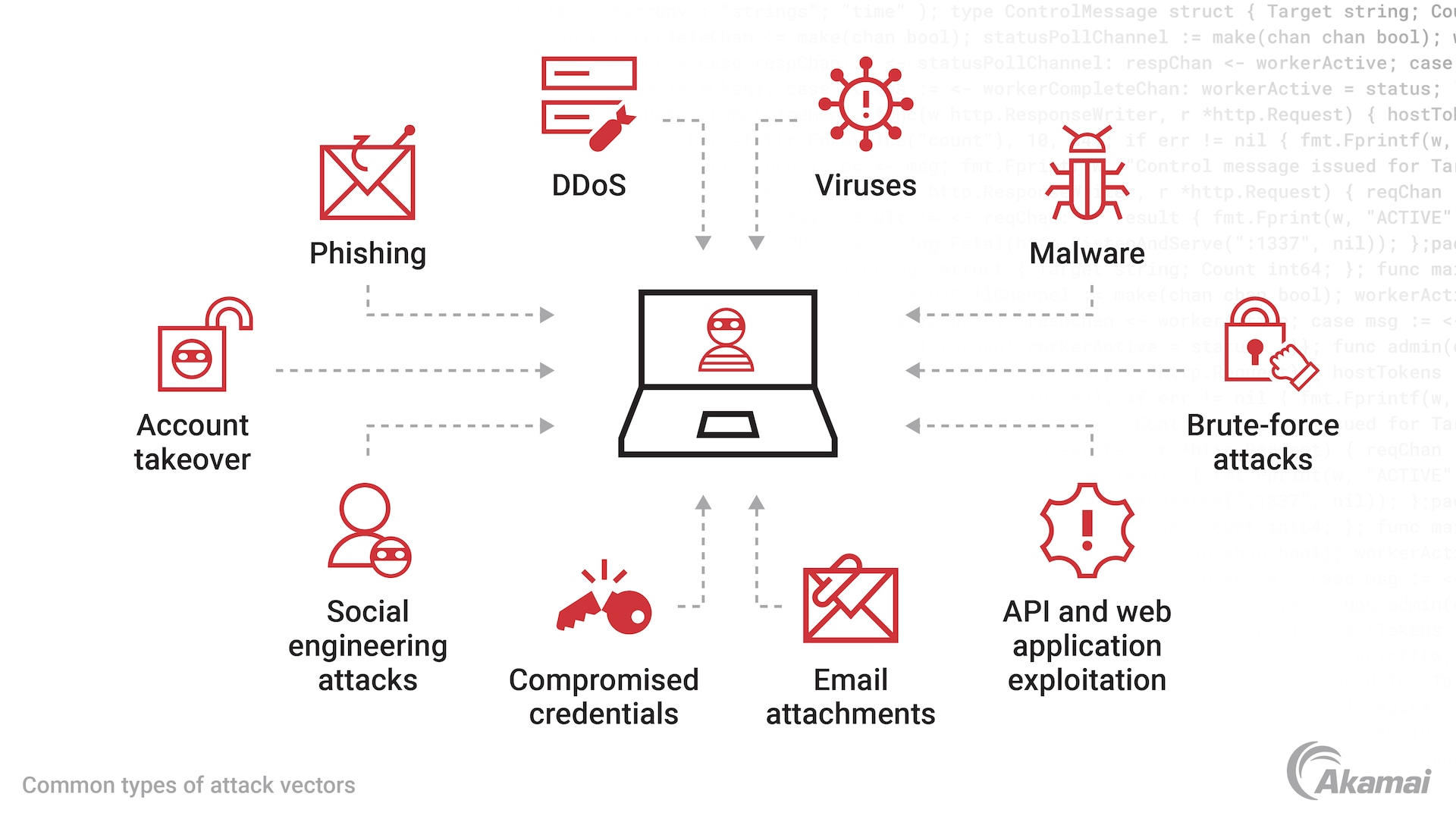
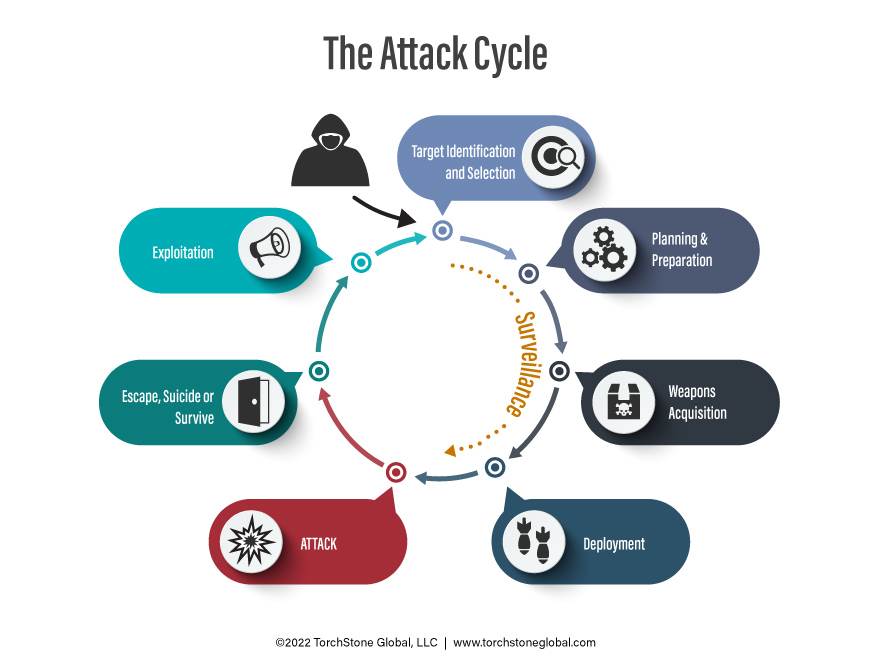
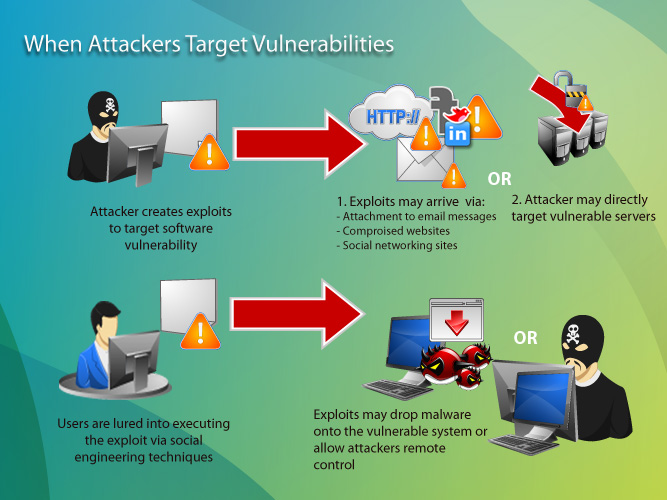
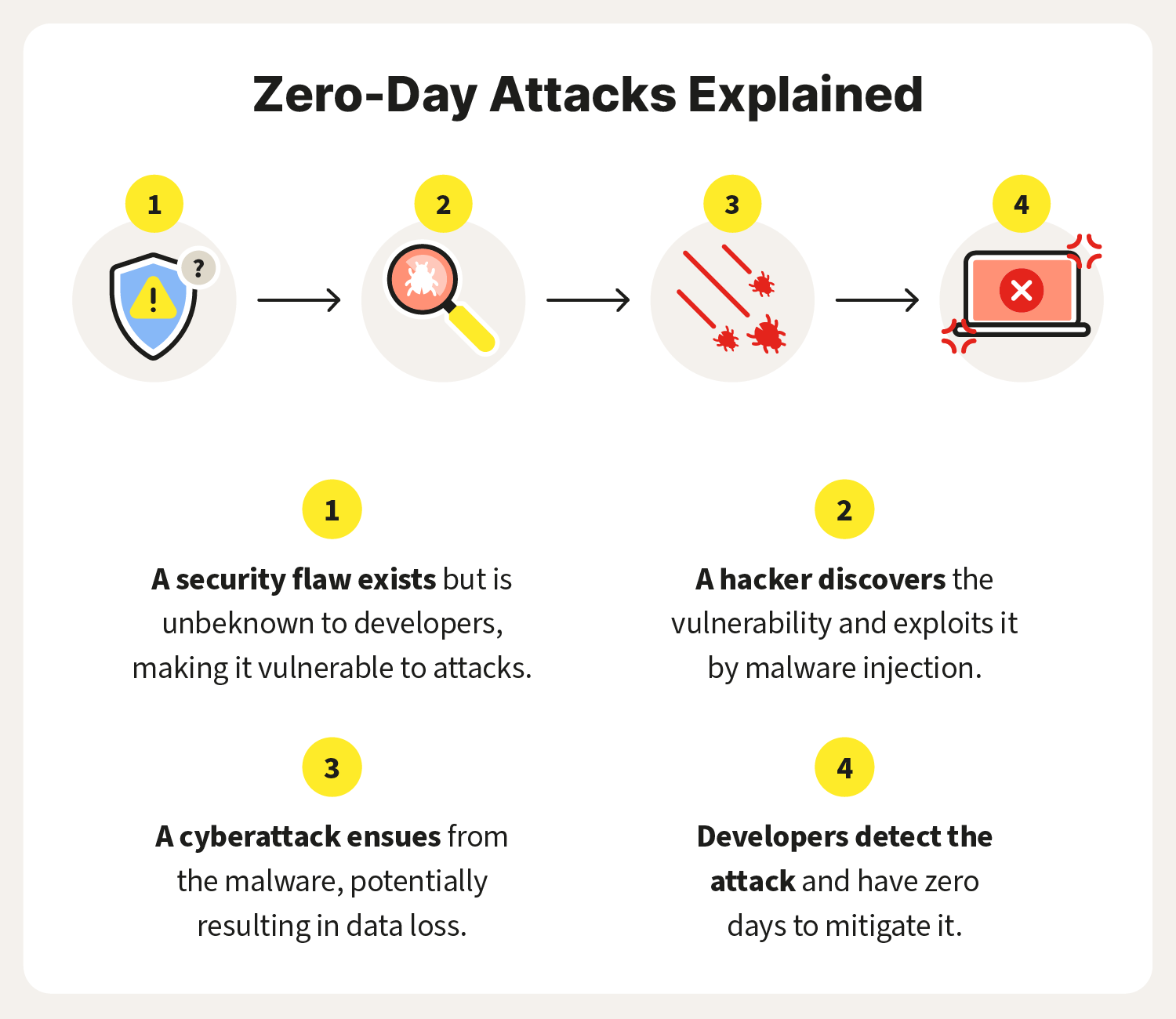
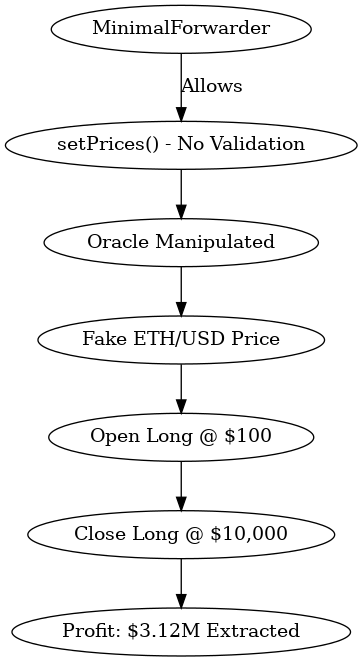
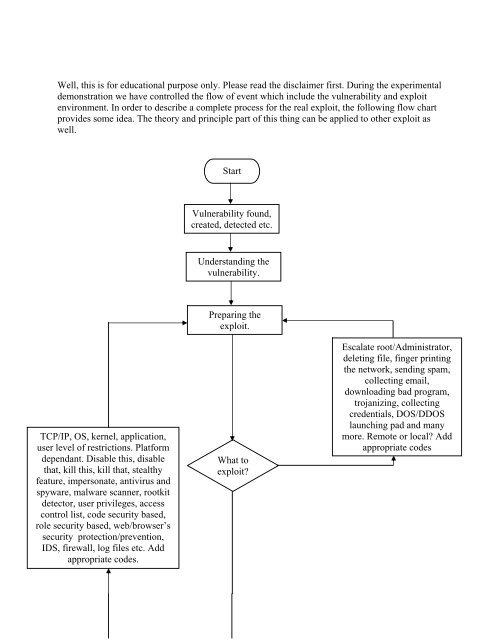
Exploit Protection Flowchart
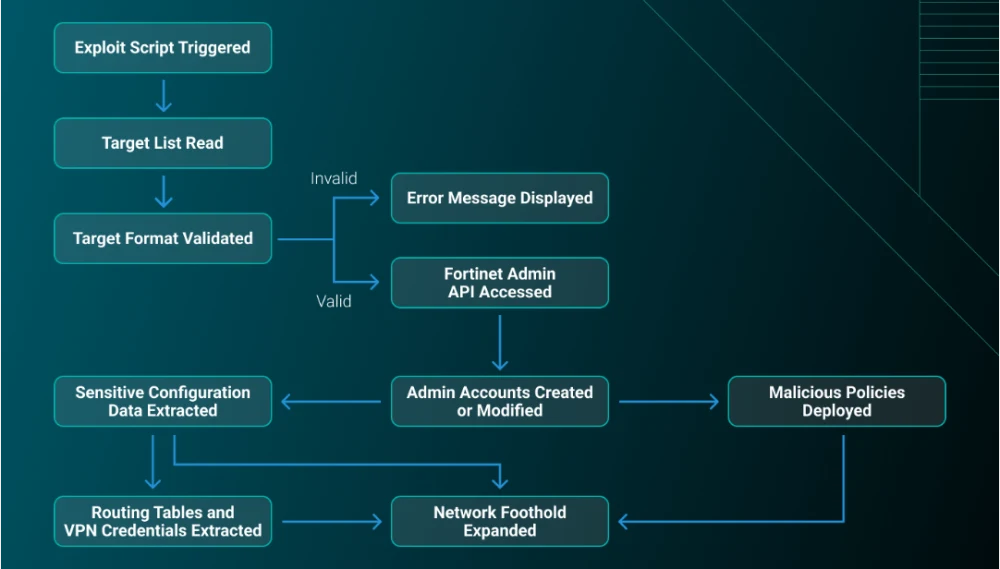
Study the characteristics of Exploit Protection Flowchart using our comprehensive set of comprehensive galleries of learning images. providing valuable teaching resources for educators and students alike. encouraging critical thinking and analytical skill development. Discover high-resolution Exploit Protection Flowchart images optimized for various applications. Excellent for educational materials, academic research, teaching resources, and learning activities All Exploit Protection Flowchart images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. The Exploit Protection Flowchart collection serves as a valuable educational resource for teachers and students. Professional licensing options accommodate both commercial and educational usage requirements. Our Exploit Protection Flowchart database continuously expands with fresh, relevant content from skilled photographers. Each image in our Exploit Protection Flowchart gallery undergoes rigorous quality assessment before inclusion. The Exploit Protection Flowchart archive serves professionals, educators, and creatives across diverse industries. Cost-effective licensing makes professional Exploit Protection Flowchart photography accessible to all budgets. Diverse style options within the Exploit Protection Flowchart collection suit various aesthetic preferences. Instant download capabilities enable immediate access to chosen Exploit Protection Flowchart images. Time-saving browsing features help users locate ideal Exploit Protection Flowchart images quickly. The Exploit Protection Flowchart collection represents years of careful curation and professional standards.


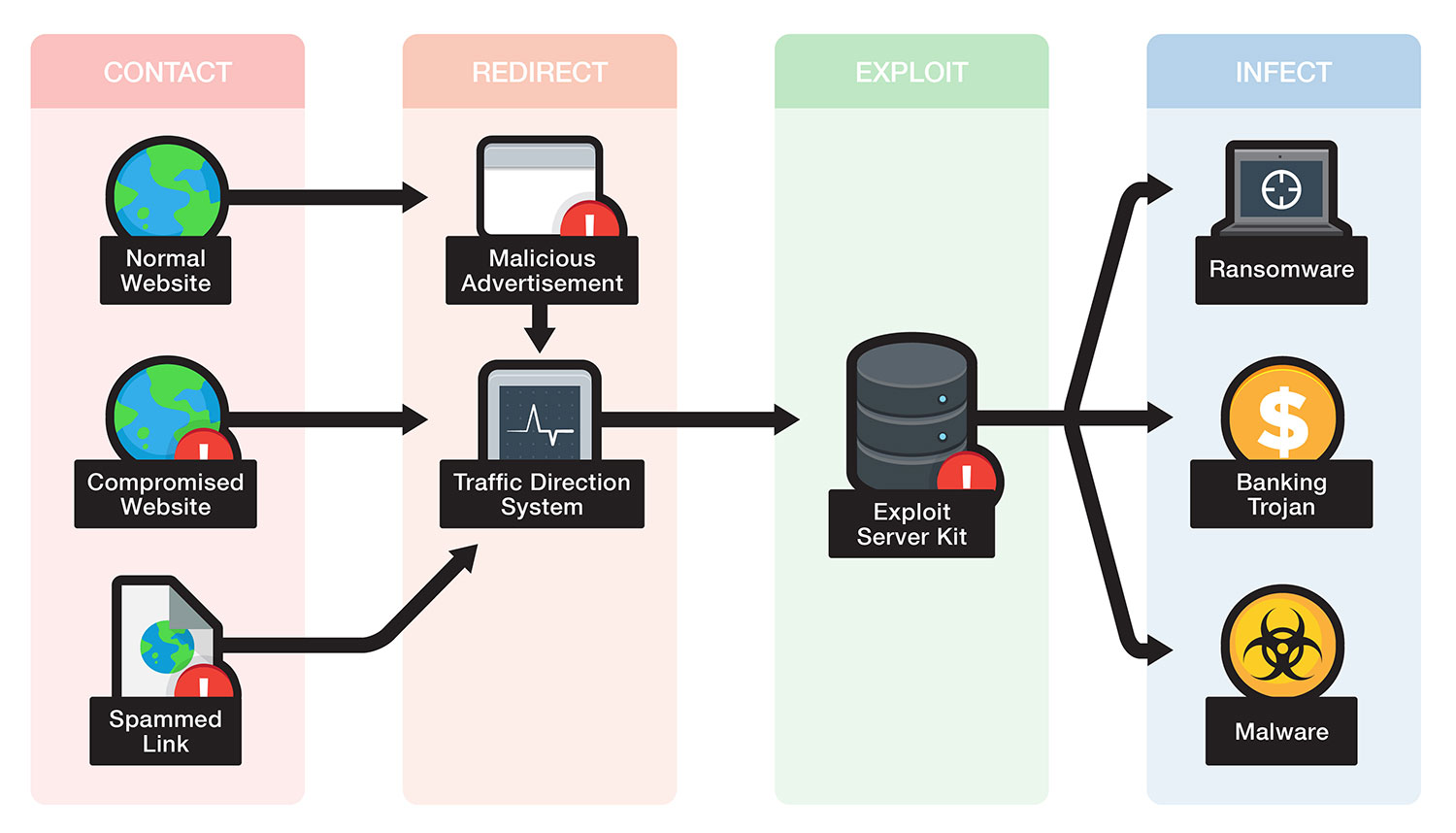




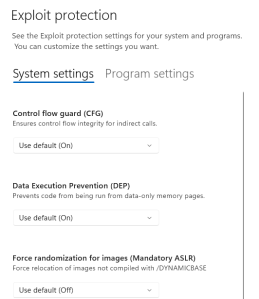




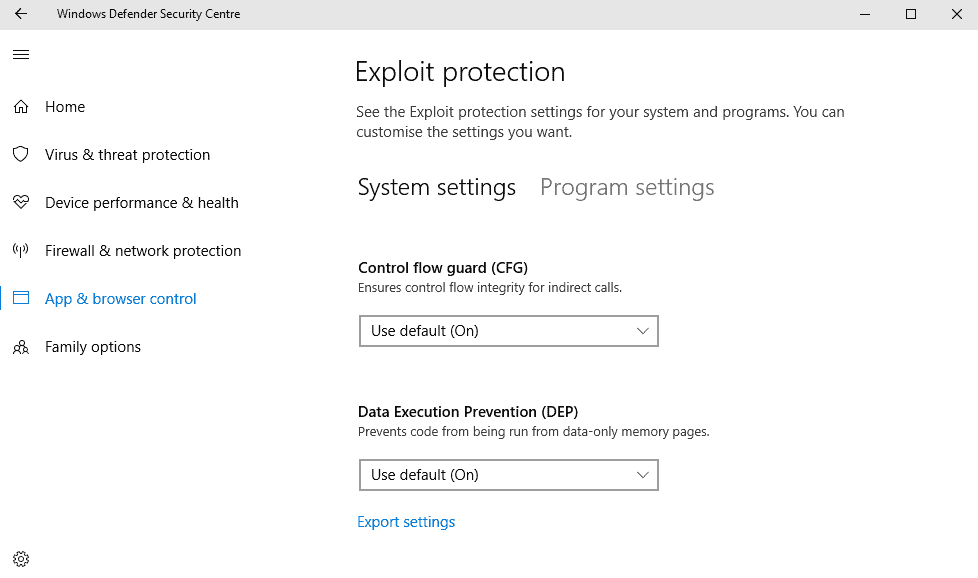
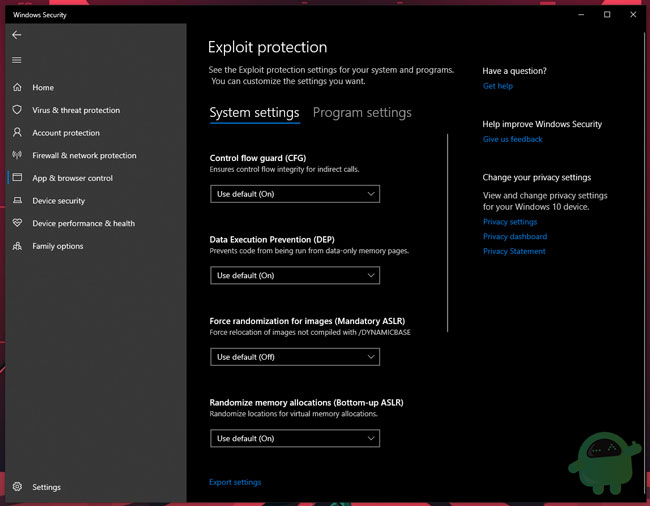
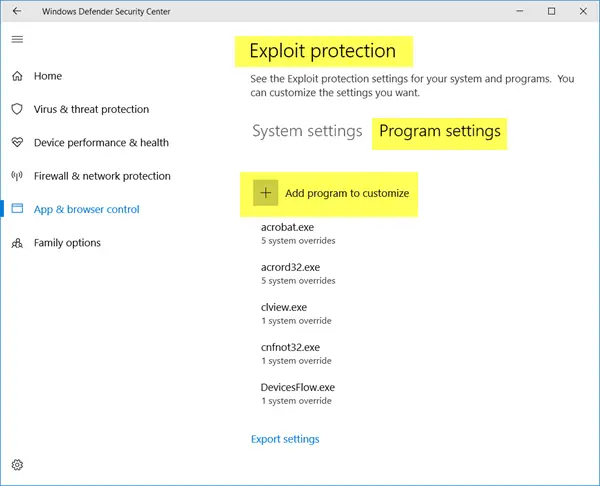
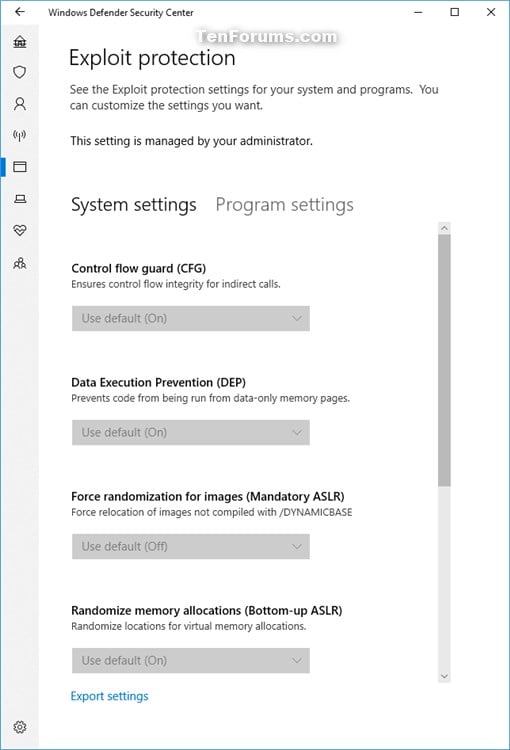

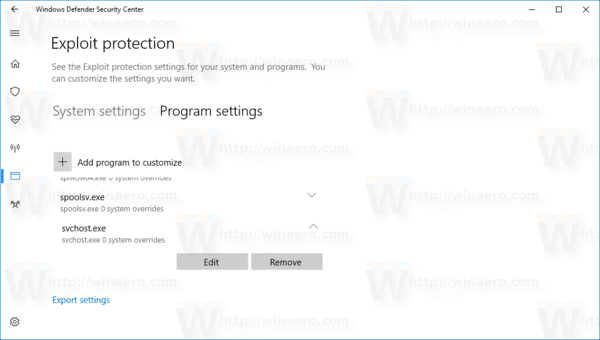
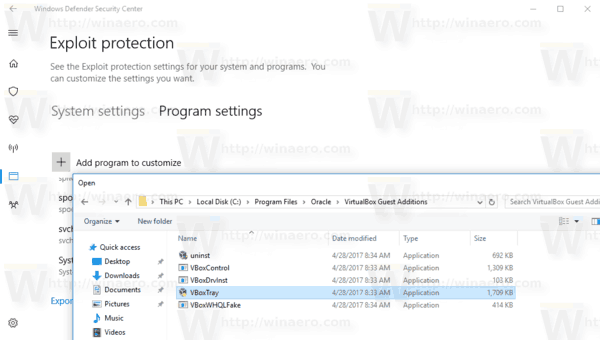
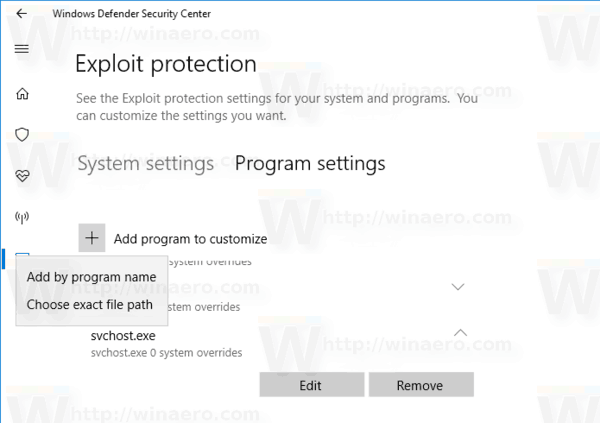


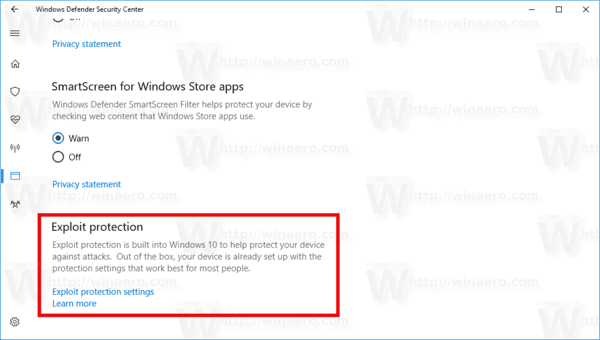

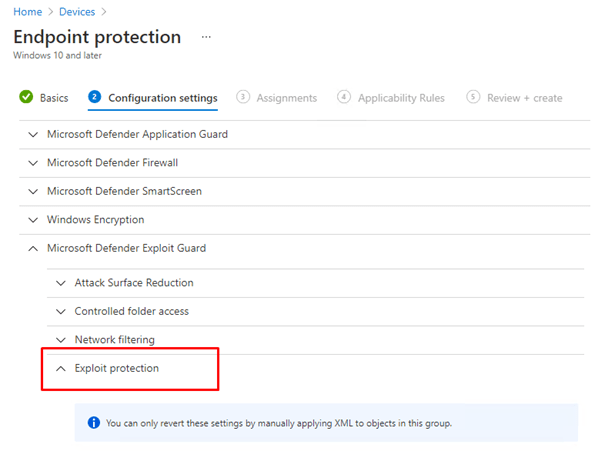
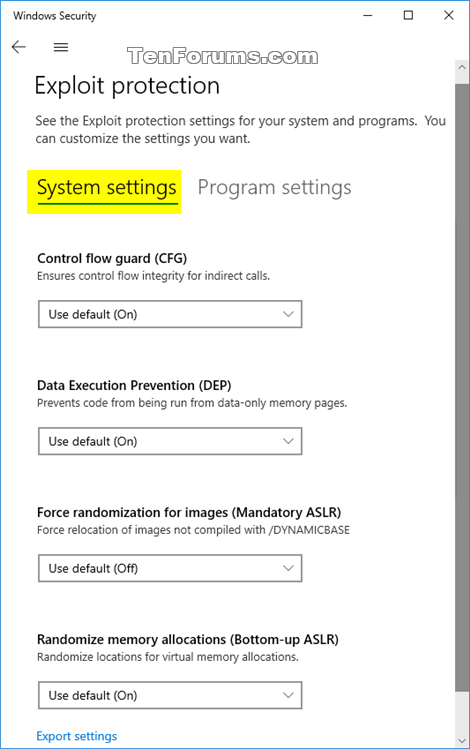

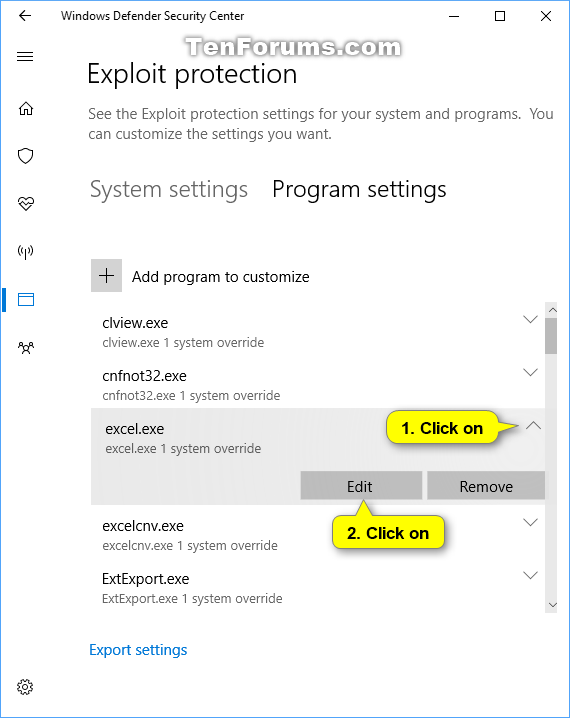

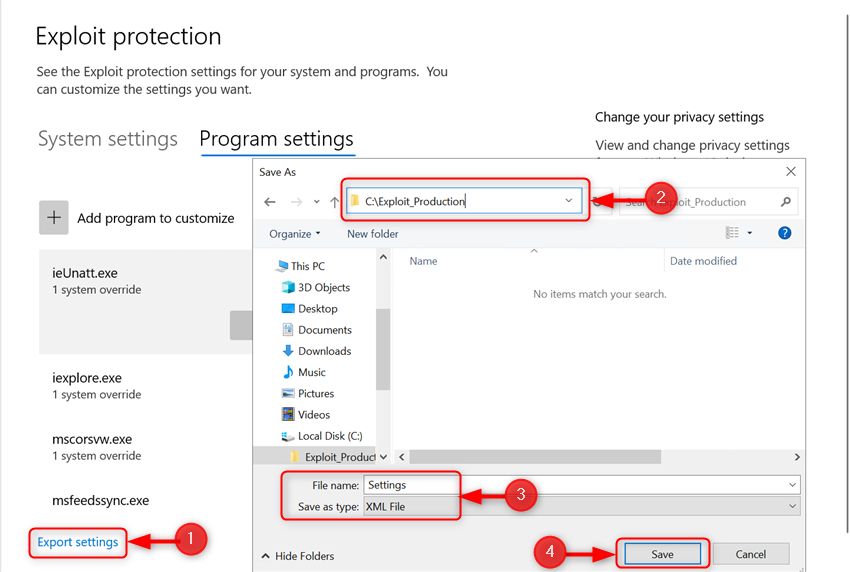





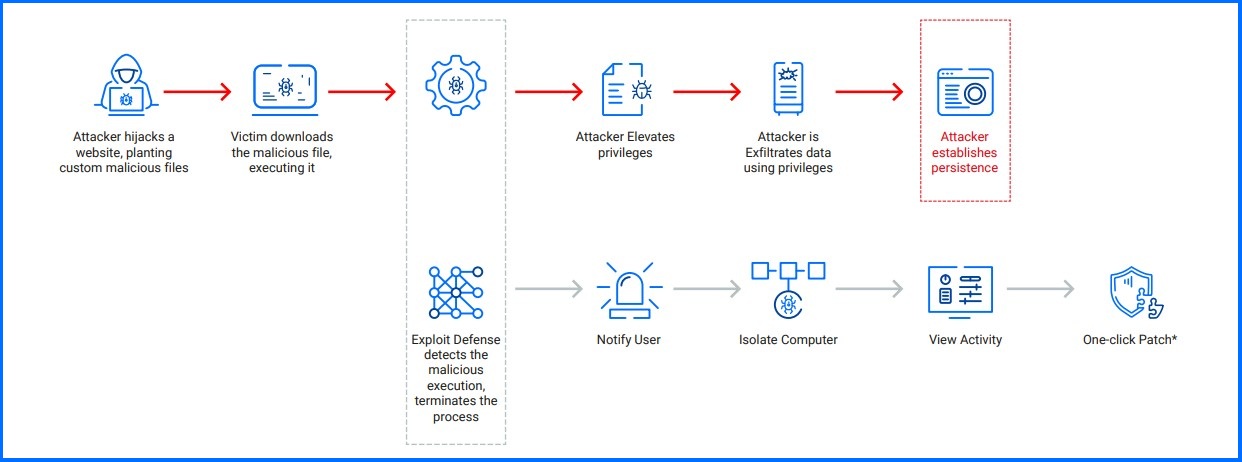

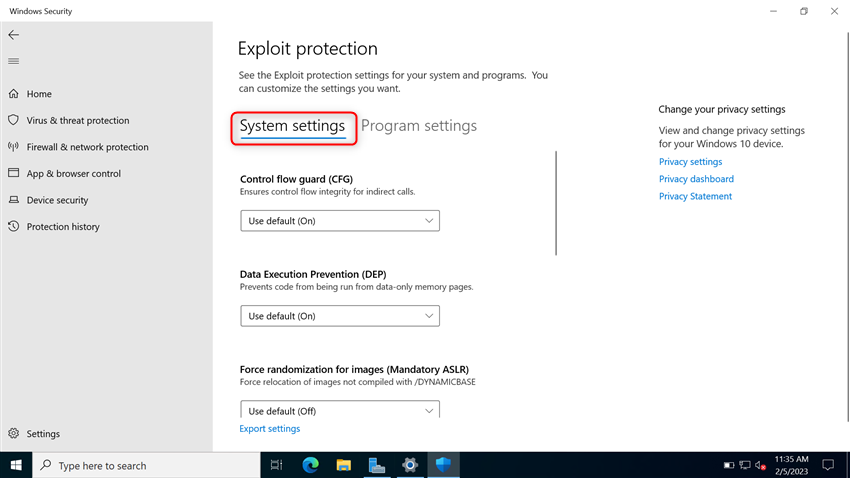






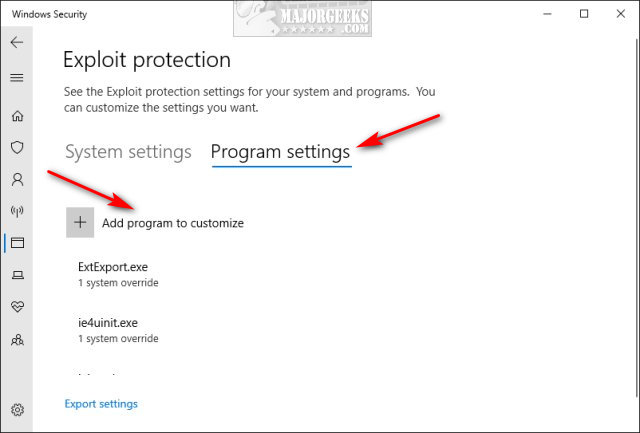
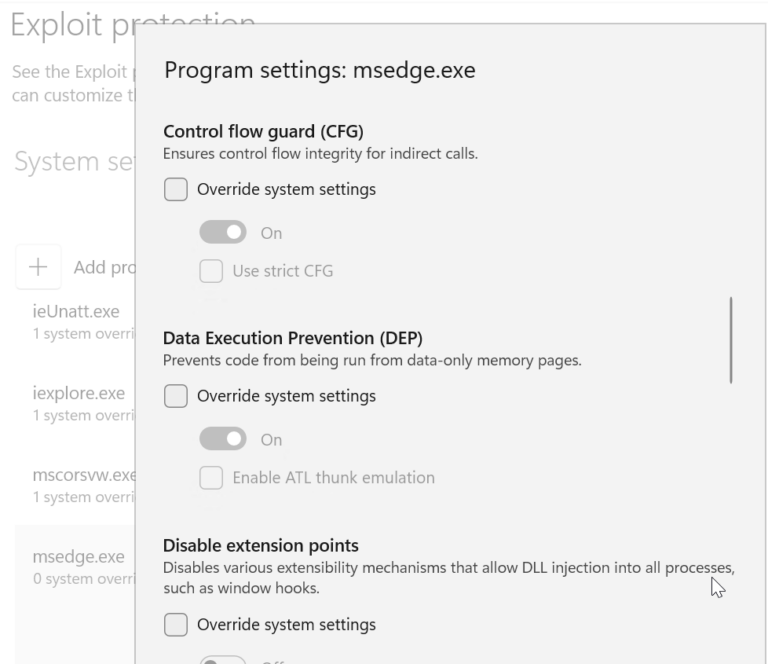
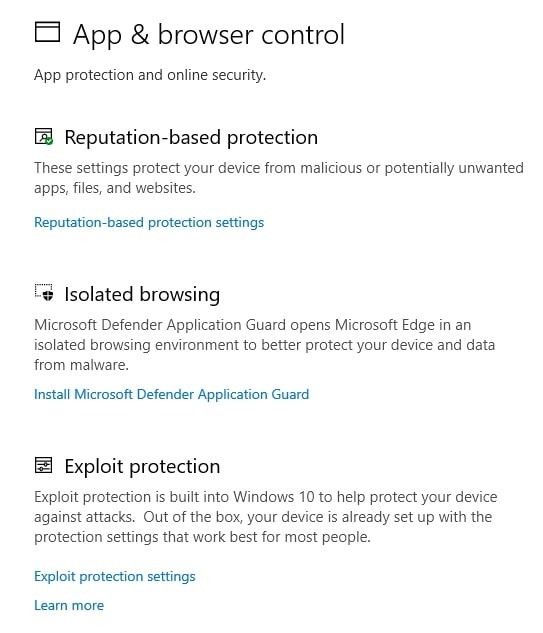

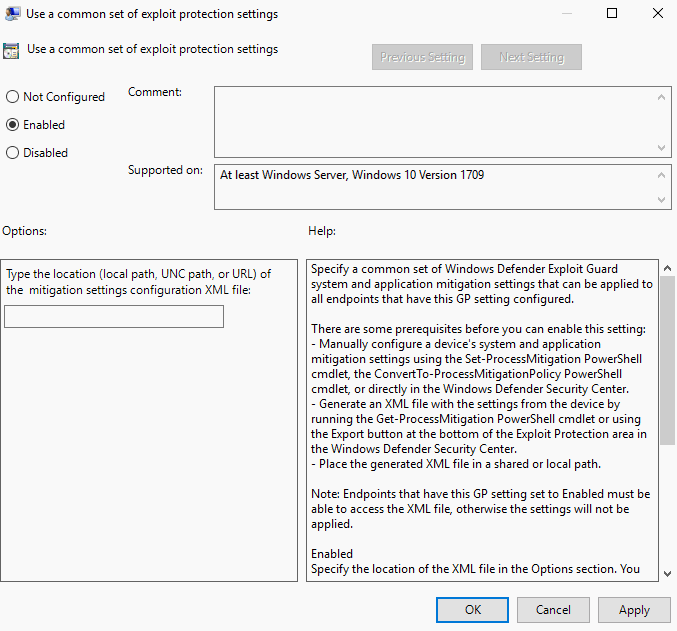



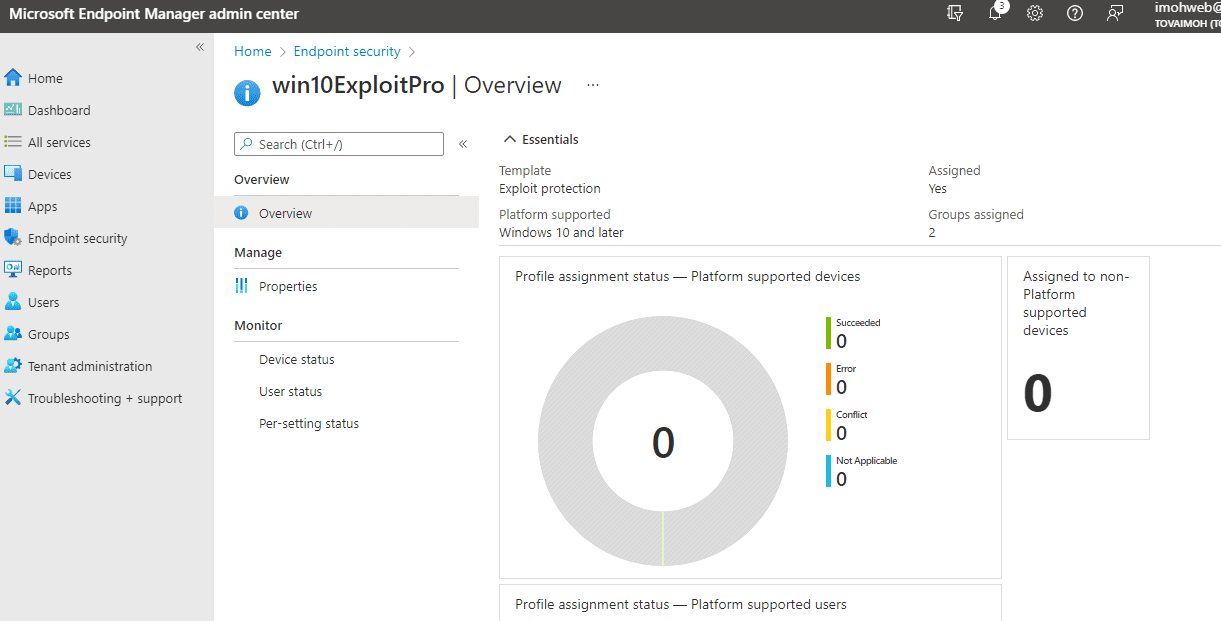


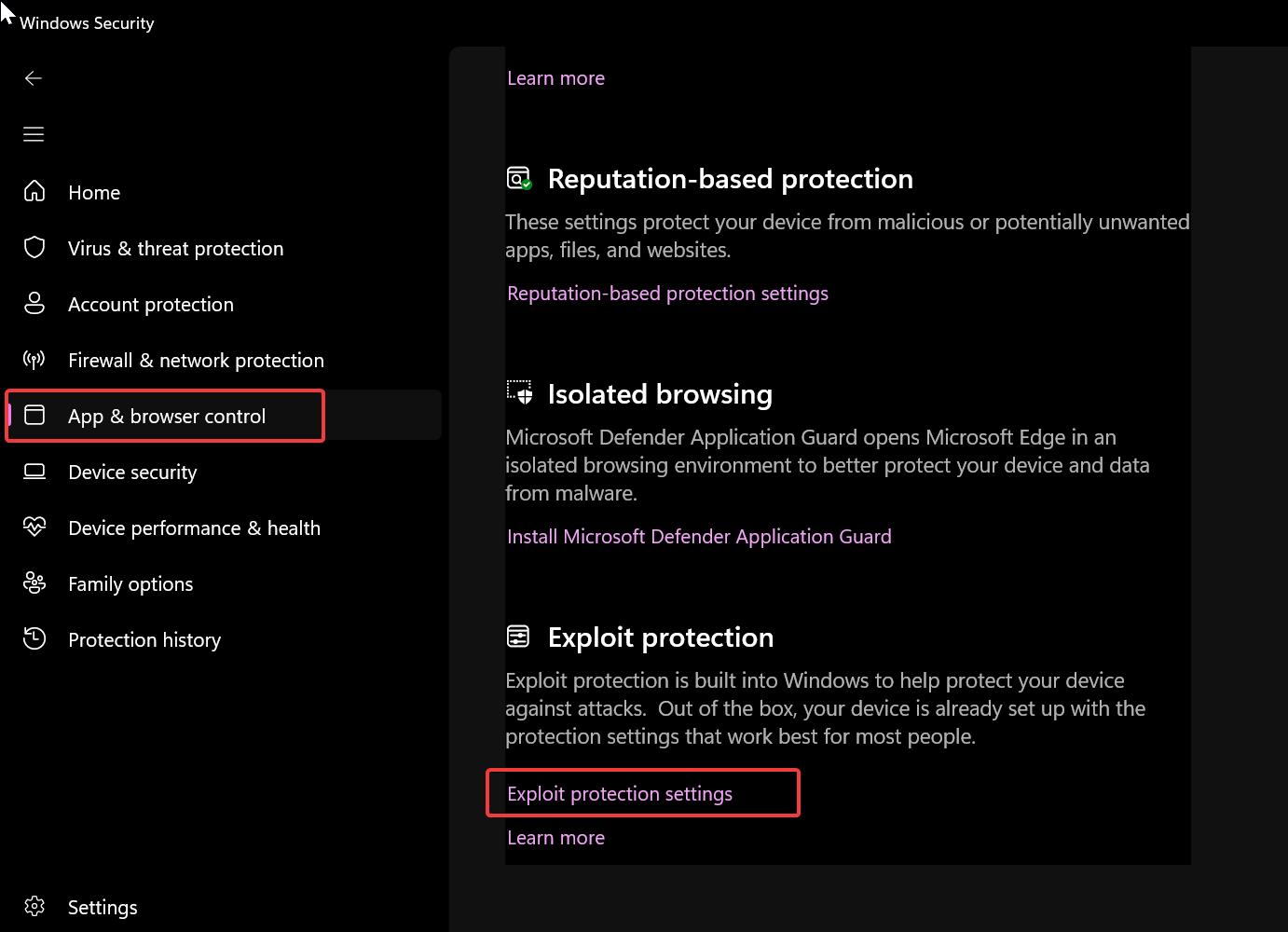
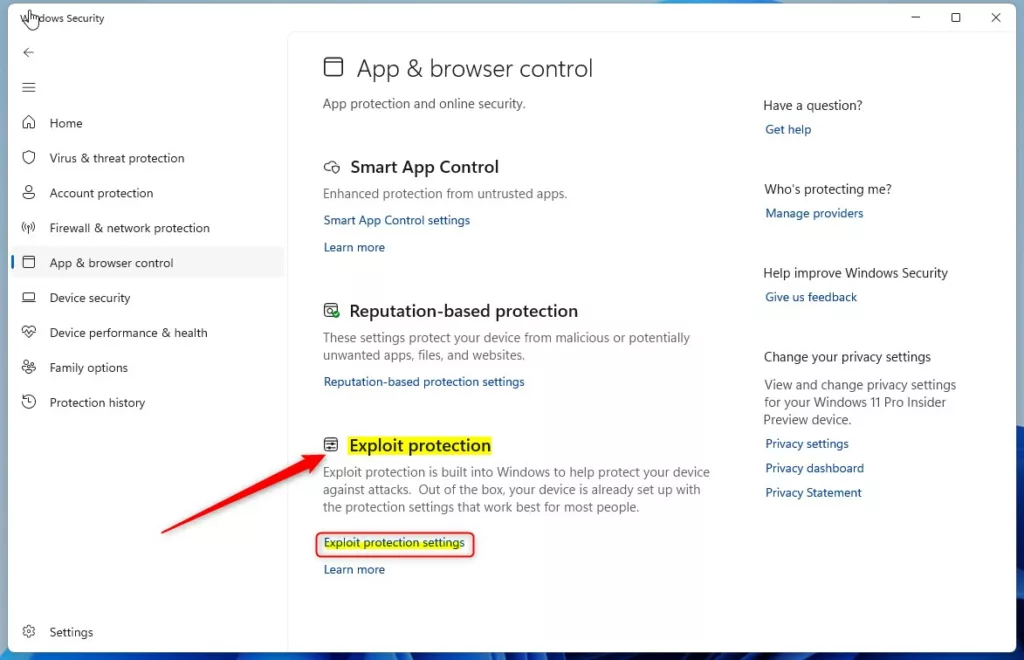
![[How To] Configure Exploit Protection For Windows Security In Windows 10](https://htse.kapilarya.com/Configure-Exploit-Protection-For-Windows-Security-In-Windows-10-1.png)






![[How To] Configure Exploit Protection For Windows Security In Windows 10](https://htse.kapilarya.com/Configure-Exploit-Protection-For-Windows-Security-In-Windows-10-5.png)




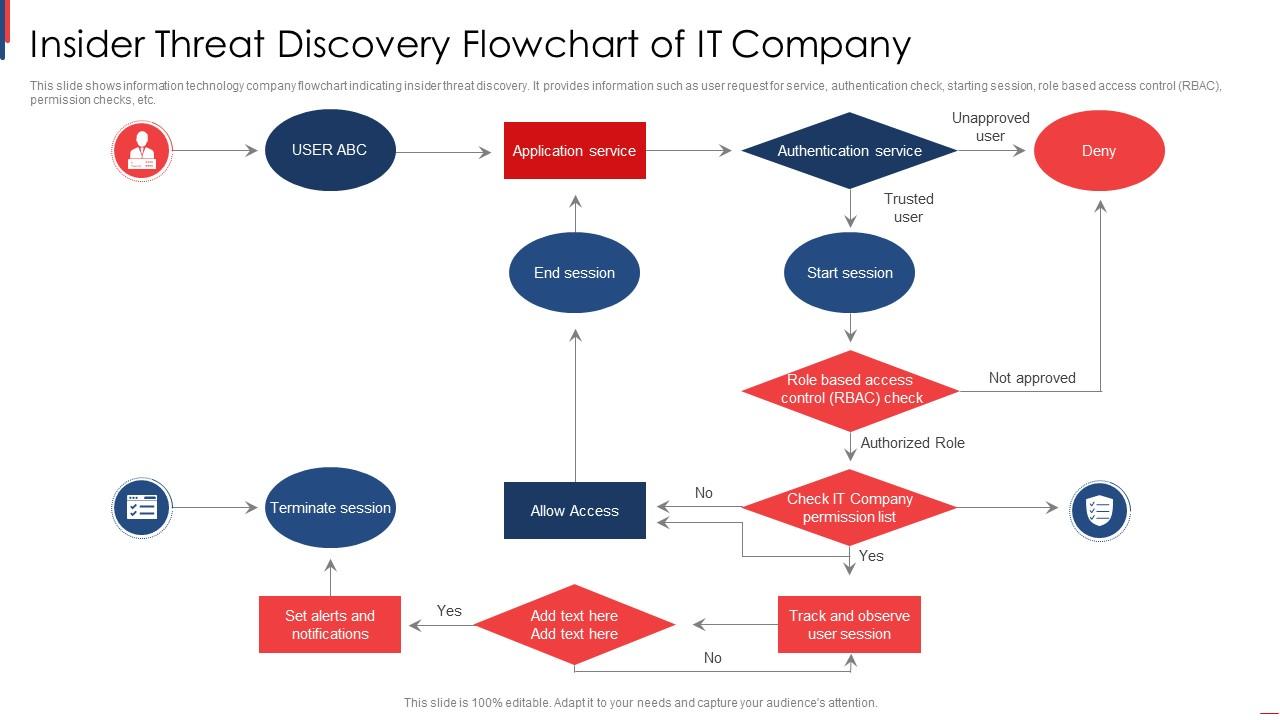
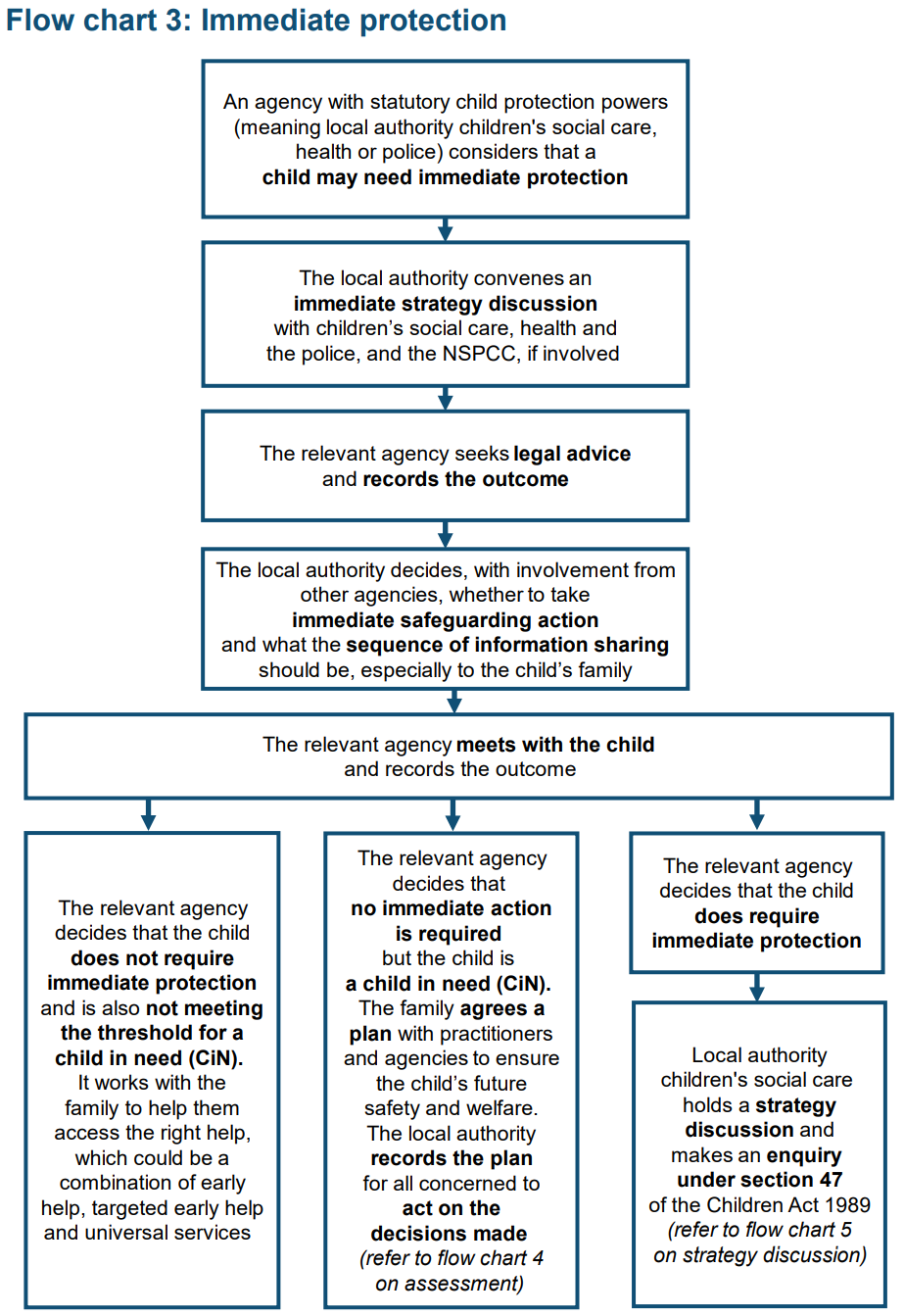








![Section 47 child protection flow chart [79] | Download Scientific Diagram](https://www.researchgate.net/publication/366793302/figure/fig1/AS:11431281164395667@1685707016206/Section-47-child-protection-flow-chart-79.png)