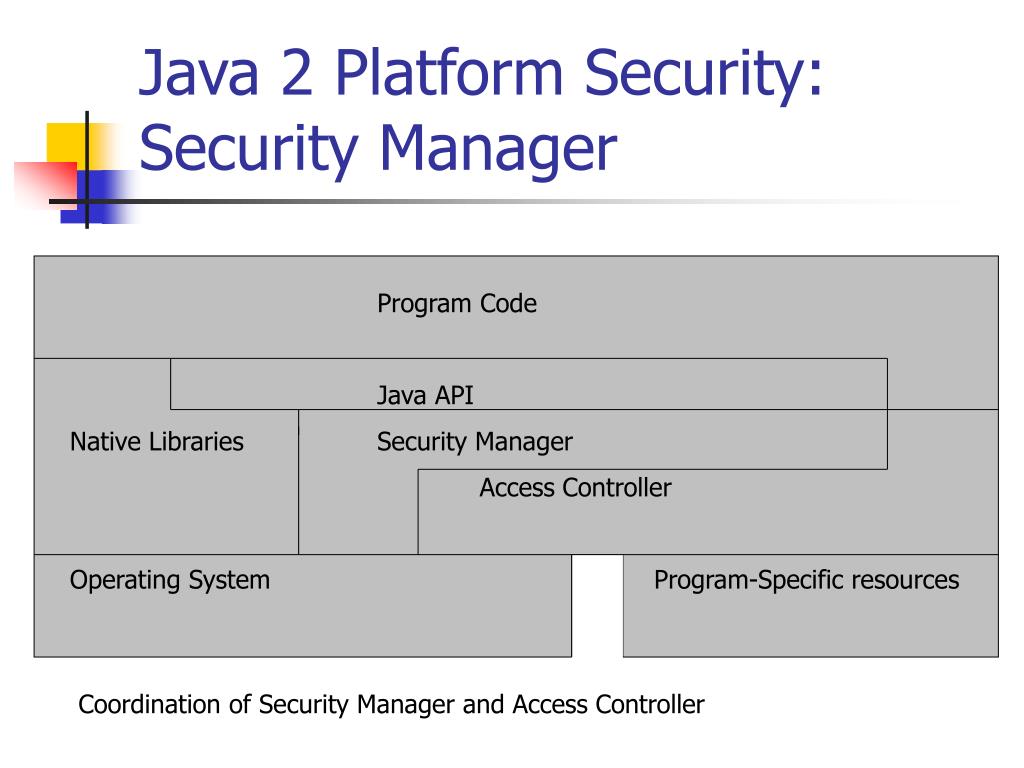
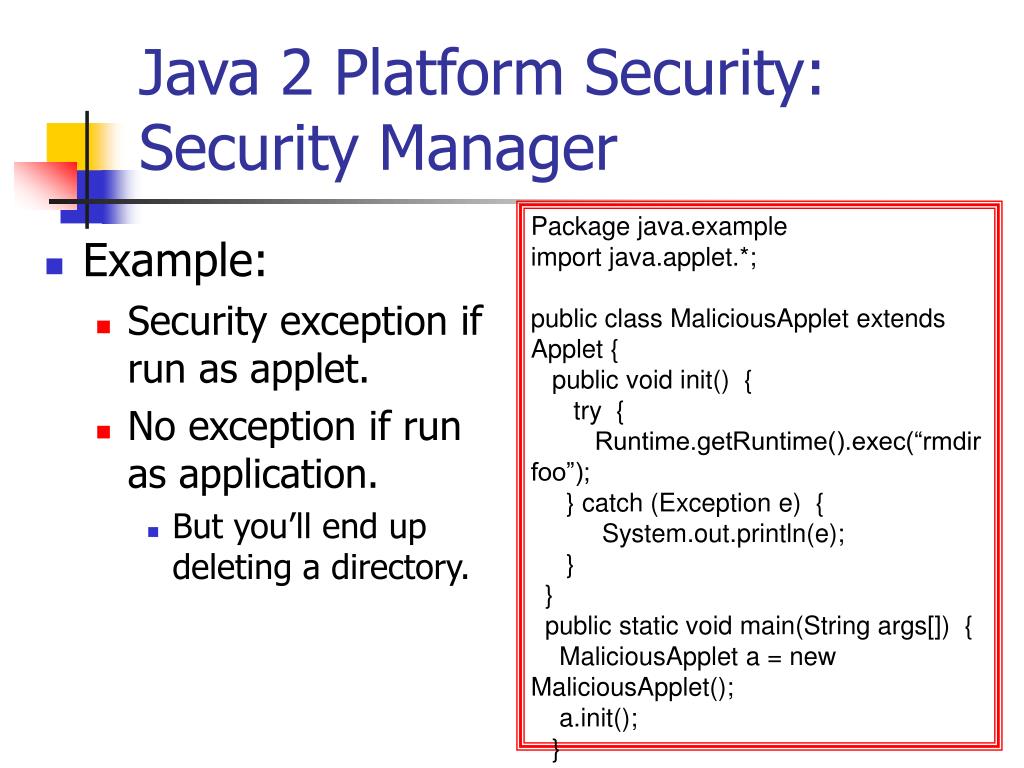
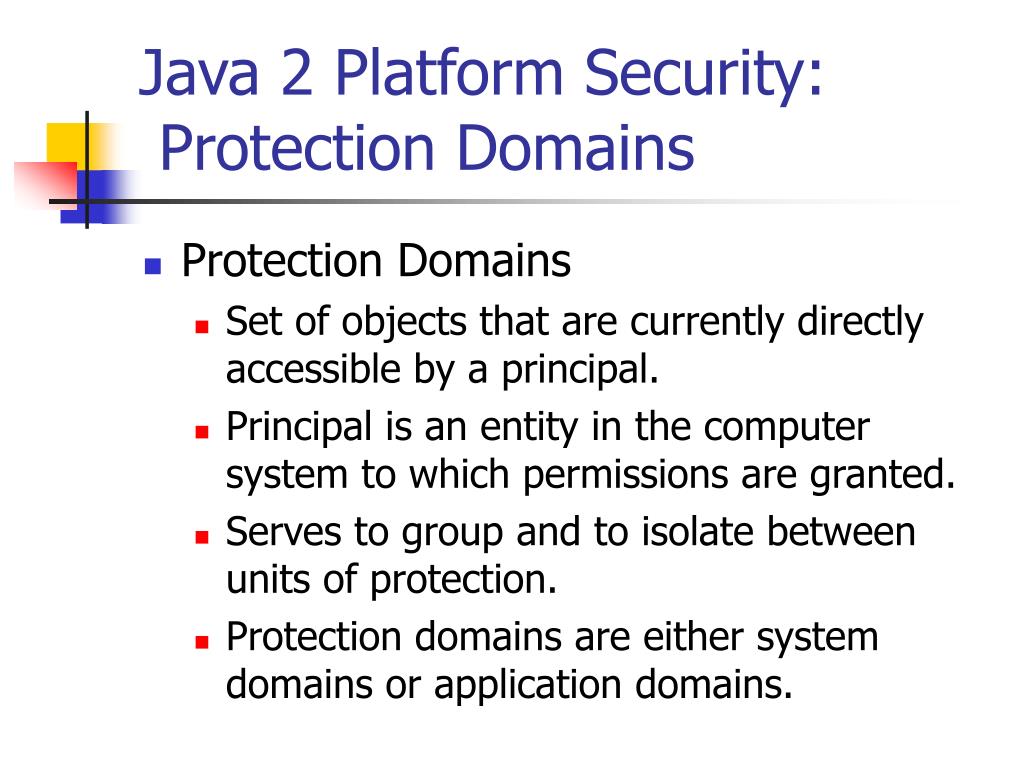
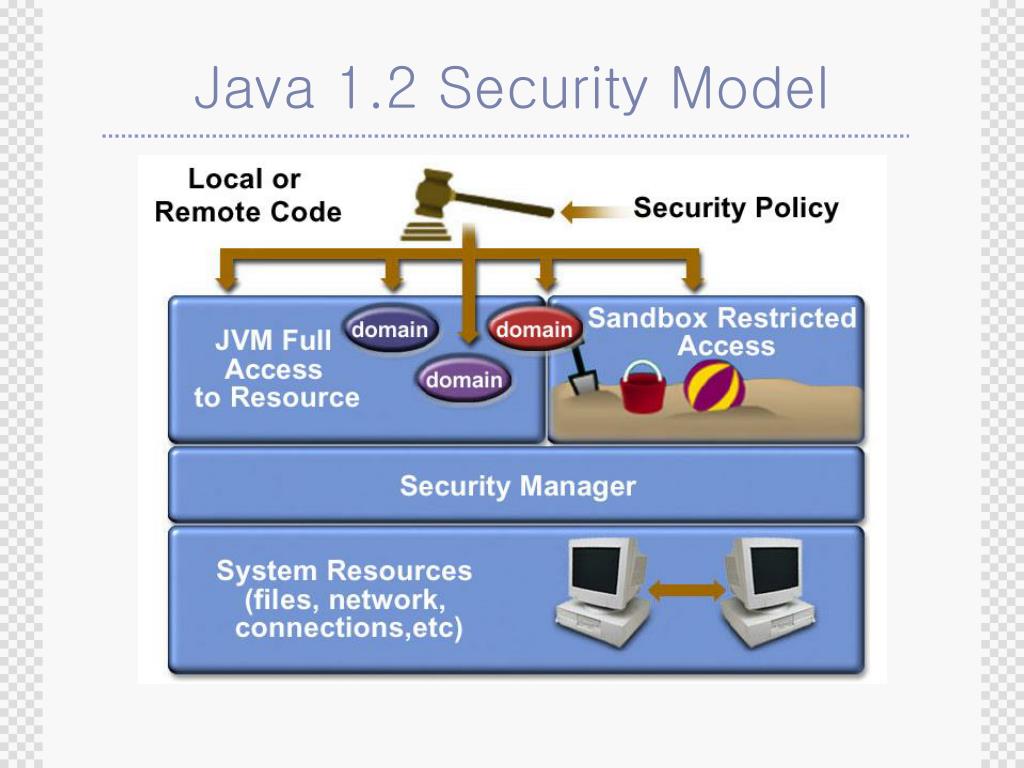
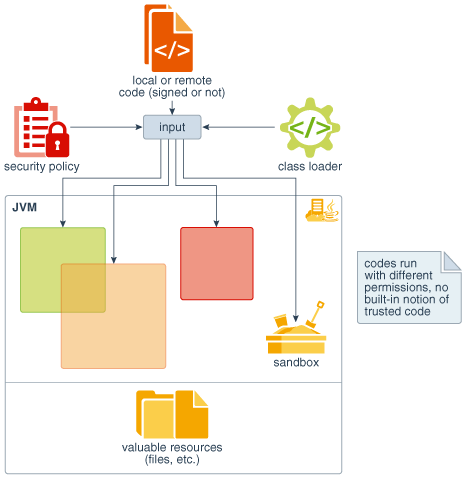
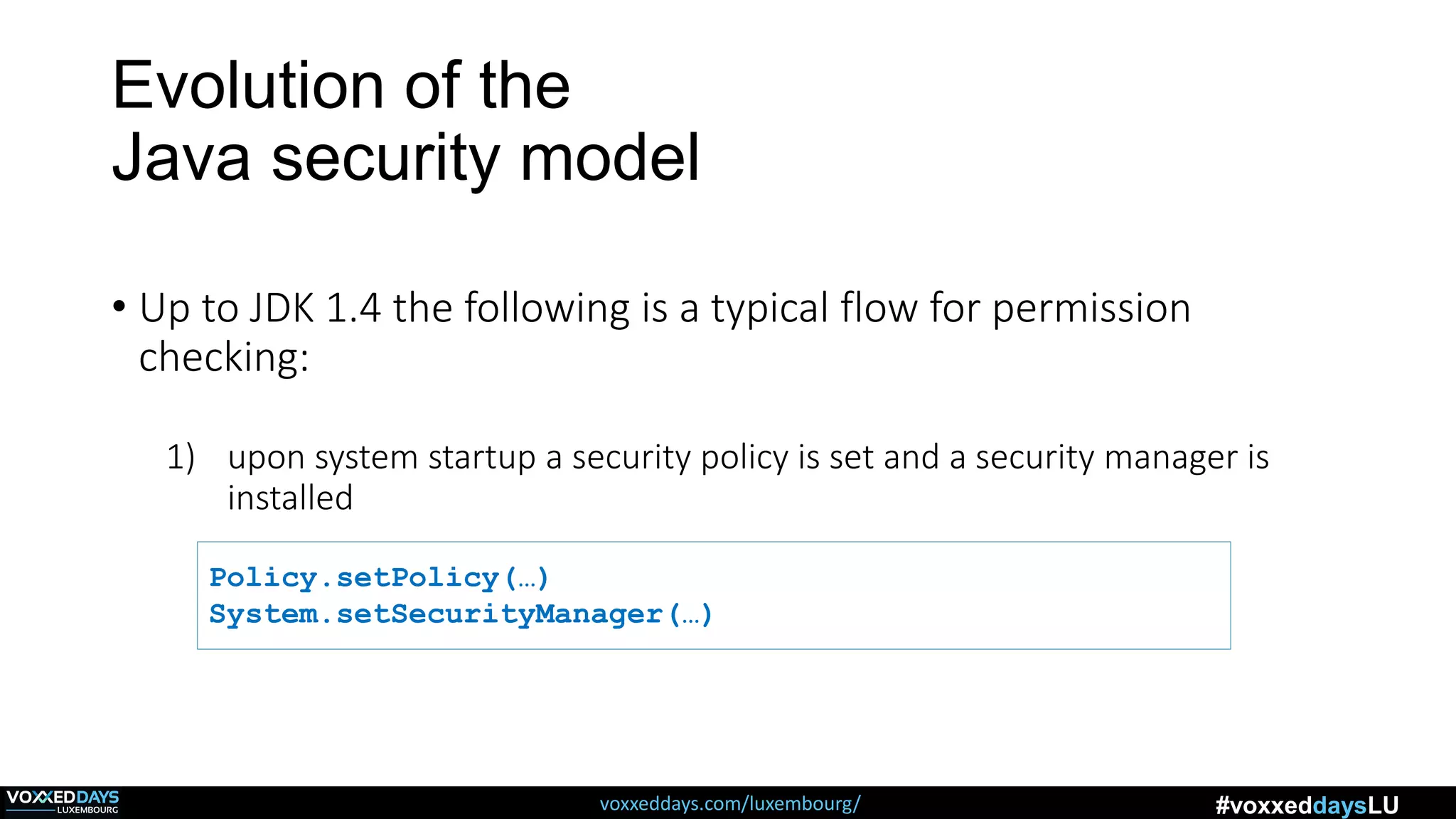
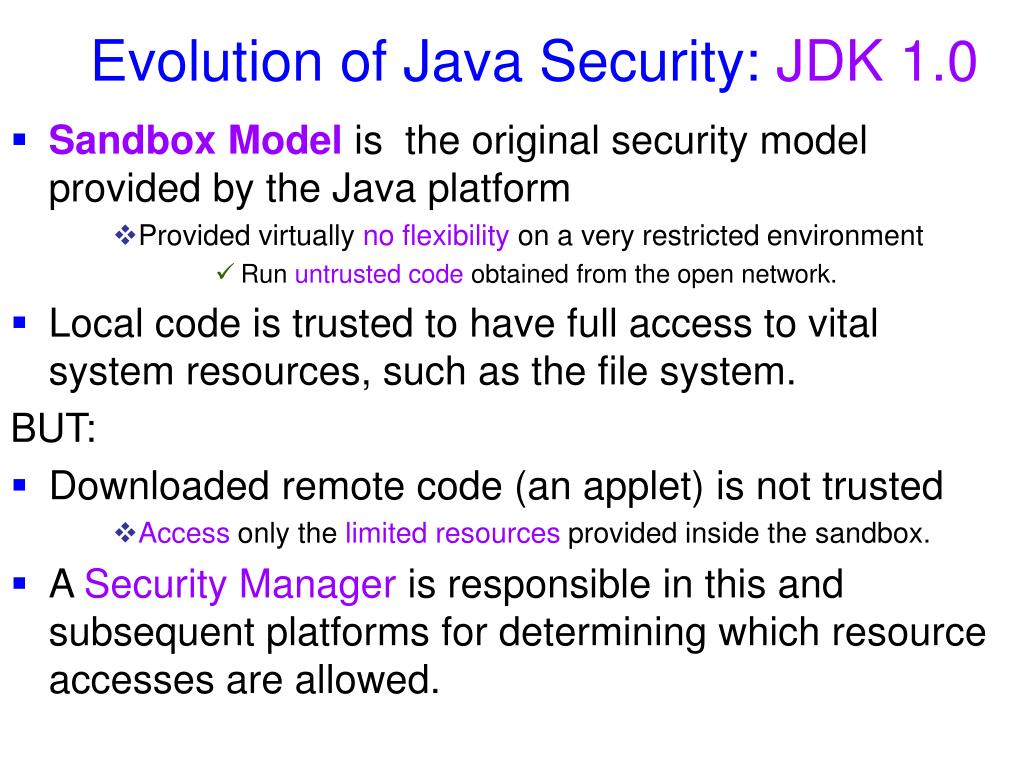
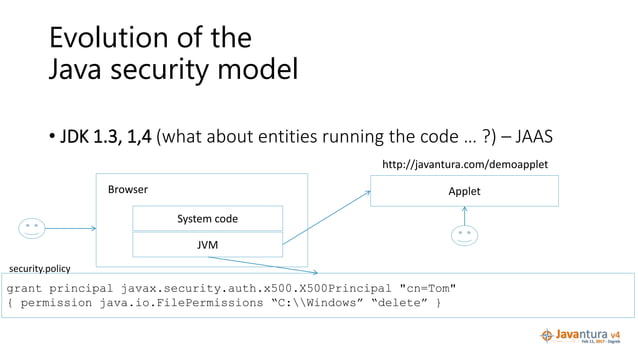
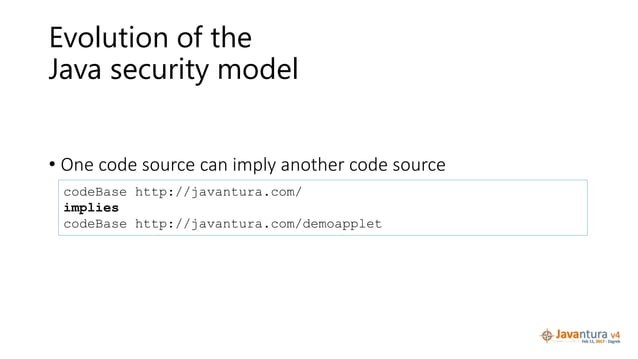
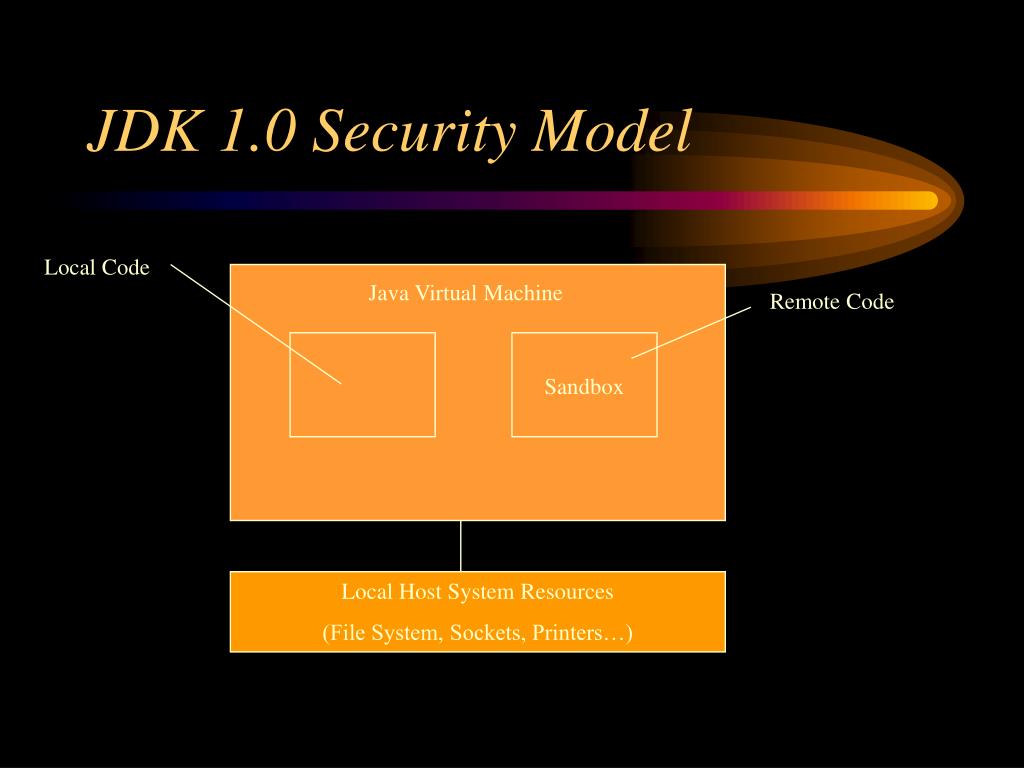
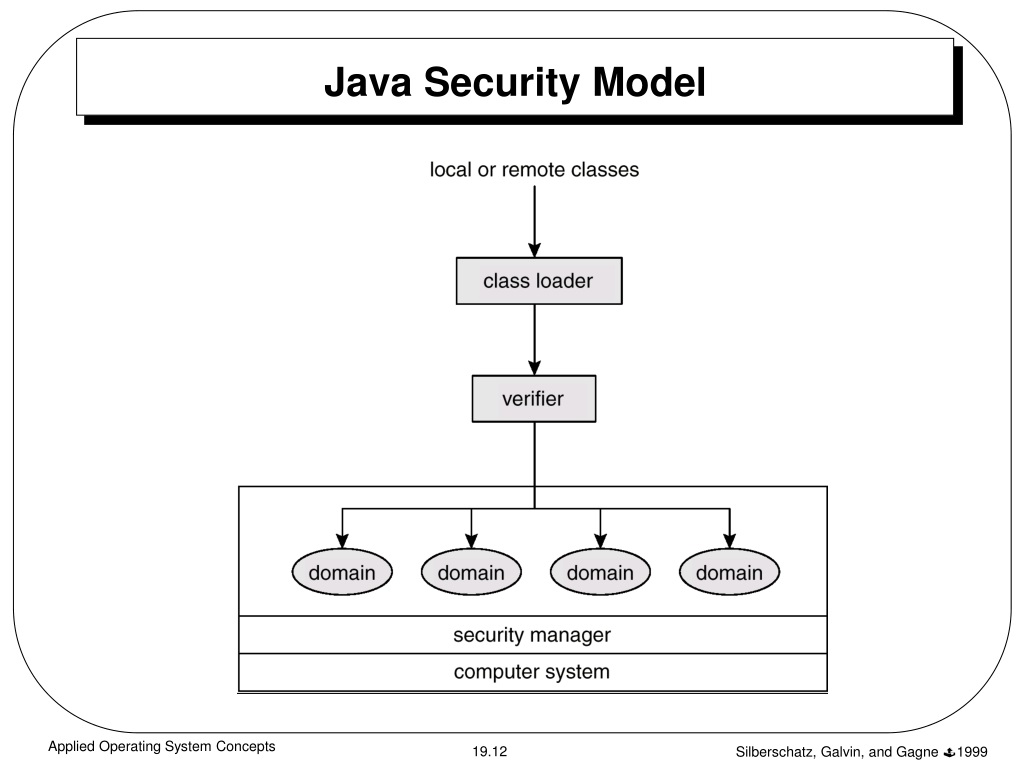
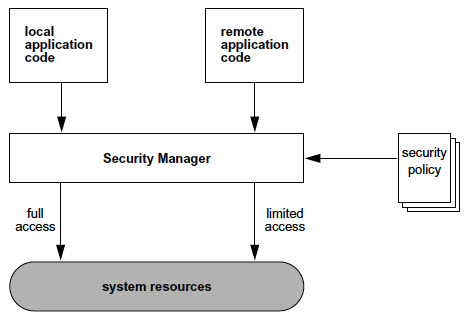
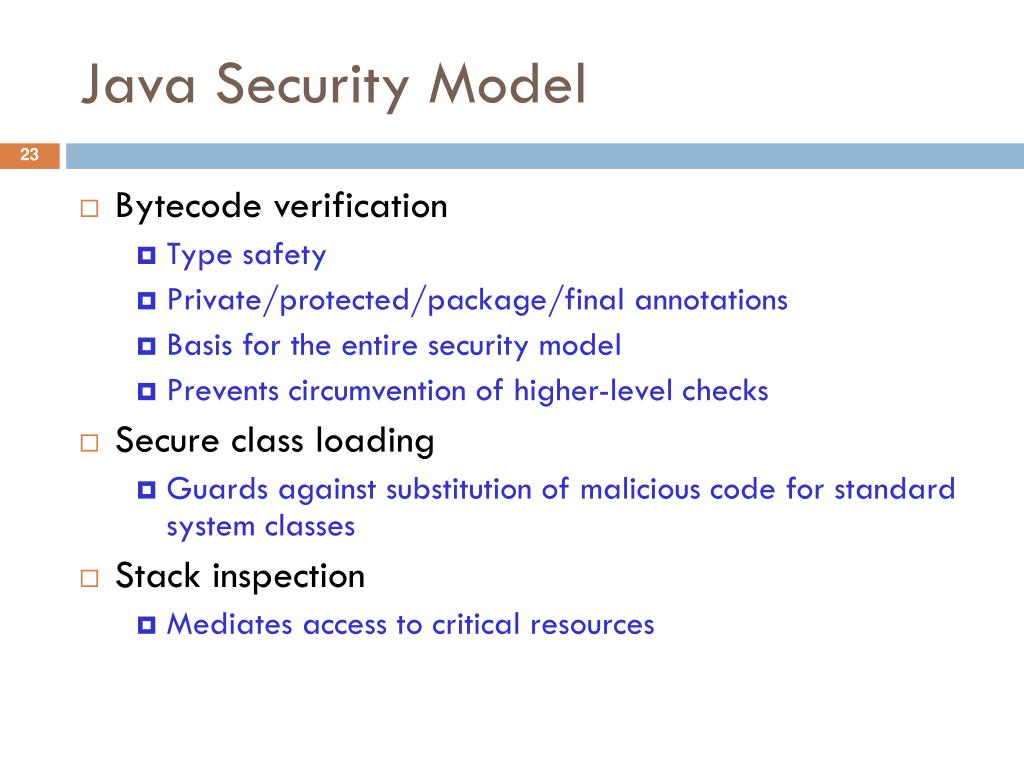
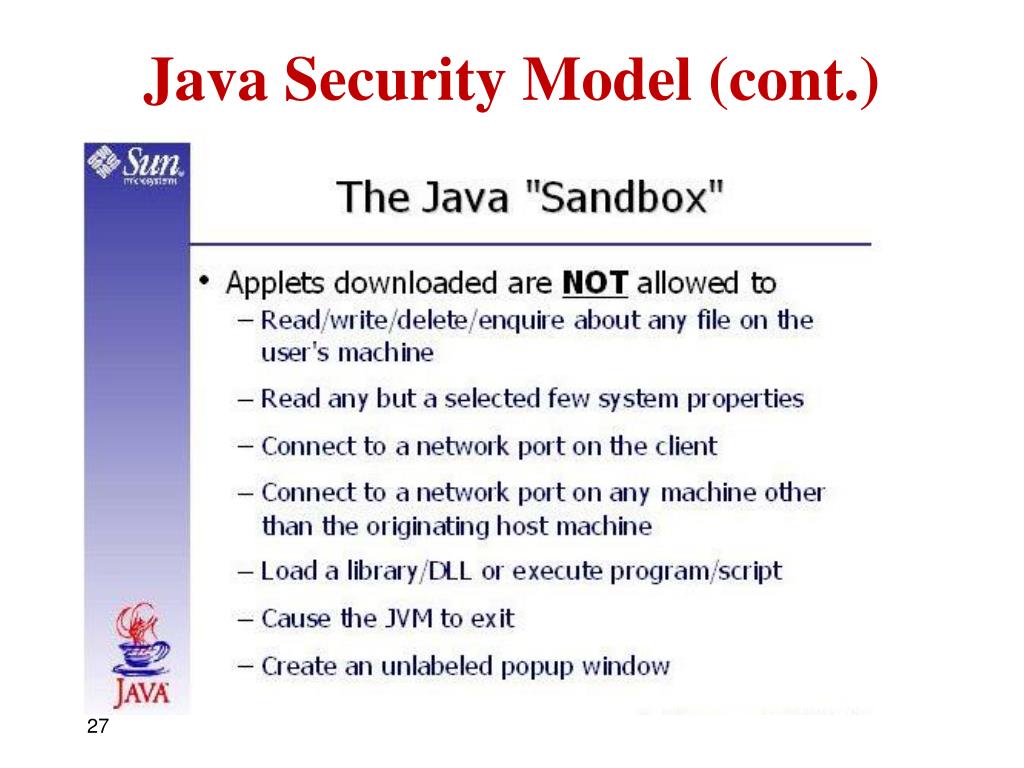
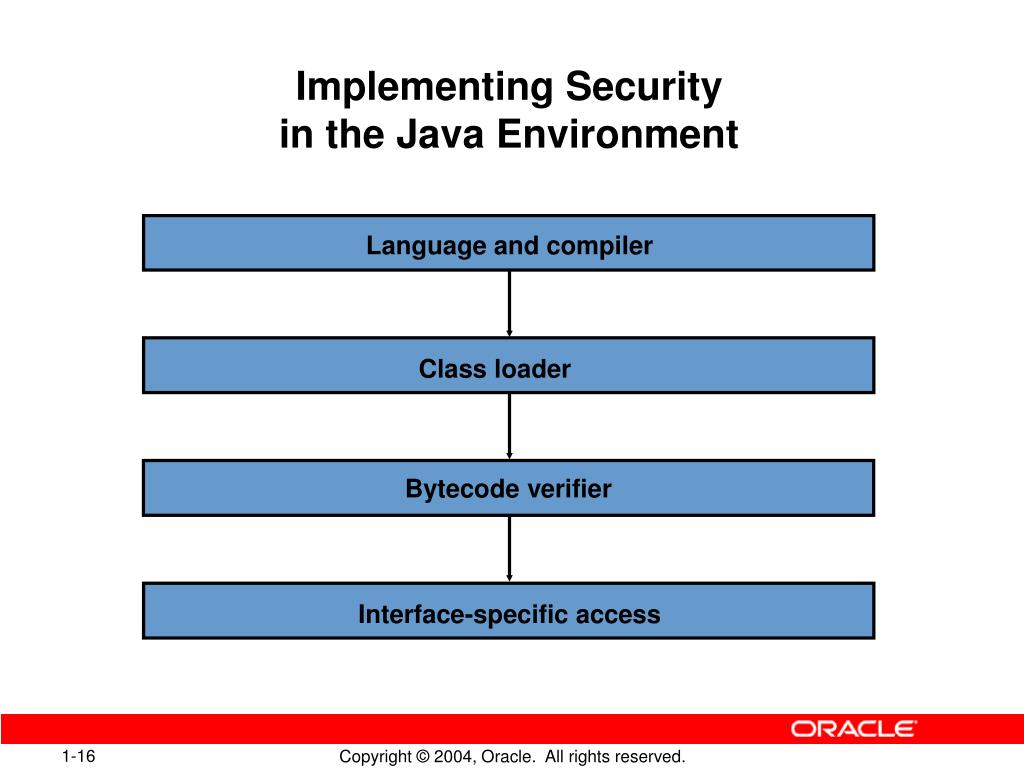
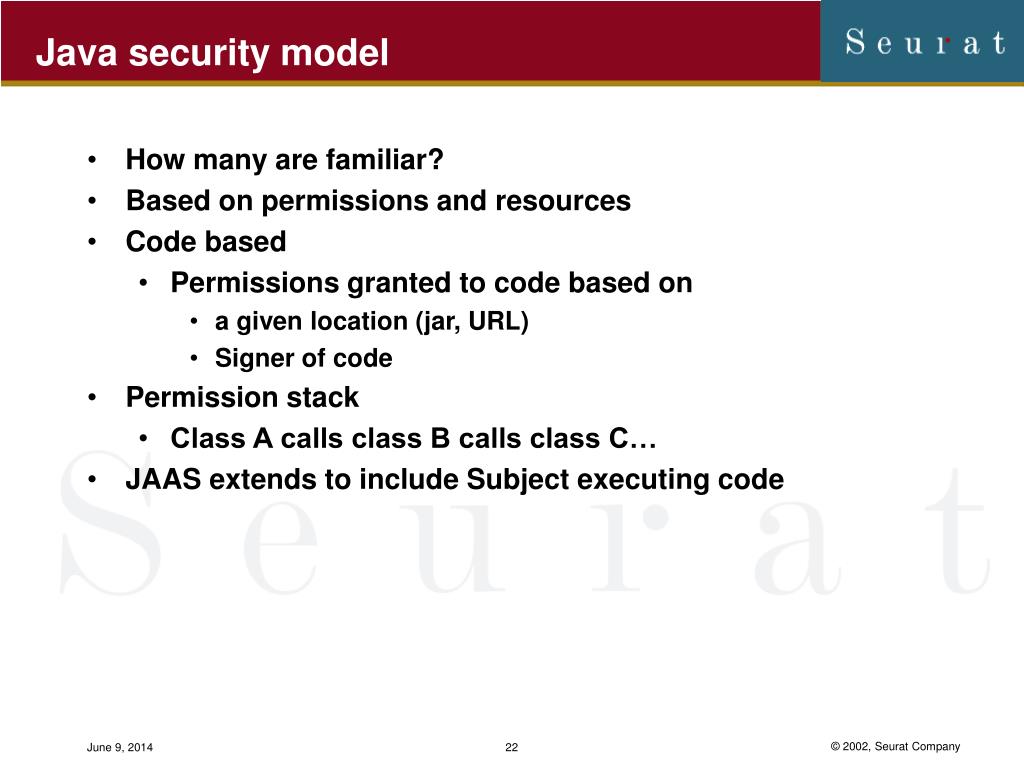
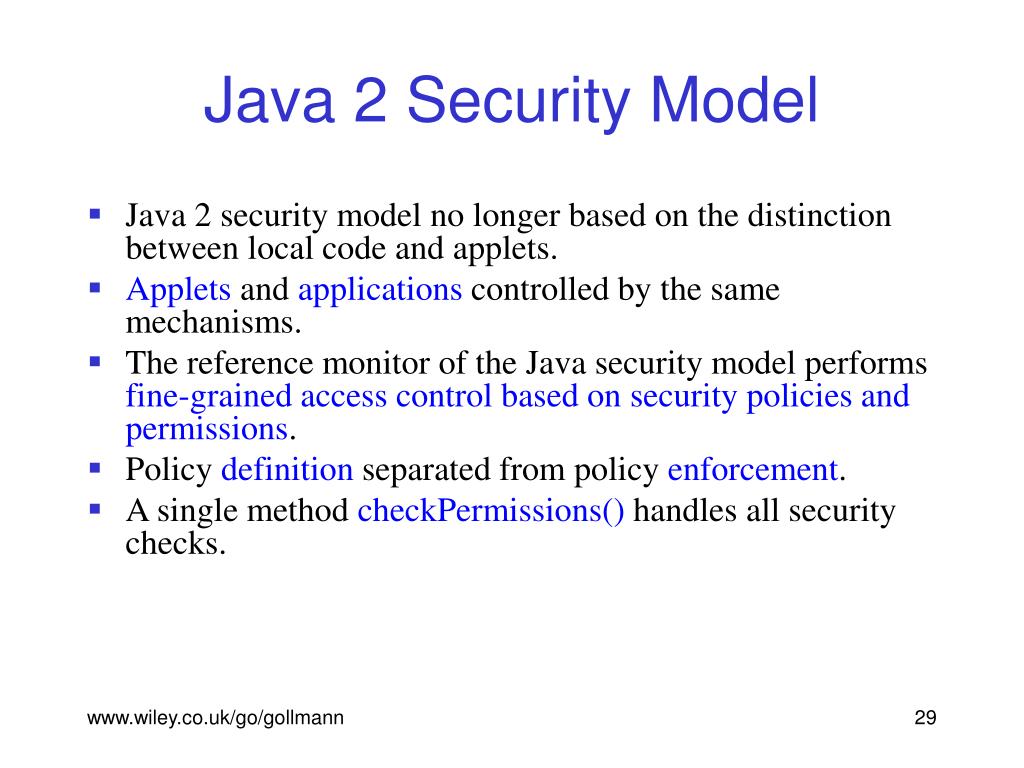
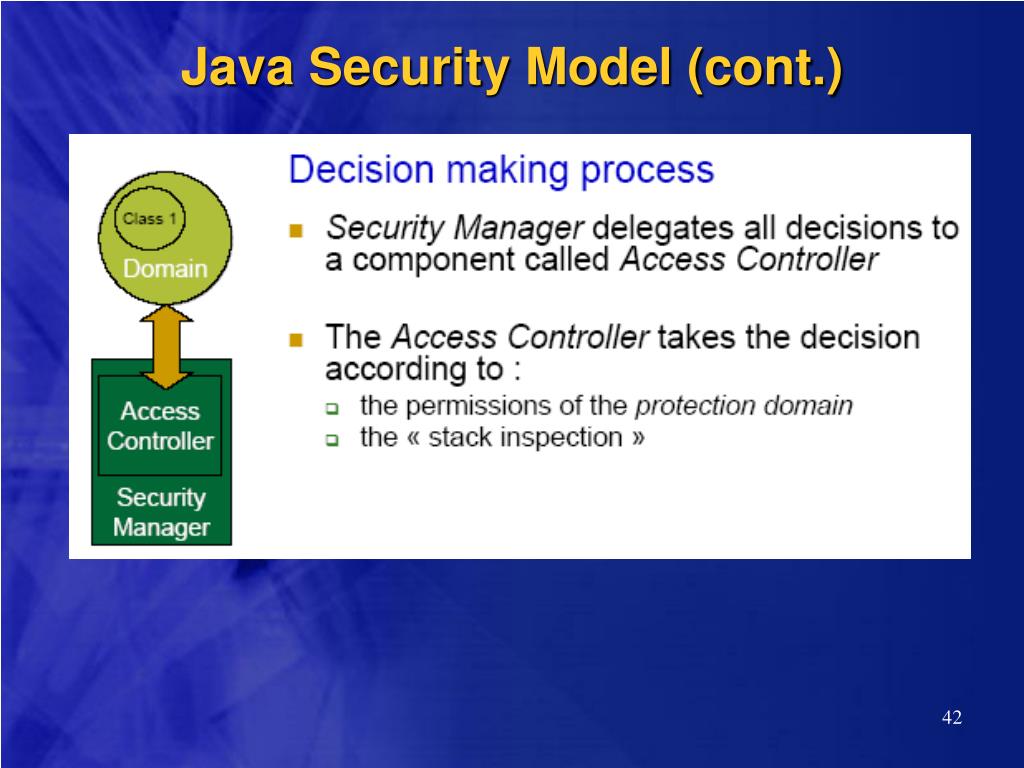
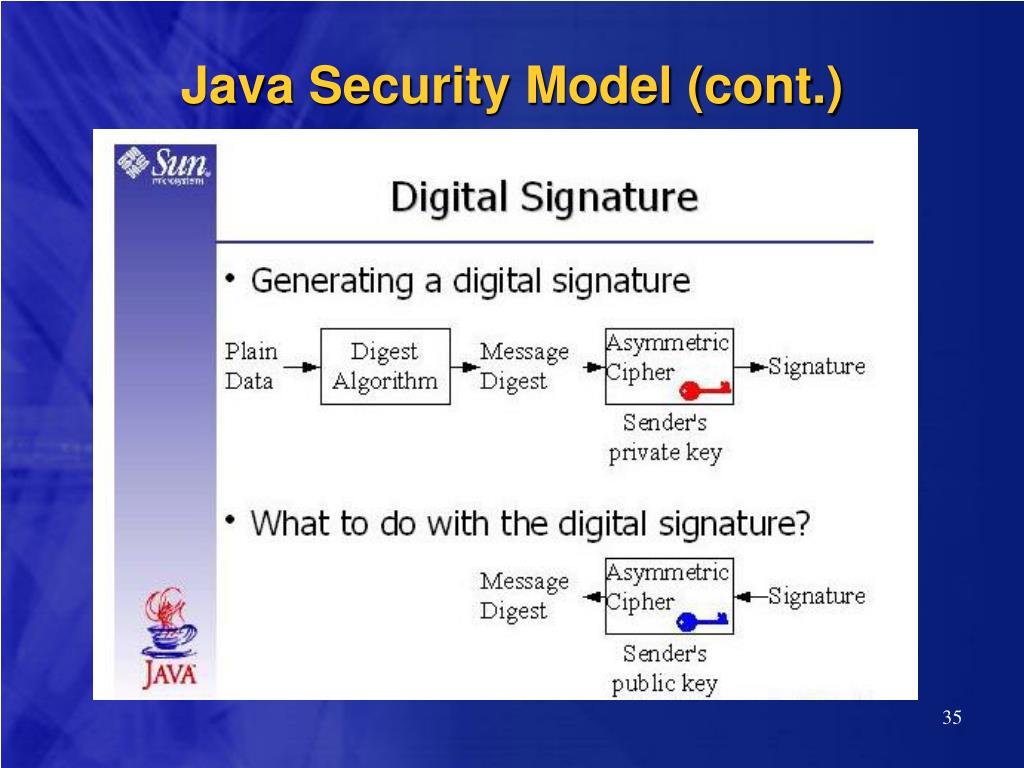
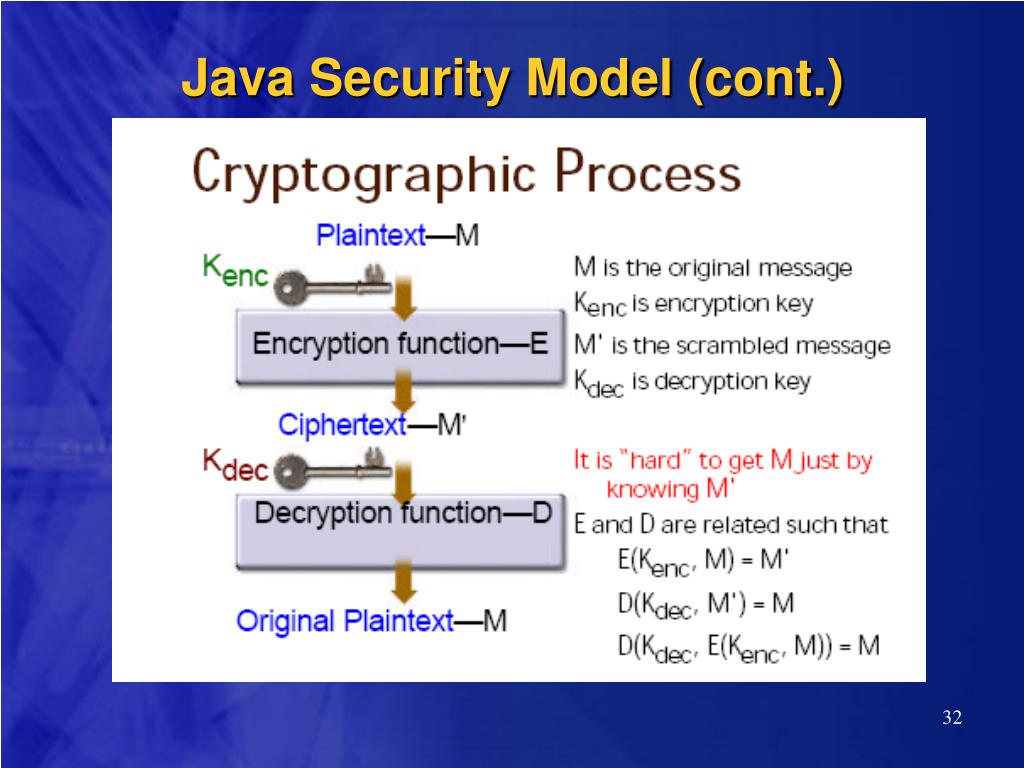
Java Security Model
Discover traditions with our cultural Java Security Model gallery of substantial collections of diverse images. celebrating diversity through photography, images, and pictures. designed to promote cultural understanding. Browse our premium Java Security Model gallery featuring professionally curated photographs. Suitable for various applications including web design, social media, personal projects, and digital content creation All Java Security Model images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Discover the perfect Java Security Model images to enhance your visual communication needs. Cost-effective licensing makes professional Java Security Model photography accessible to all budgets. Reliable customer support ensures smooth experience throughout the Java Security Model selection process. The Java Security Model collection represents years of careful curation and professional standards. Professional licensing options accommodate both commercial and educational usage requirements. Instant download capabilities enable immediate access to chosen Java Security Model images. Diverse style options within the Java Security Model collection suit various aesthetic preferences. The Java Security Model archive serves professionals, educators, and creatives across diverse industries. Comprehensive tagging systems facilitate quick discovery of relevant Java Security Model content. Whether for commercial projects or personal use, our Java Security Model collection delivers consistent excellence.
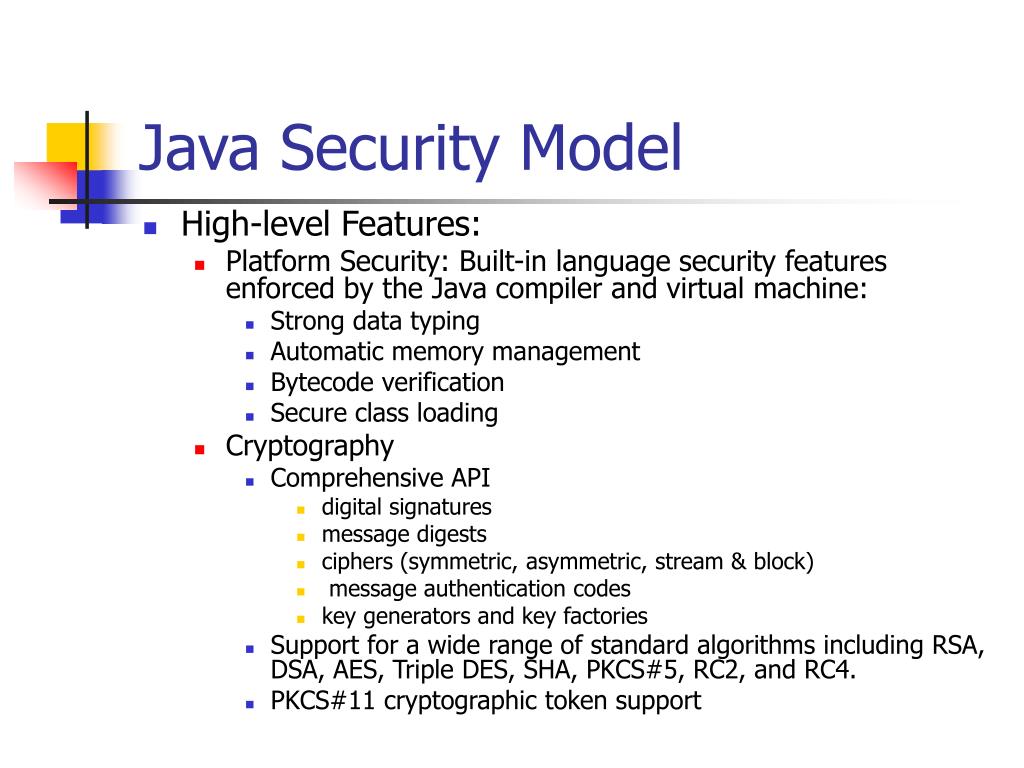
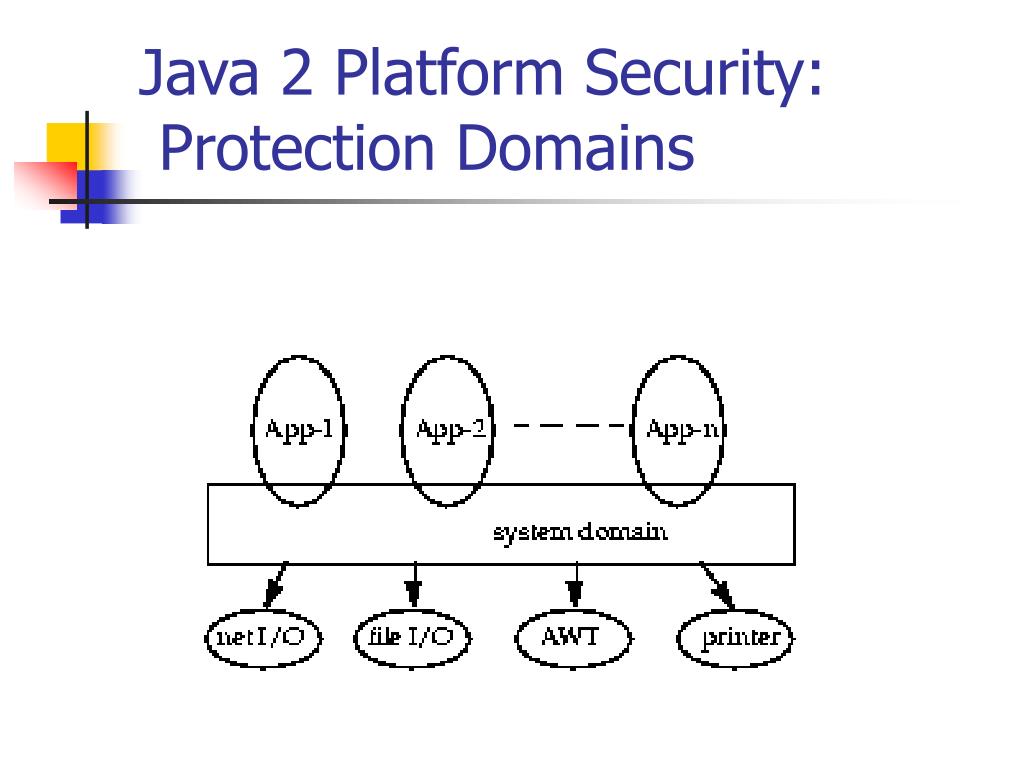
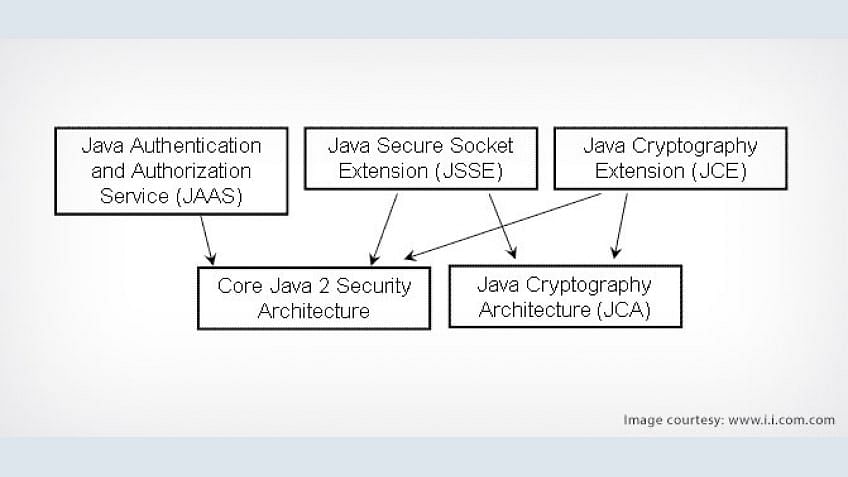
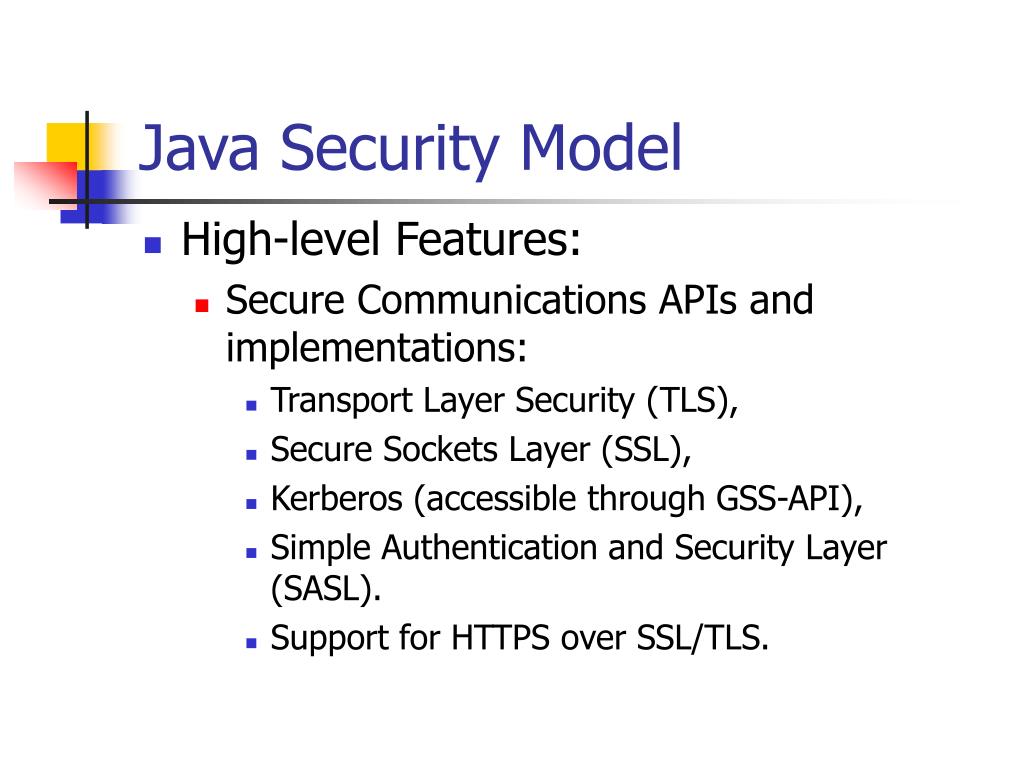
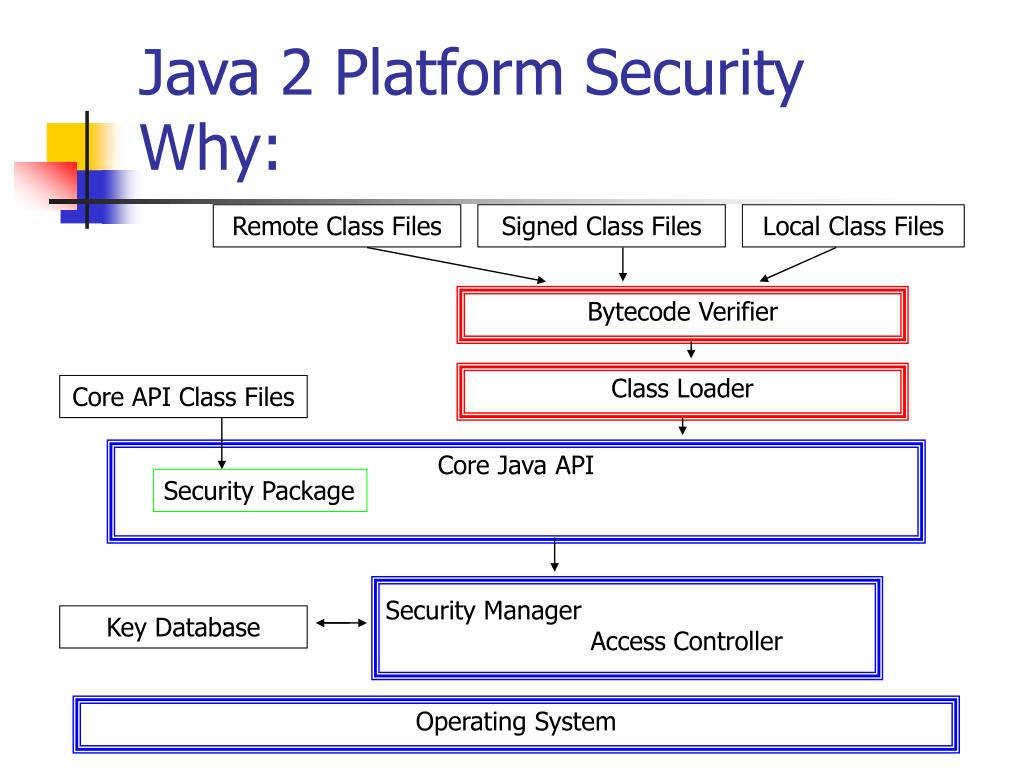


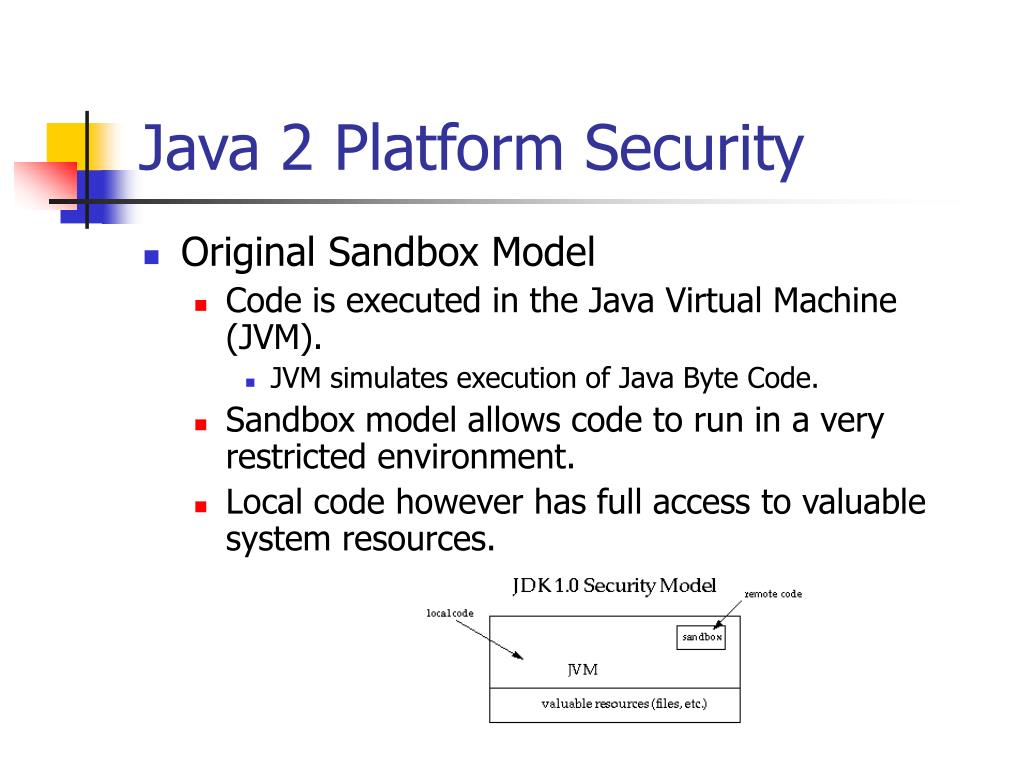
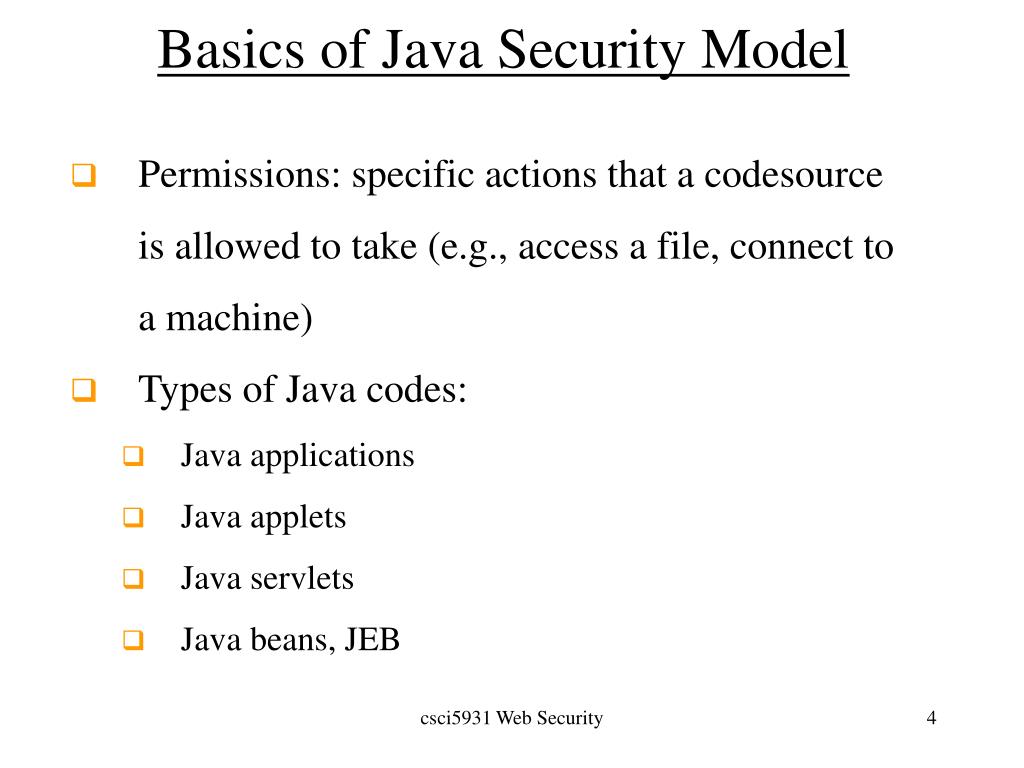




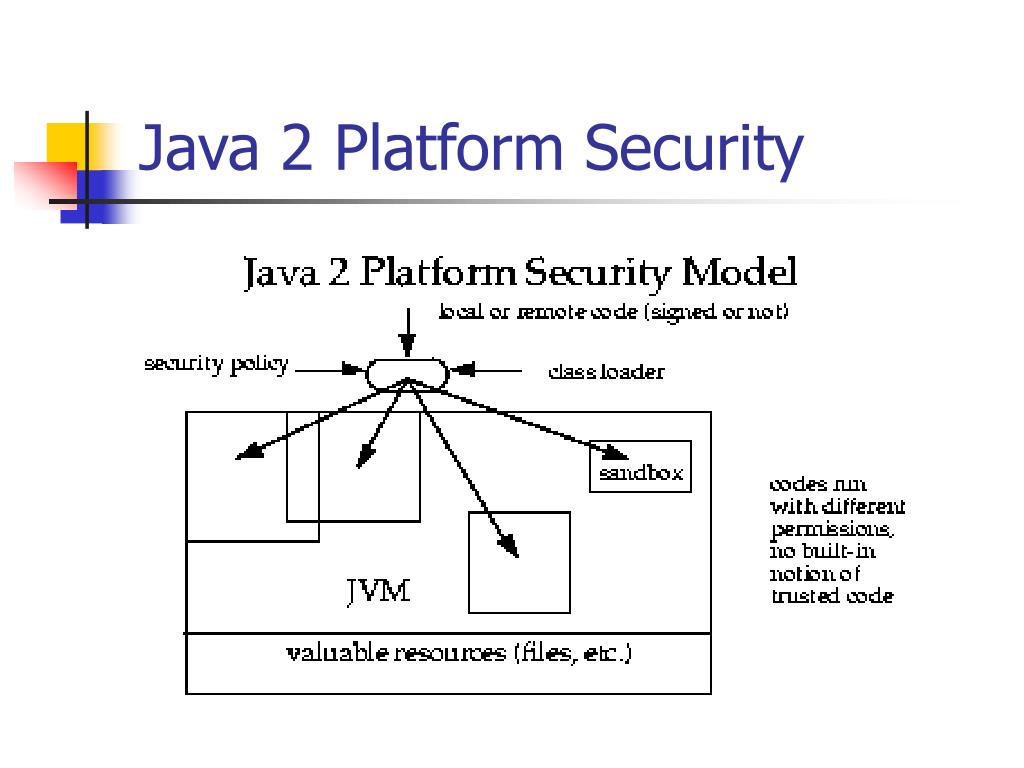







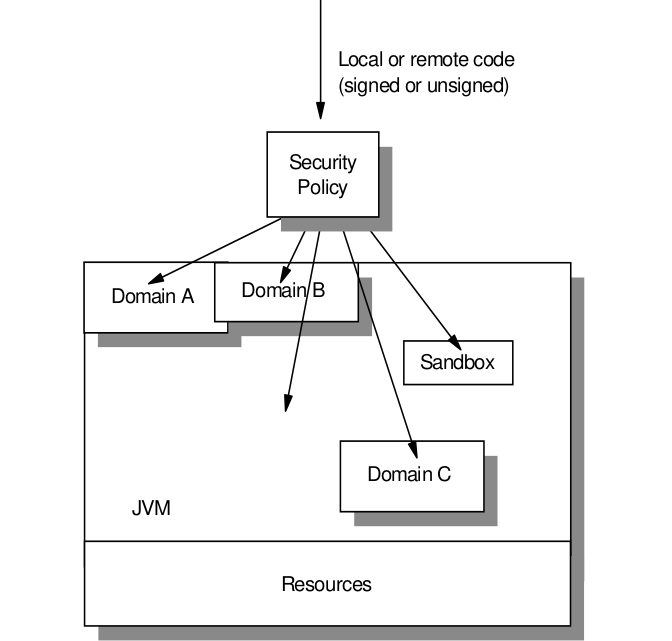





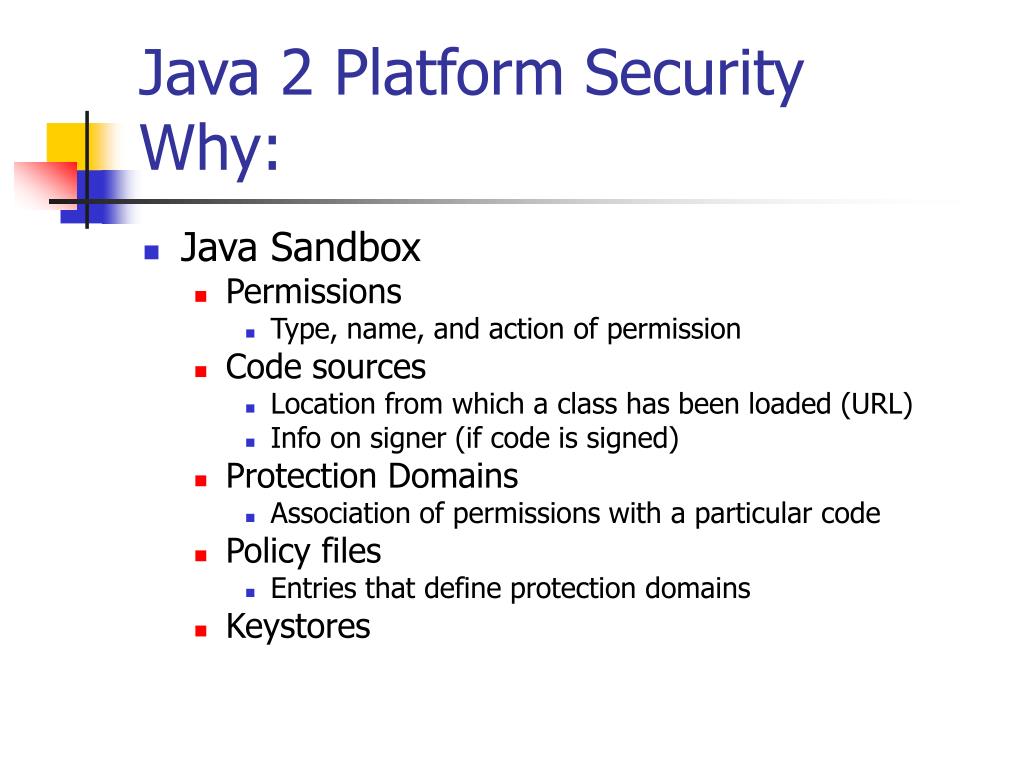






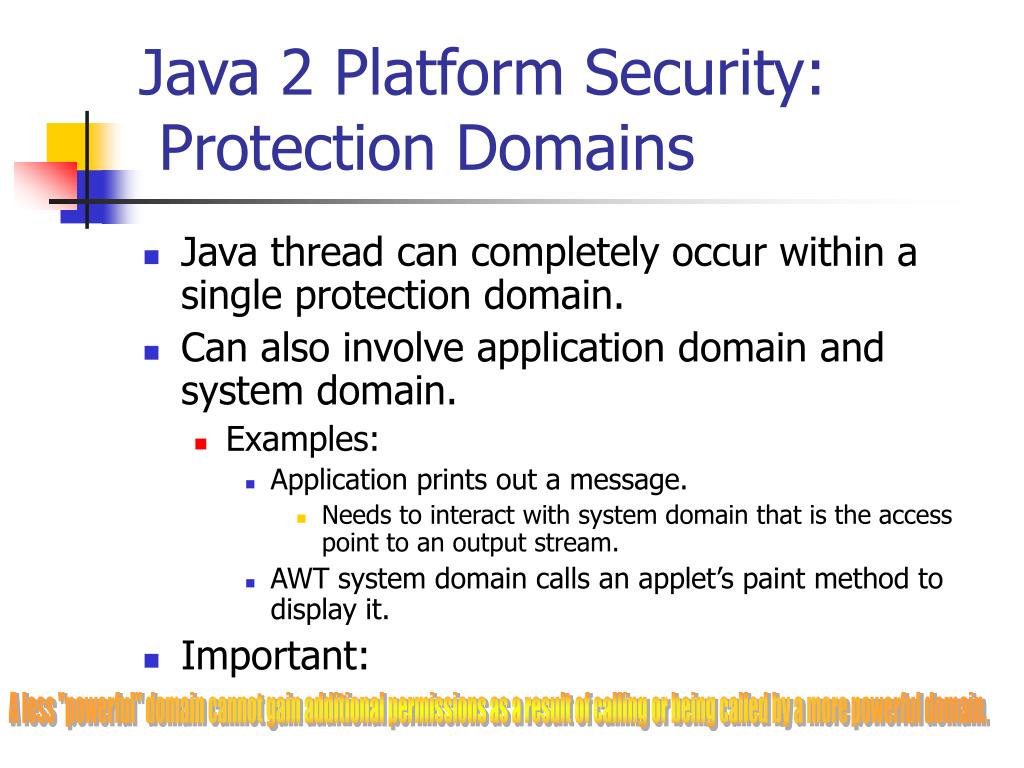

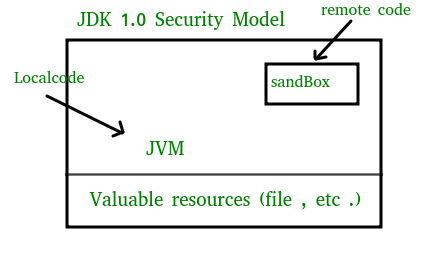
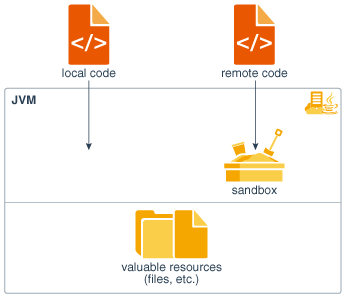

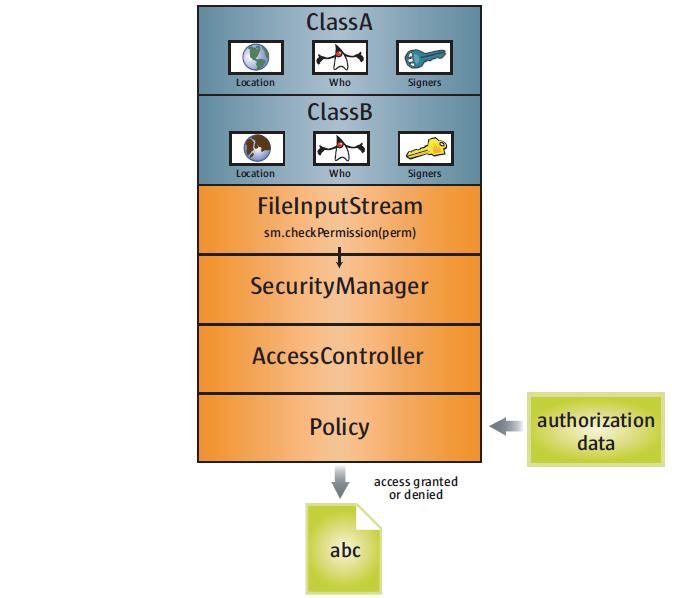

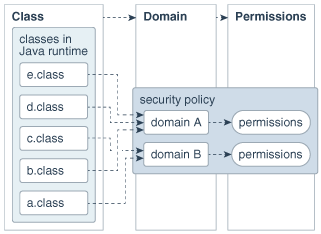

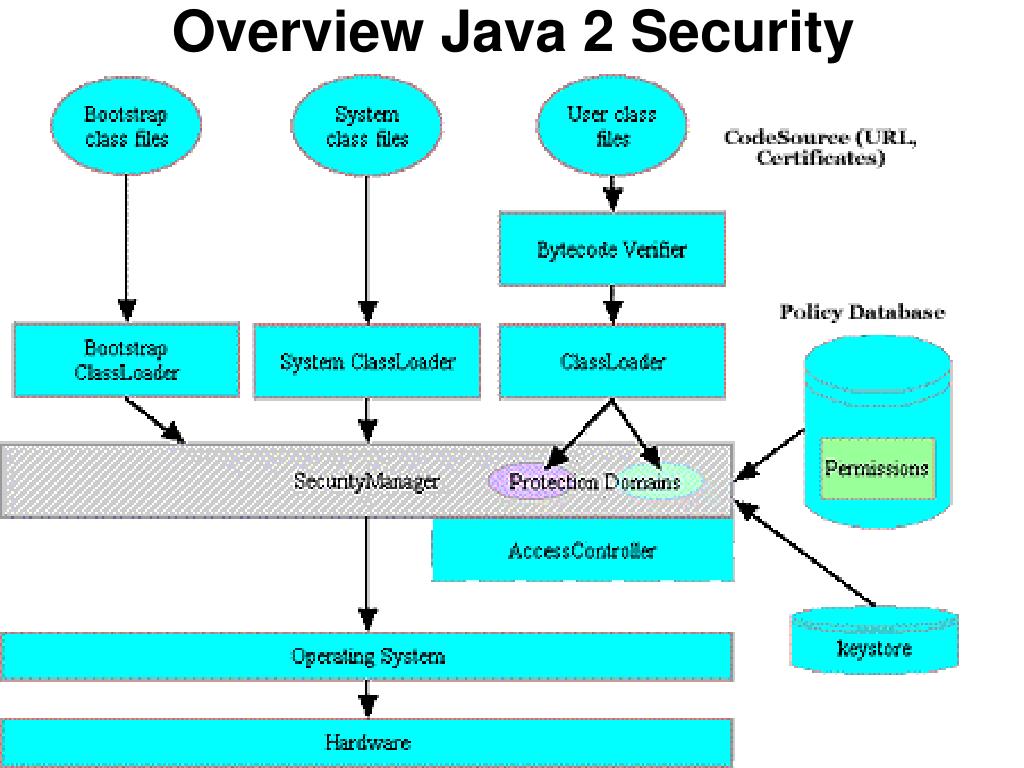
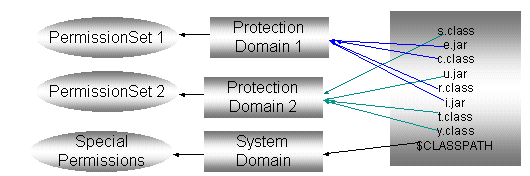
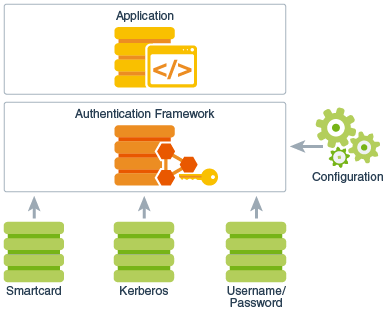
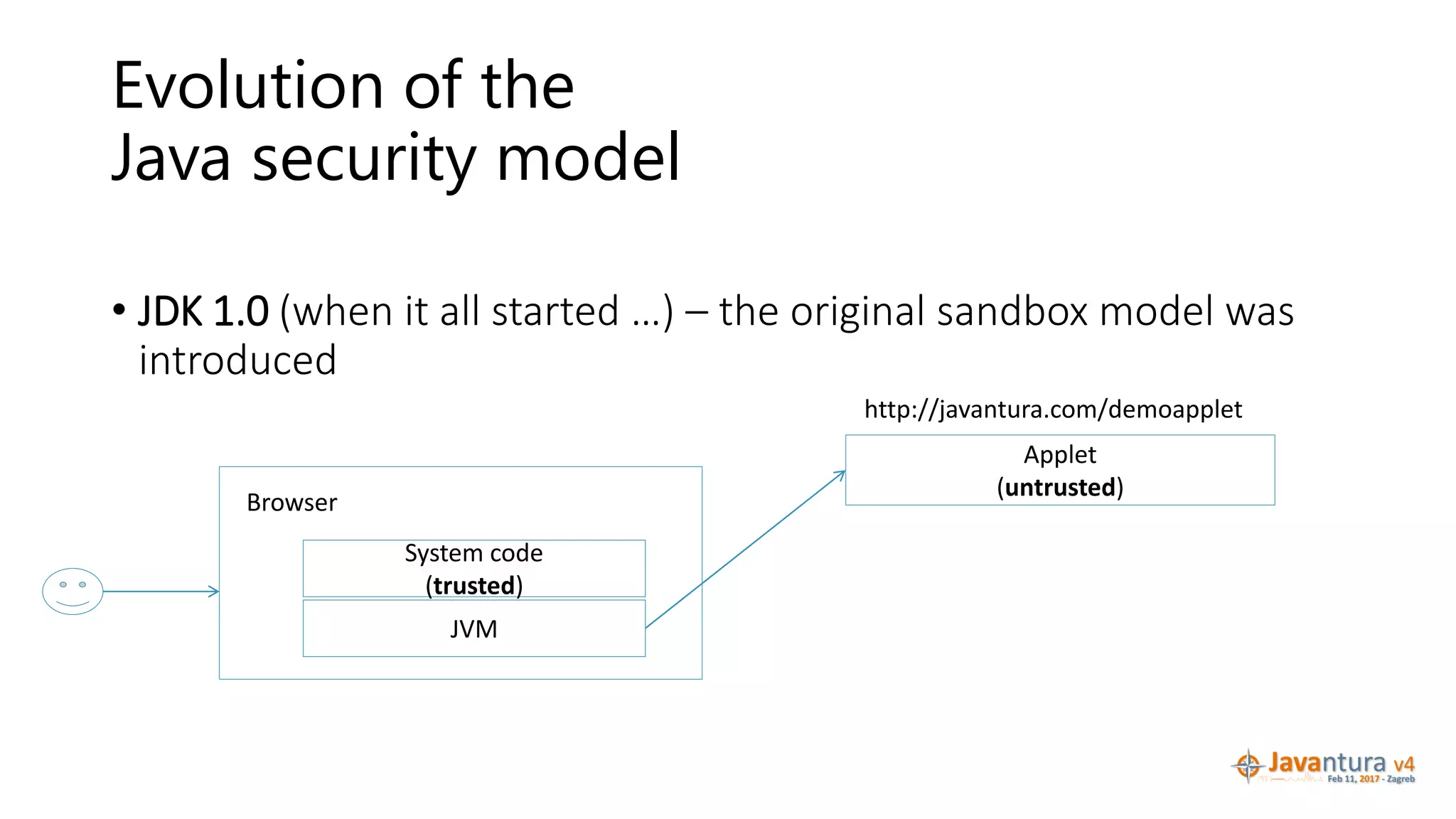
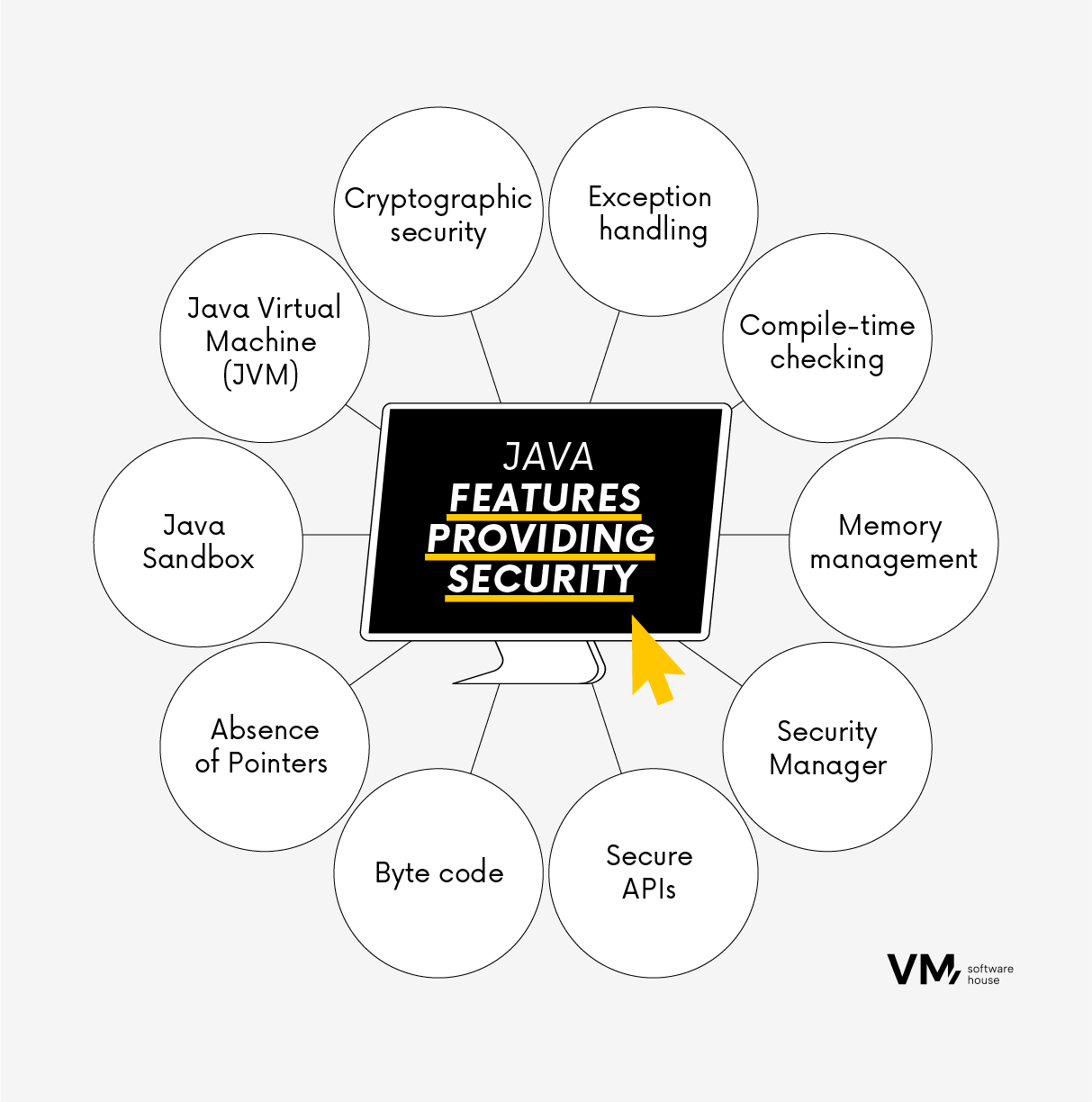

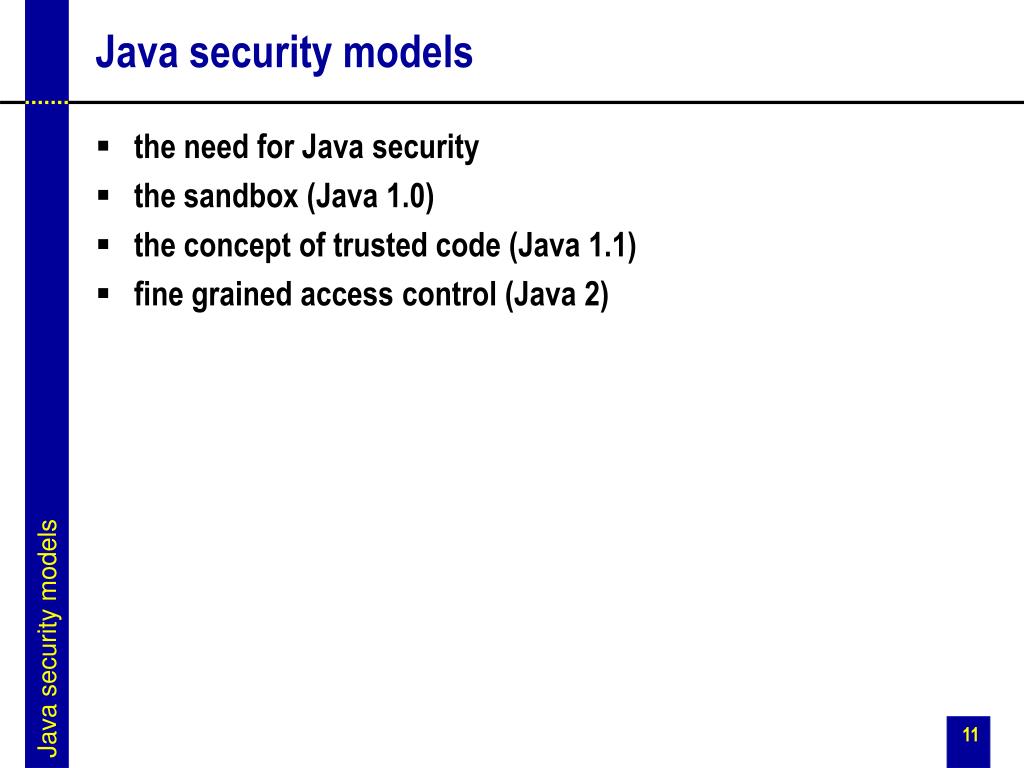
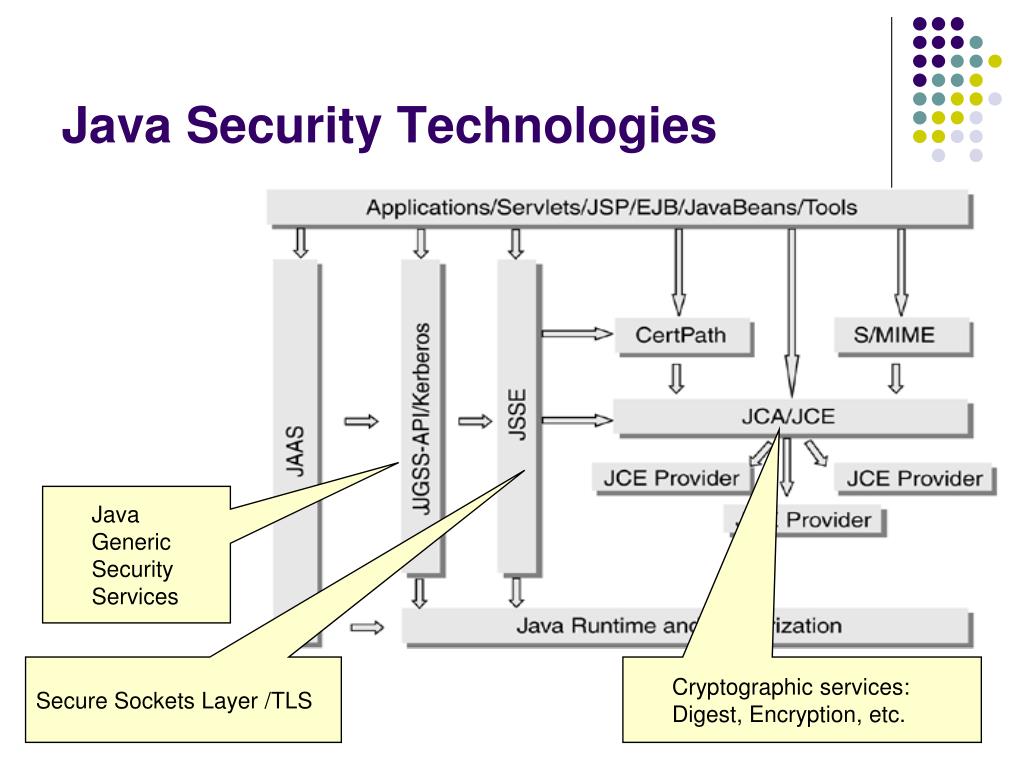
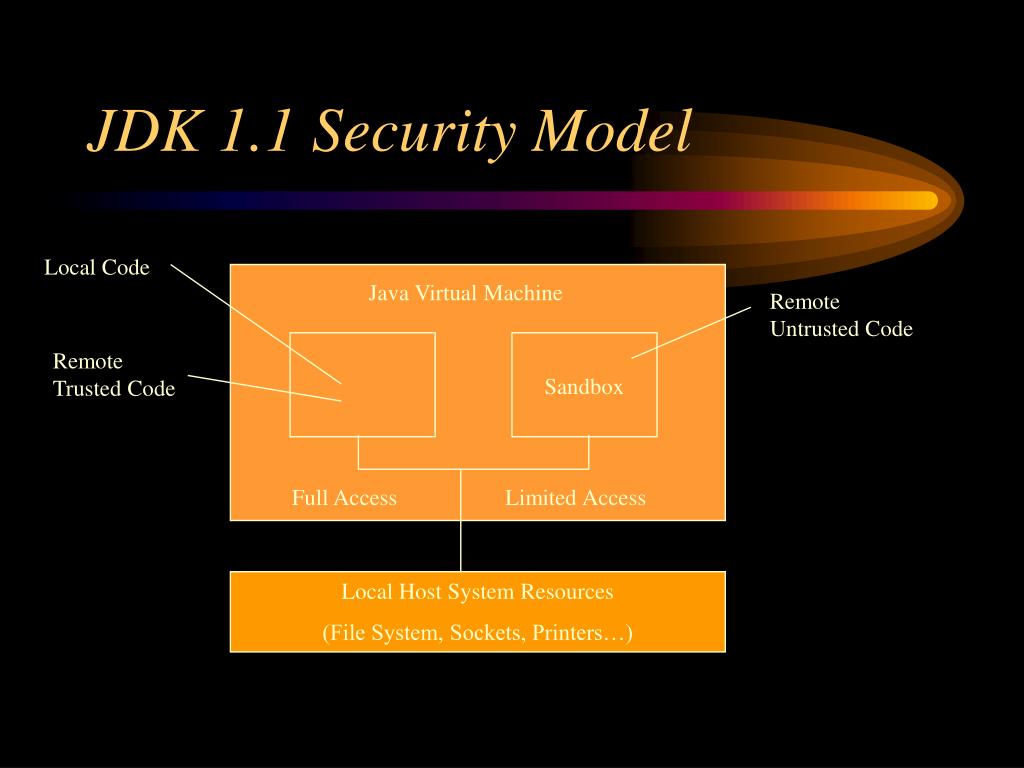


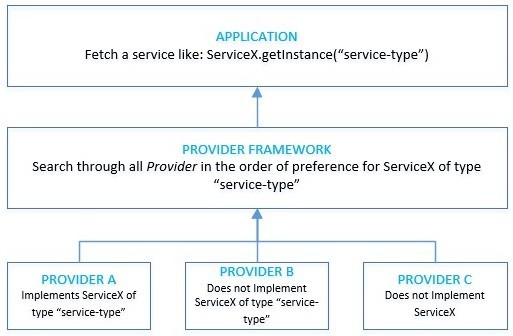
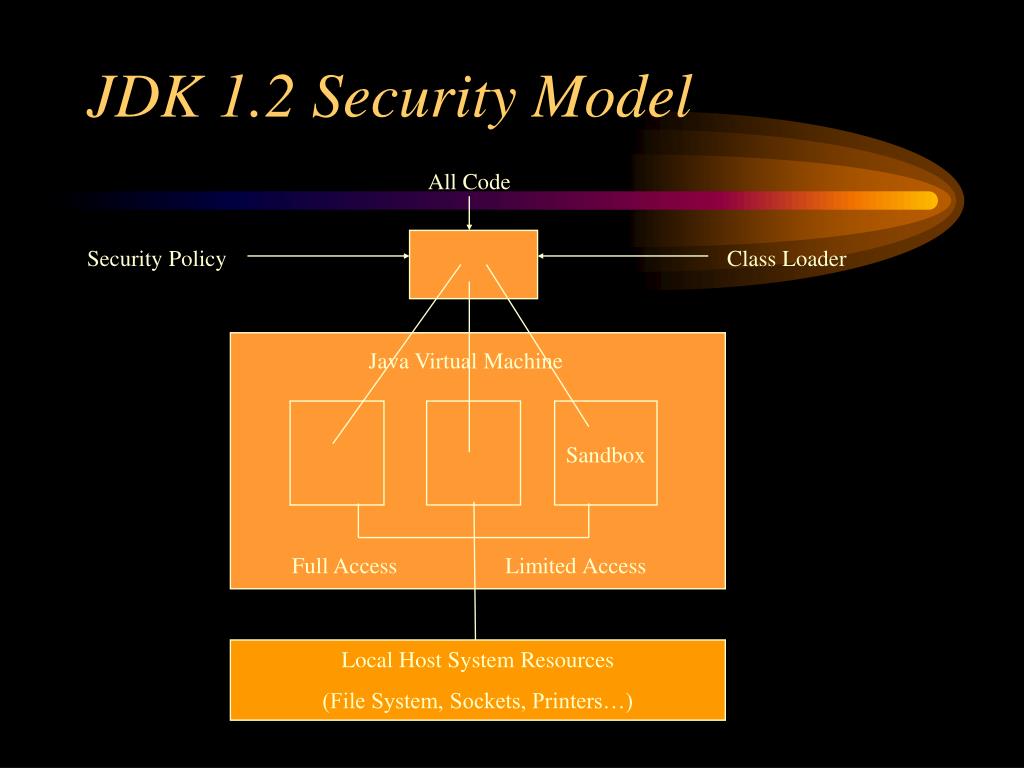
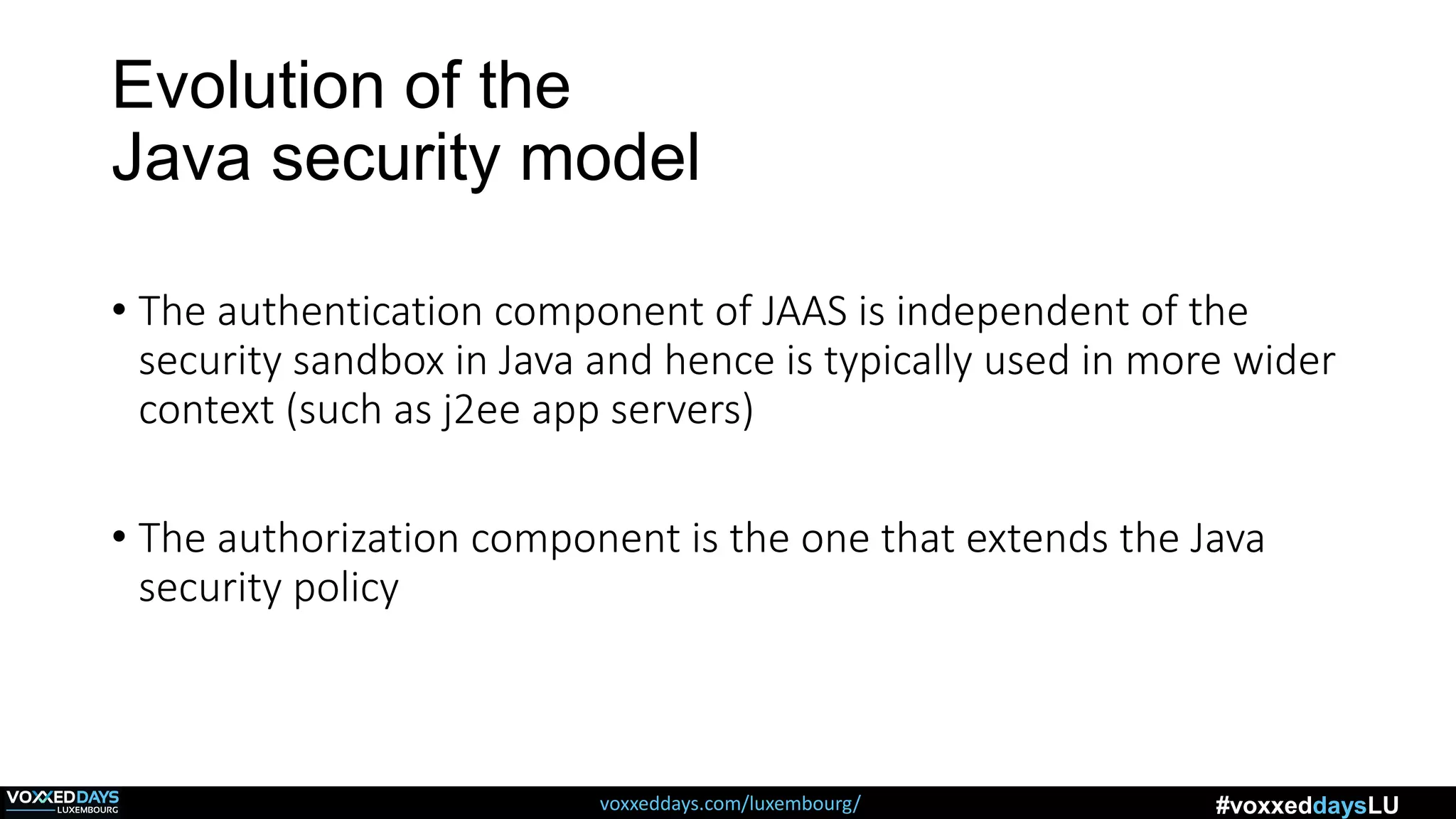

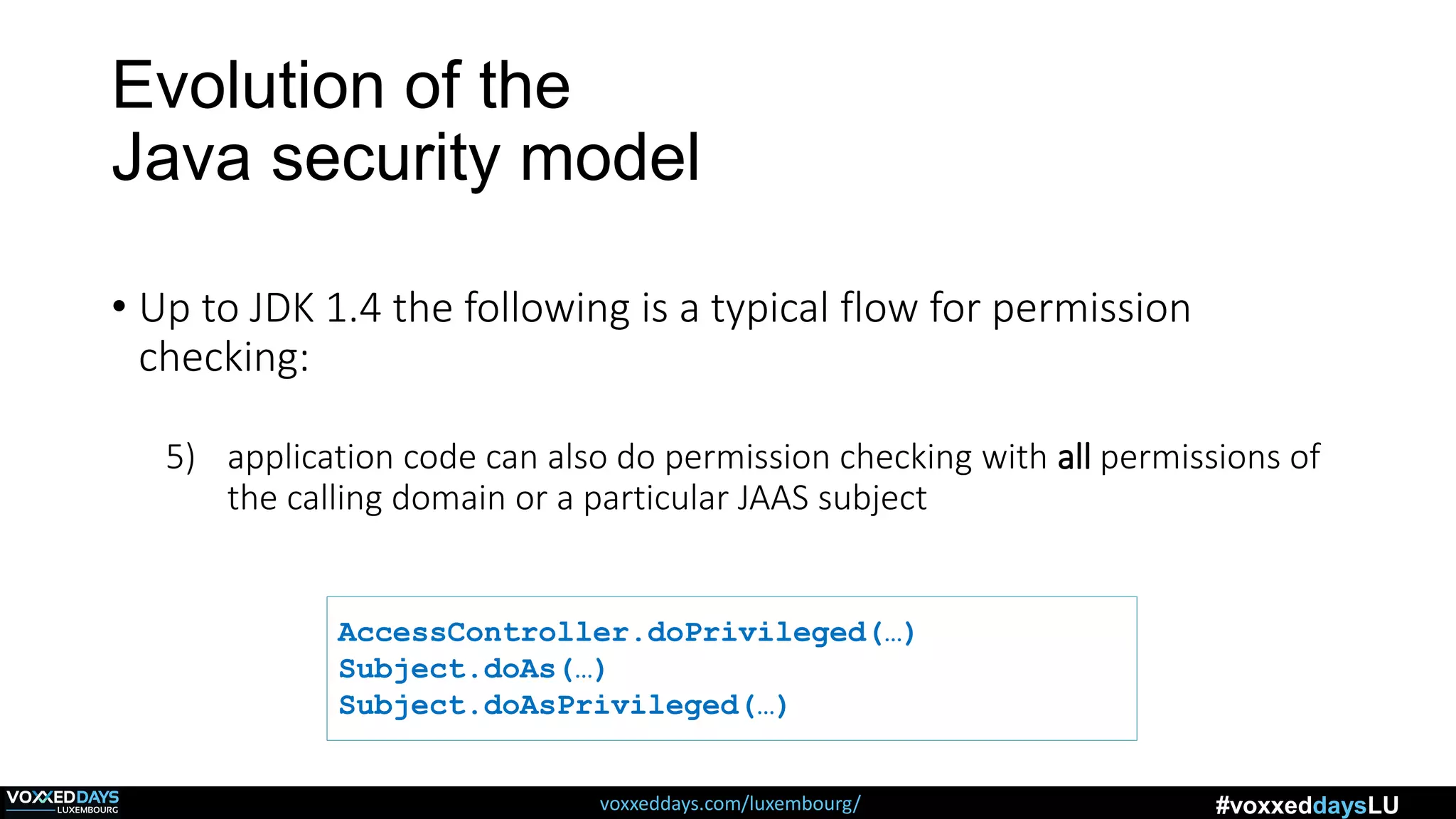

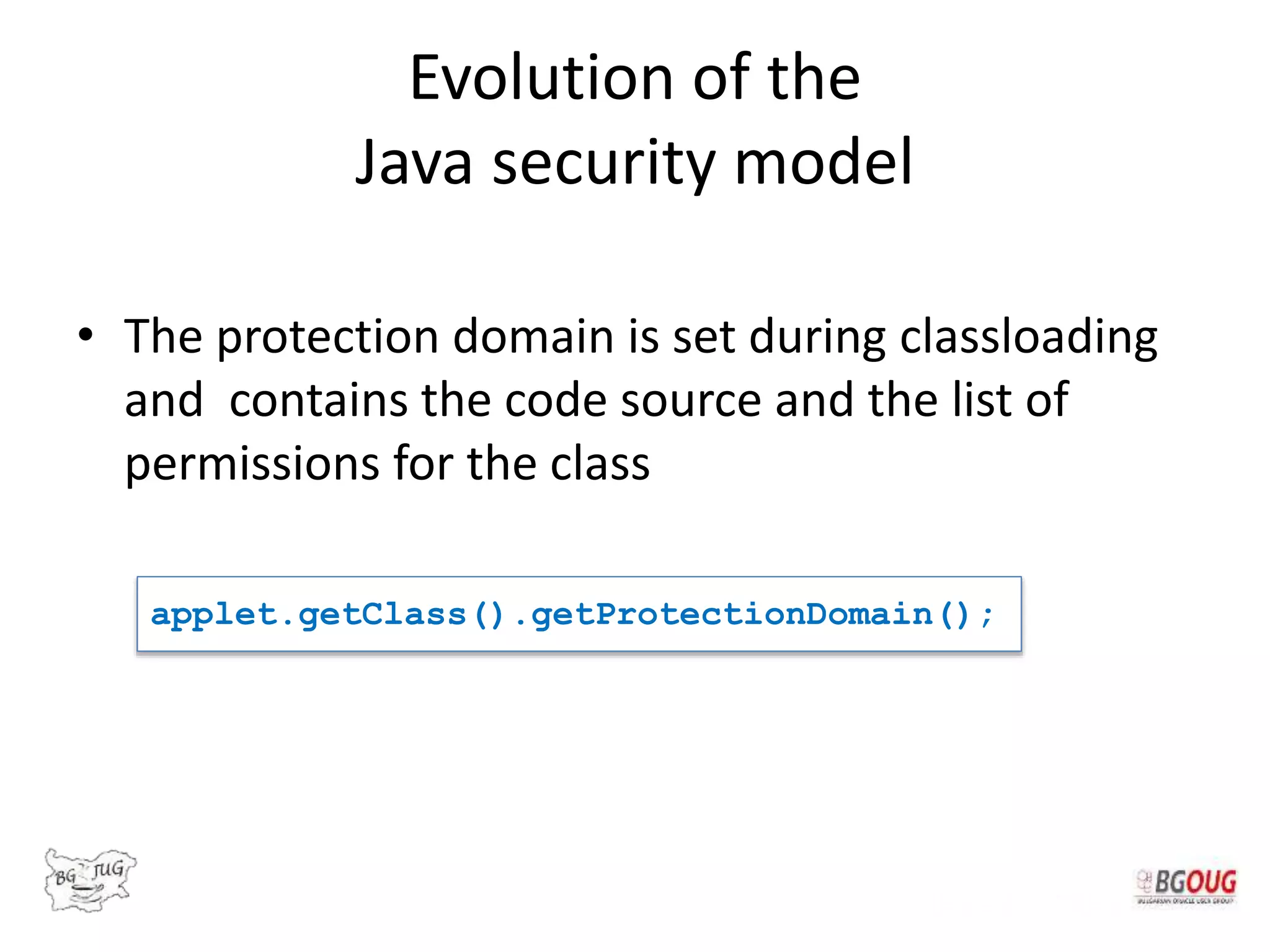

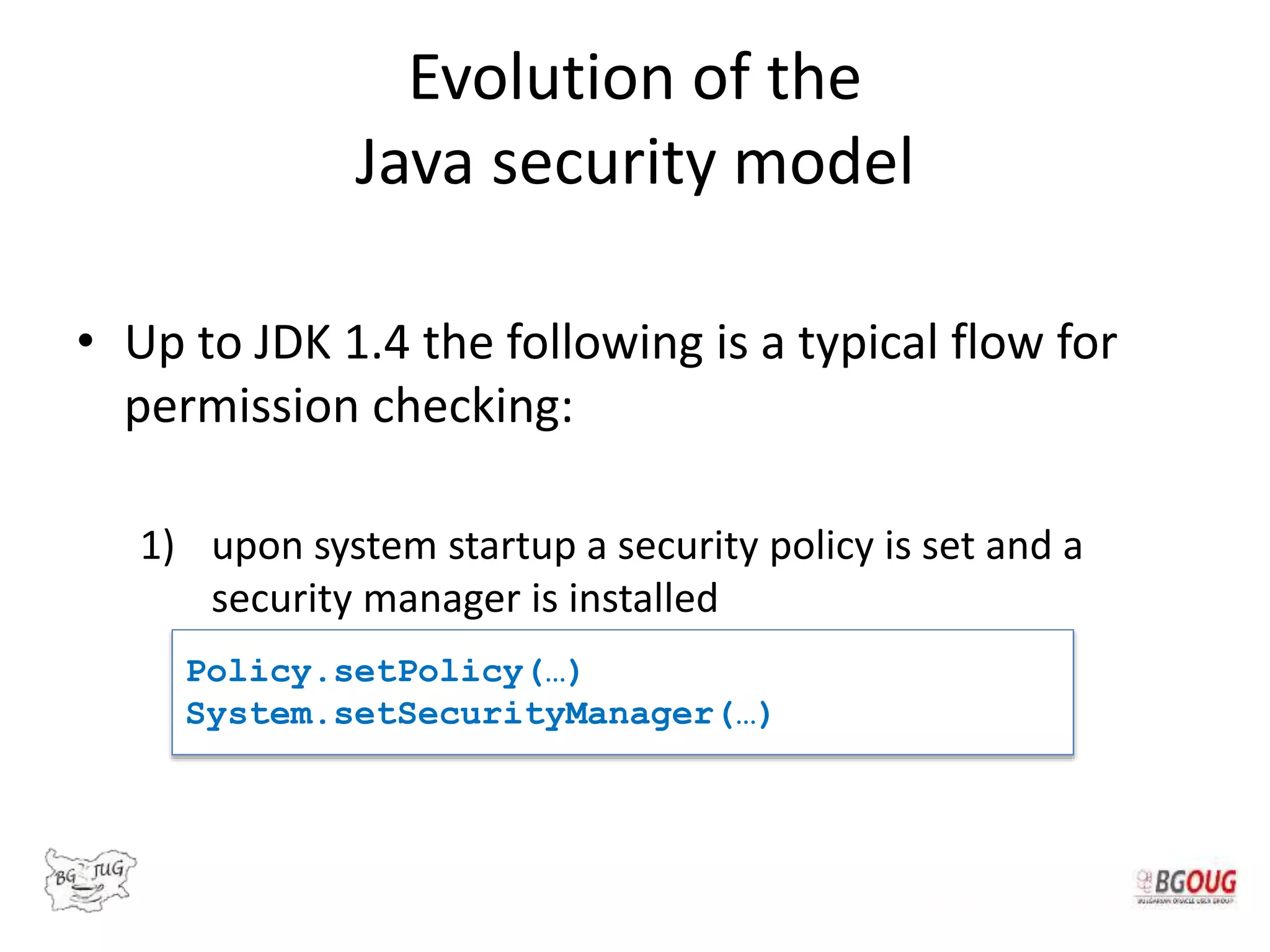




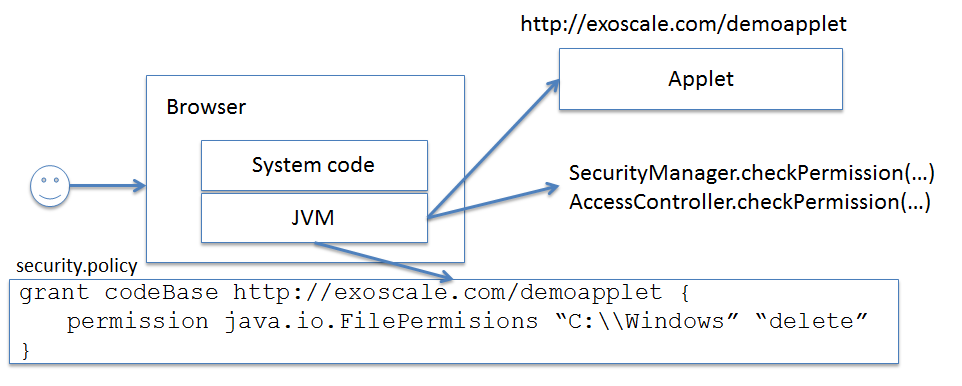

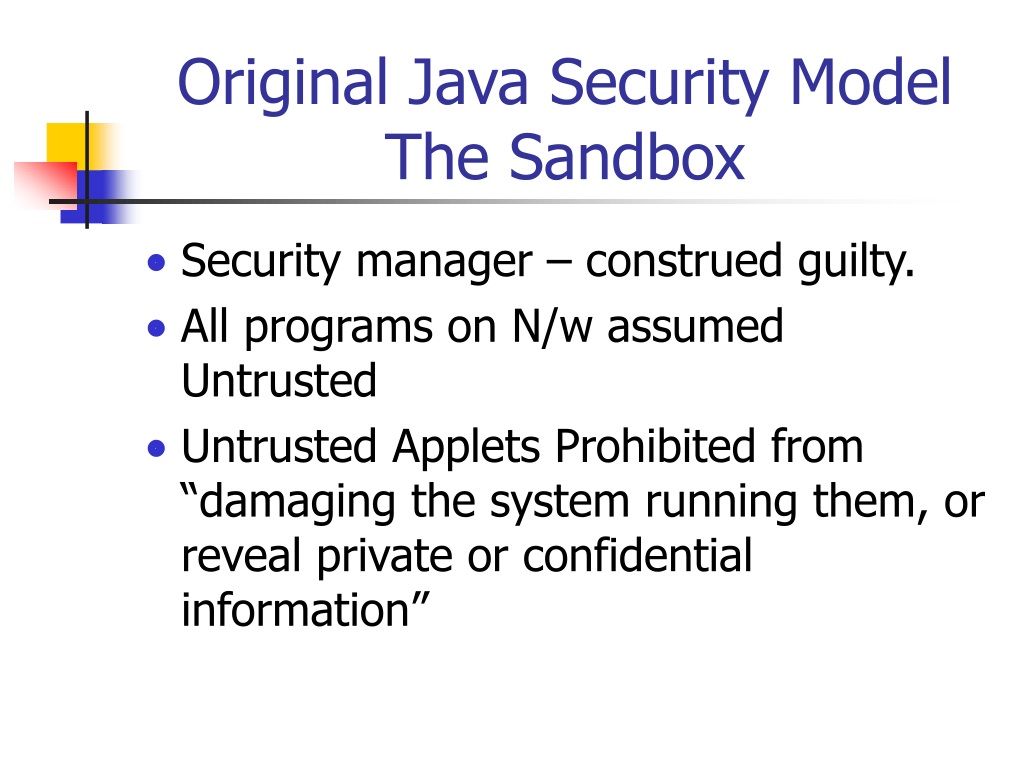
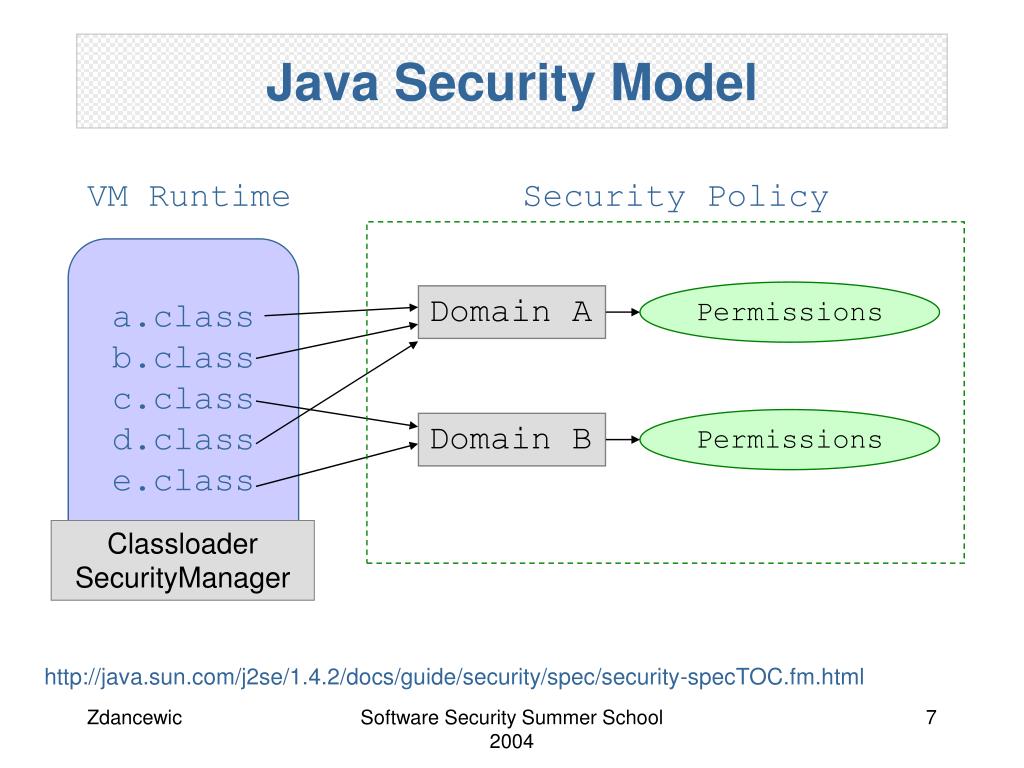
![Different Classes of Security (Ch. 2, Sec. 9) [Securing Java]](https://www.securingjava.com/images/Fig02.08.gif)

![Safety of Implementation - Learning Java, 4th Edition [Book]](https://www.oreilly.com/api/v2/epubs/9781449372477/files/httpatomoreillycomsourceoreillyimages1707598.png)



![[Chapter 1] 1.5 Safety of Implementation](https://web.deu.edu.tr/doc/oreily/java/exp/figs/je0103.gif)

