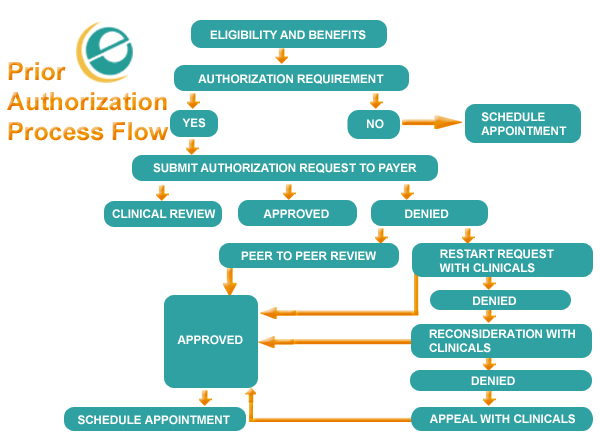
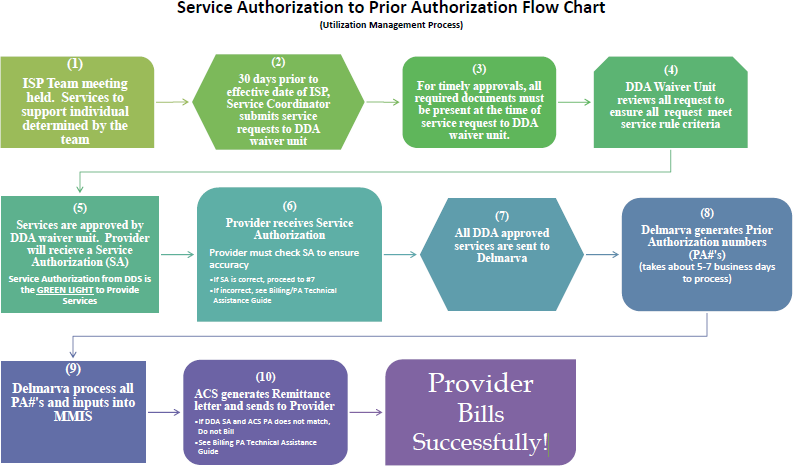
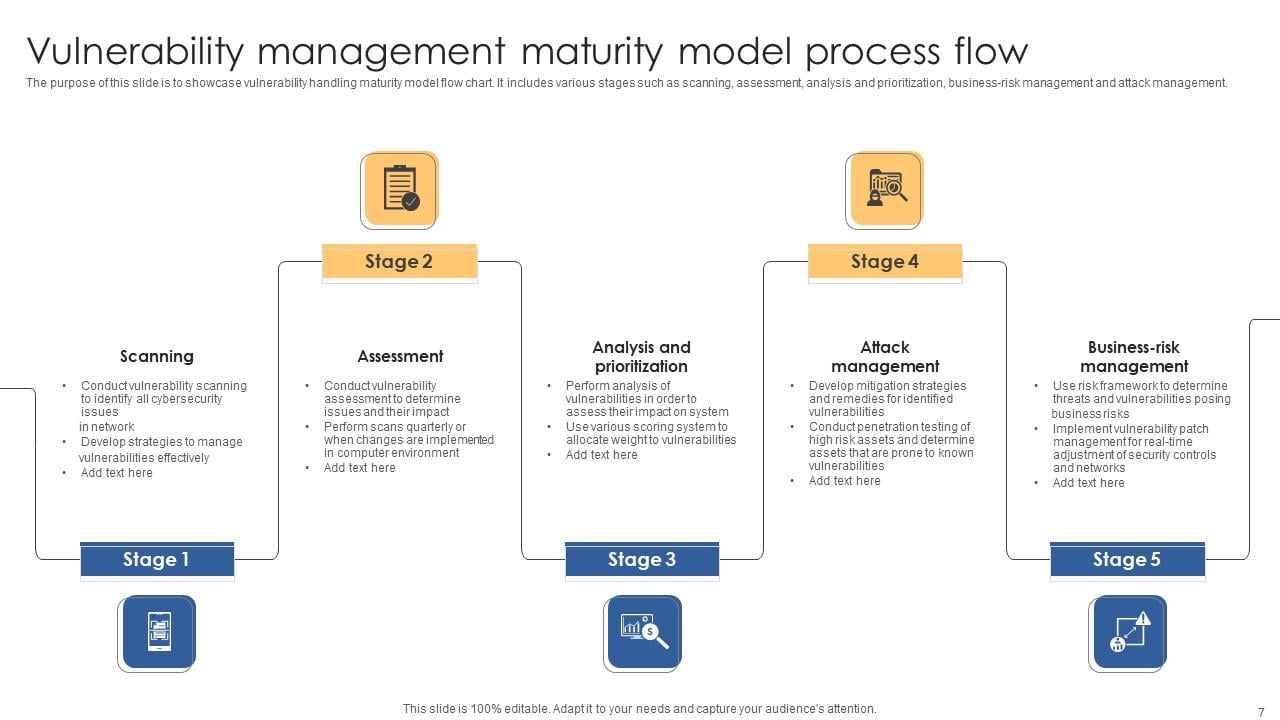
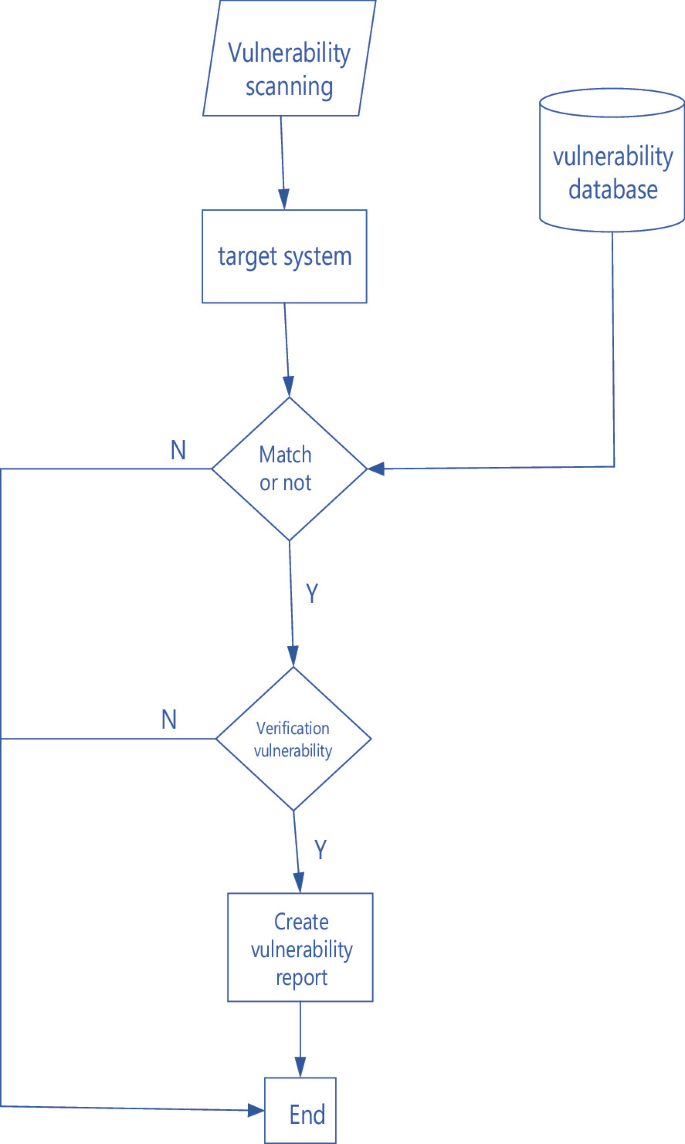
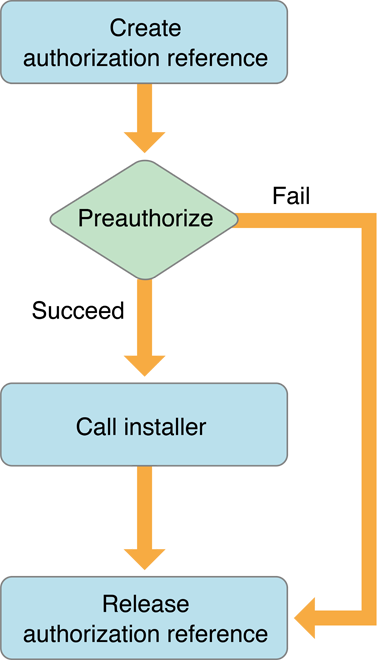
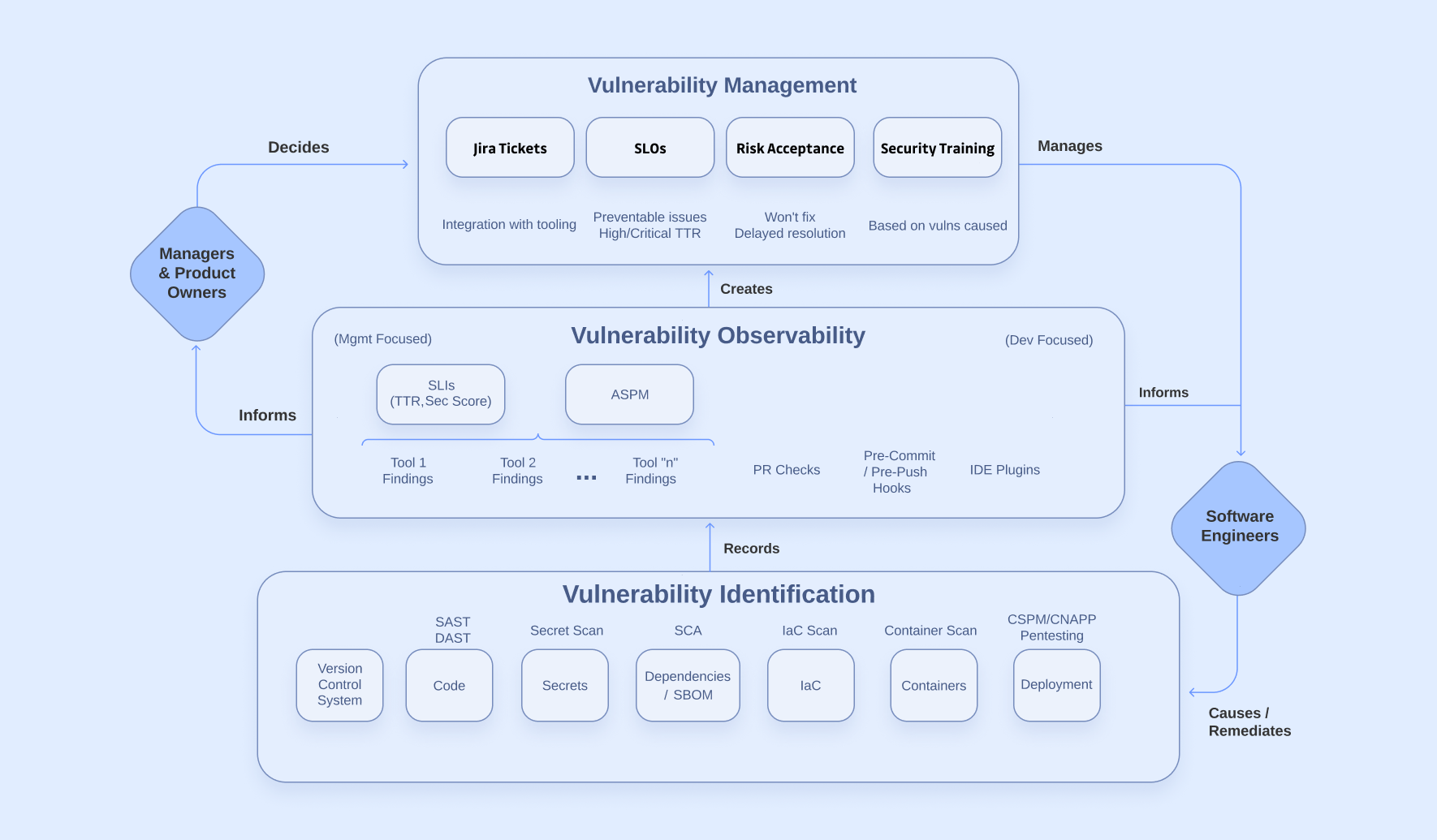
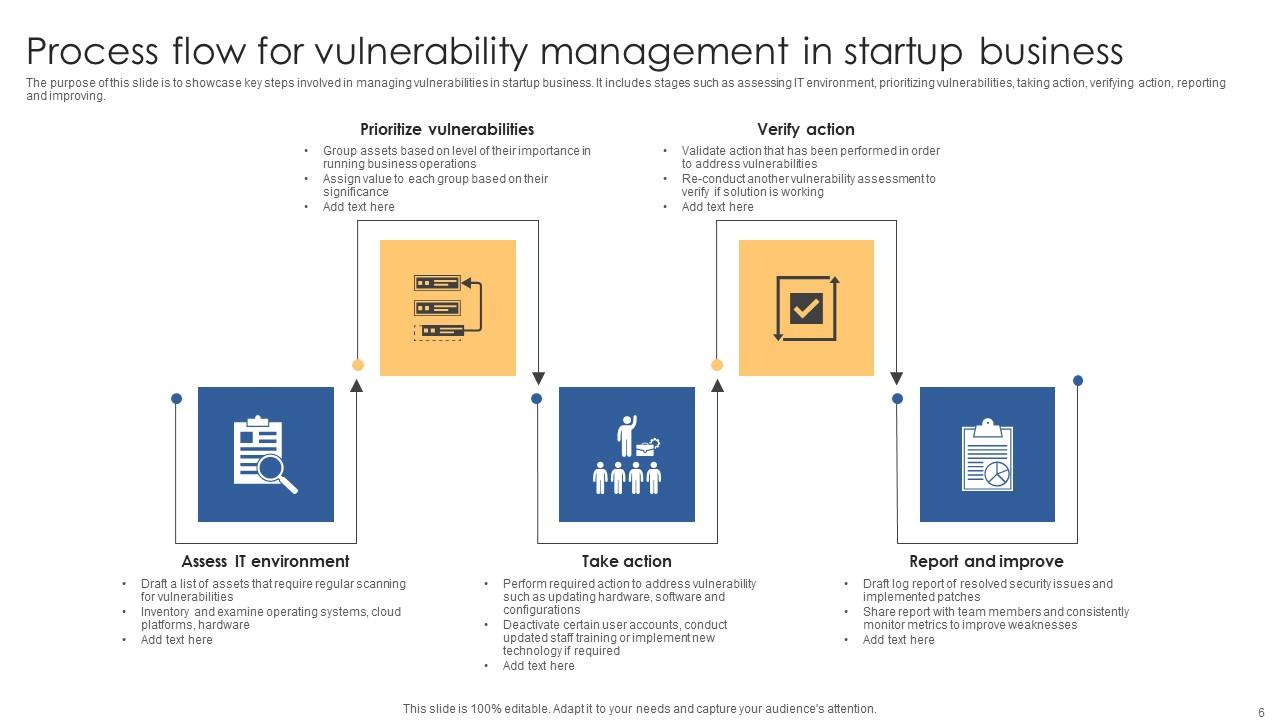
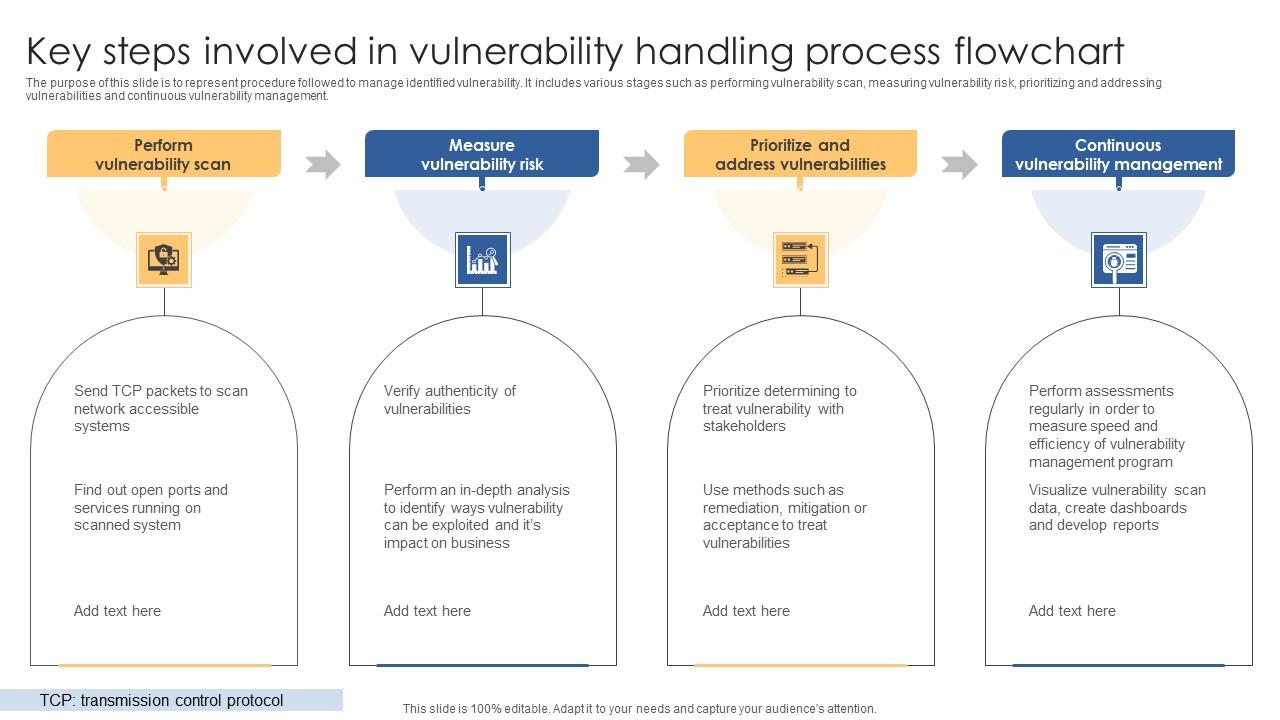
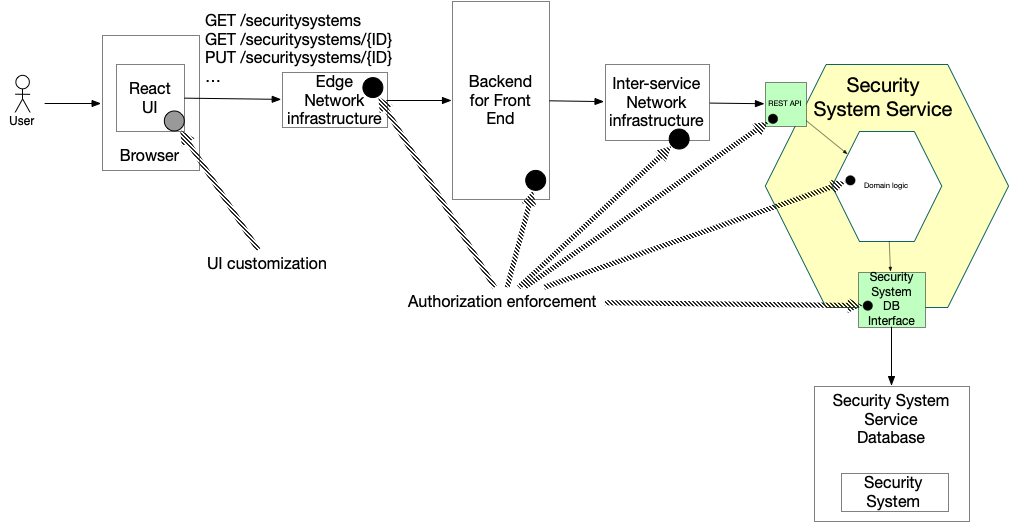
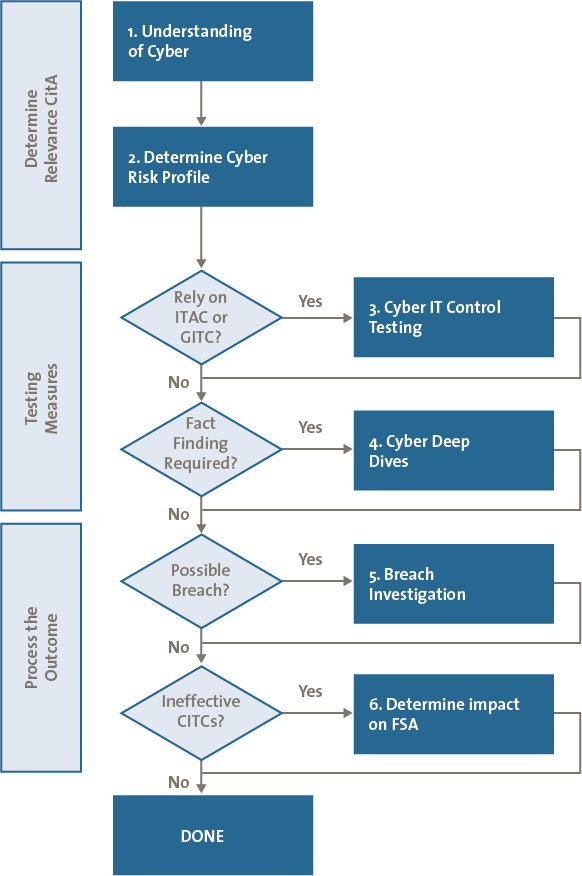
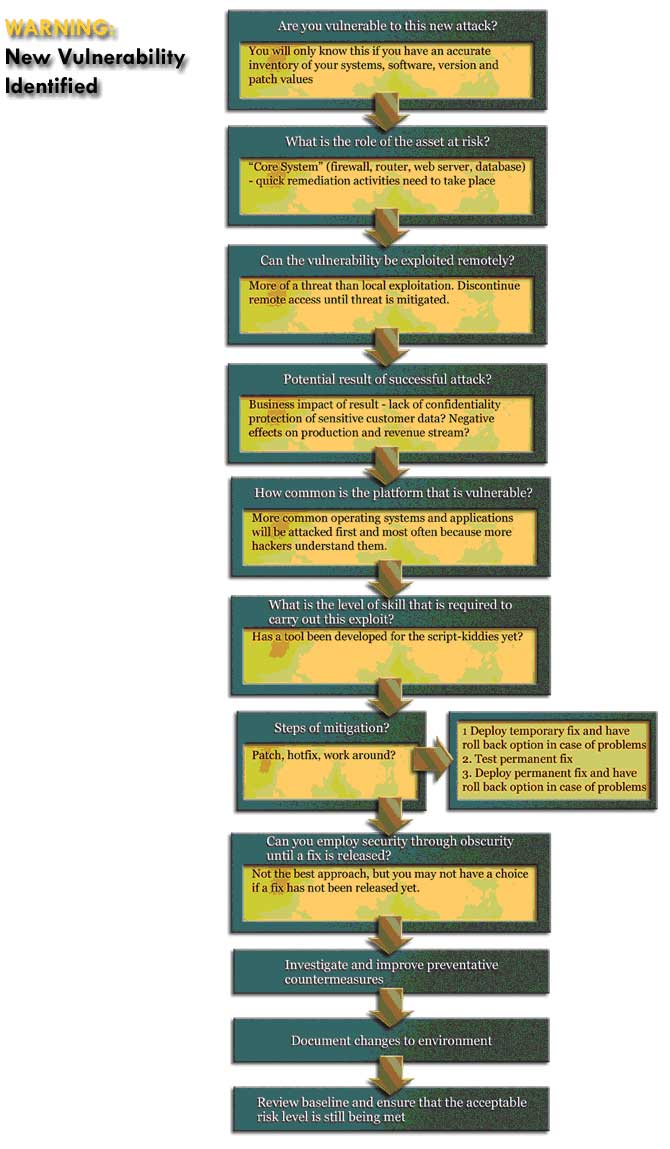
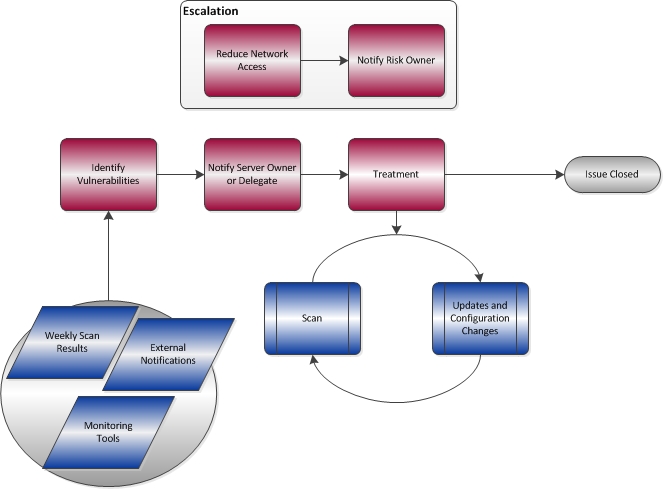
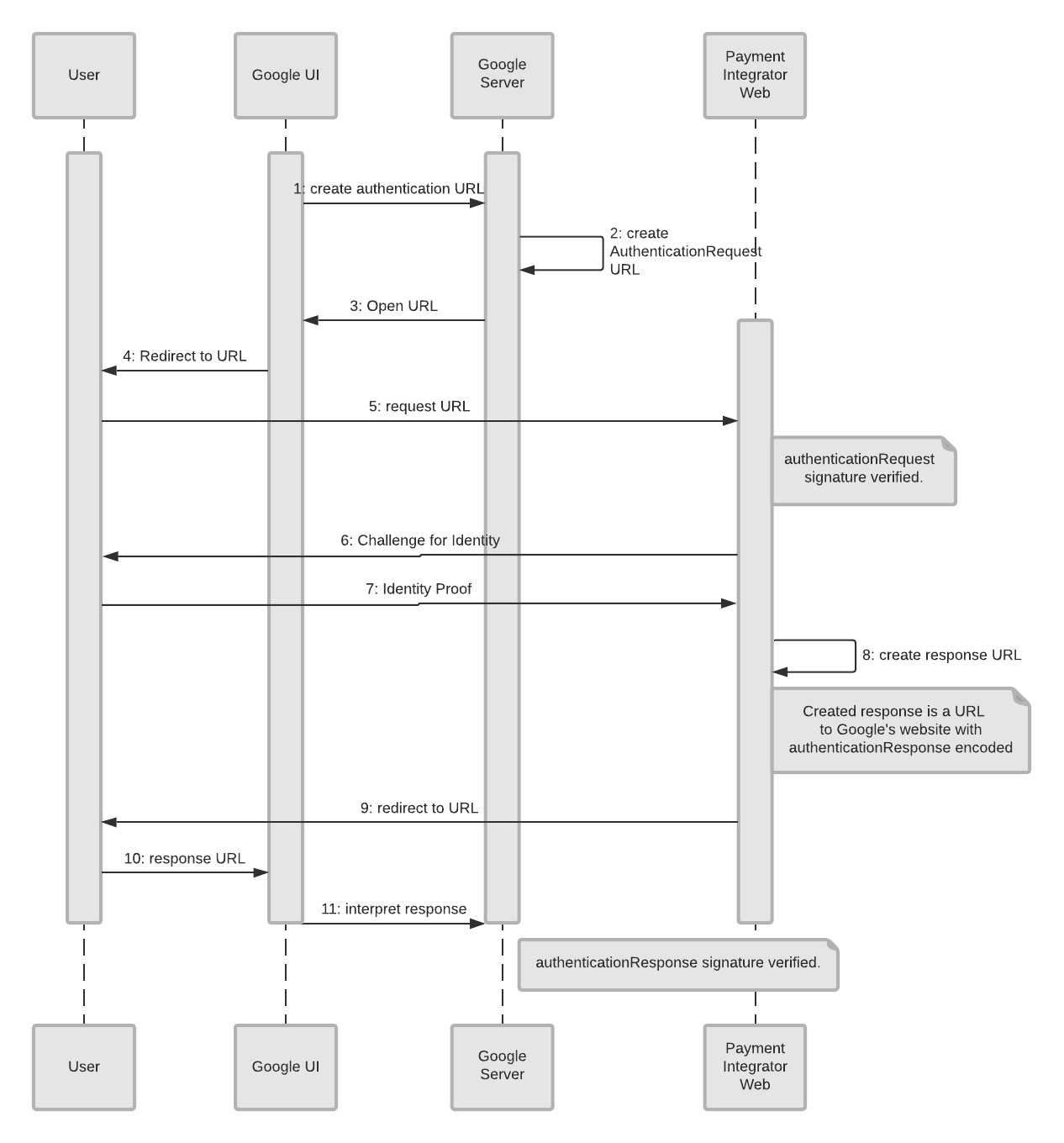
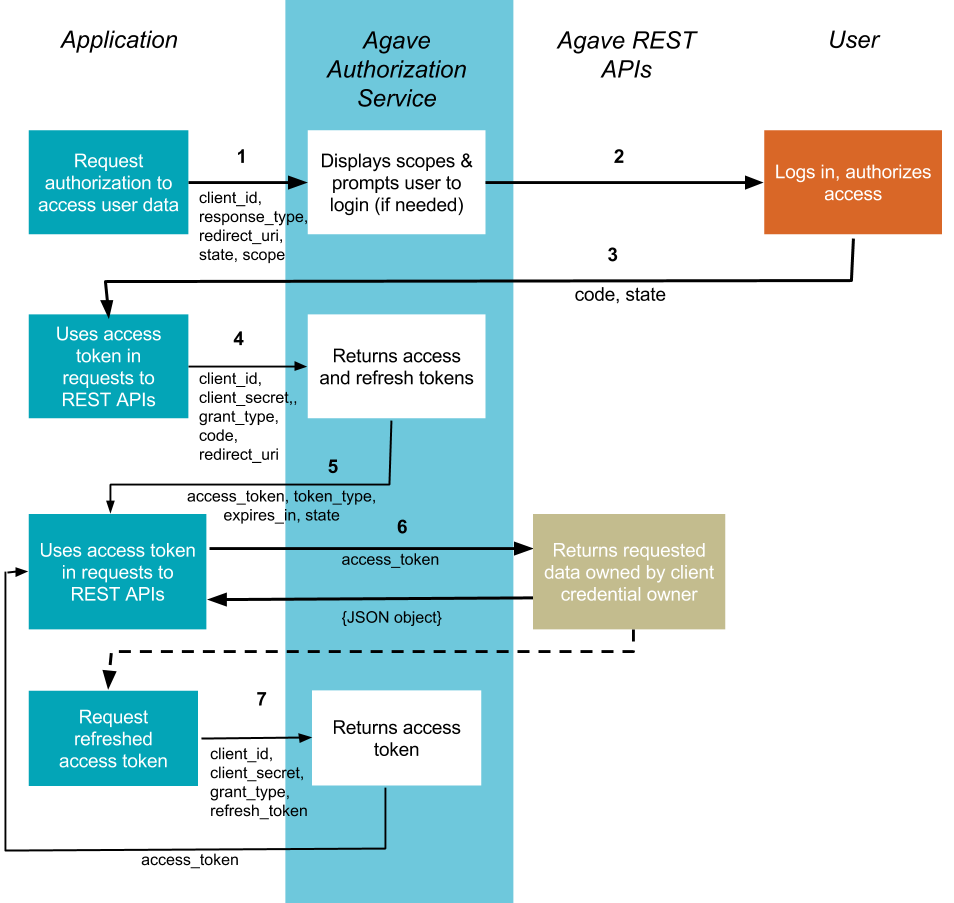
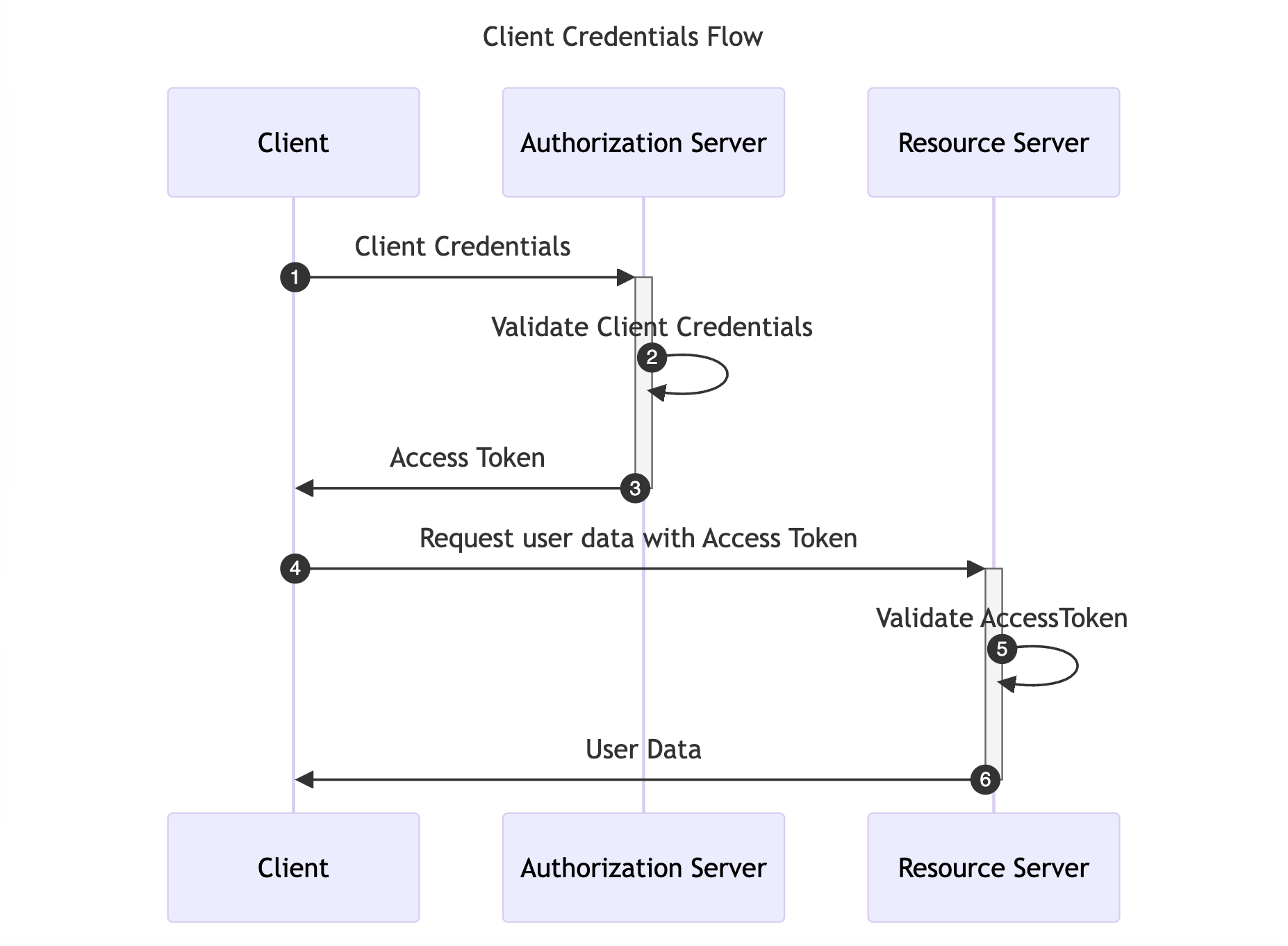
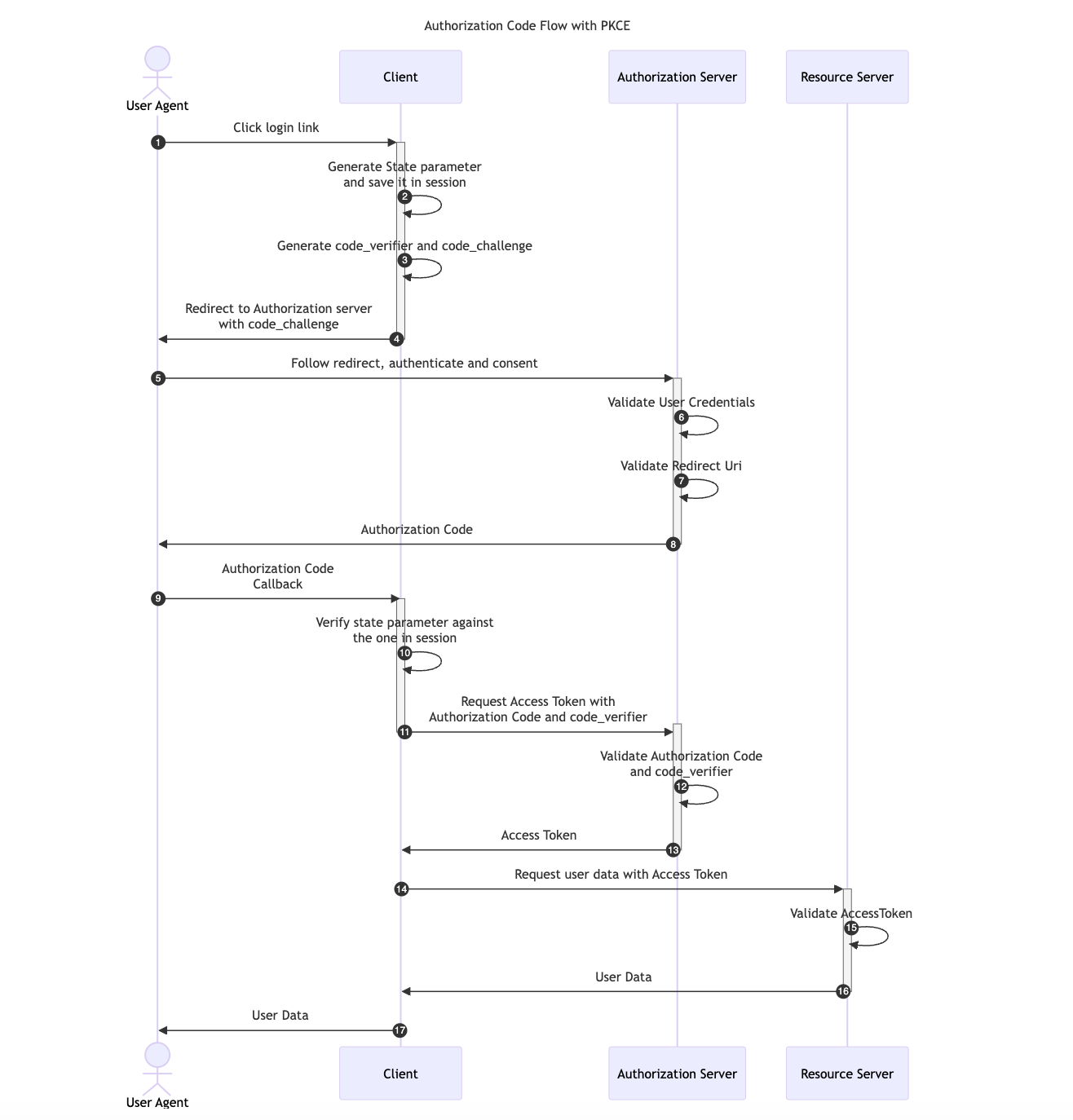
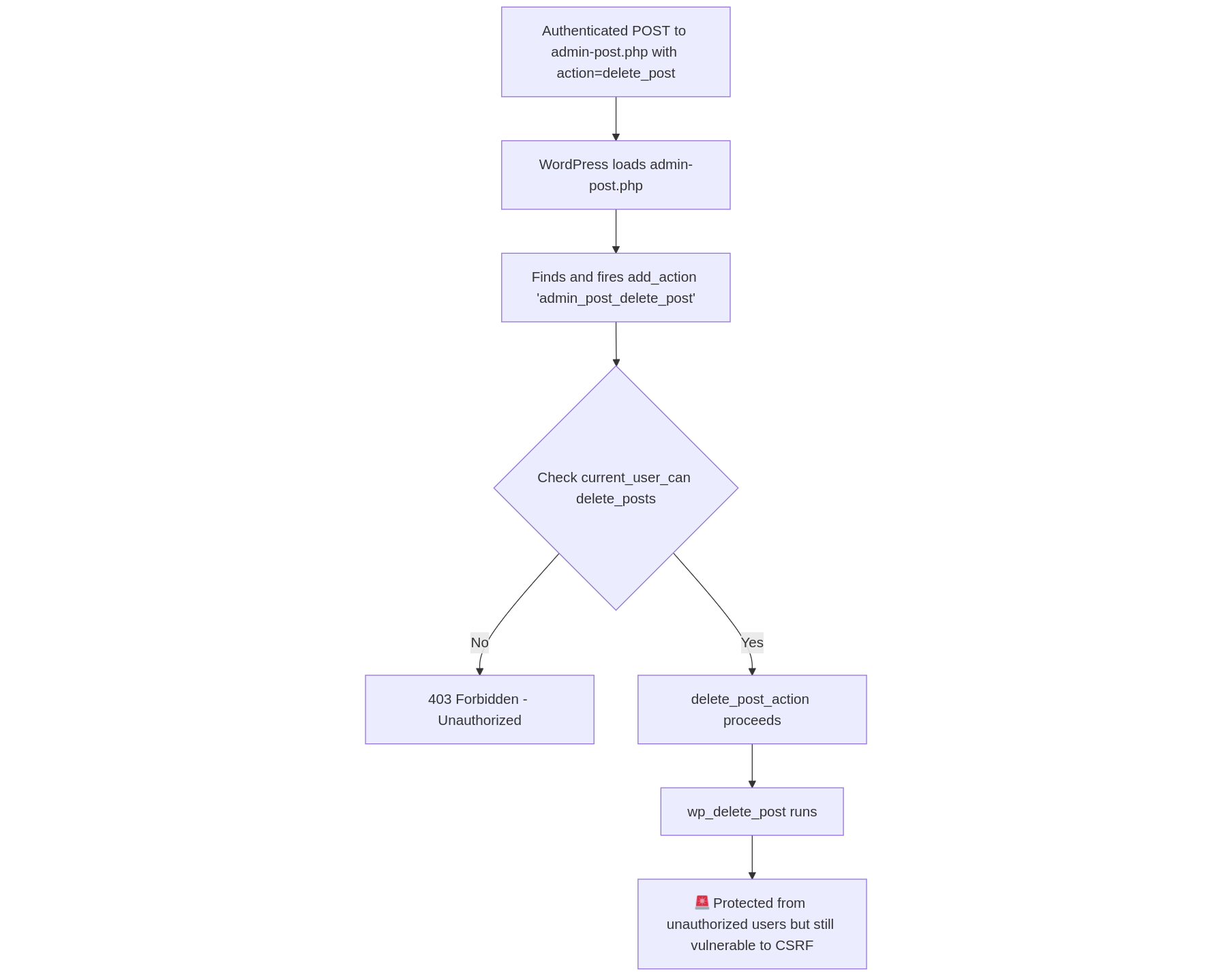
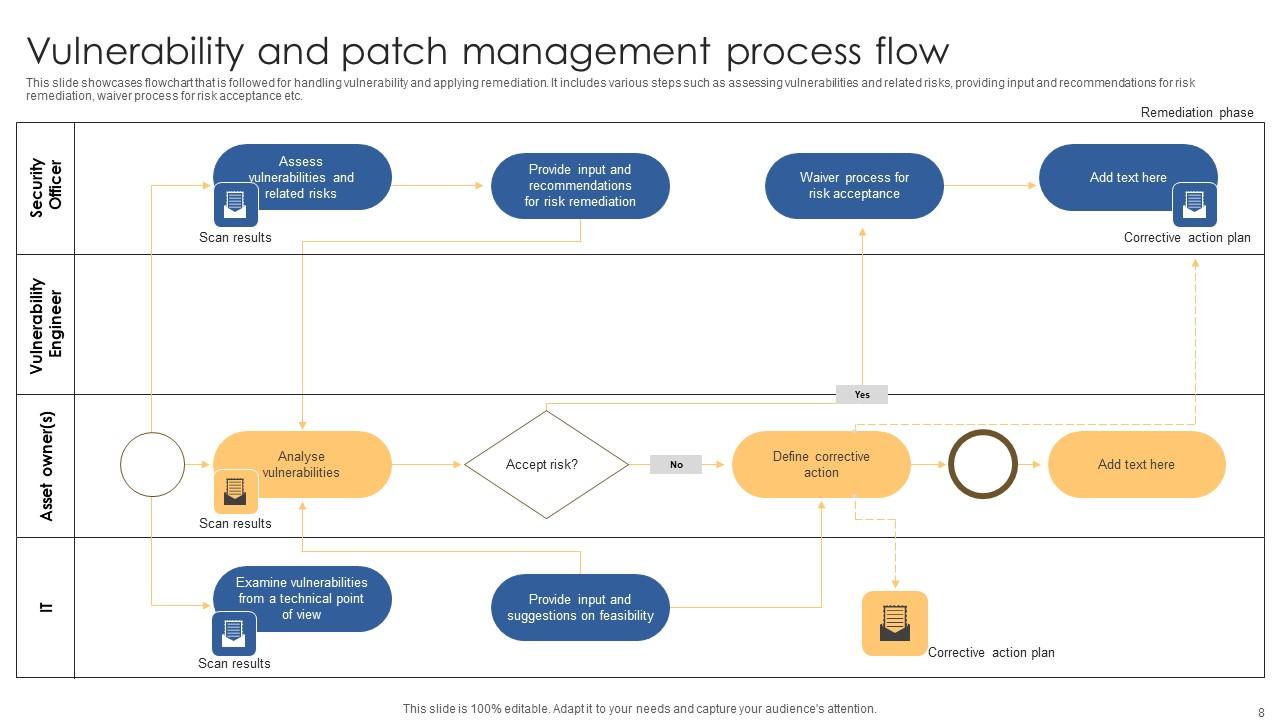
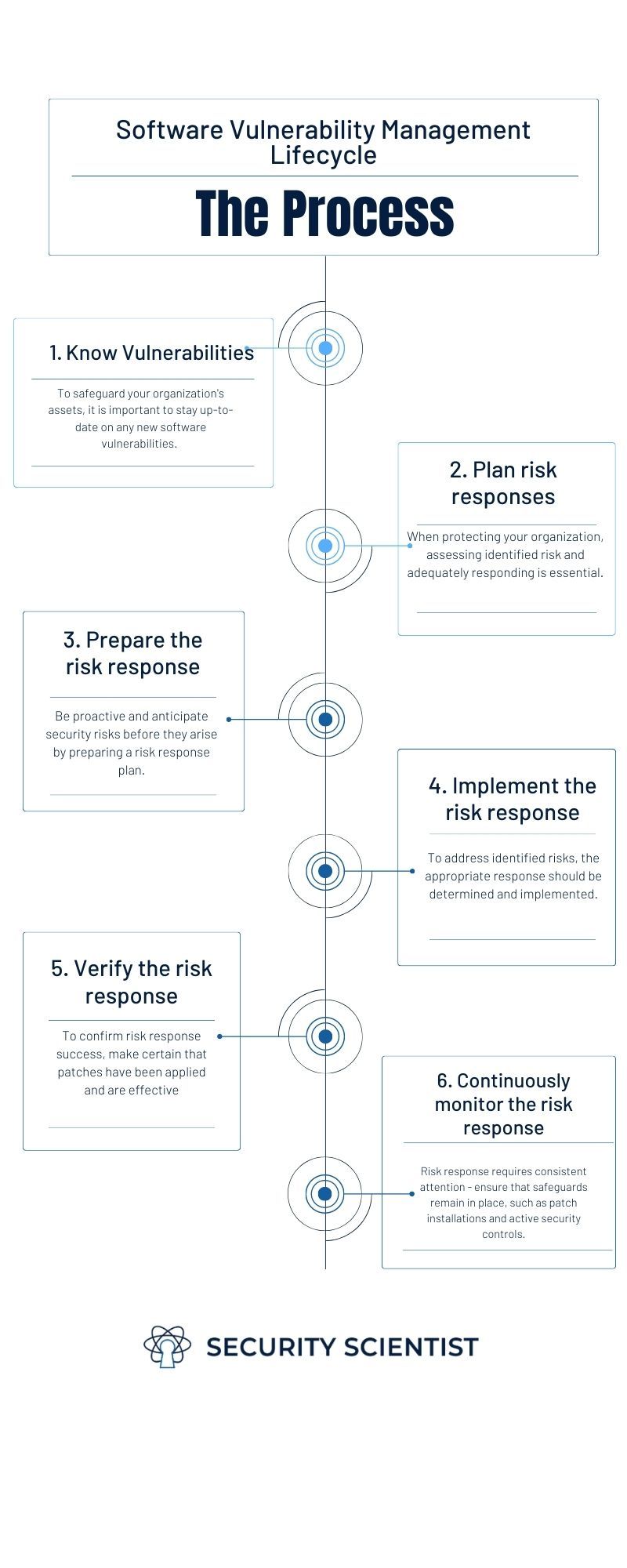
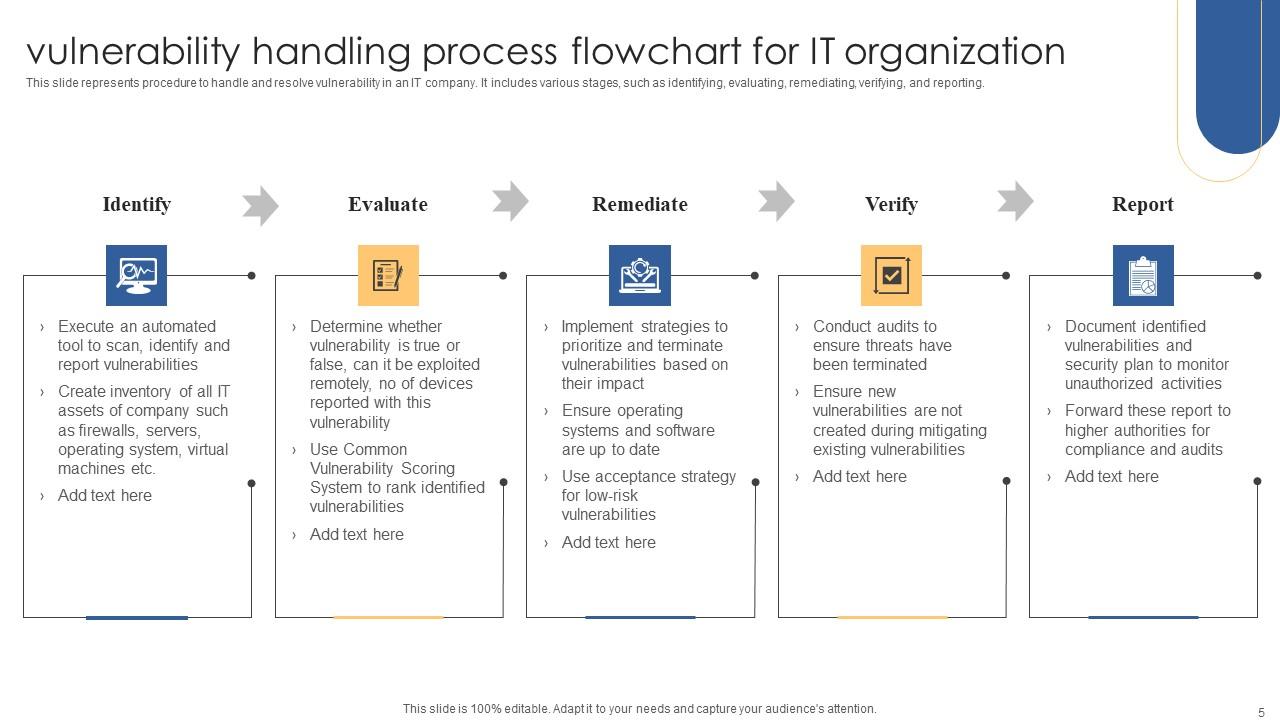
Flow Chart Of Authorization Vulnerability
Our professional Flow Chart Of Authorization Vulnerability collection provides extensive collections of meticulously documented images. optimized for both digital and print applications across multiple platforms. supporting commercial, educational, and research applications. Discover high-resolution Flow Chart Of Authorization Vulnerability images optimized for various applications. Perfect for marketing materials, corporate presentations, advertising campaigns, and professional publications All Flow Chart Of Authorization Vulnerability images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Our Flow Chart Of Authorization Vulnerability collection provides reliable visual resources for business presentations and marketing materials. Cost-effective licensing makes professional Flow Chart Of Authorization Vulnerability photography accessible to all budgets. Our Flow Chart Of Authorization Vulnerability database continuously expands with fresh, relevant content from skilled photographers. Time-saving browsing features help users locate ideal Flow Chart Of Authorization Vulnerability images quickly. Advanced search capabilities make finding the perfect Flow Chart Of Authorization Vulnerability image effortless and efficient. Each image in our Flow Chart Of Authorization Vulnerability gallery undergoes rigorous quality assessment before inclusion. The Flow Chart Of Authorization Vulnerability collection represents years of careful curation and professional standards. Multiple resolution options ensure optimal performance across different platforms and applications.
















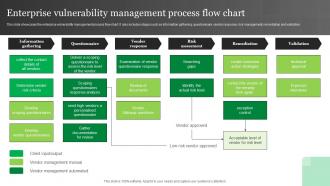



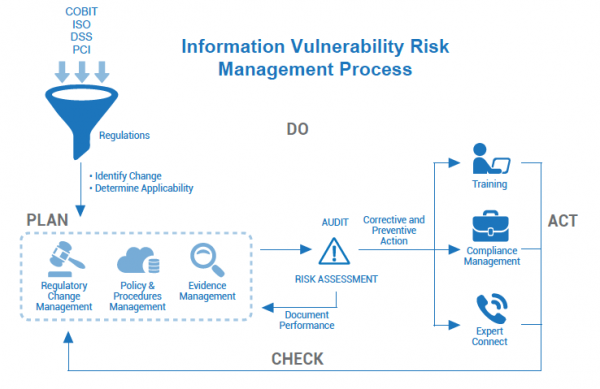









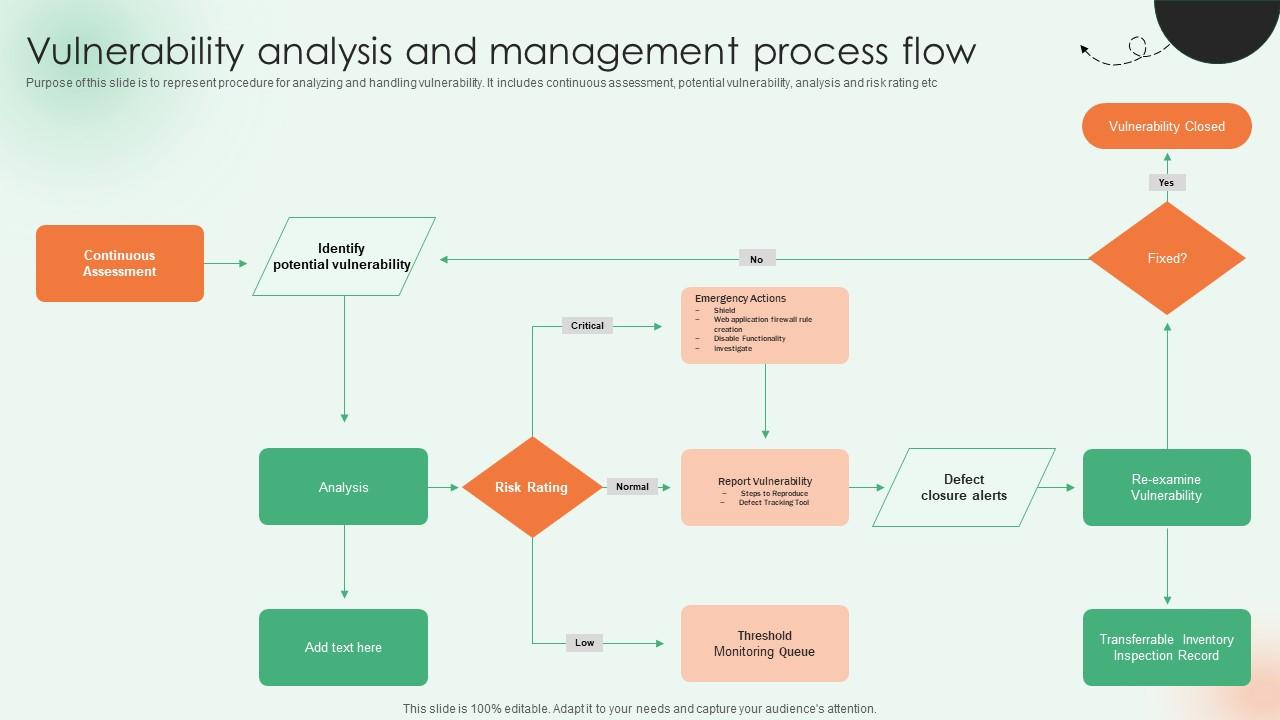
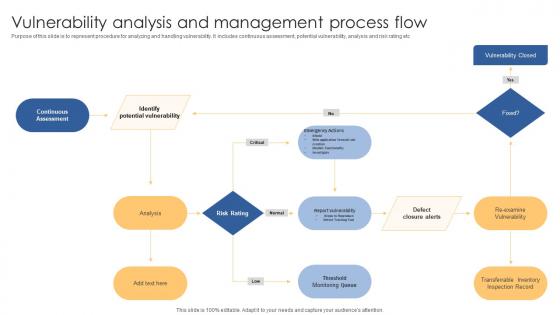



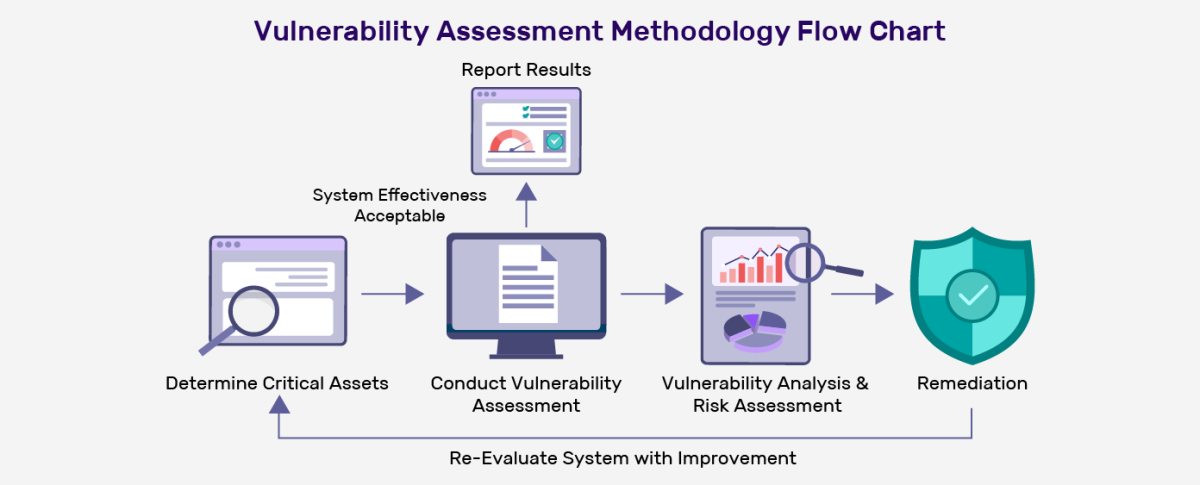










![OAuth authorization flow [8]. | Download Scientific Diagram](https://www.researchgate.net/publication/352391149/figure/fig1/AS:1034806368415744@1623728472100/OAuth-authorization-flow-8_Q640.jpg)








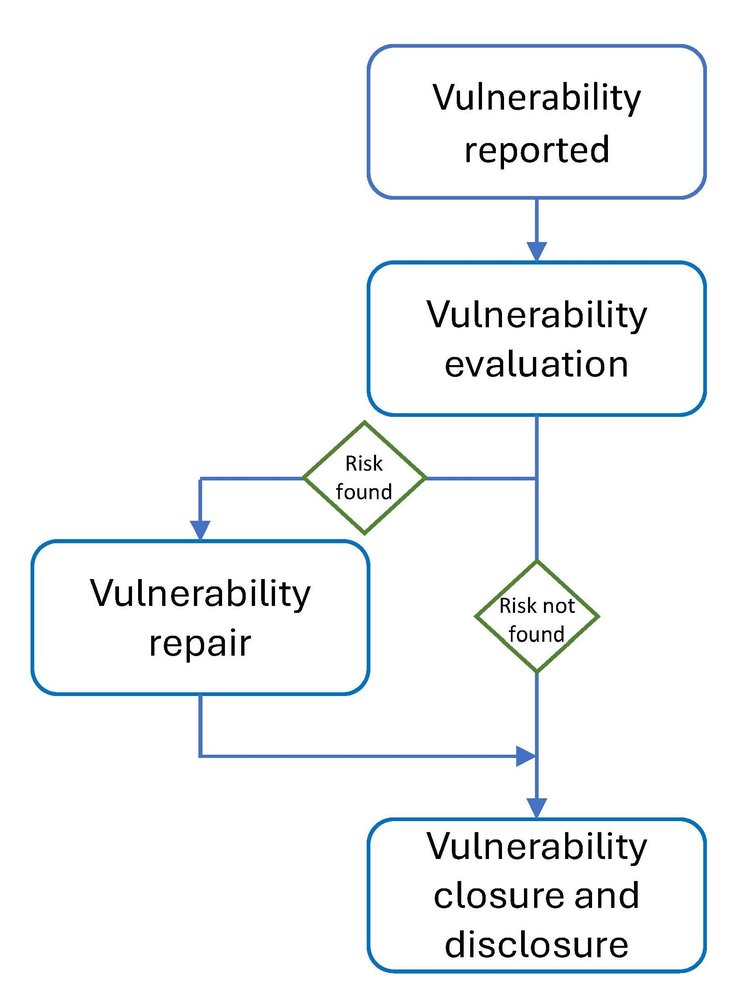



![The Ultimate Guide to B2B Vulnerability [Includes Flowchart]](https://www.tales.co.nz/wp-content/uploads/sites/62/2022/12/flowchart-600x1024.jpg)