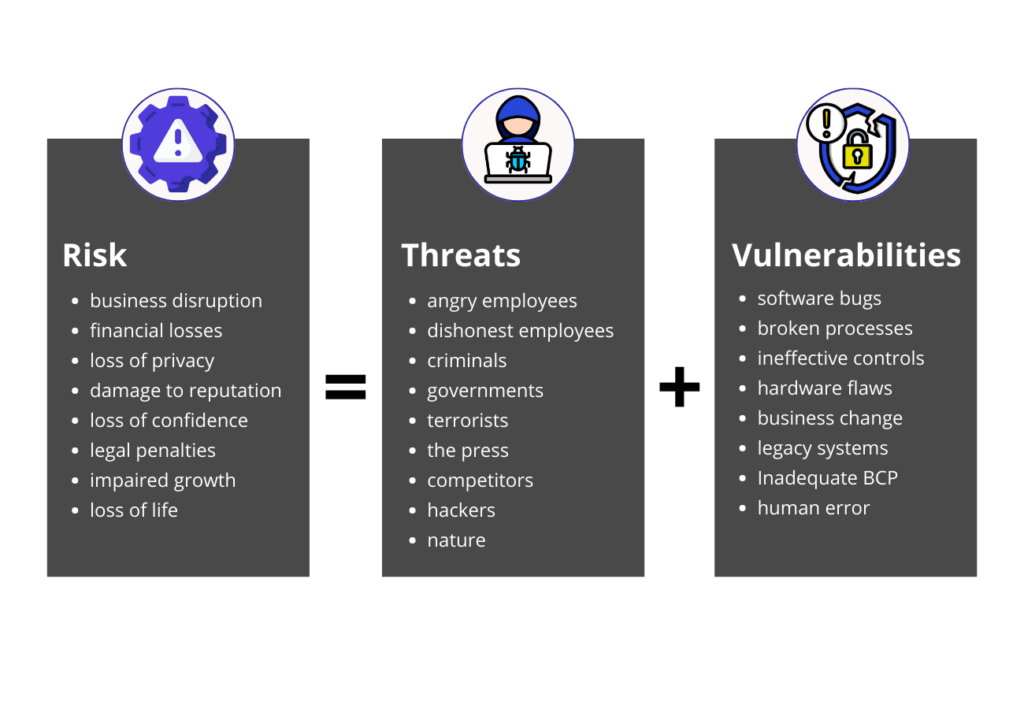
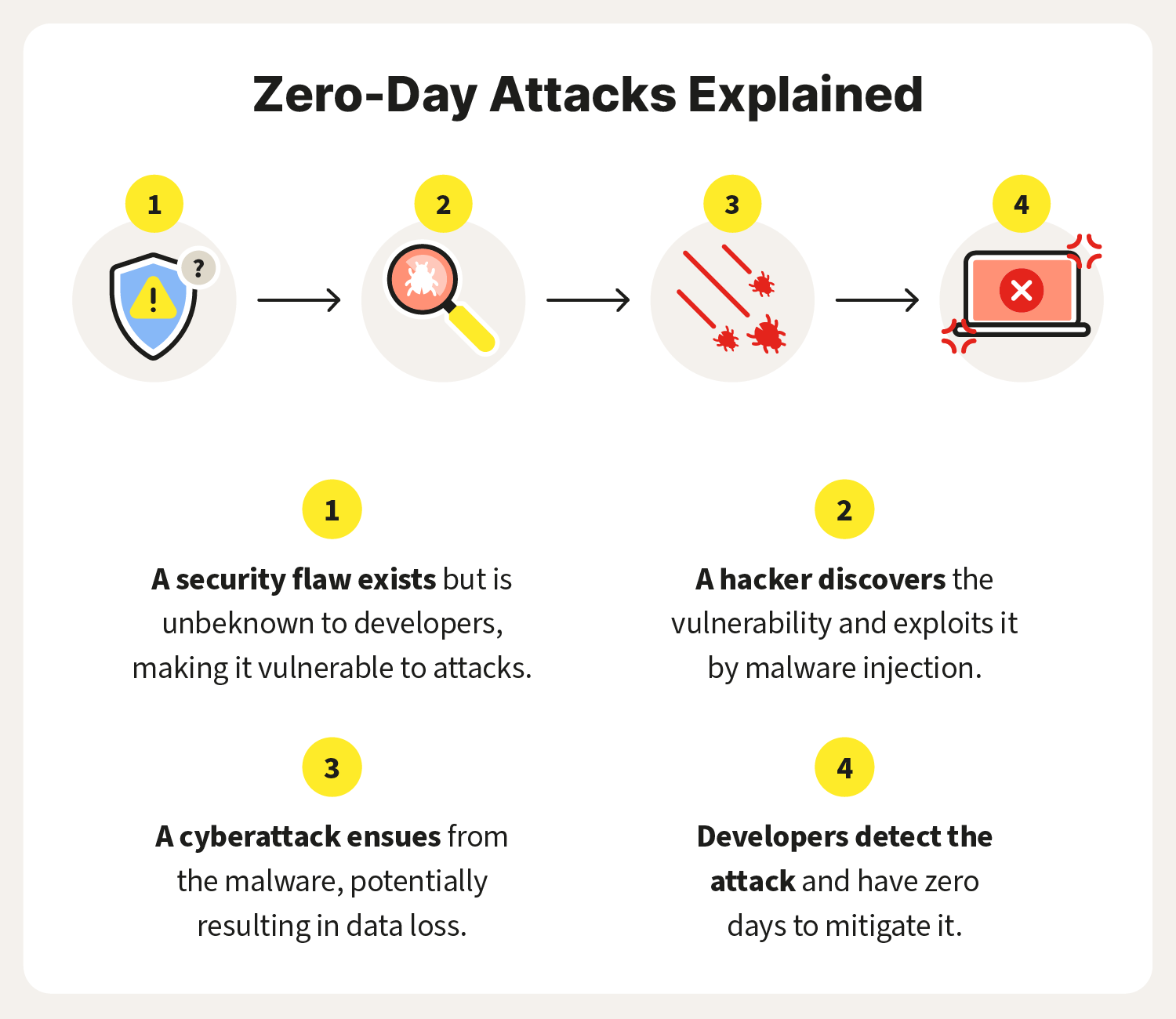
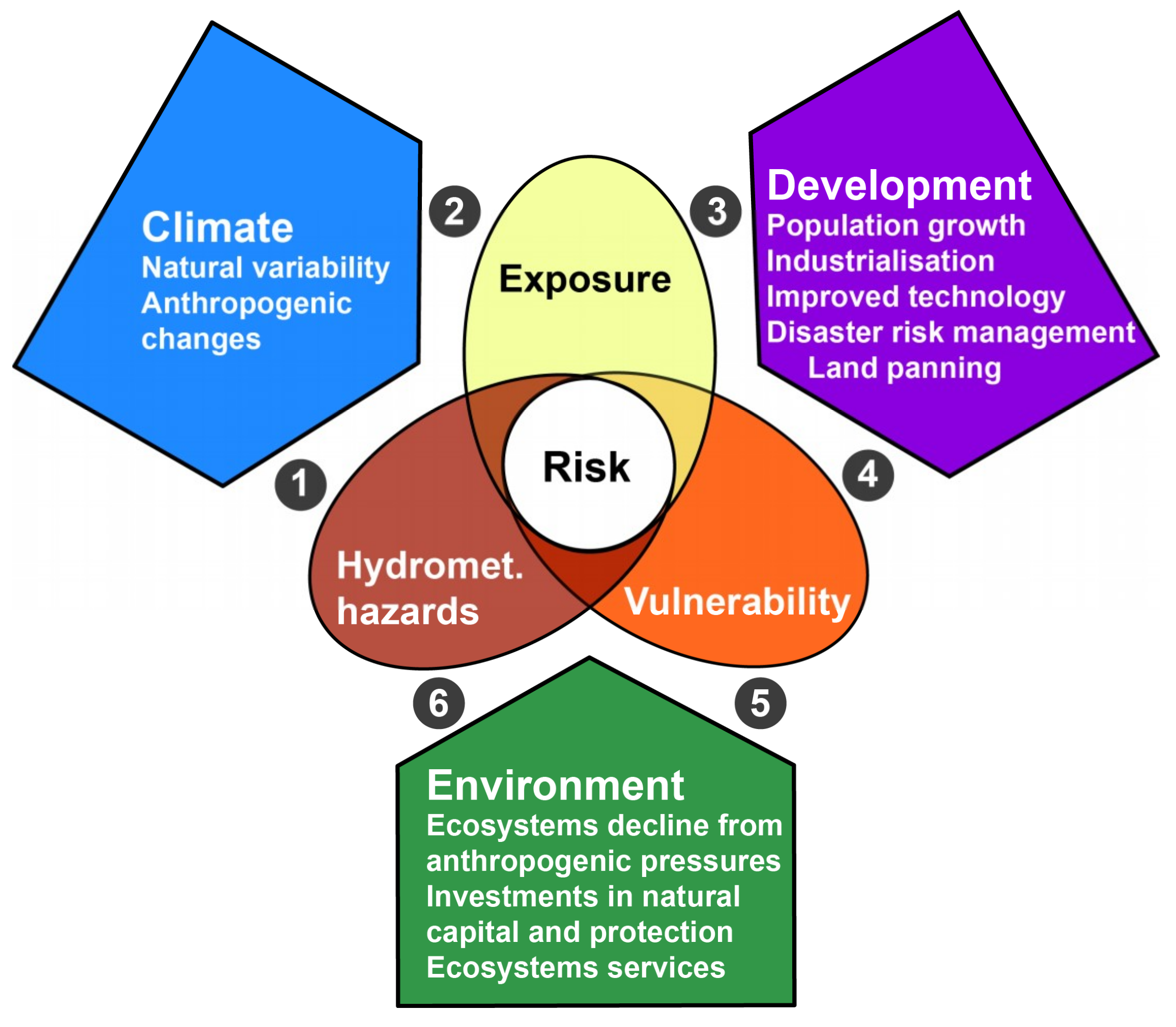
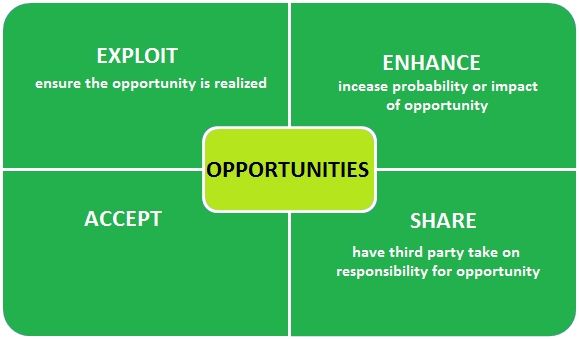
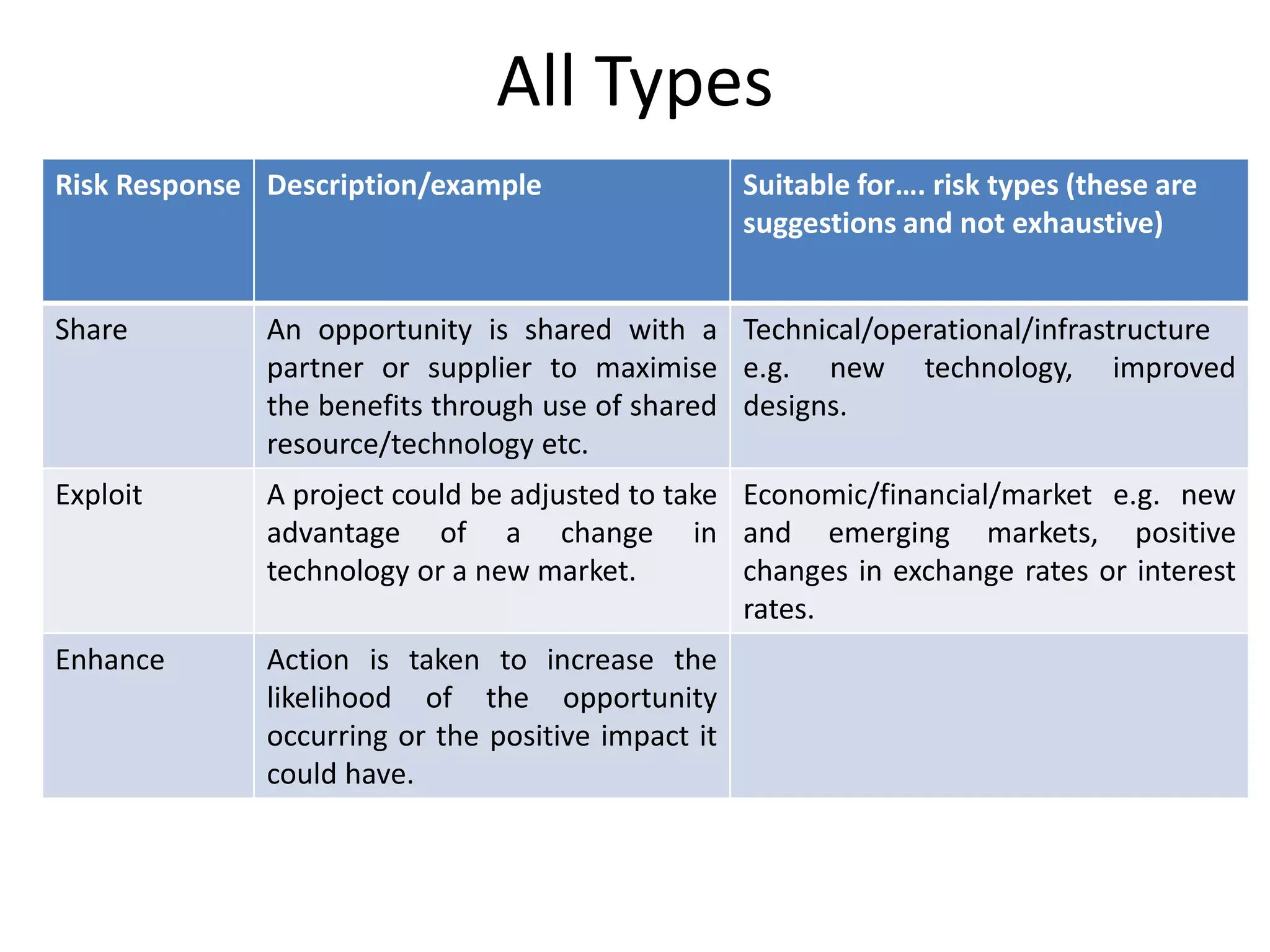
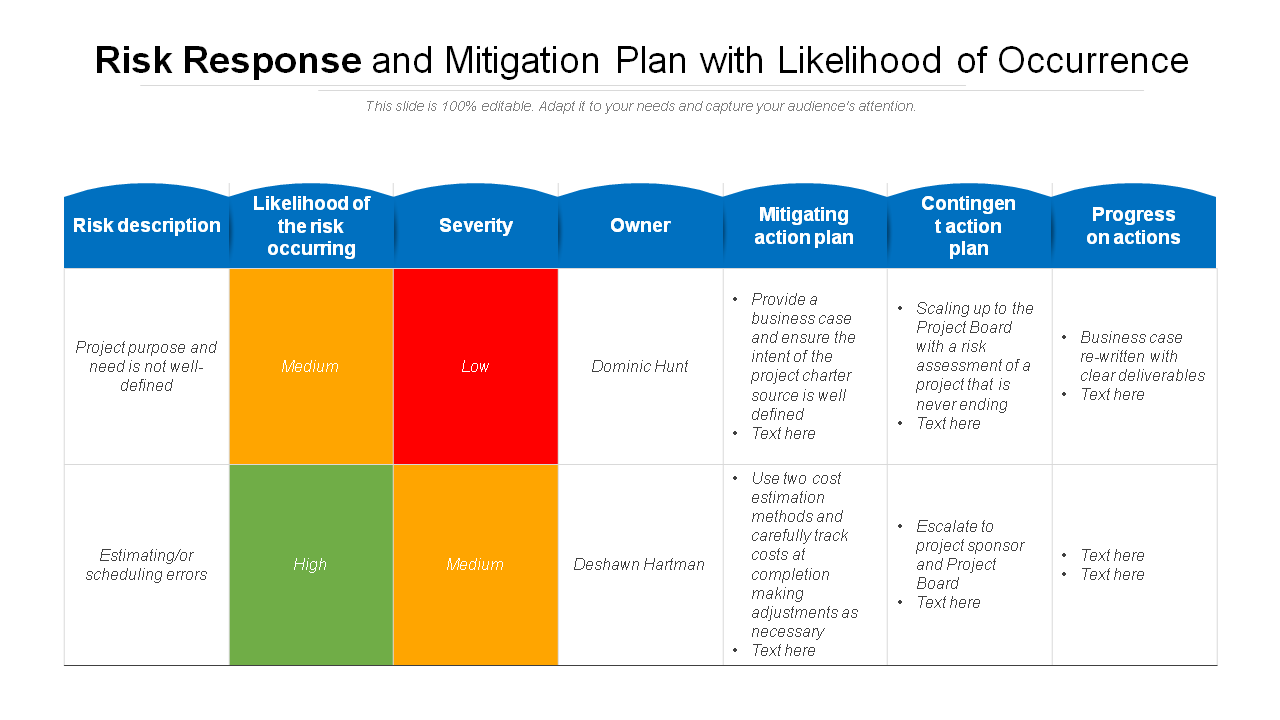
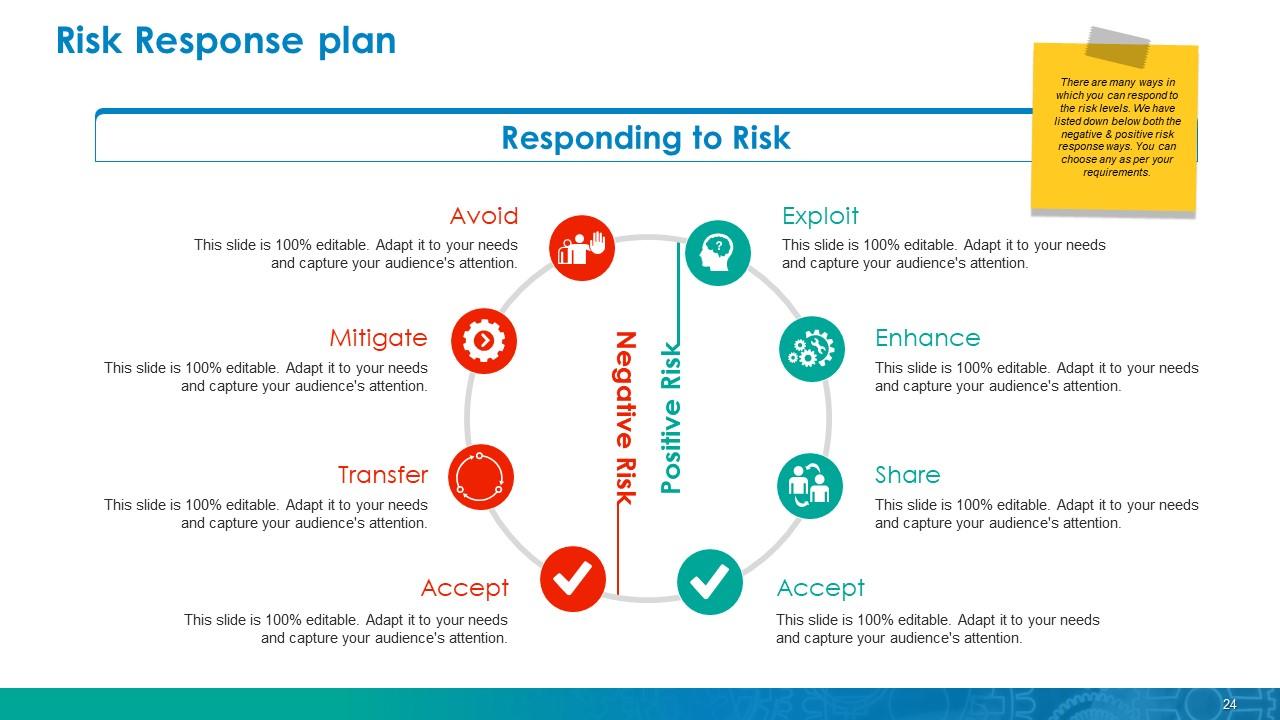
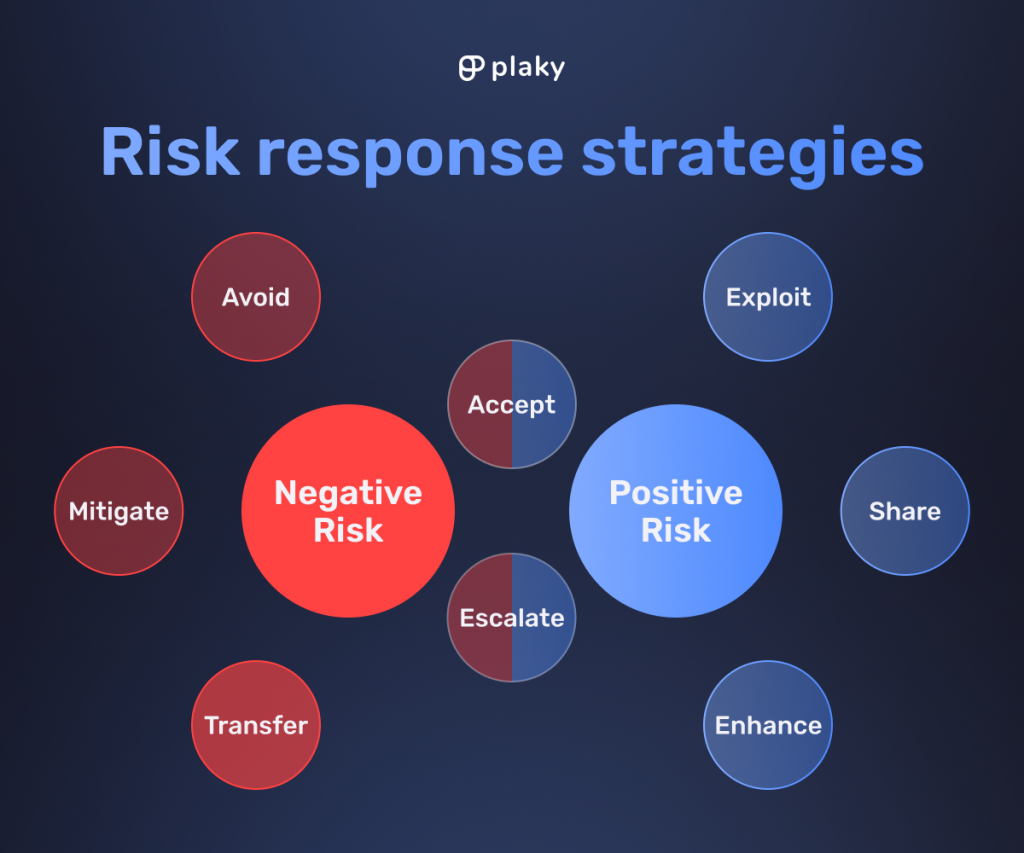
Exploit Risk Response
Drive innovation with our technology Exploit Risk Response gallery of extensive collections of digital images. technologically showcasing photography, images, and pictures. ideal for innovation showcases and presentations. Browse our premium Exploit Risk Response gallery featuring professionally curated photographs. Suitable for various applications including web design, social media, personal projects, and digital content creation All Exploit Risk Response images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Explore the versatility of our Exploit Risk Response collection for various creative and professional projects. Reliable customer support ensures smooth experience throughout the Exploit Risk Response selection process. Cost-effective licensing makes professional Exploit Risk Response photography accessible to all budgets. Regular updates keep the Exploit Risk Response collection current with contemporary trends and styles. Advanced search capabilities make finding the perfect Exploit Risk Response image effortless and efficient. Our Exploit Risk Response database continuously expands with fresh, relevant content from skilled photographers. Diverse style options within the Exploit Risk Response collection suit various aesthetic preferences. The Exploit Risk Response collection represents years of careful curation and professional standards. The Exploit Risk Response archive serves professionals, educators, and creatives across diverse industries.







































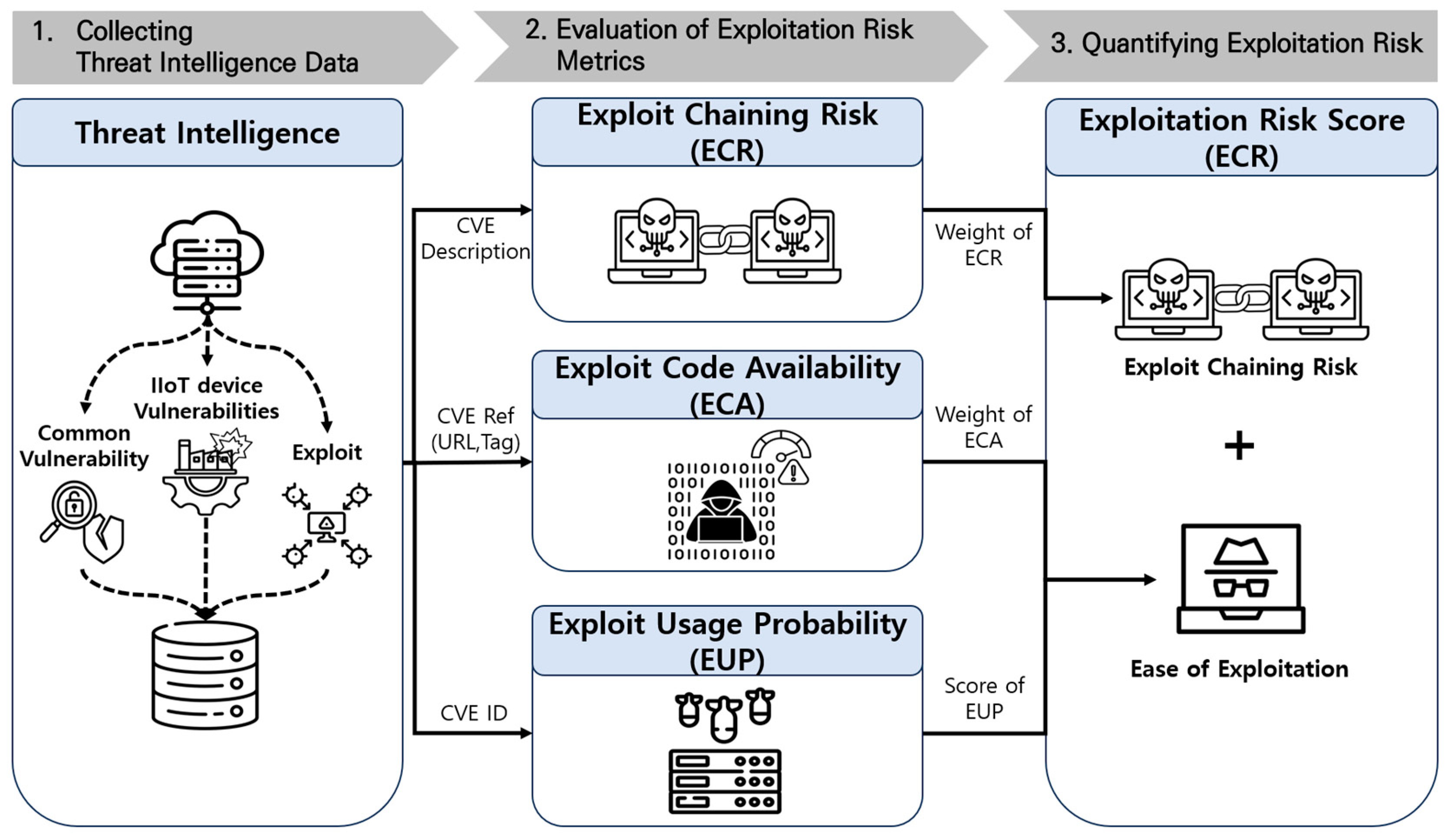
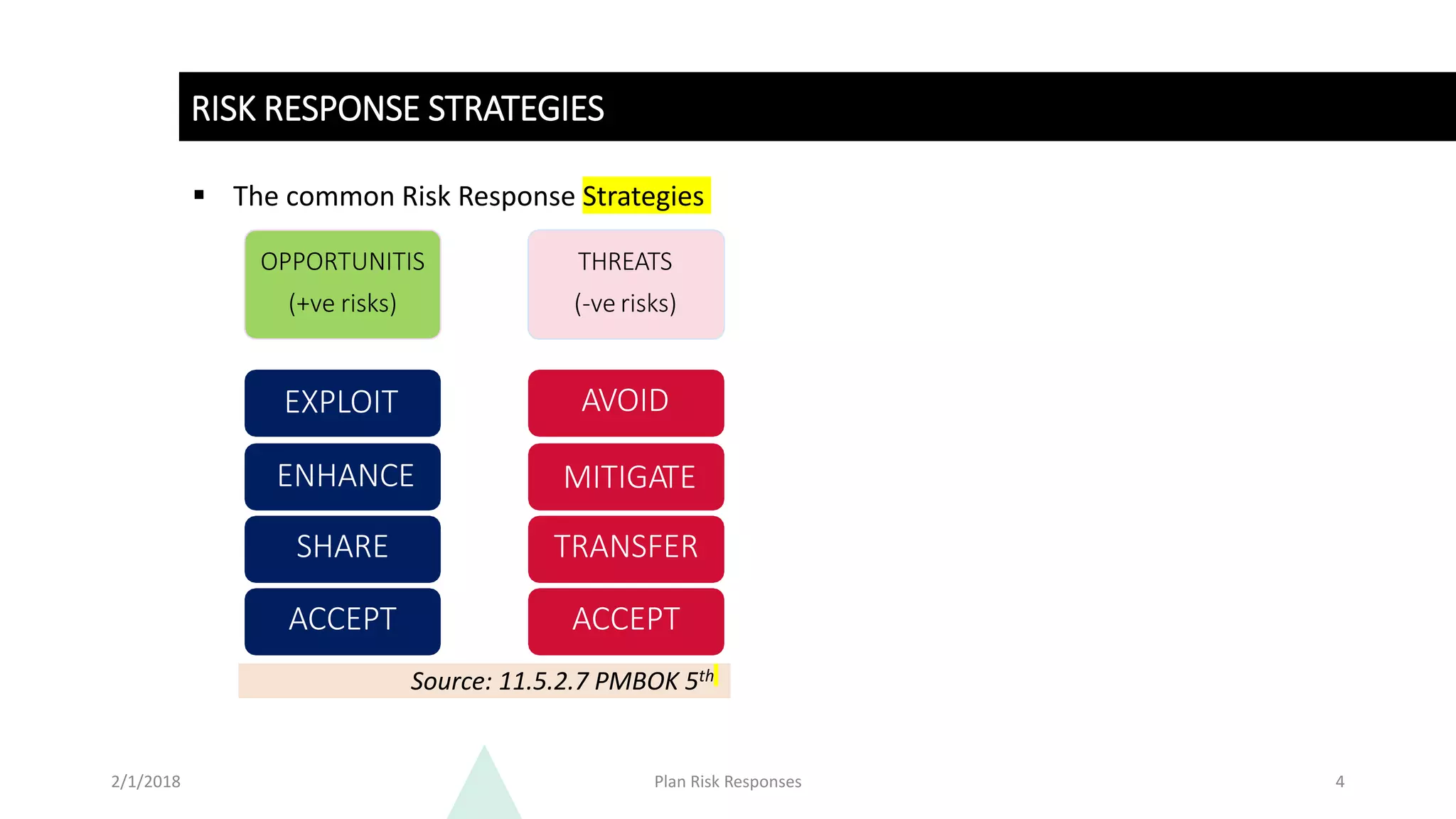


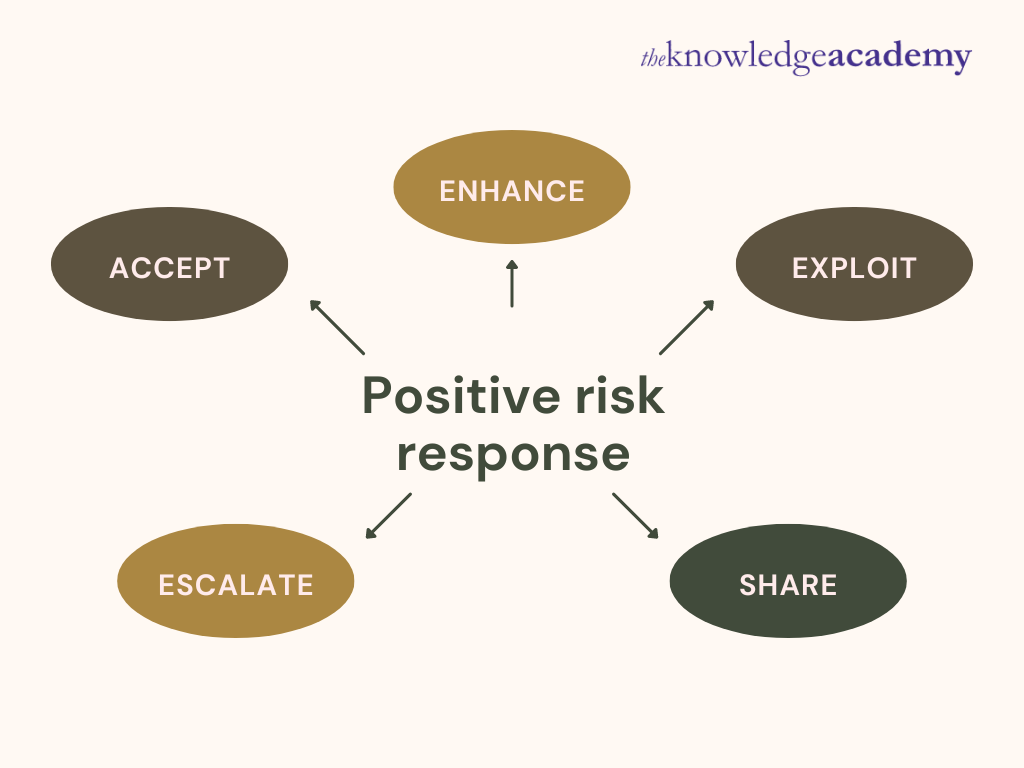

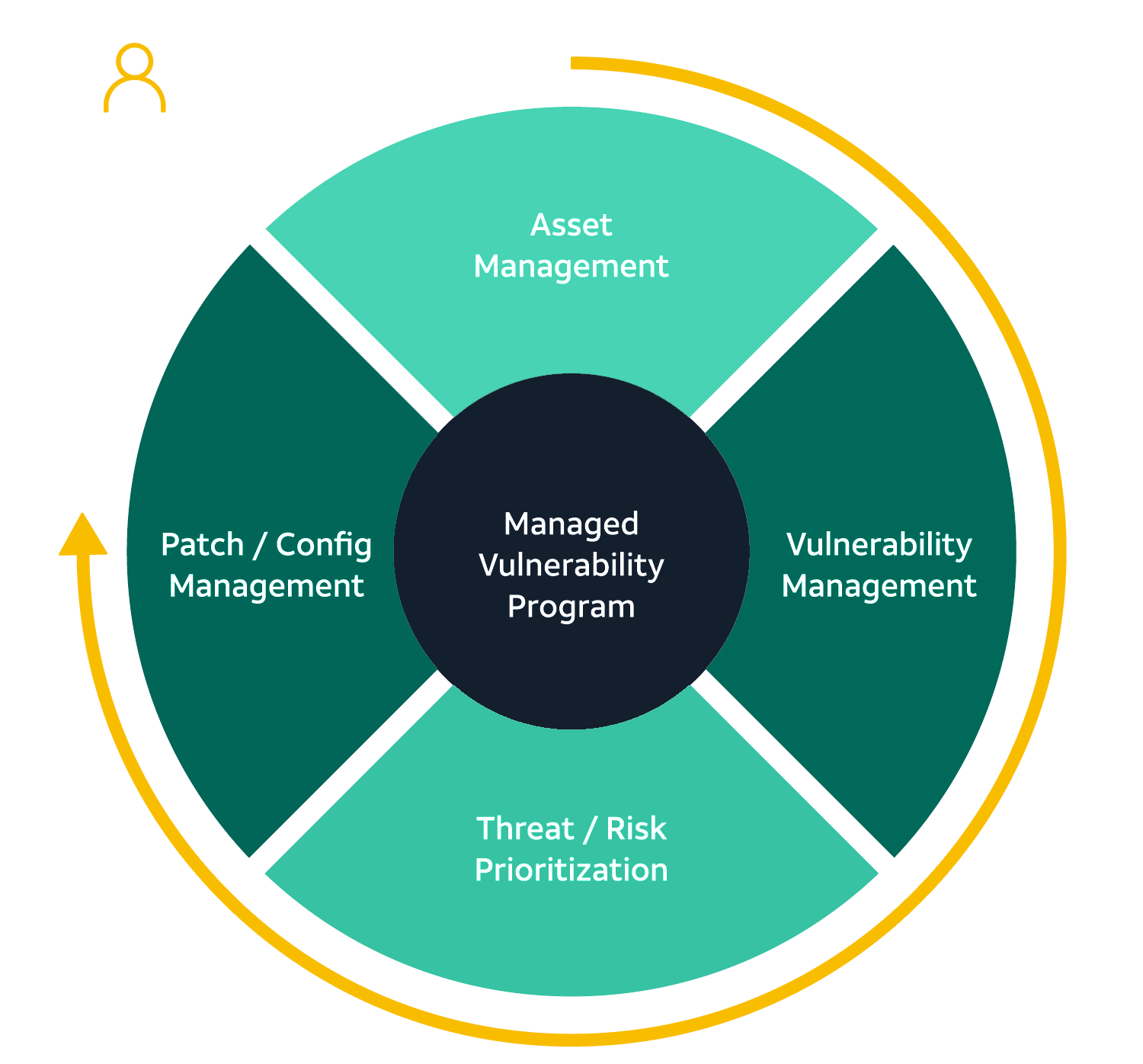





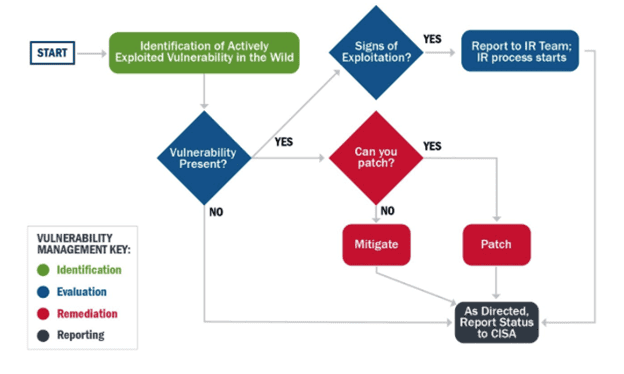
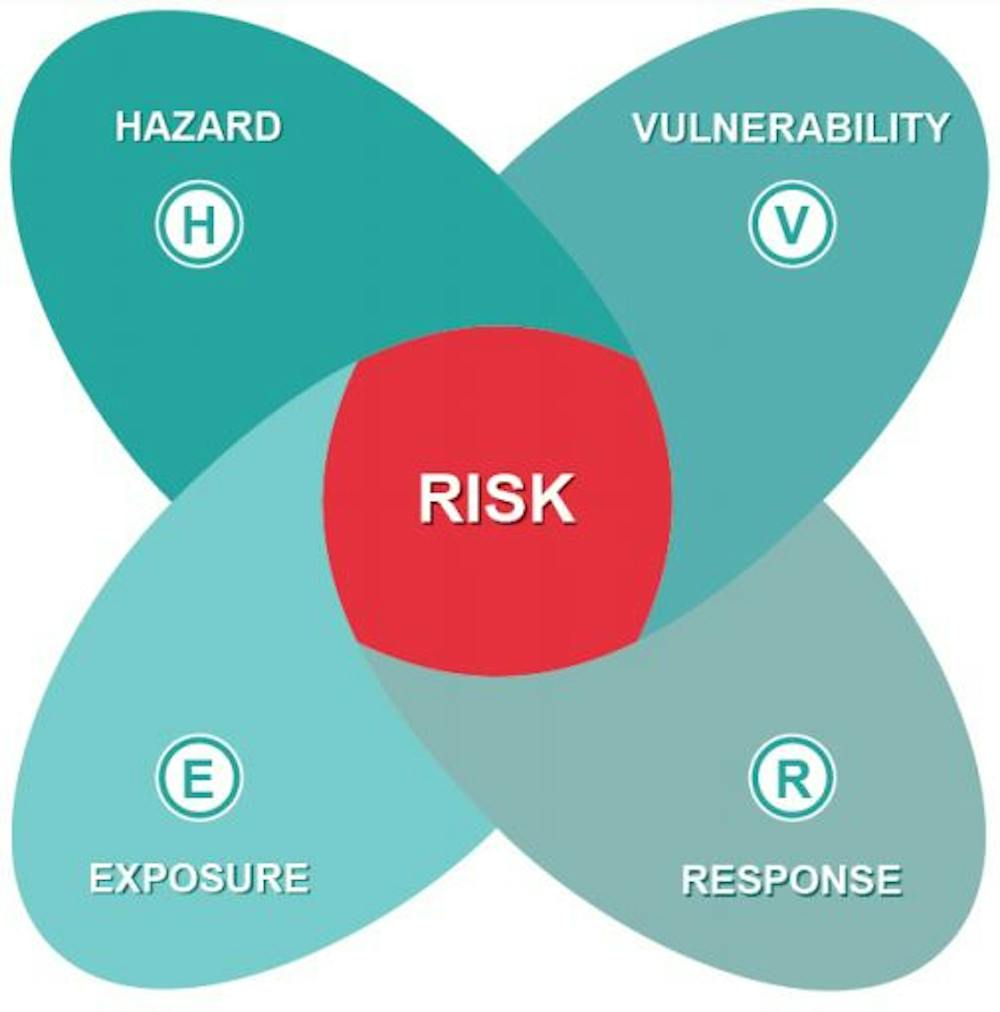


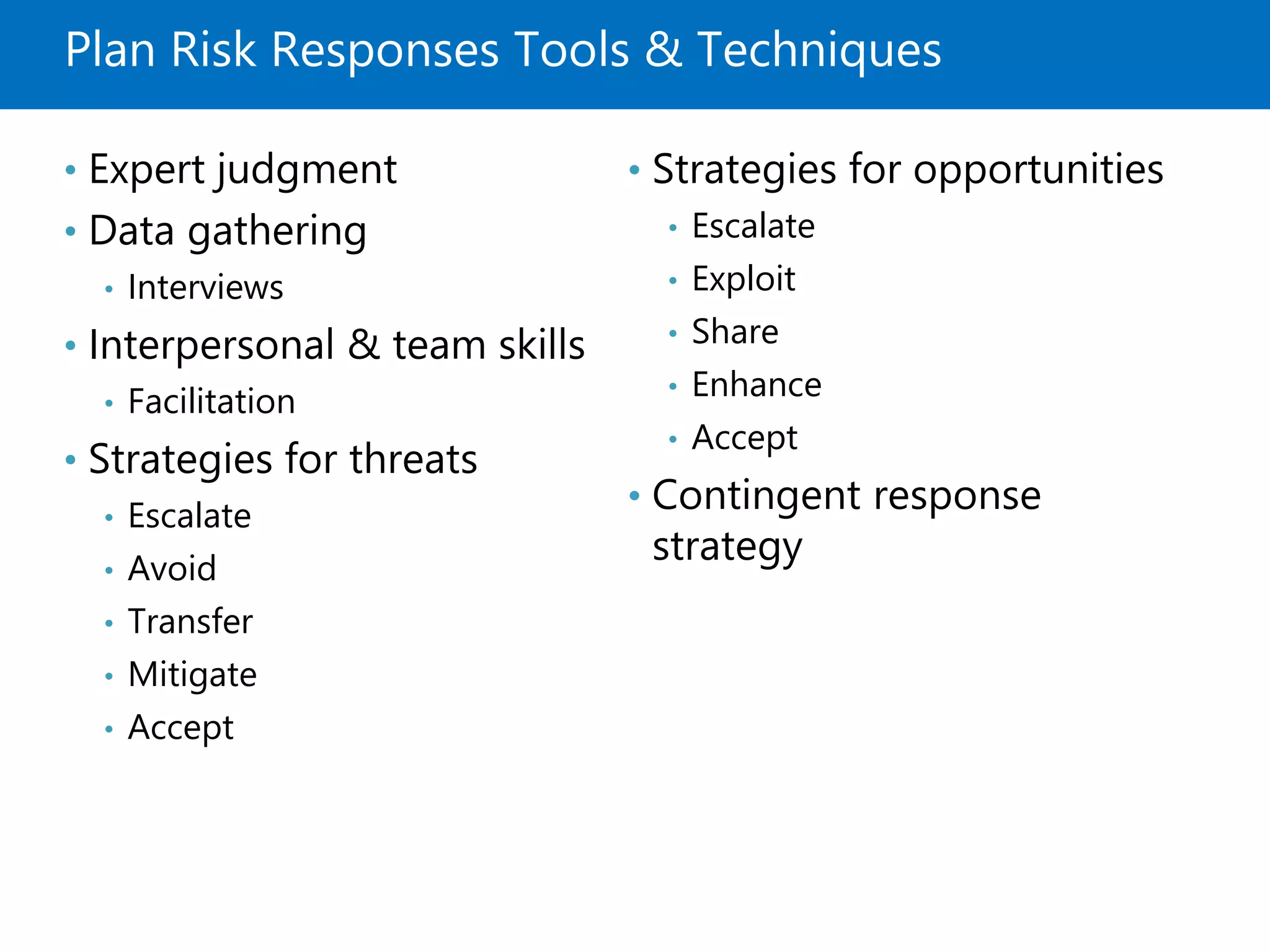
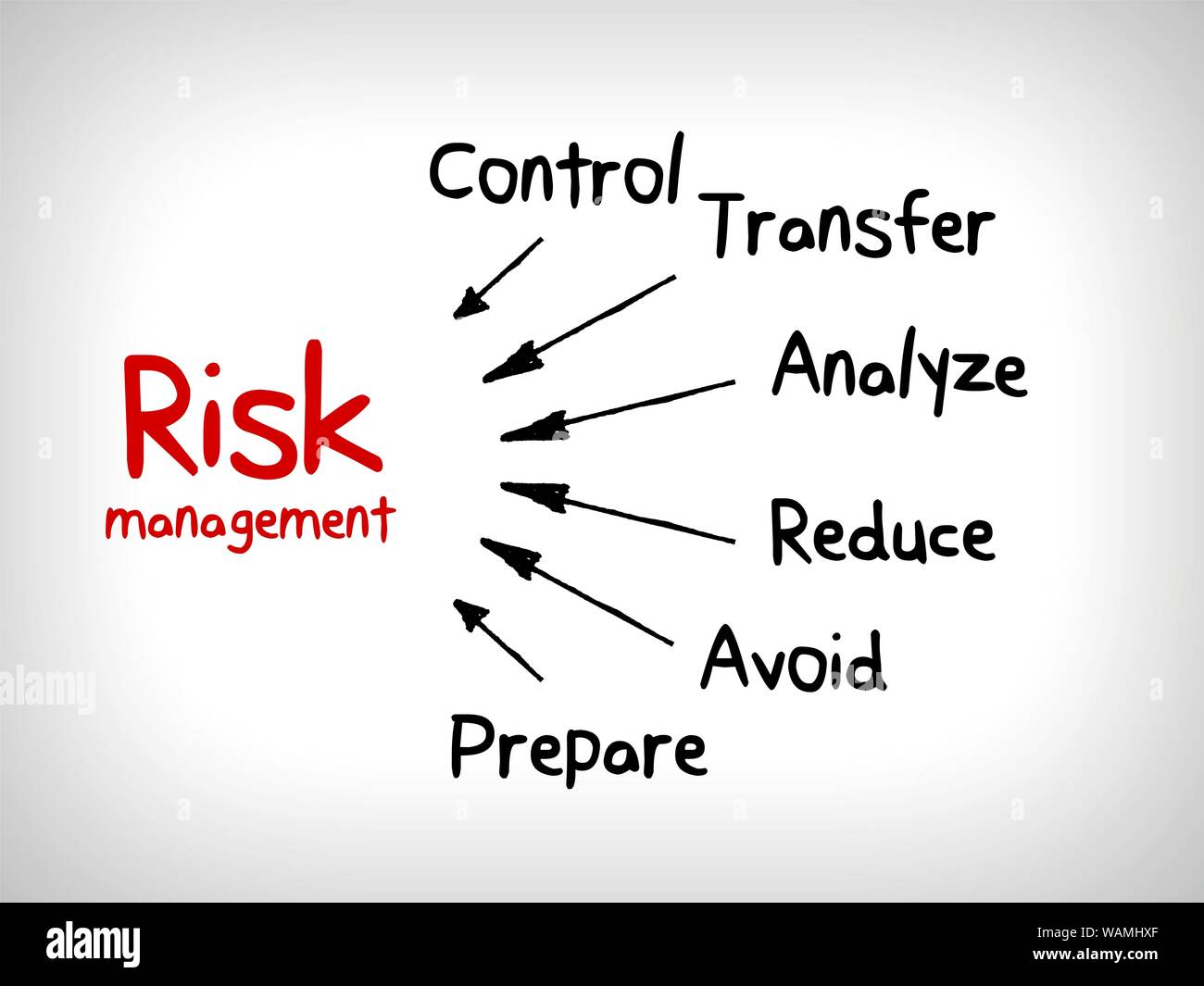






![Enterprise Security Risk Management (ESRM) Framework [+Plan Template]](https://www.alertmedia.com/wp-content/uploads/2022/01/Blog-9-Risk-Matrix-Inline-v1.jpg)
.png)
















.jpg)
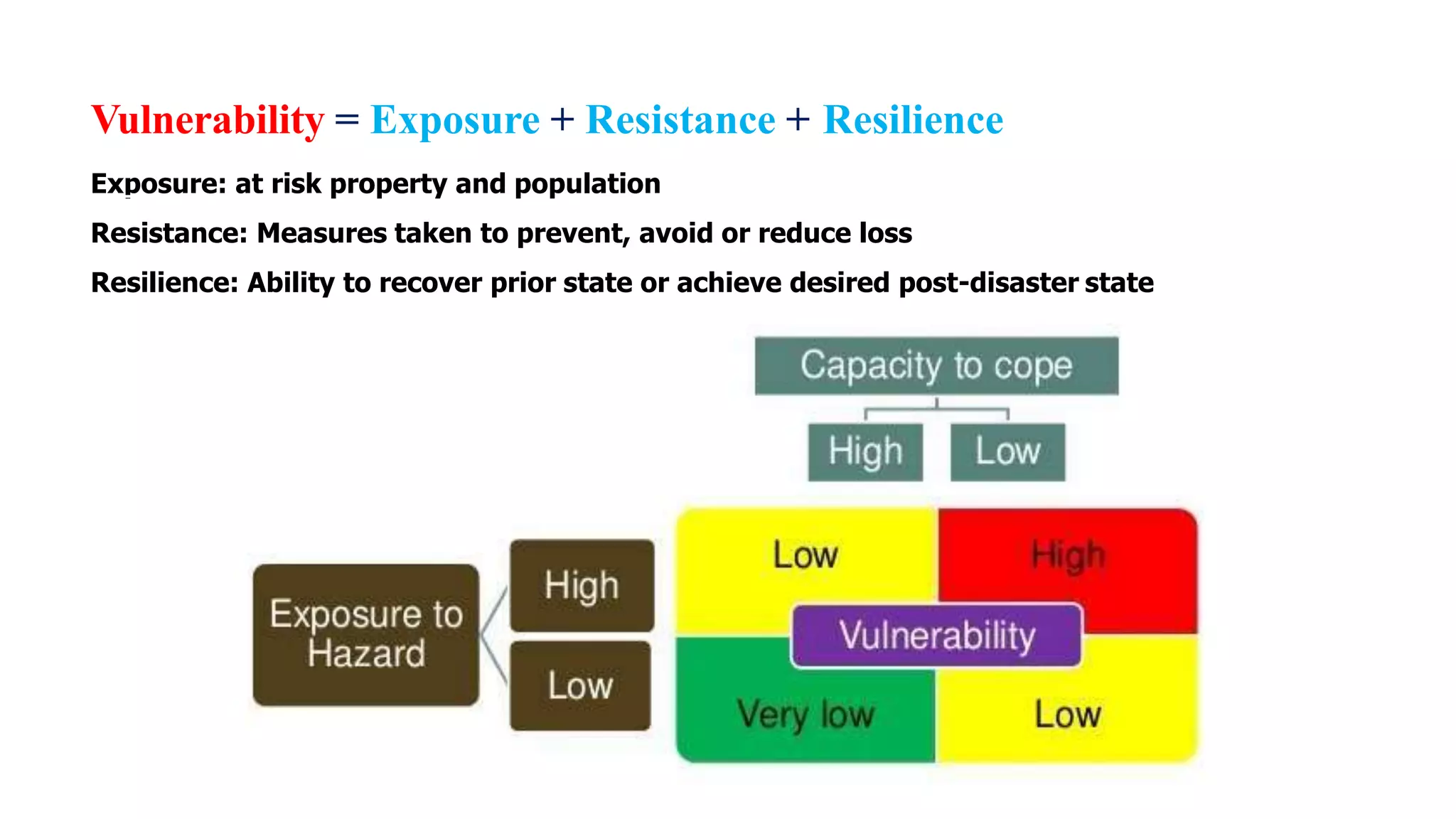
![Risk, threat, vulnerability and asset relationship [II] | Download ...](https://www.researchgate.net/profile/Unal_Tatar/publication/261427321/figure/download/fig1/AS:734192098877440@1552056445179/Risk-threat-vulnerability-and-asset-relationship-II.jpg)