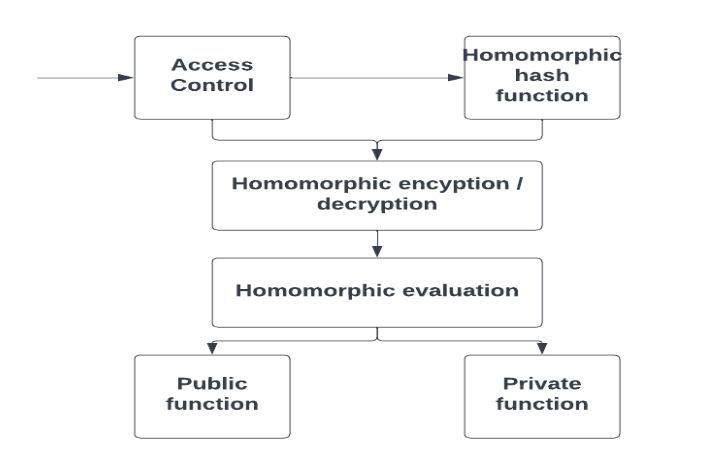
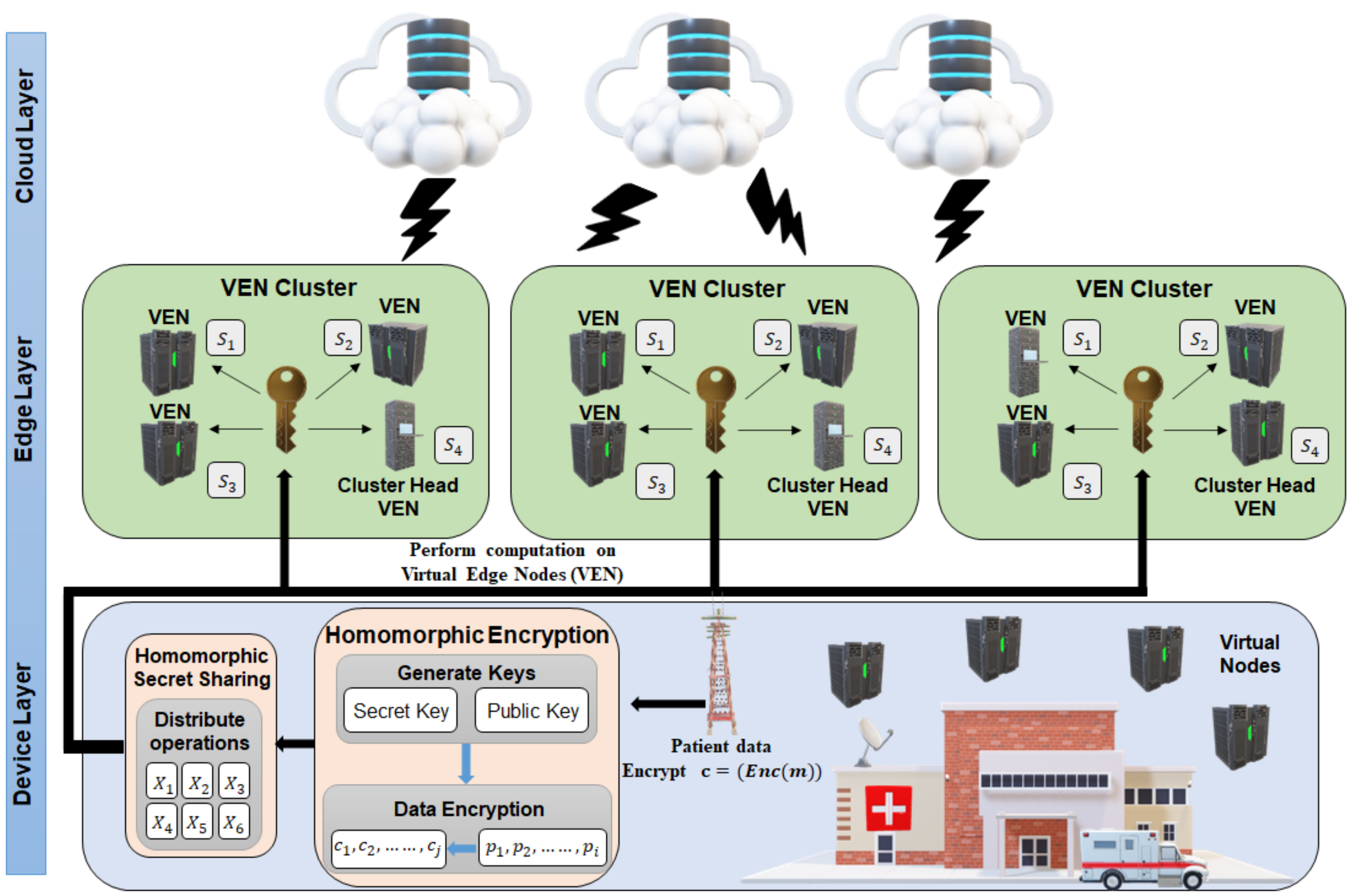
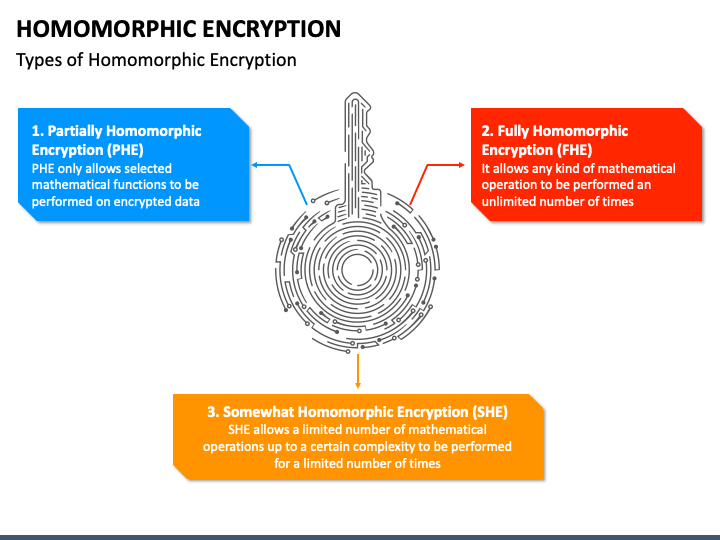
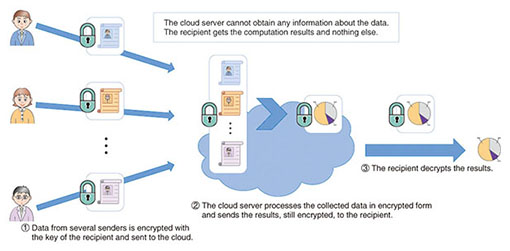
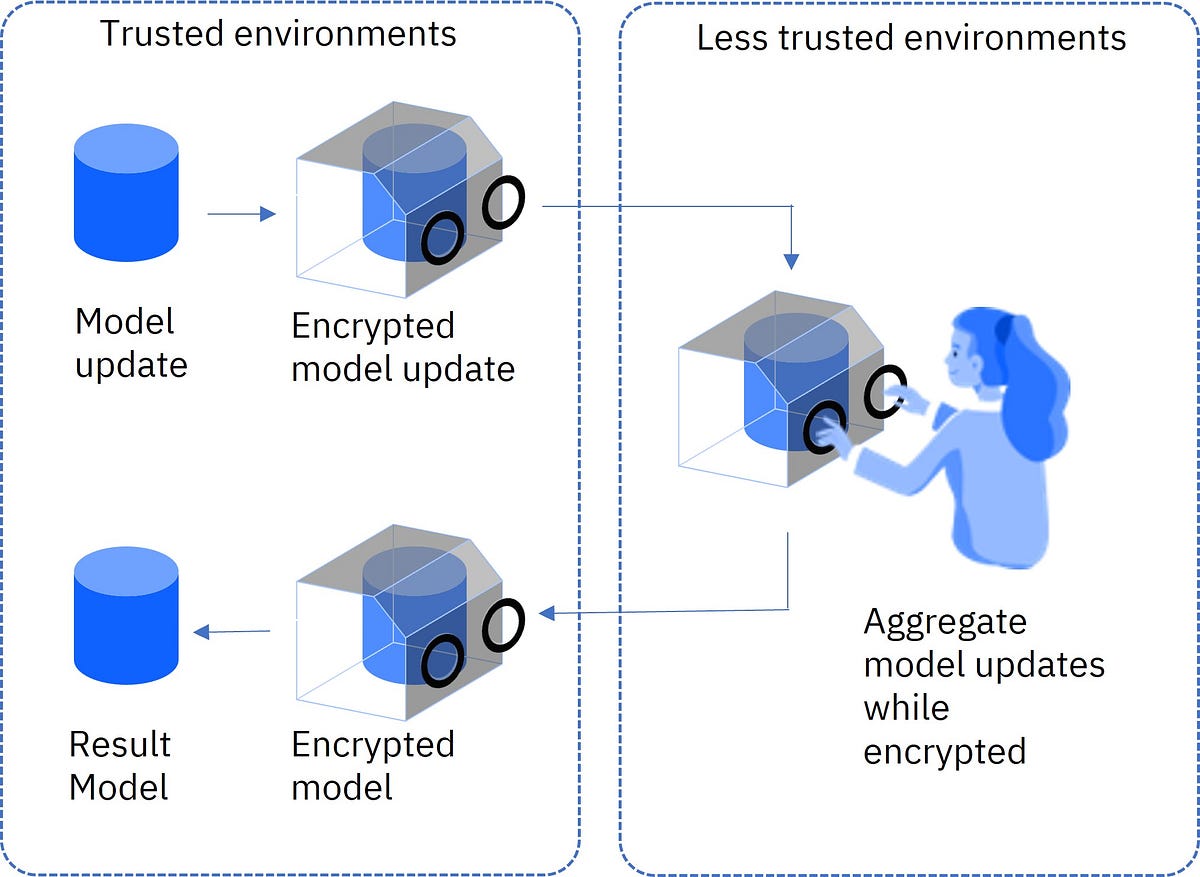
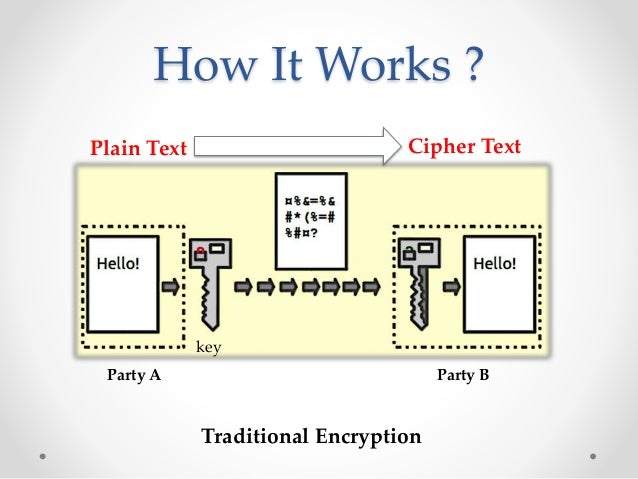
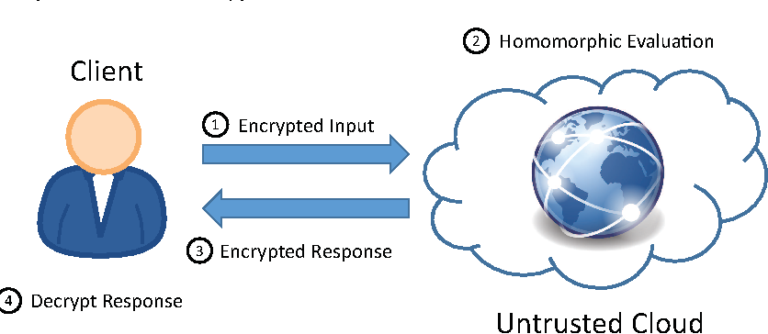
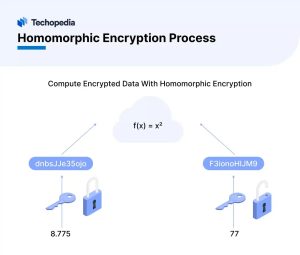
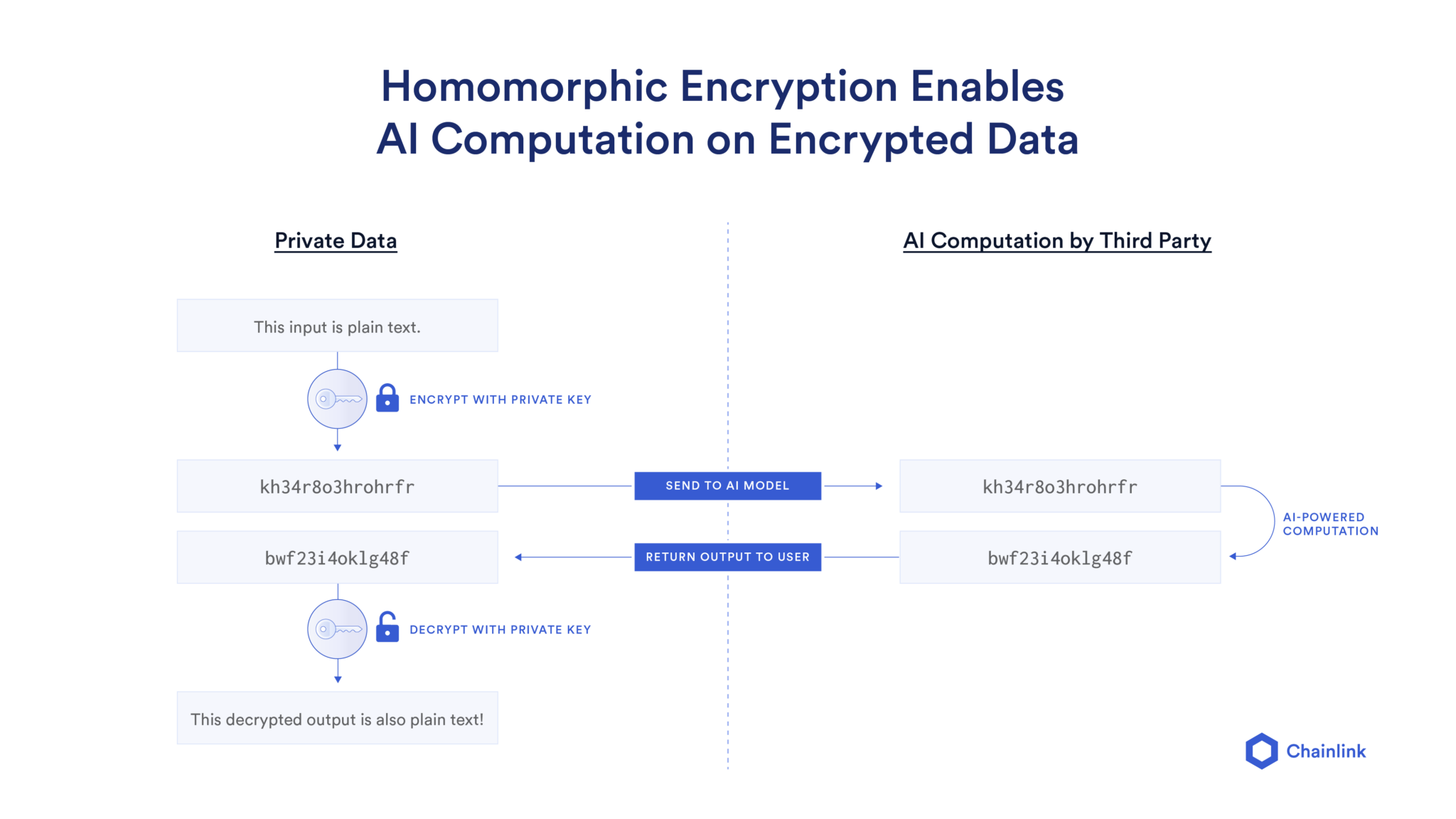
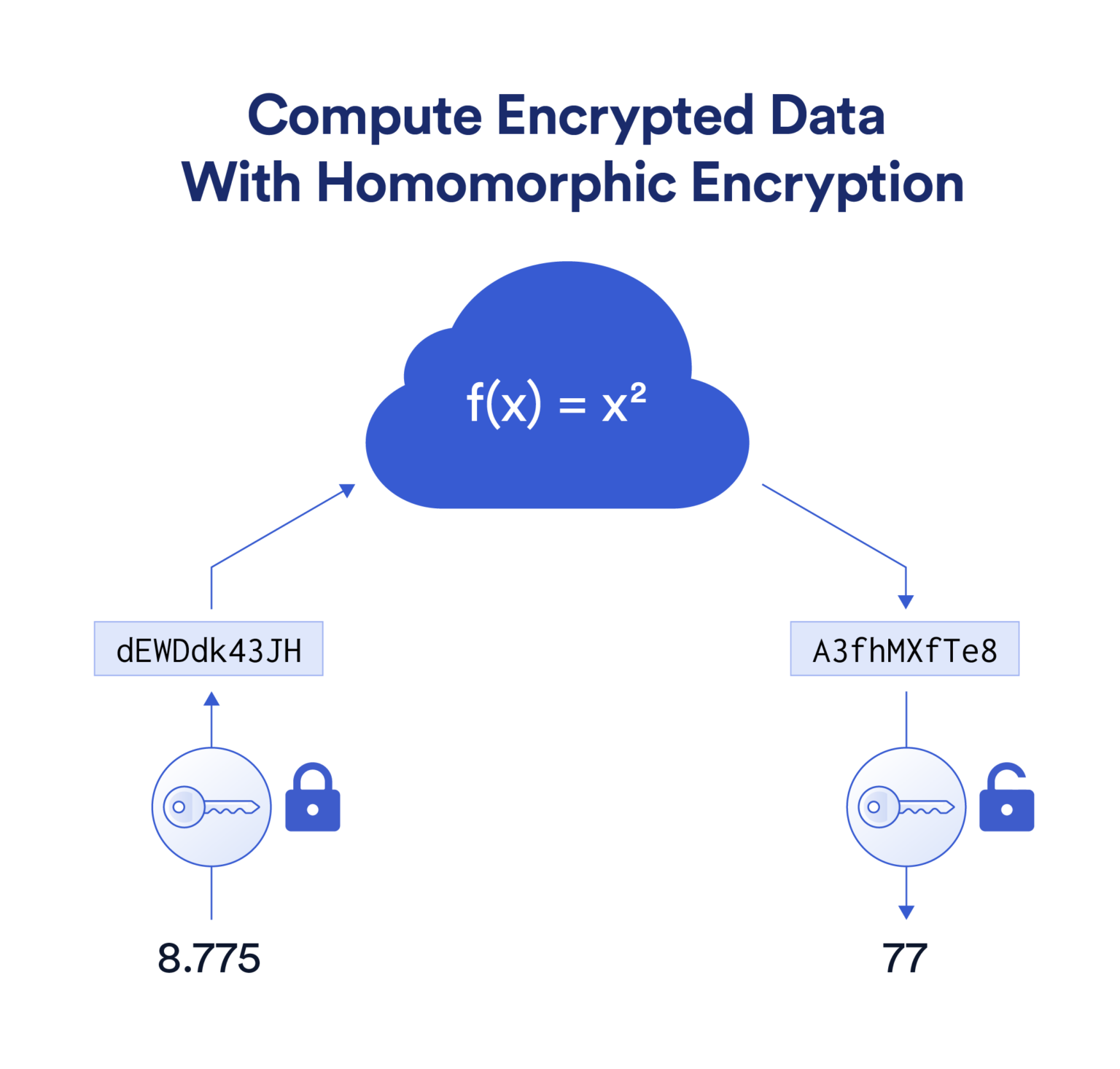
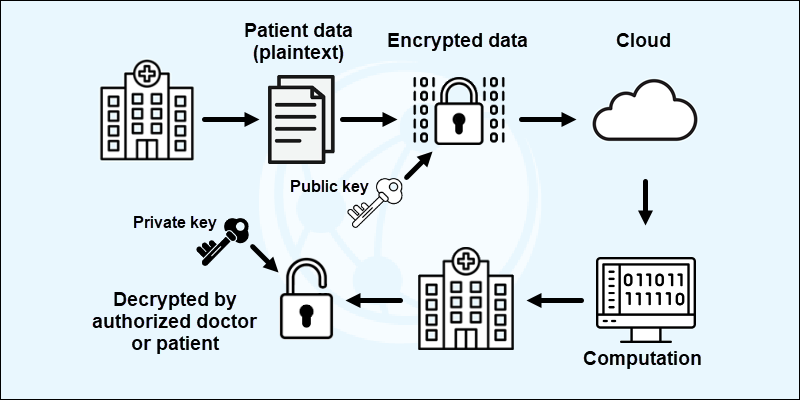
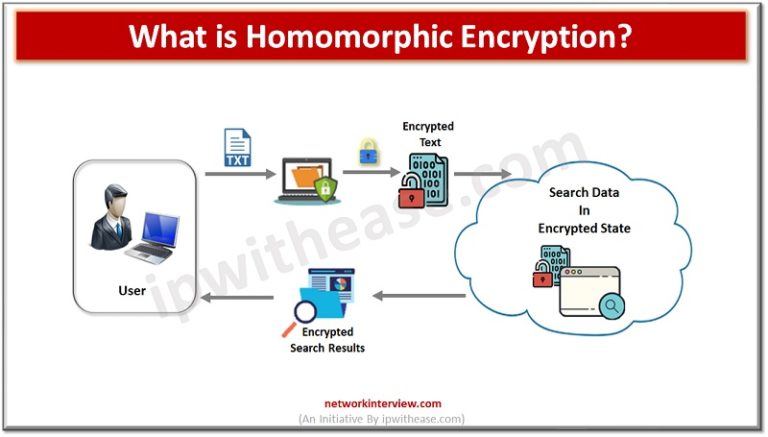
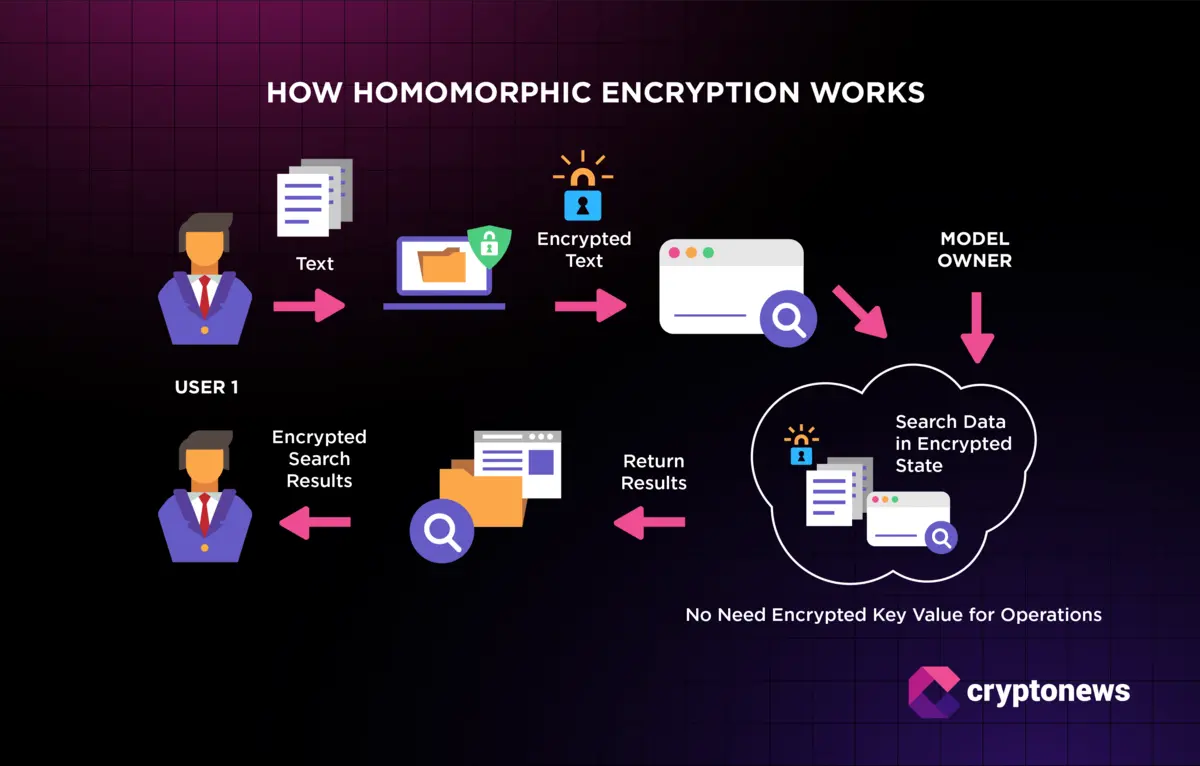
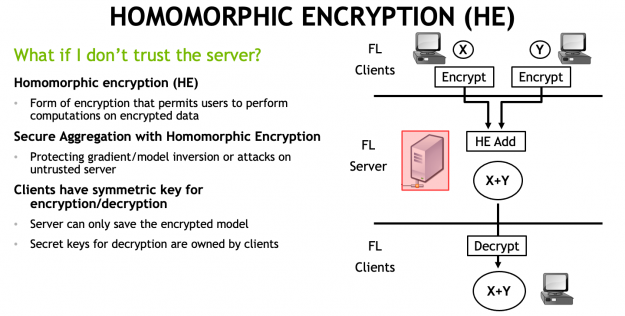
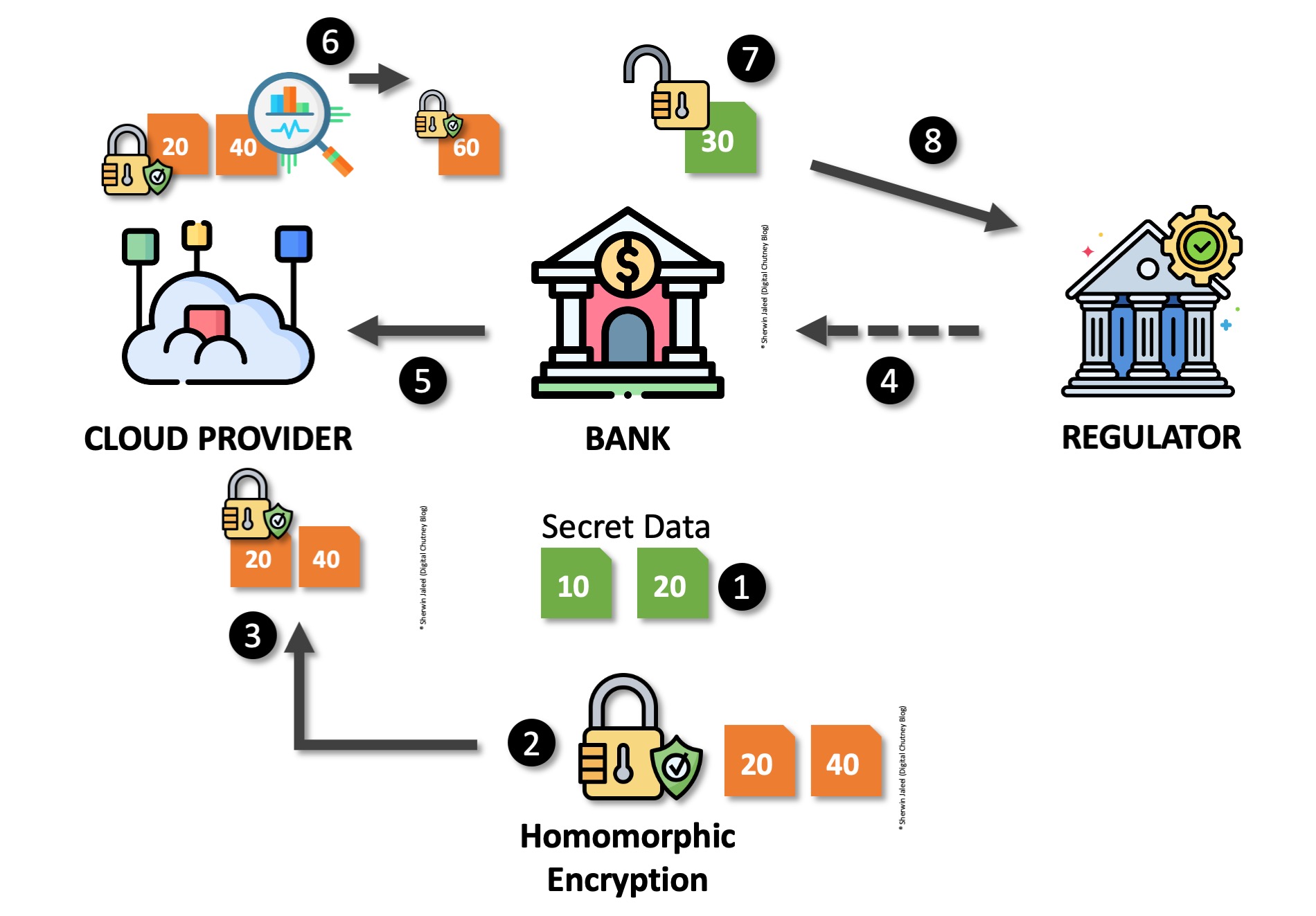
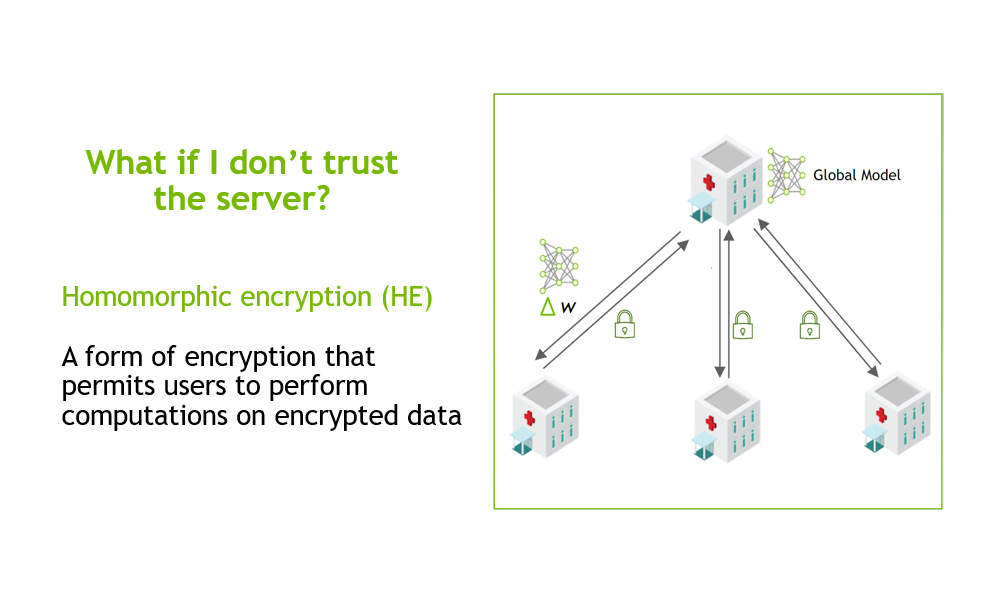
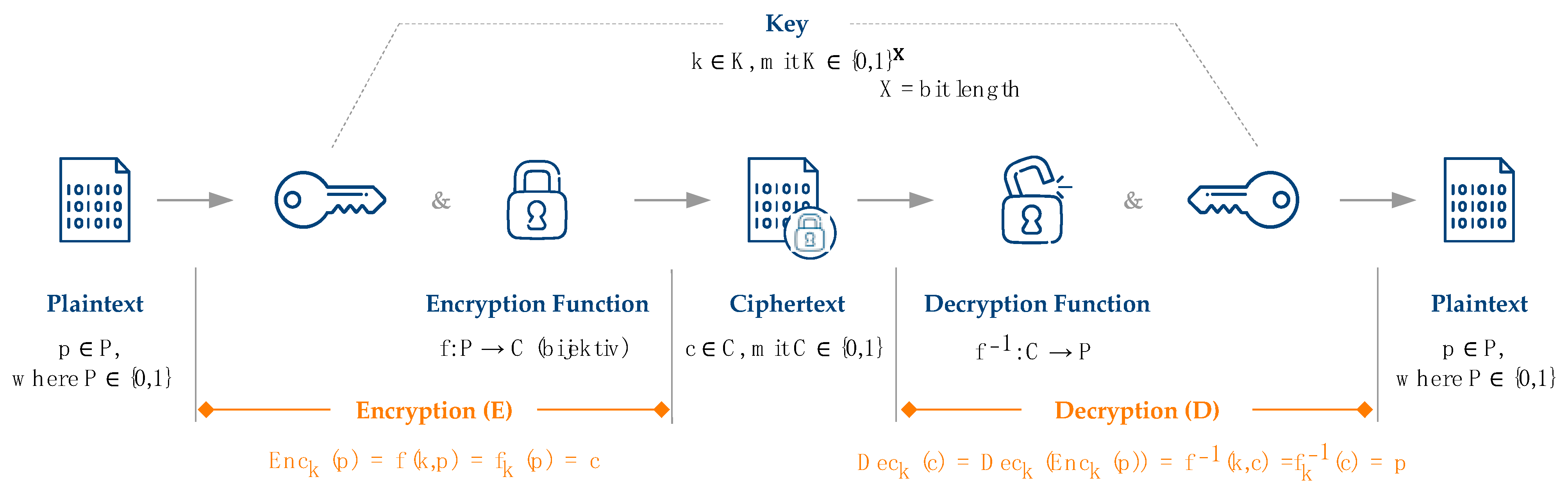
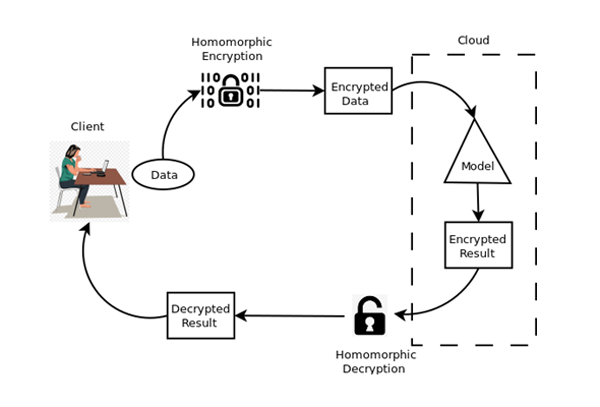
Homomorphic Encryption Process
Explore the world with our stunning travel Homomorphic Encryption Process collection of comprehensive galleries of wanderlust images. adventurously capturing photography, images, and pictures. designed to inspire wanderlust and exploration. Browse our premium Homomorphic Encryption Process gallery featuring professionally curated photographs. Suitable for various applications including web design, social media, personal projects, and digital content creation All Homomorphic Encryption Process images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Discover the perfect Homomorphic Encryption Process images to enhance your visual communication needs. Each image in our Homomorphic Encryption Process gallery undergoes rigorous quality assessment before inclusion. Instant download capabilities enable immediate access to chosen Homomorphic Encryption Process images. Multiple resolution options ensure optimal performance across different platforms and applications. Cost-effective licensing makes professional Homomorphic Encryption Process photography accessible to all budgets. Advanced search capabilities make finding the perfect Homomorphic Encryption Process image effortless and efficient. Time-saving browsing features help users locate ideal Homomorphic Encryption Process images quickly. The Homomorphic Encryption Process archive serves professionals, educators, and creatives across diverse industries. Our Homomorphic Encryption Process database continuously expands with fresh, relevant content from skilled photographers. The Homomorphic Encryption Process collection represents years of careful curation and professional standards.
![Homomorphic Encryption Process [29] | Download Scientific Diagram](https://www.researchgate.net/publication/376536908/figure/fig1/AS:11431281212478880@1702657567226/Homomorphic-Encryption-Process-29_Q640.jpg)




![Homomorphic Encryption Process [29] | Download Scientific Diagram](https://www.researchgate.net/publication/376536908/figure/tbl2/AS:11431281212507059@1702657567583/8F-HE-based-encryption-and-computation-time_Q320.jpg)
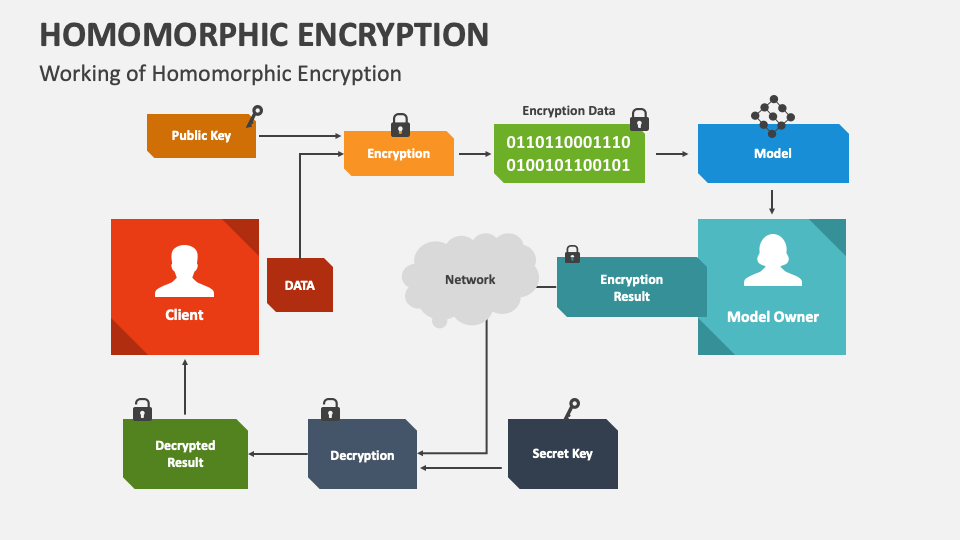

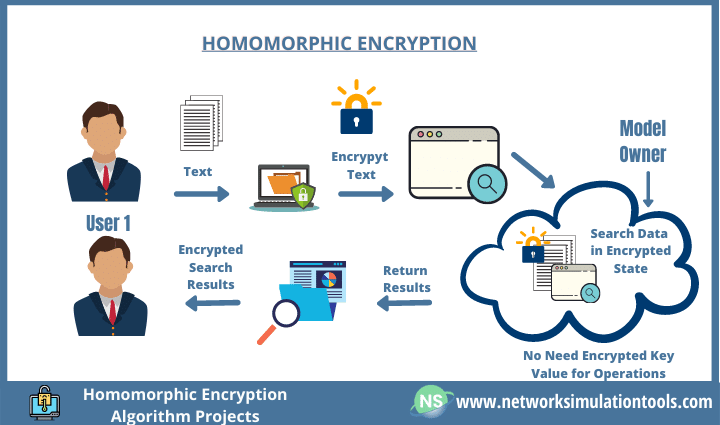














![Fully Homomorphic Encryption (FHE) [26]. | Download Scientific Diagram](https://www.researchgate.net/publication/324692976/figure/fig1/AS:771287425245184@1560900660500/Fully-Homomorphic-Encryption-FHE-26.png)
![Homomorphic Encryption [21] | Download Scientific Diagram](https://www.researchgate.net/profile/Nashwan-Al-Thobhani/publication/355436710/figure/fig7/AS:1086516948410376@1636057235980/Homomorphic-Encryption-21.png)





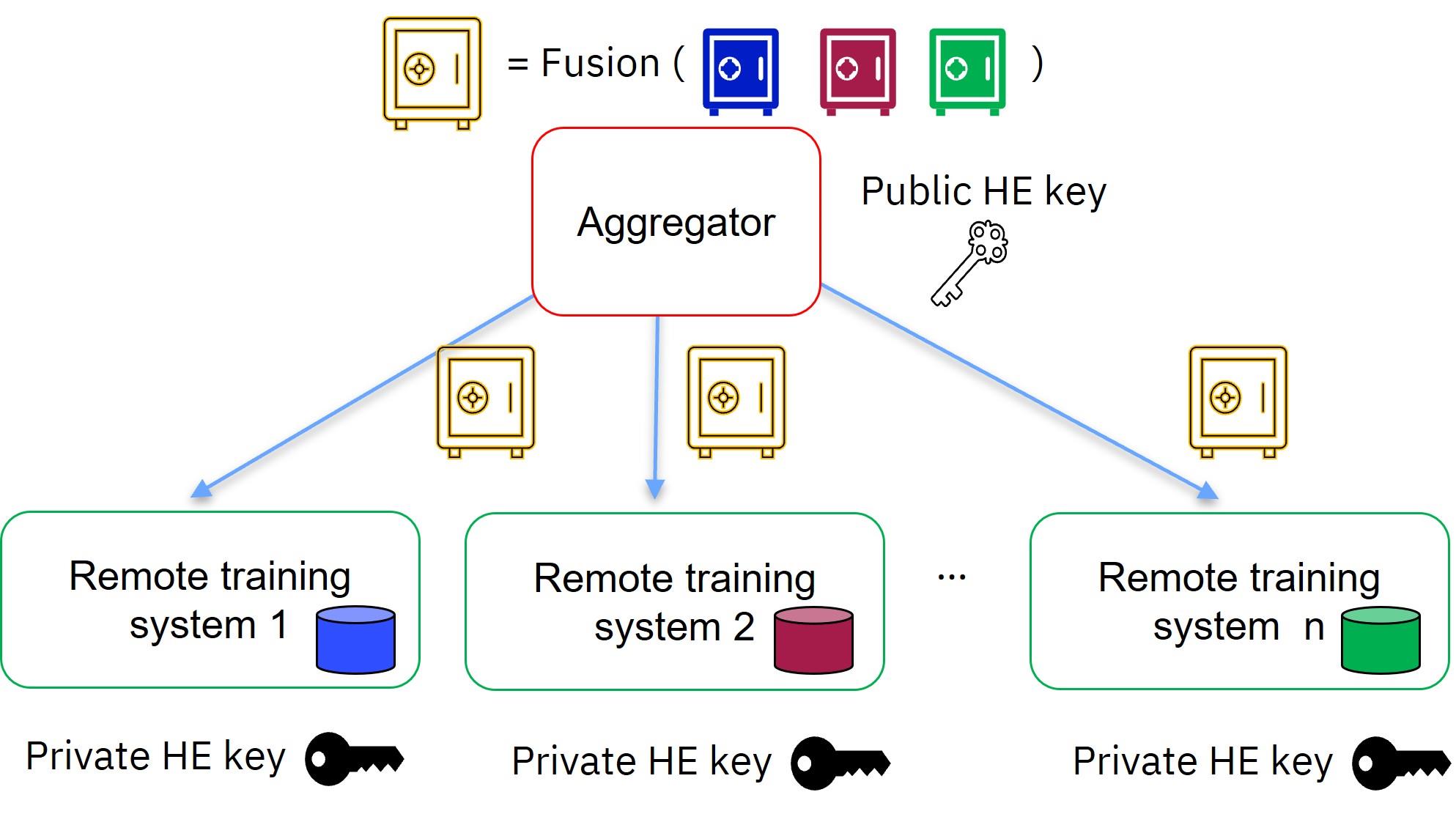
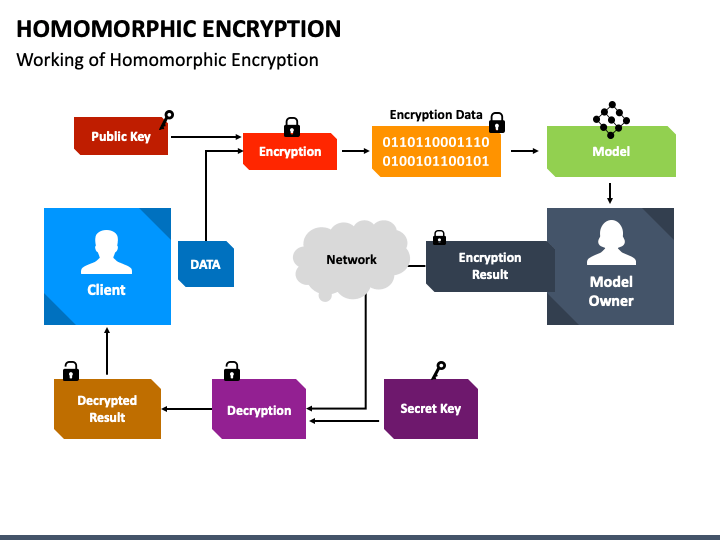
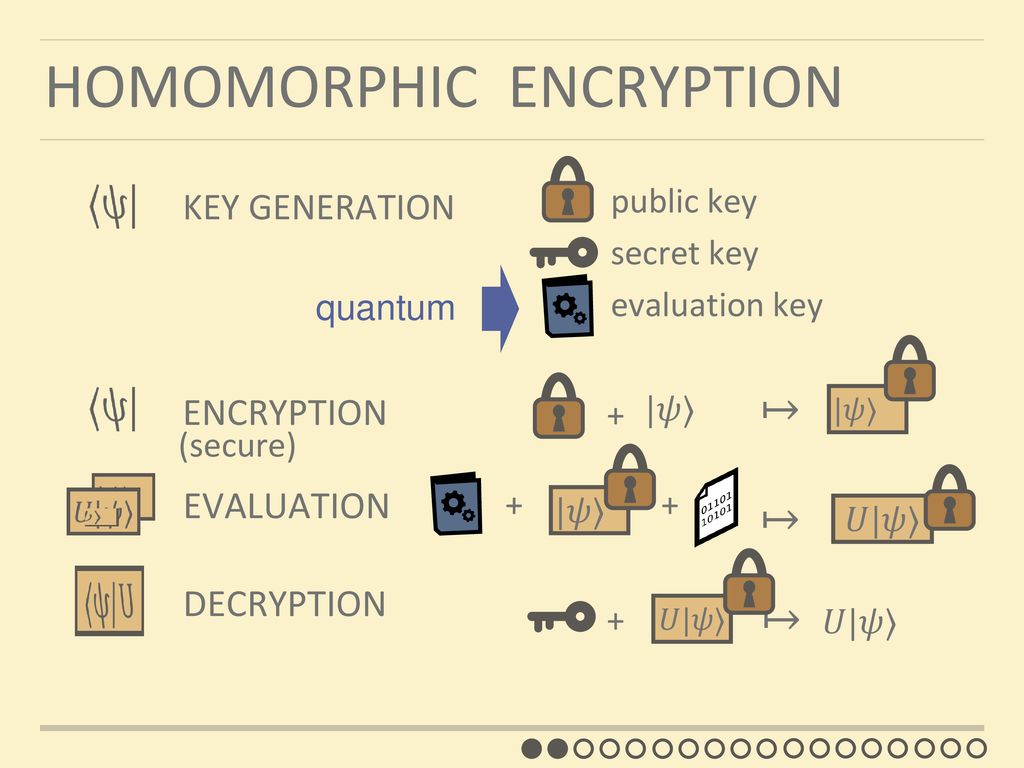

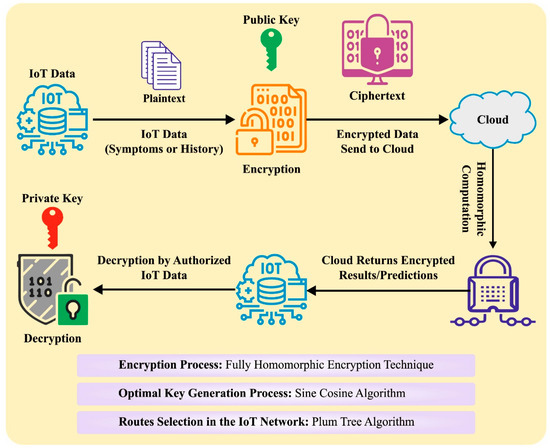








![Homomorphic Encryption Applied to Cloud Computing [17]. | Download ...](https://www.researchgate.net/profile/Kretika-Tiwari/publication/335804064/figure/fig1/AS:802874628009985@1568431636465/Process-Flow_Q320.jpg)