How Api Security Controls Fit Into A Cyber Architecture
Document the past through hundreds of historically-significant How Api Security Controls Fit Into A Cyber Architecture photographs. heritage-preserving showcasing photography, images, and pictures. designed to preserve historical significance. The How Api Security Controls Fit Into A Cyber Architecture collection maintains consistent quality standards across all images. Suitable for various applications including web design, social media, personal projects, and digital content creation All How Api Security Controls Fit Into A Cyber Architecture images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Our How Api Security Controls Fit Into A Cyber Architecture gallery offers diverse visual resources to bring your ideas to life. The How Api Security Controls Fit Into A Cyber Architecture collection represents years of careful curation and professional standards. Multiple resolution options ensure optimal performance across different platforms and applications. Advanced search capabilities make finding the perfect How Api Security Controls Fit Into A Cyber Architecture image effortless and efficient. Instant download capabilities enable immediate access to chosen How Api Security Controls Fit Into A Cyber Architecture images. The How Api Security Controls Fit Into A Cyber Architecture archive serves professionals, educators, and creatives across diverse industries.
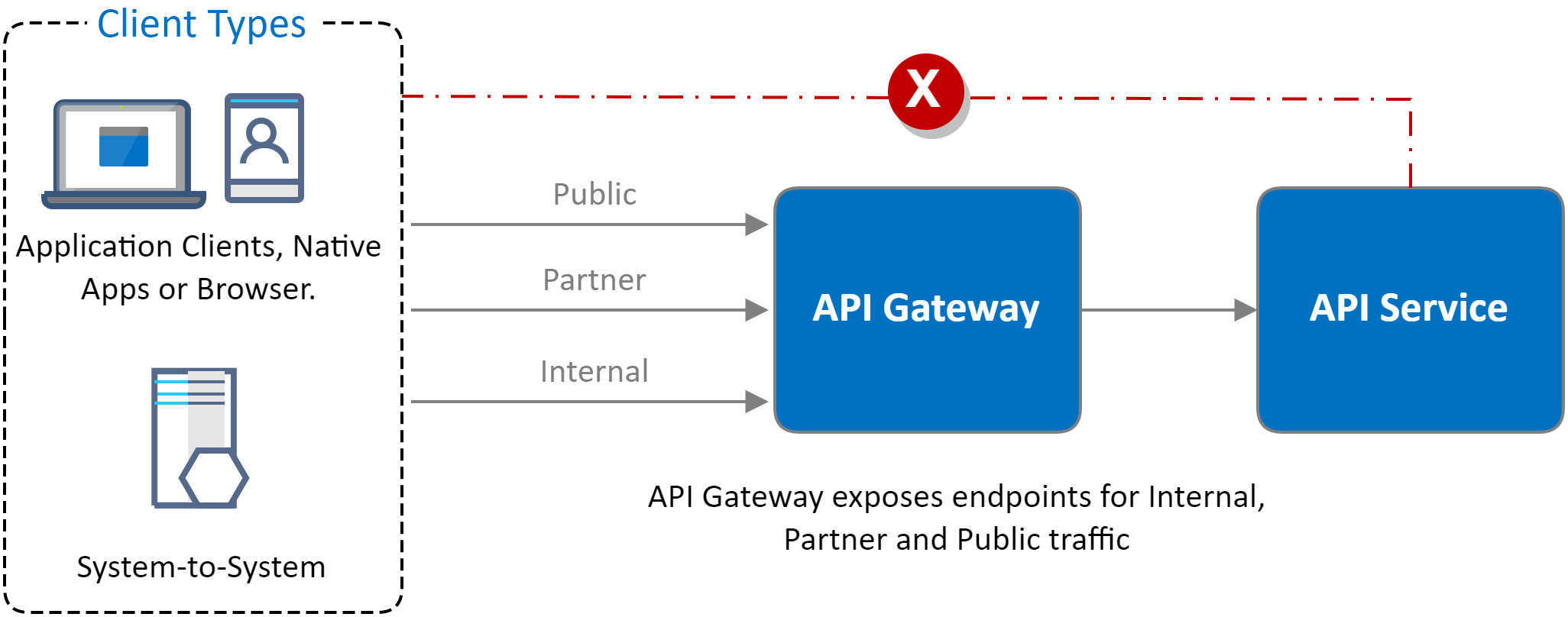
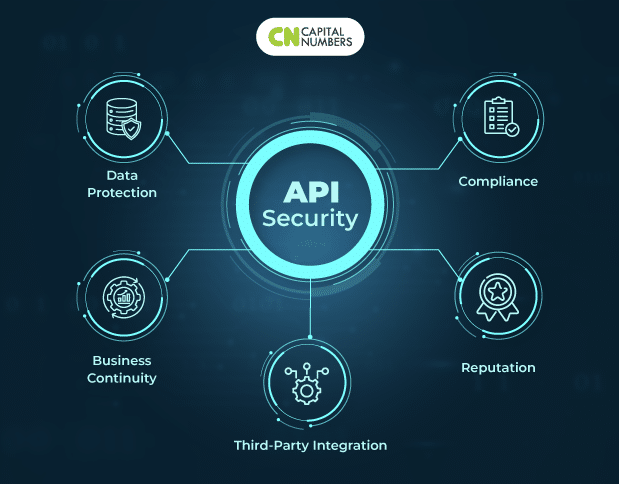




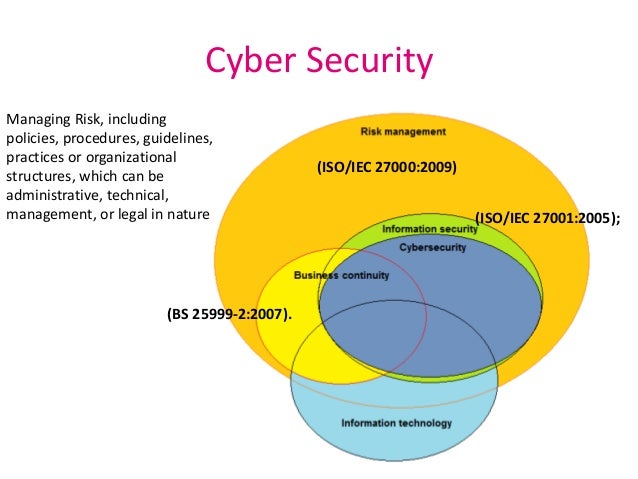
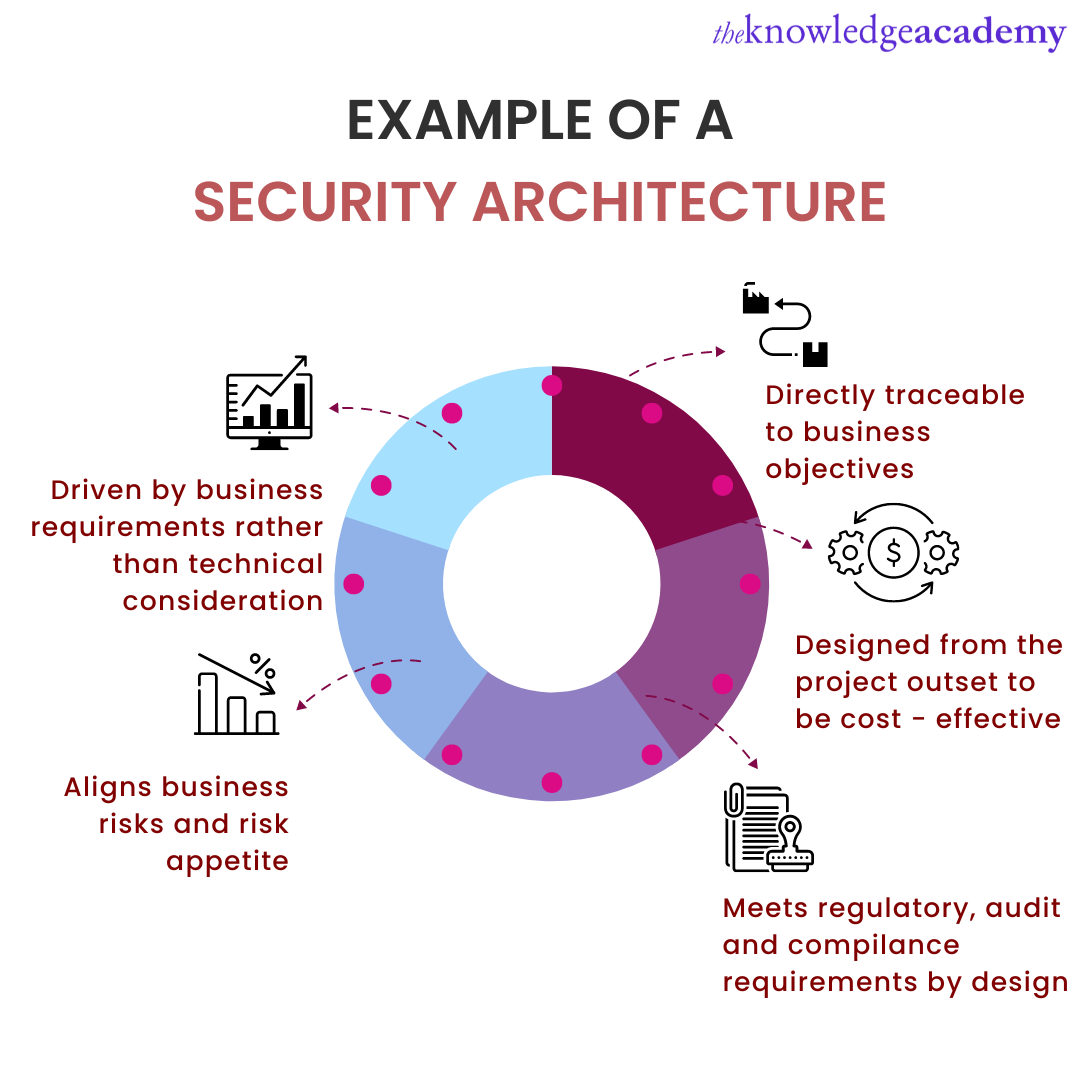
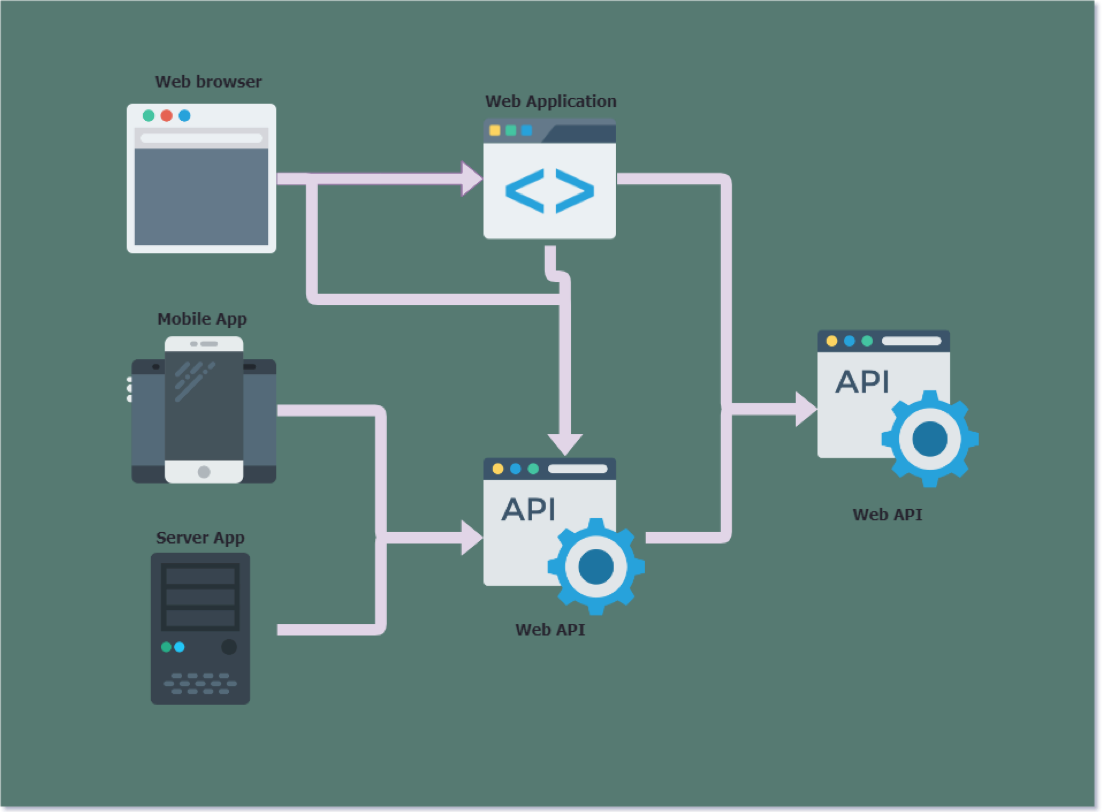

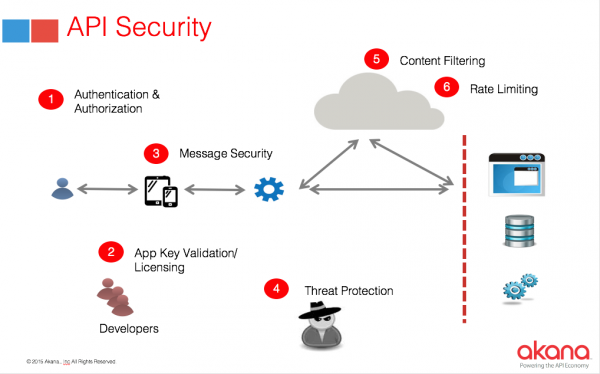
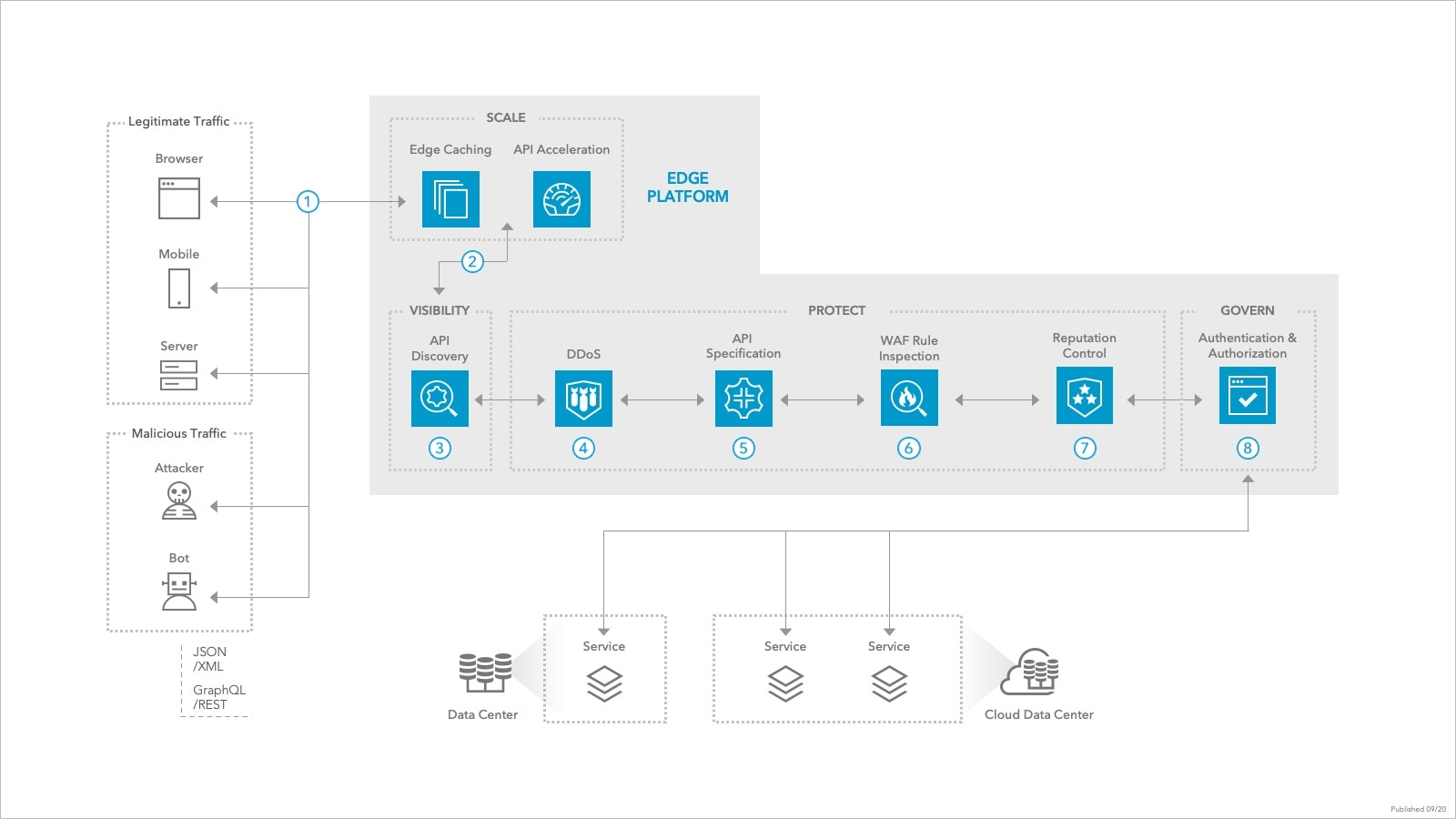




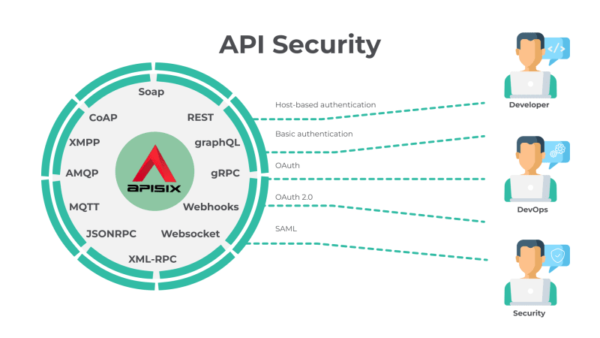
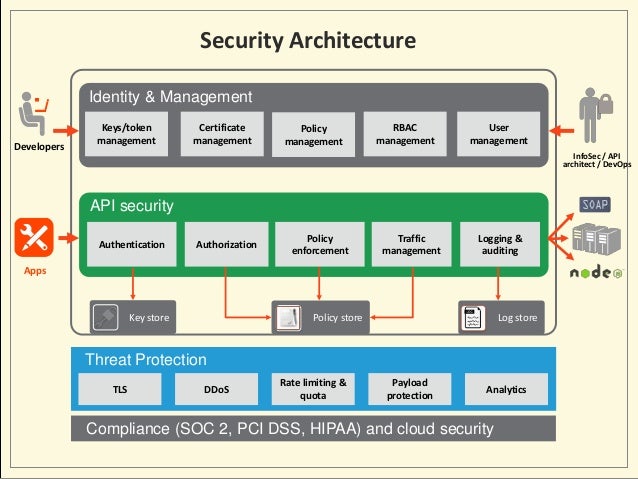
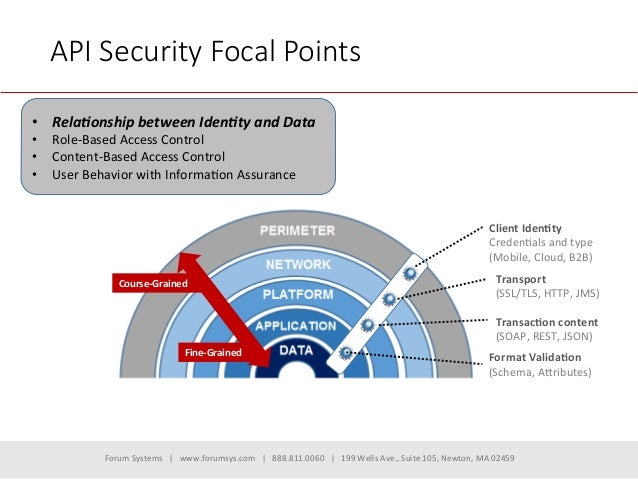

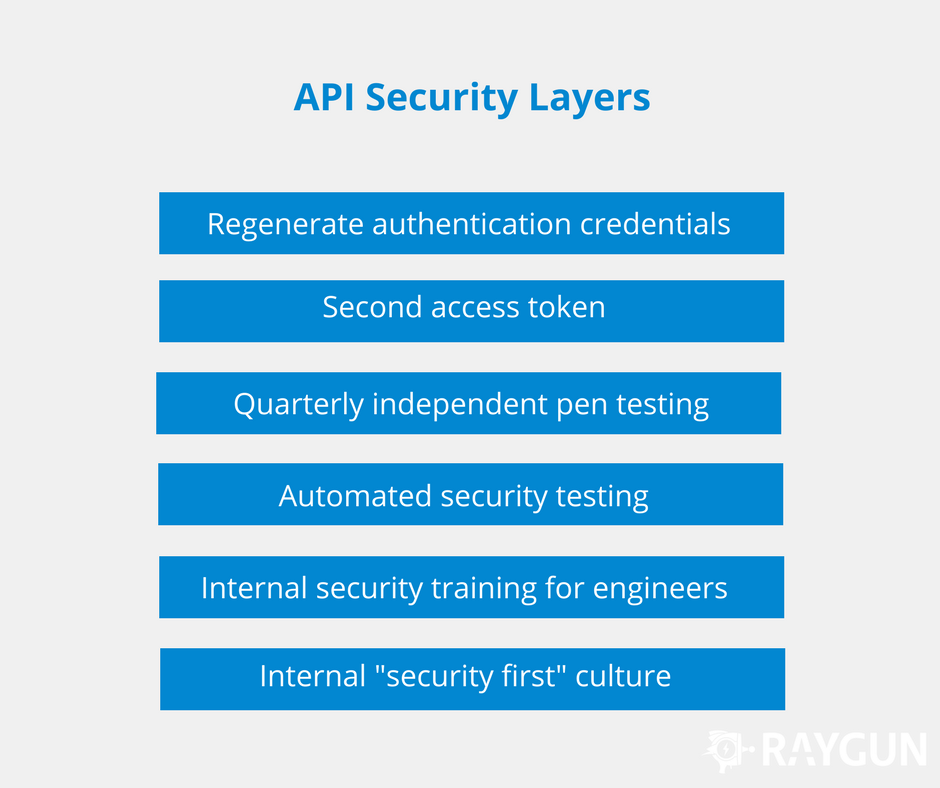
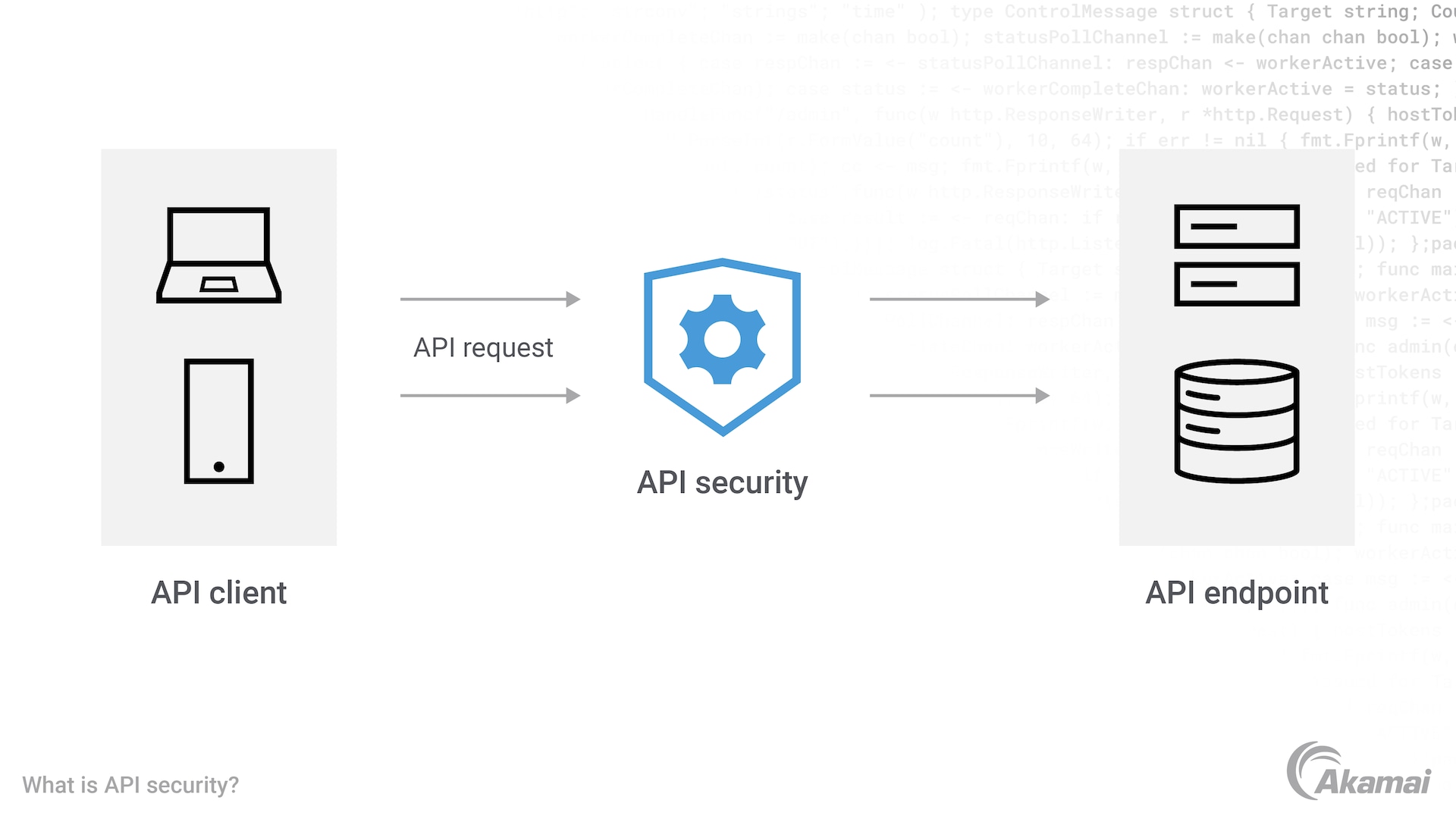





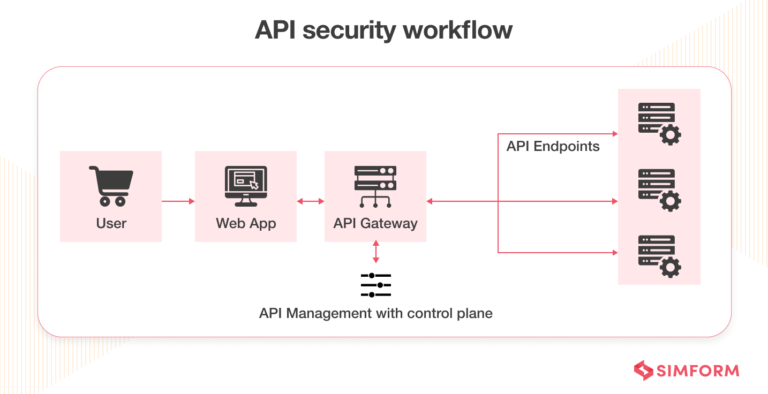






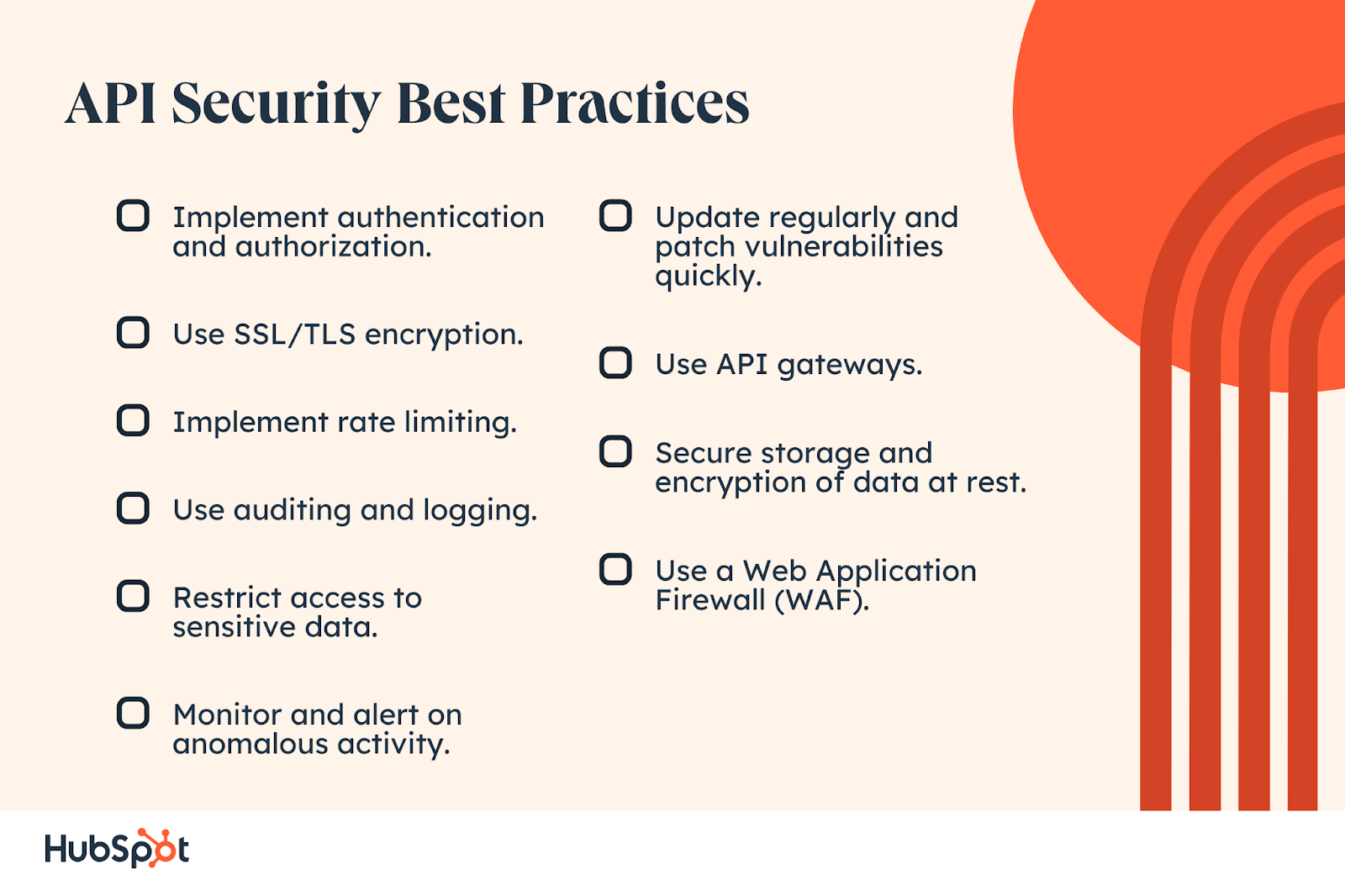



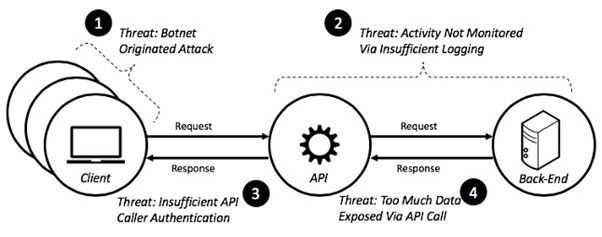

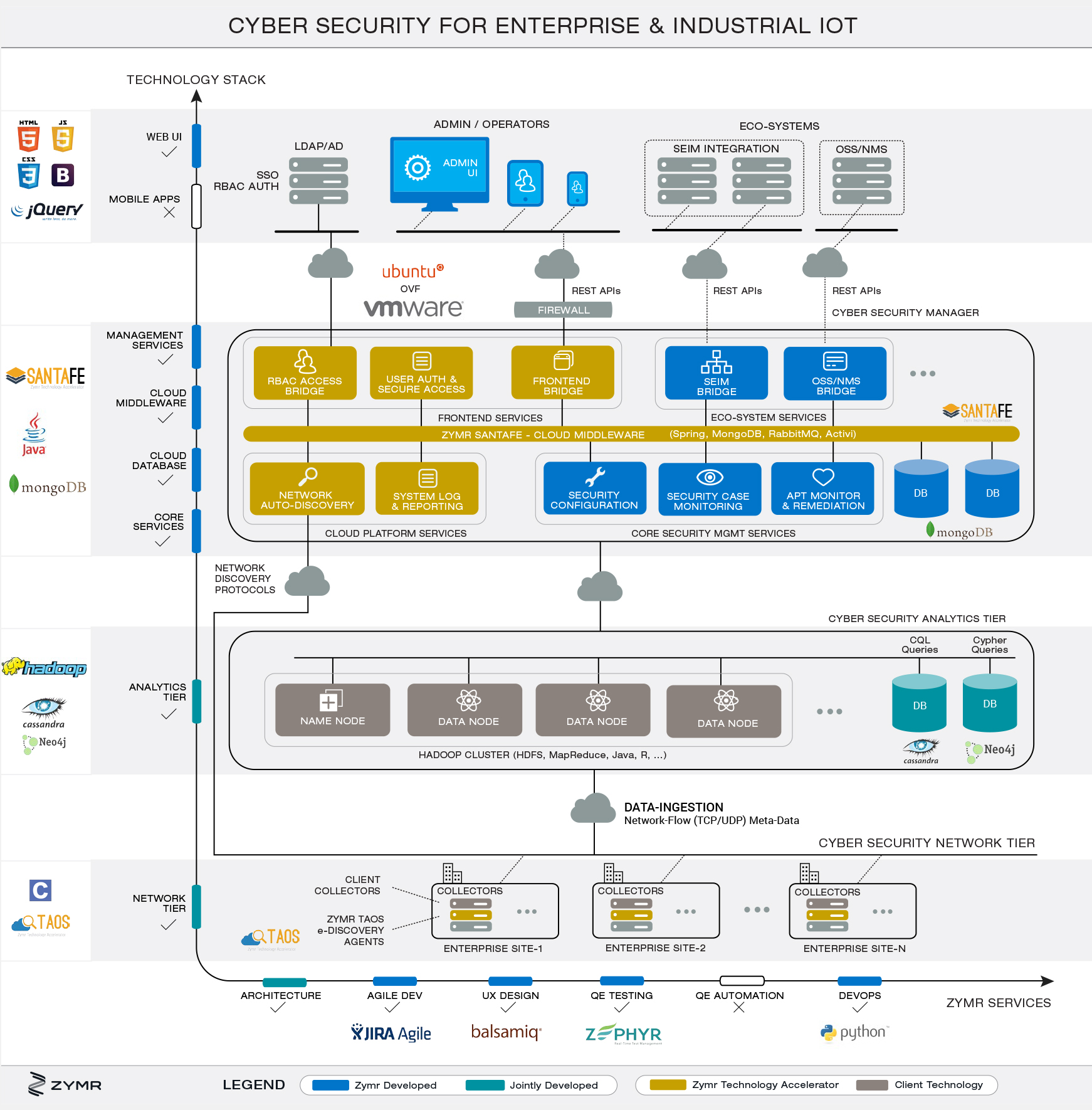
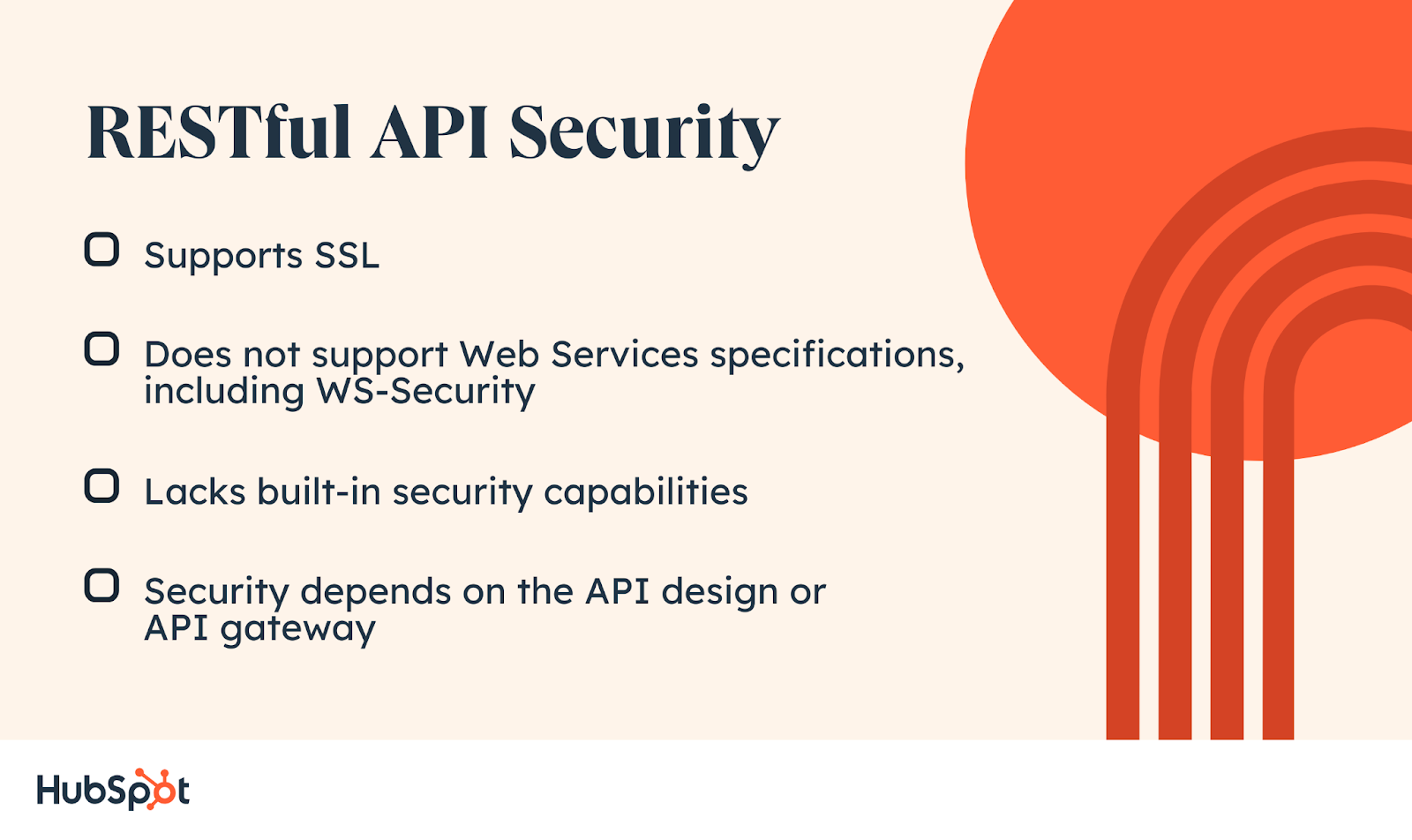
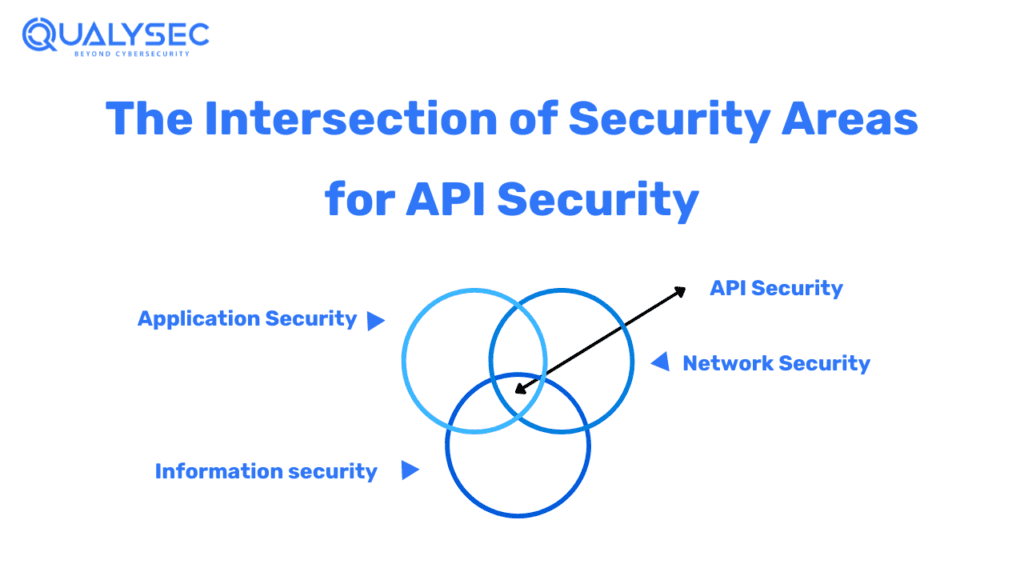
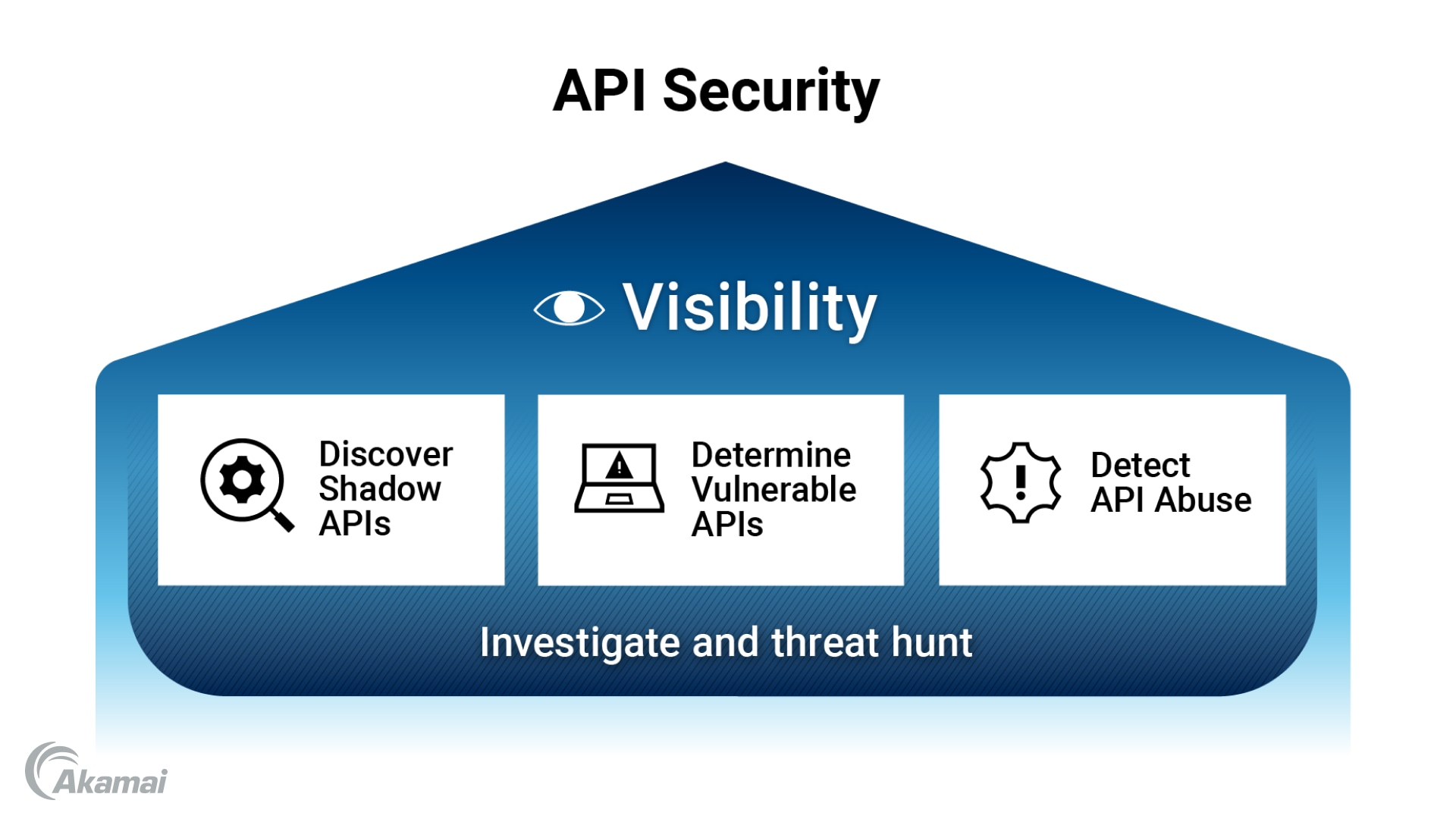

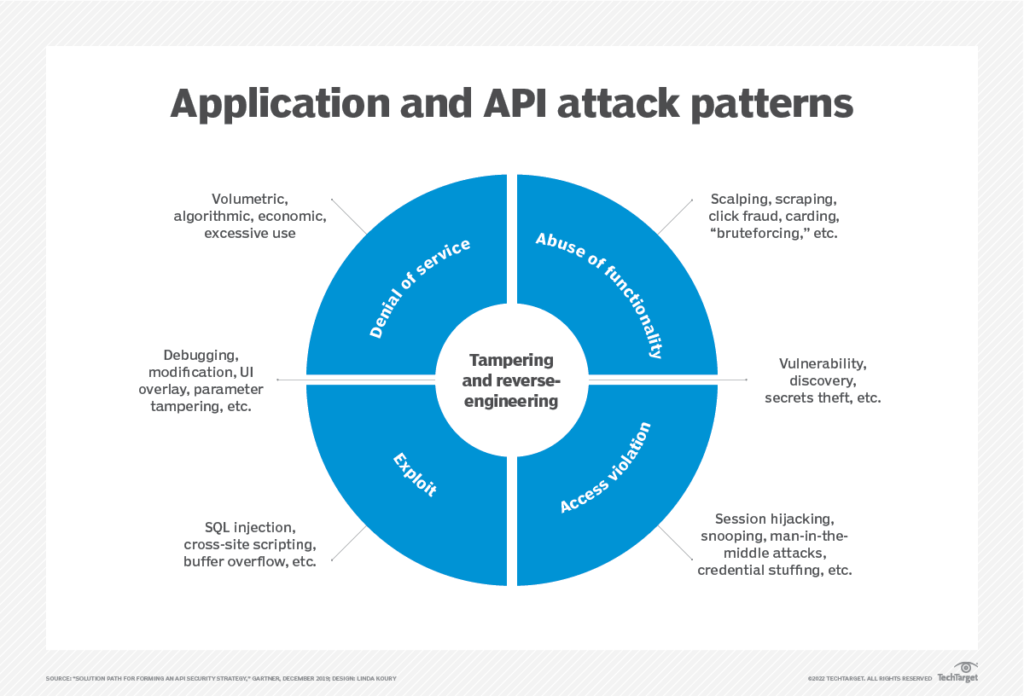











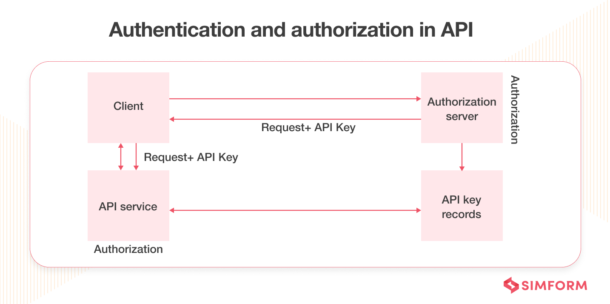

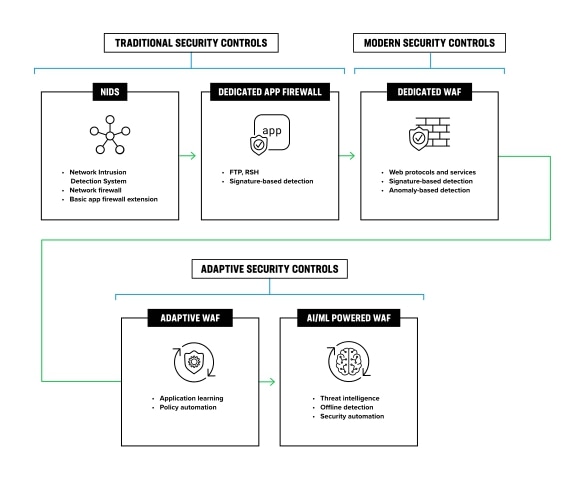



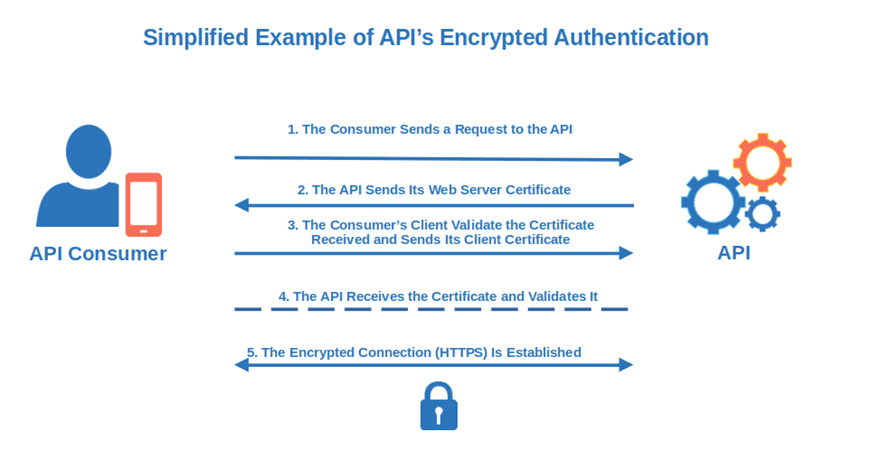



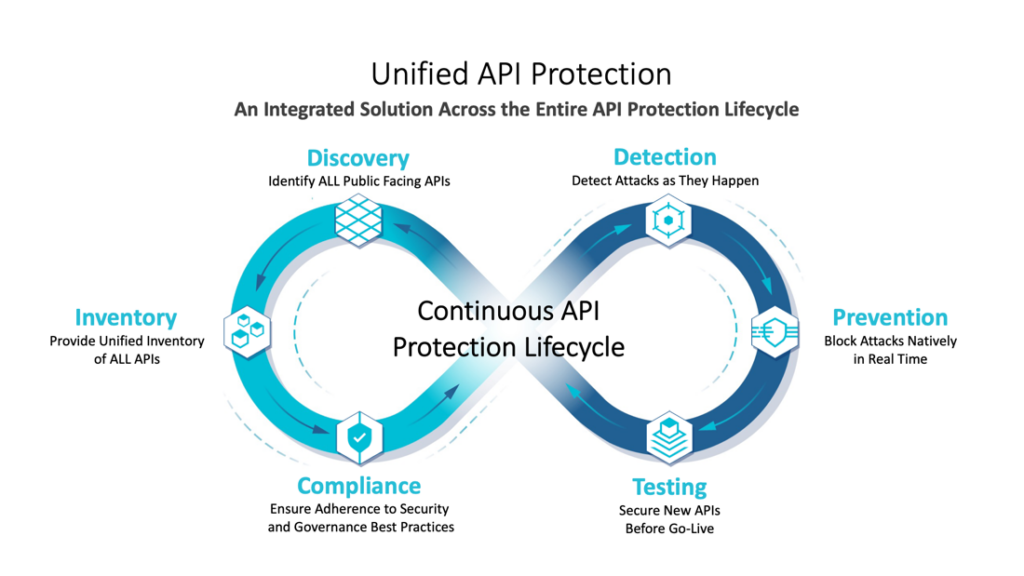




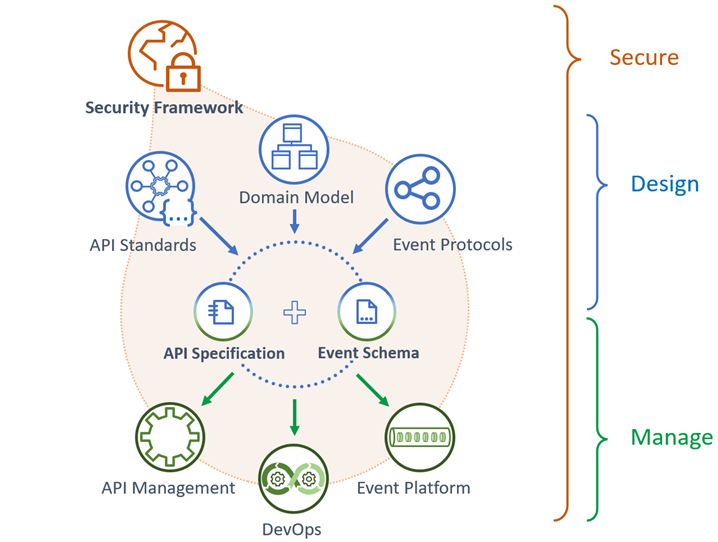

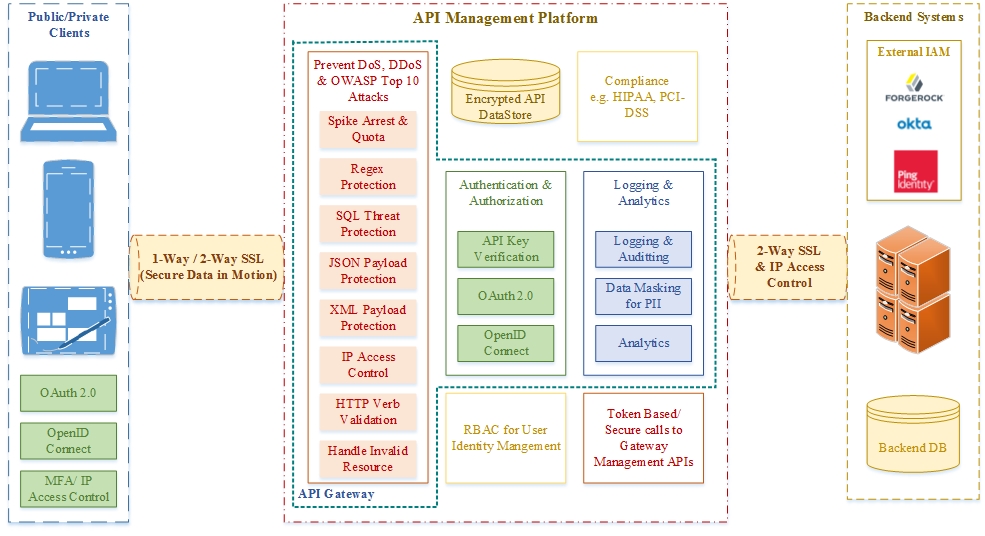
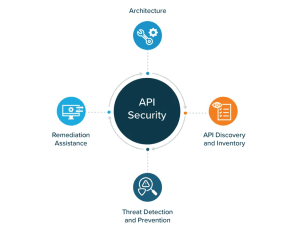
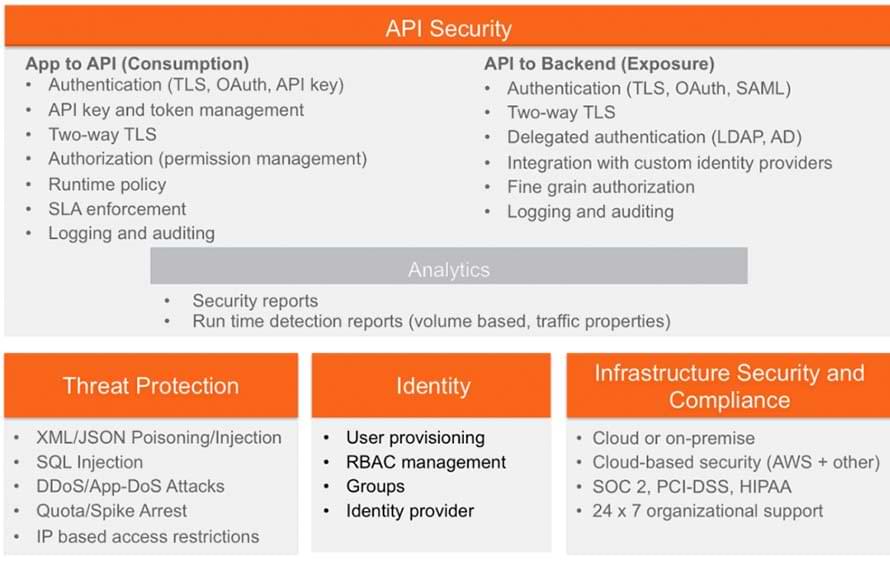
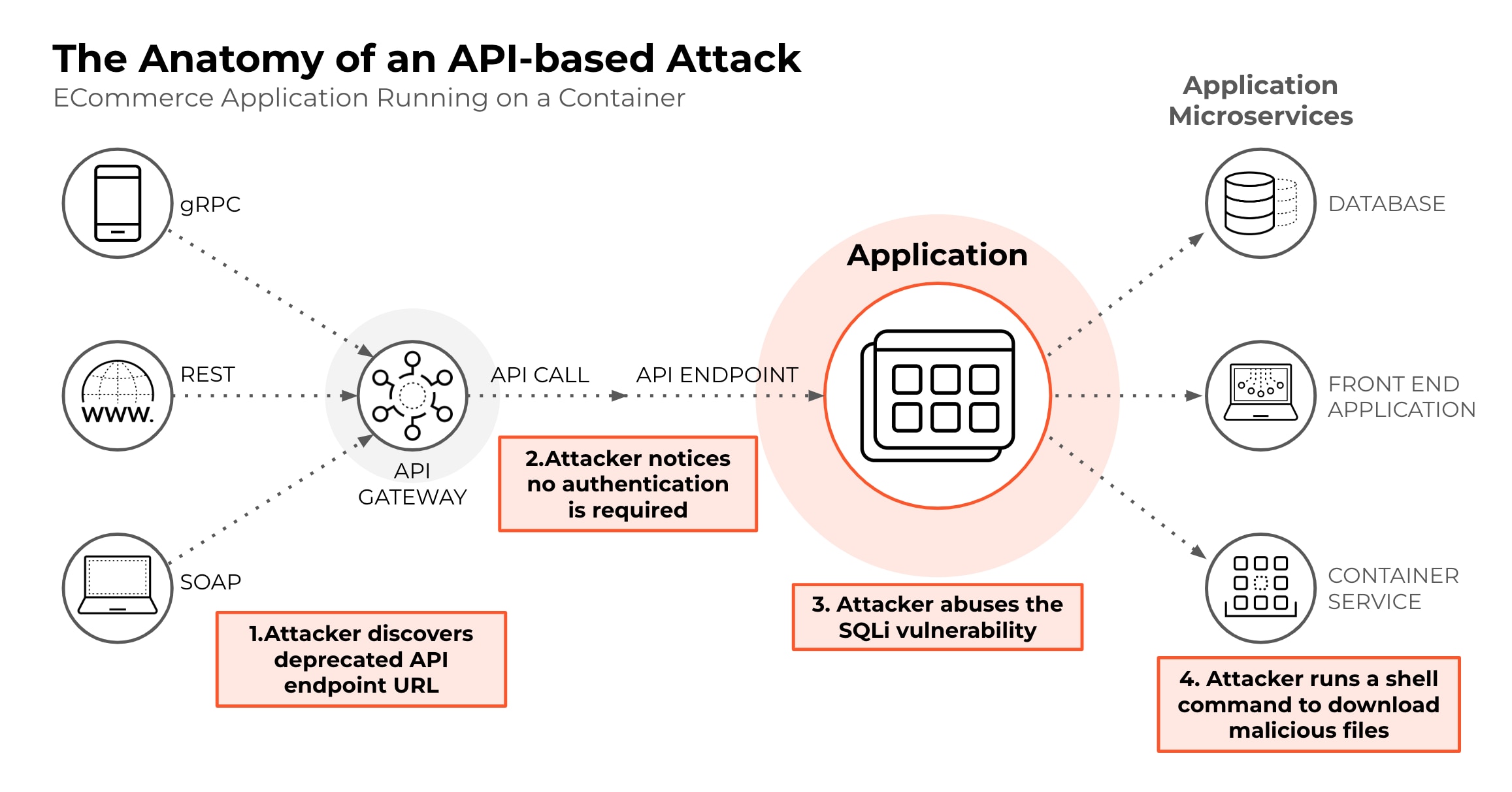
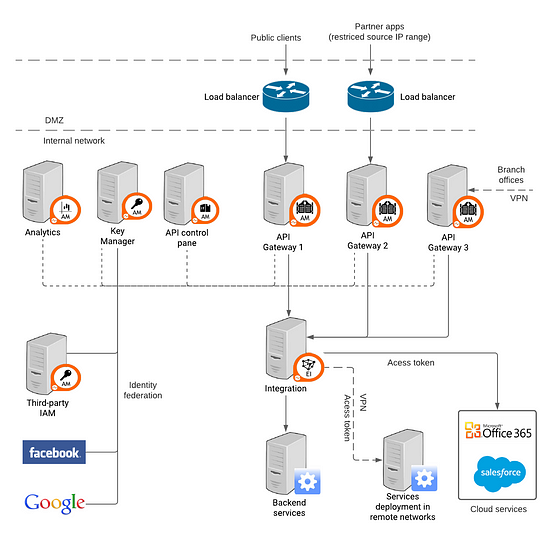
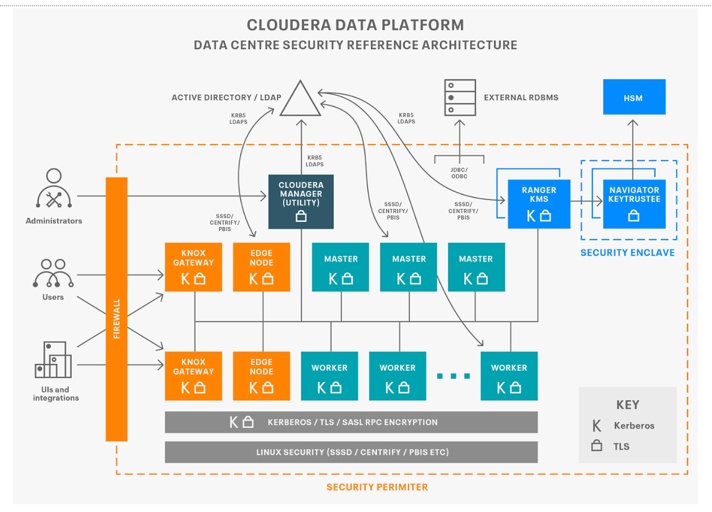
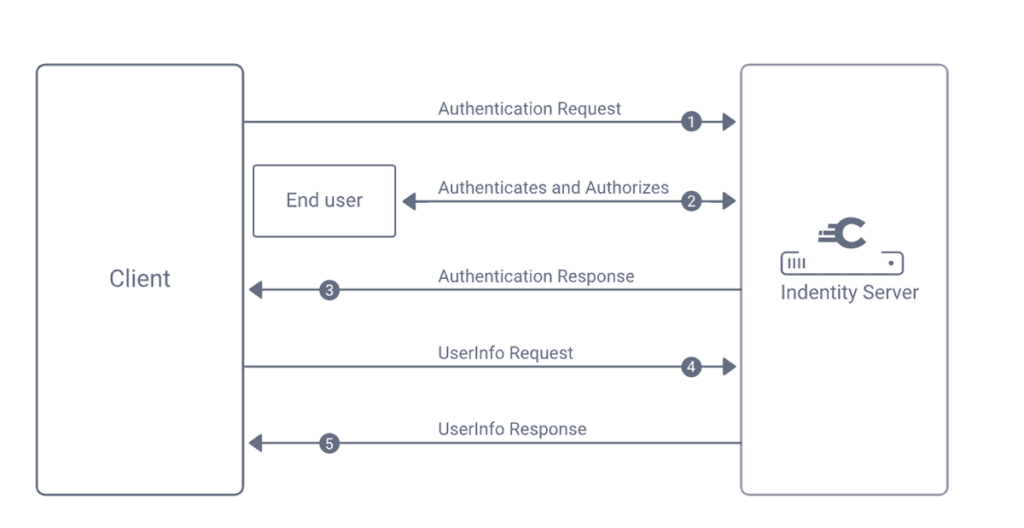
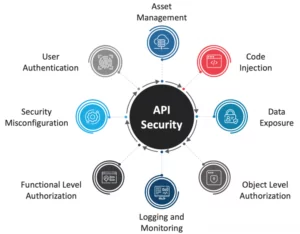
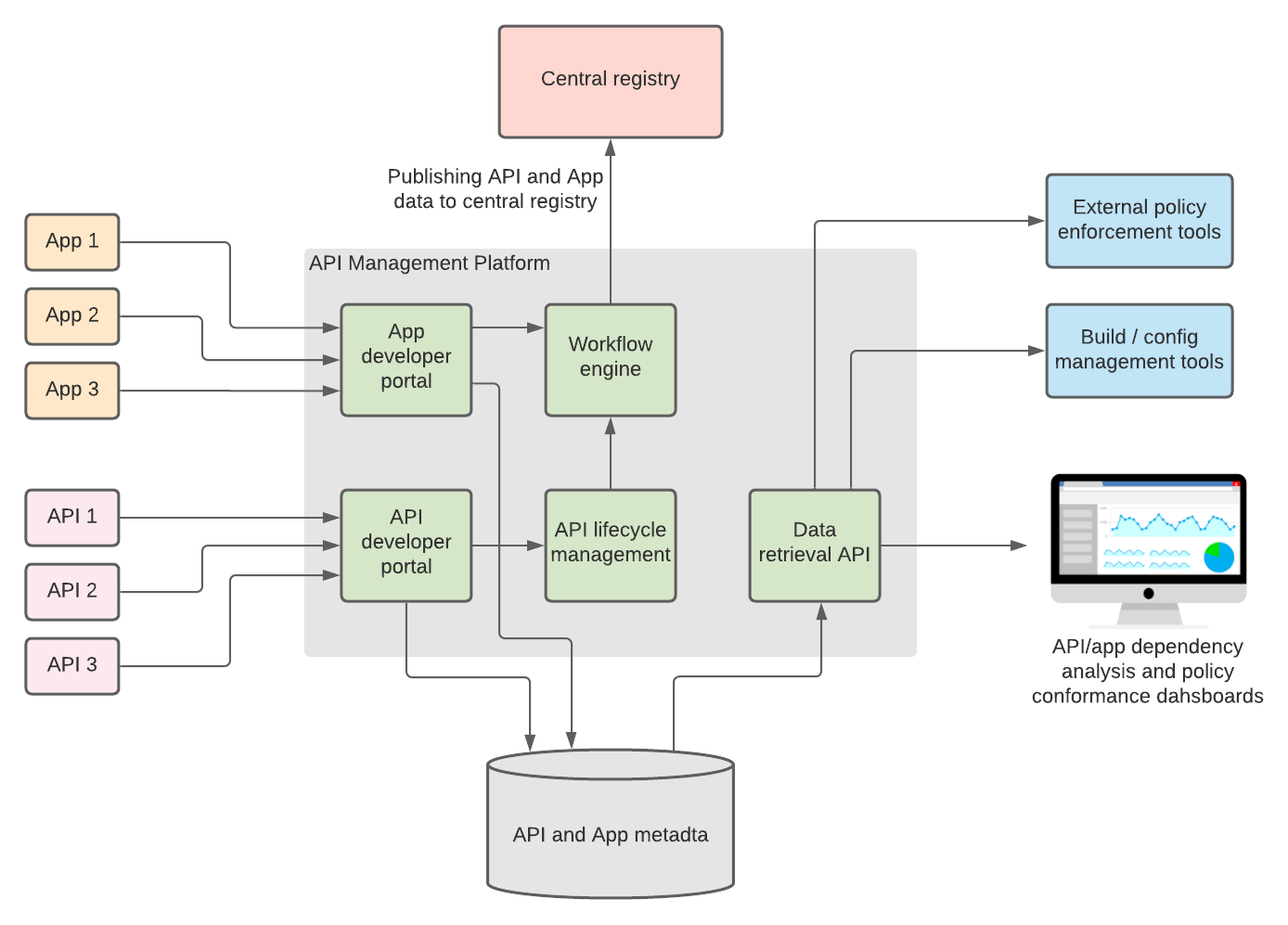
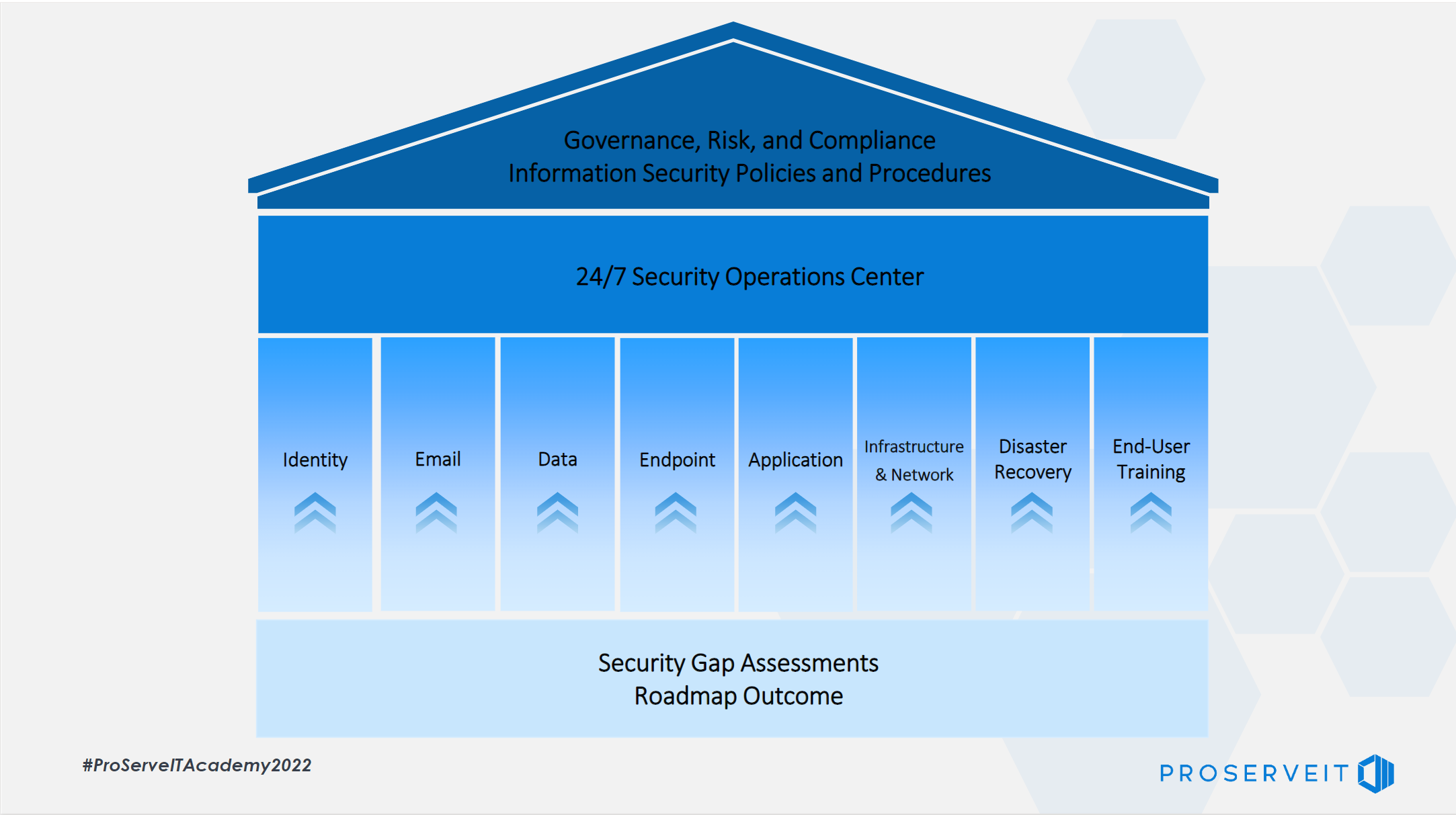

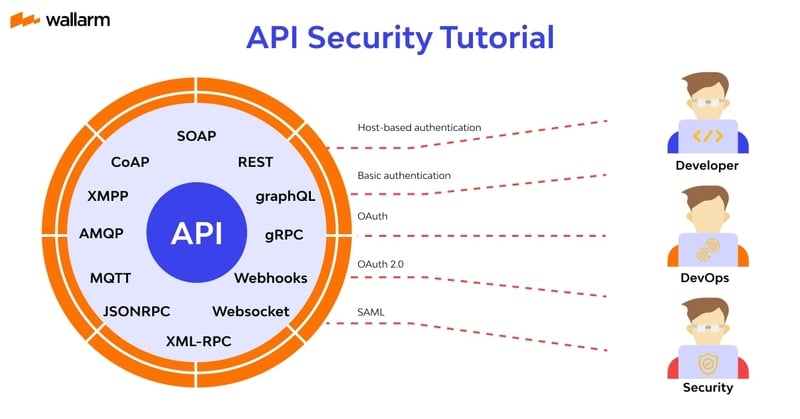
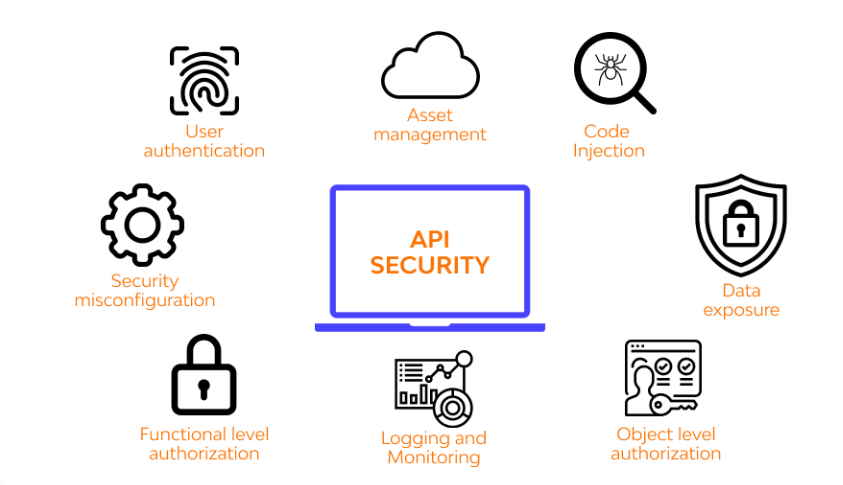

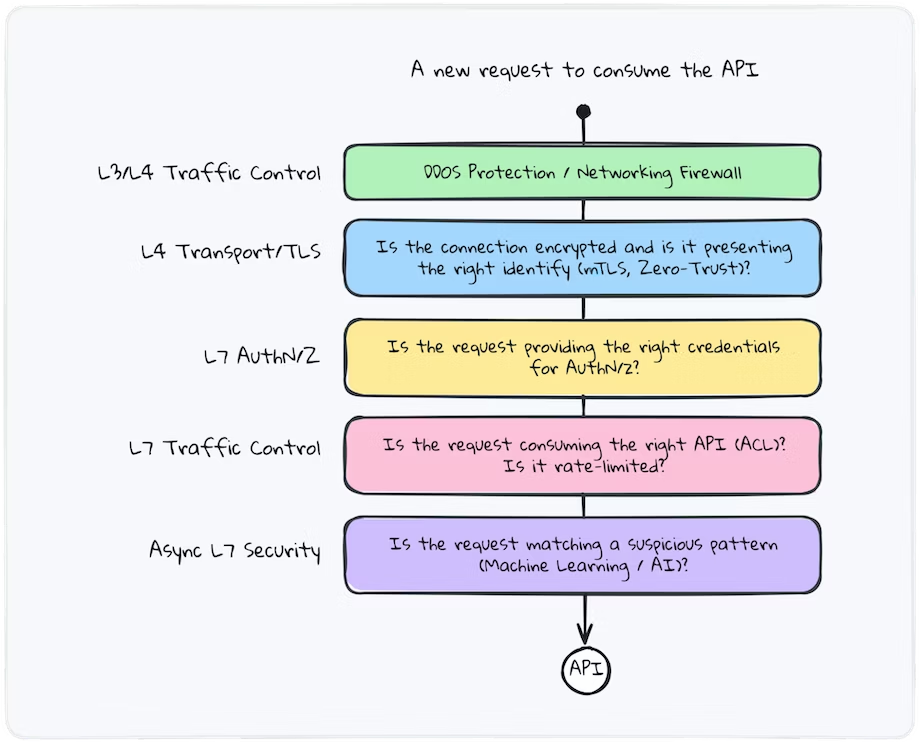
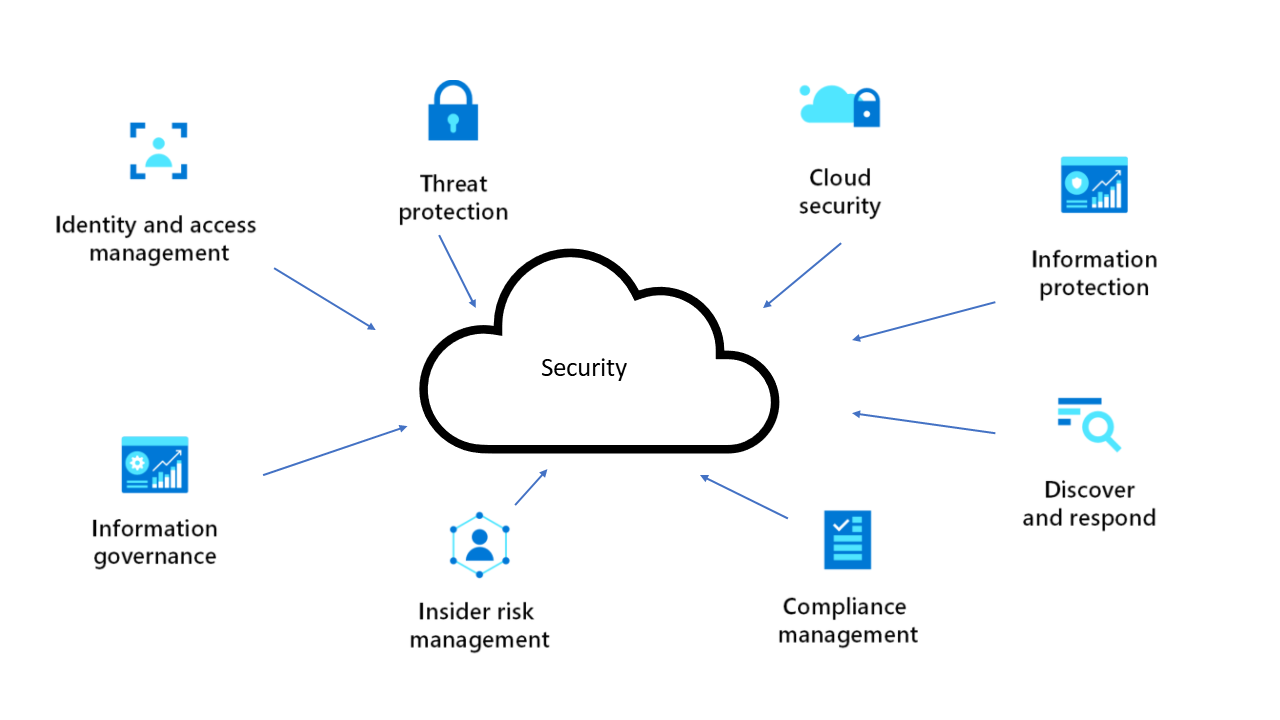
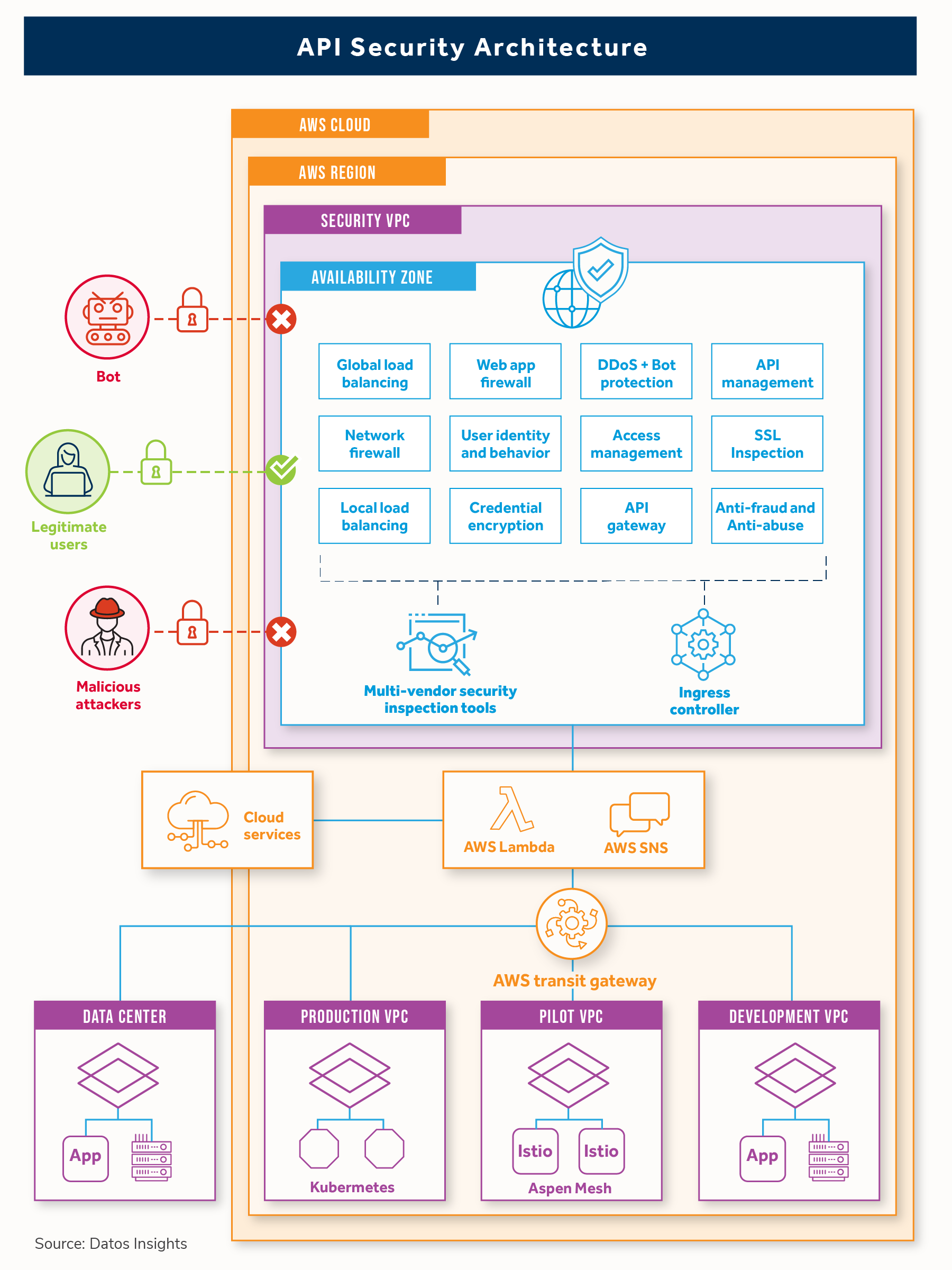
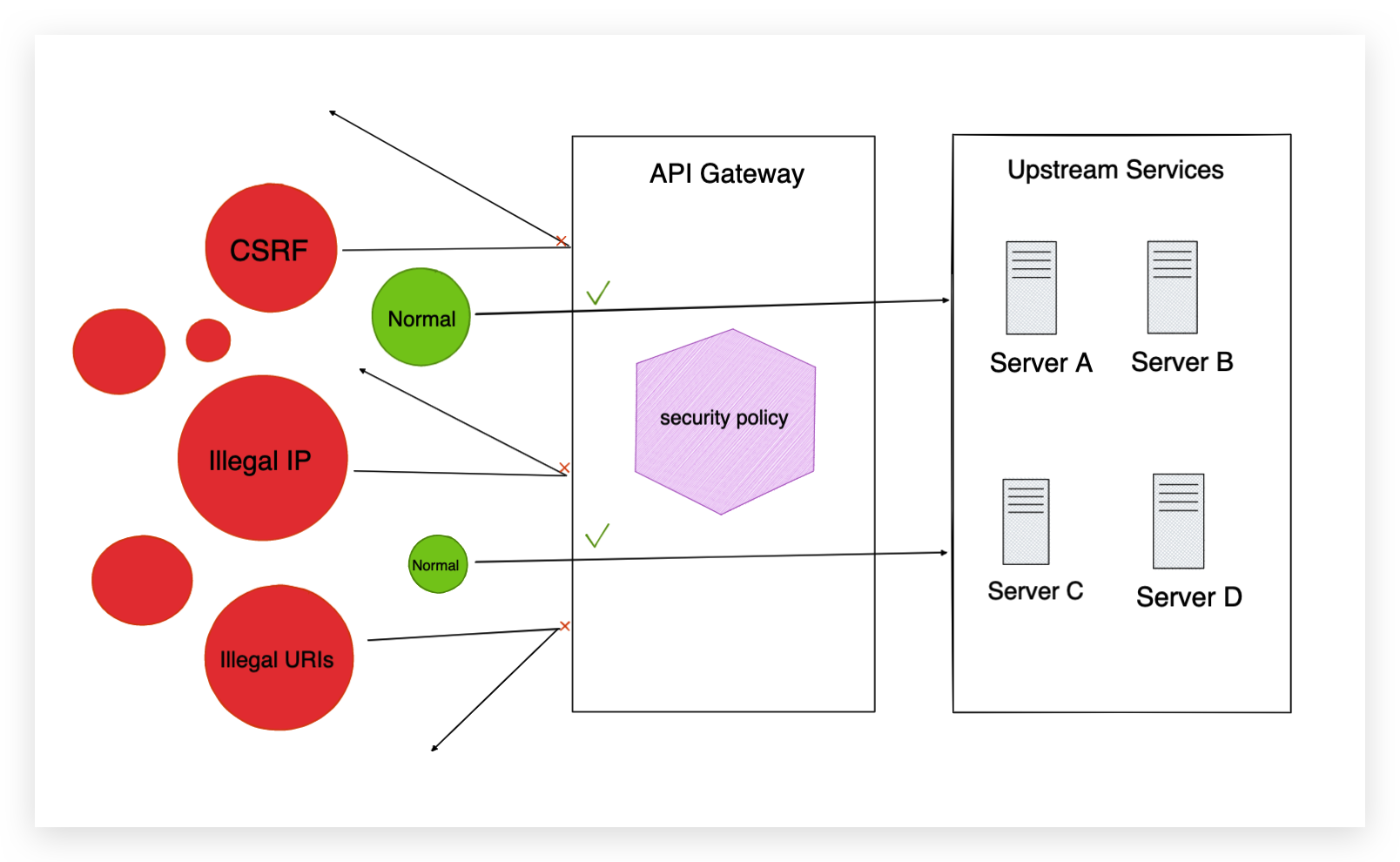




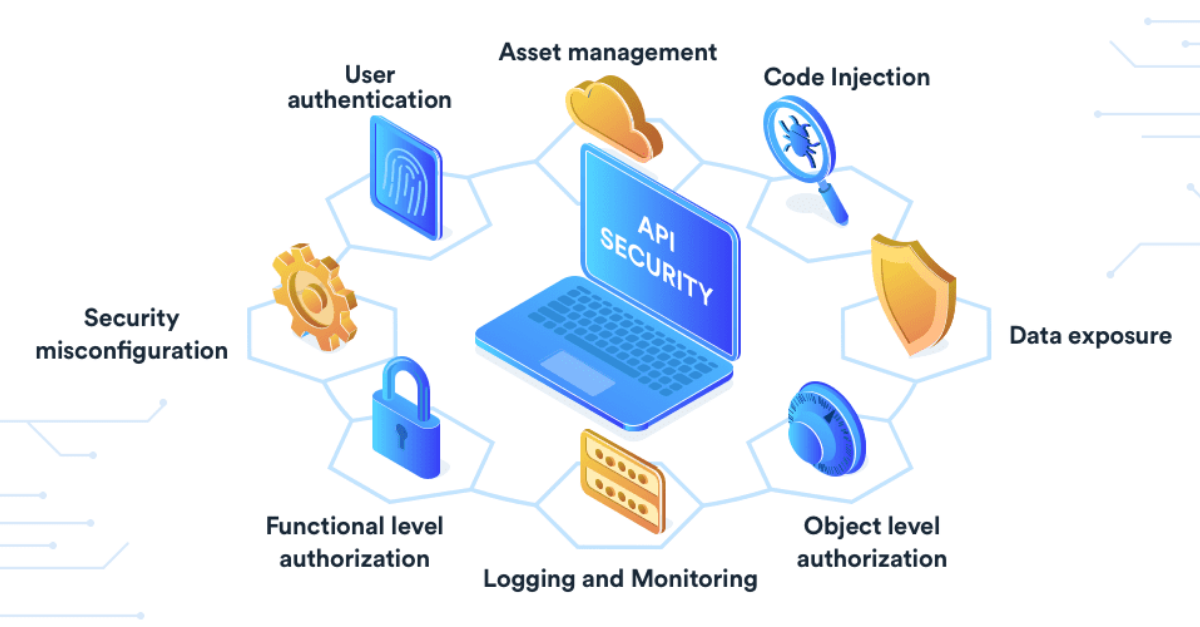
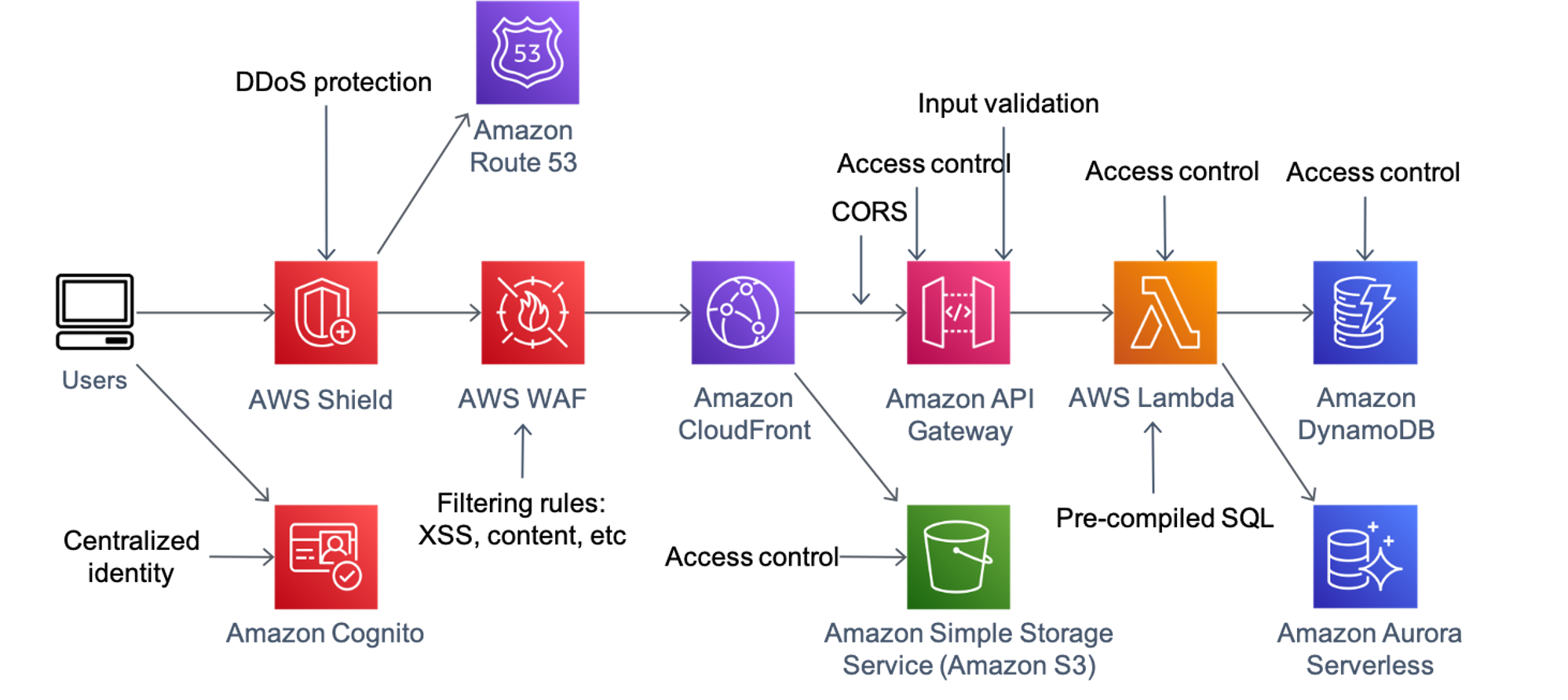
![[Cybersecurity Architecture] Governance Overview (Steer, Direction ...](https://p.51sec.org/file/netsec/2022/12/chrome_1imNRQcdRr.png)