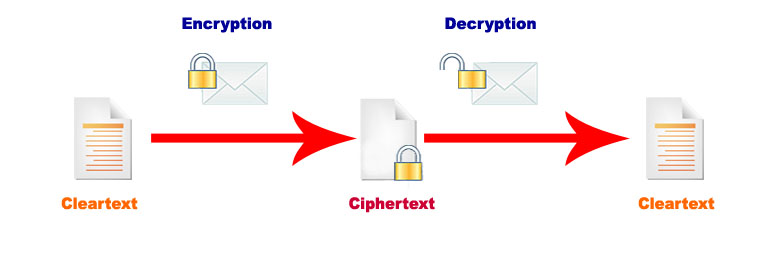
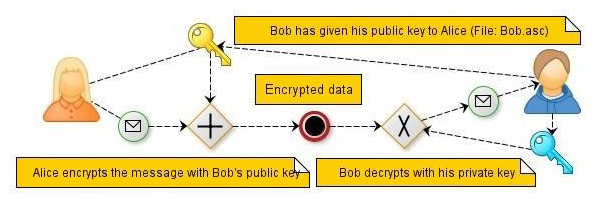
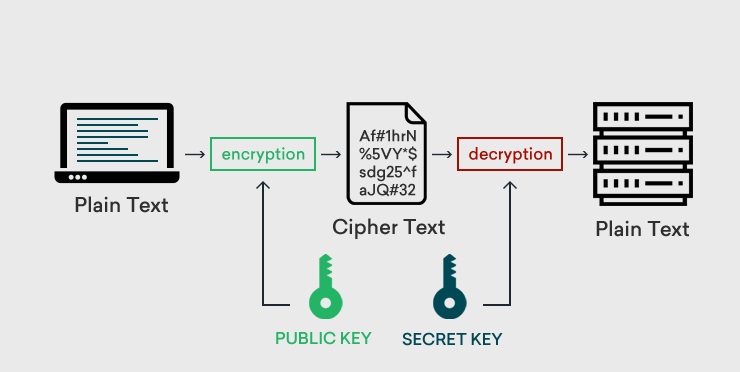
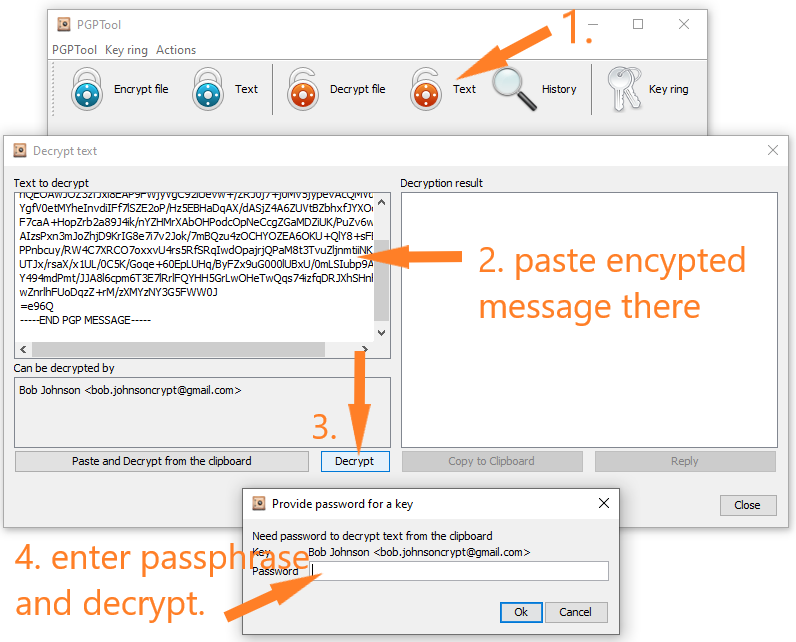
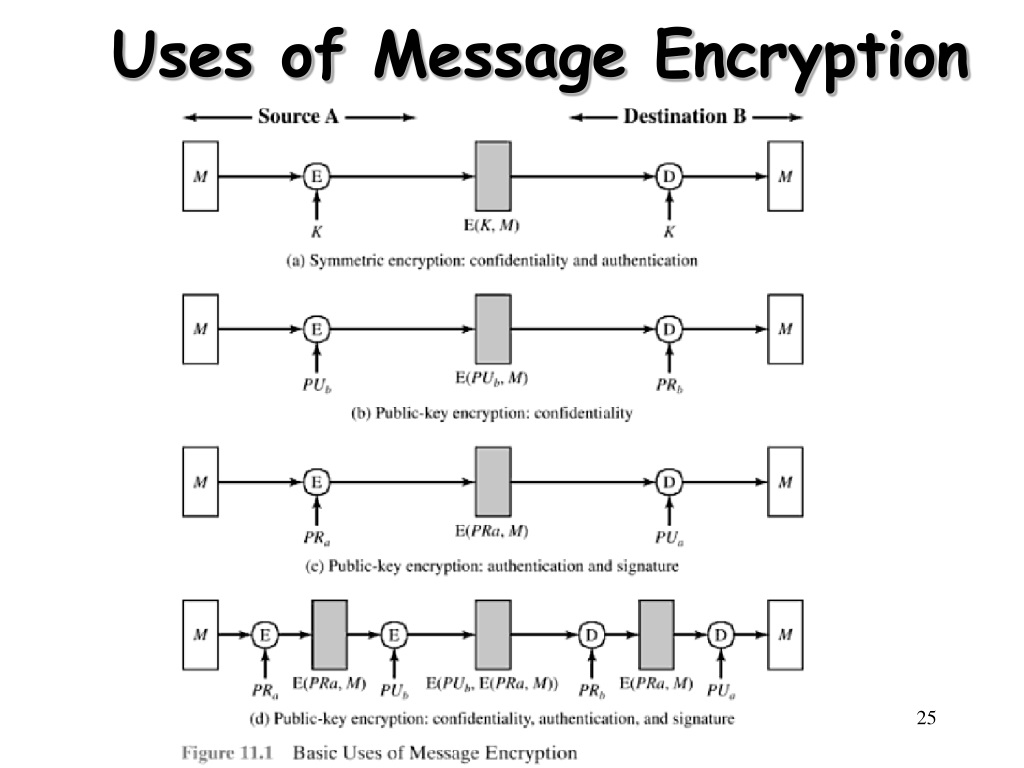
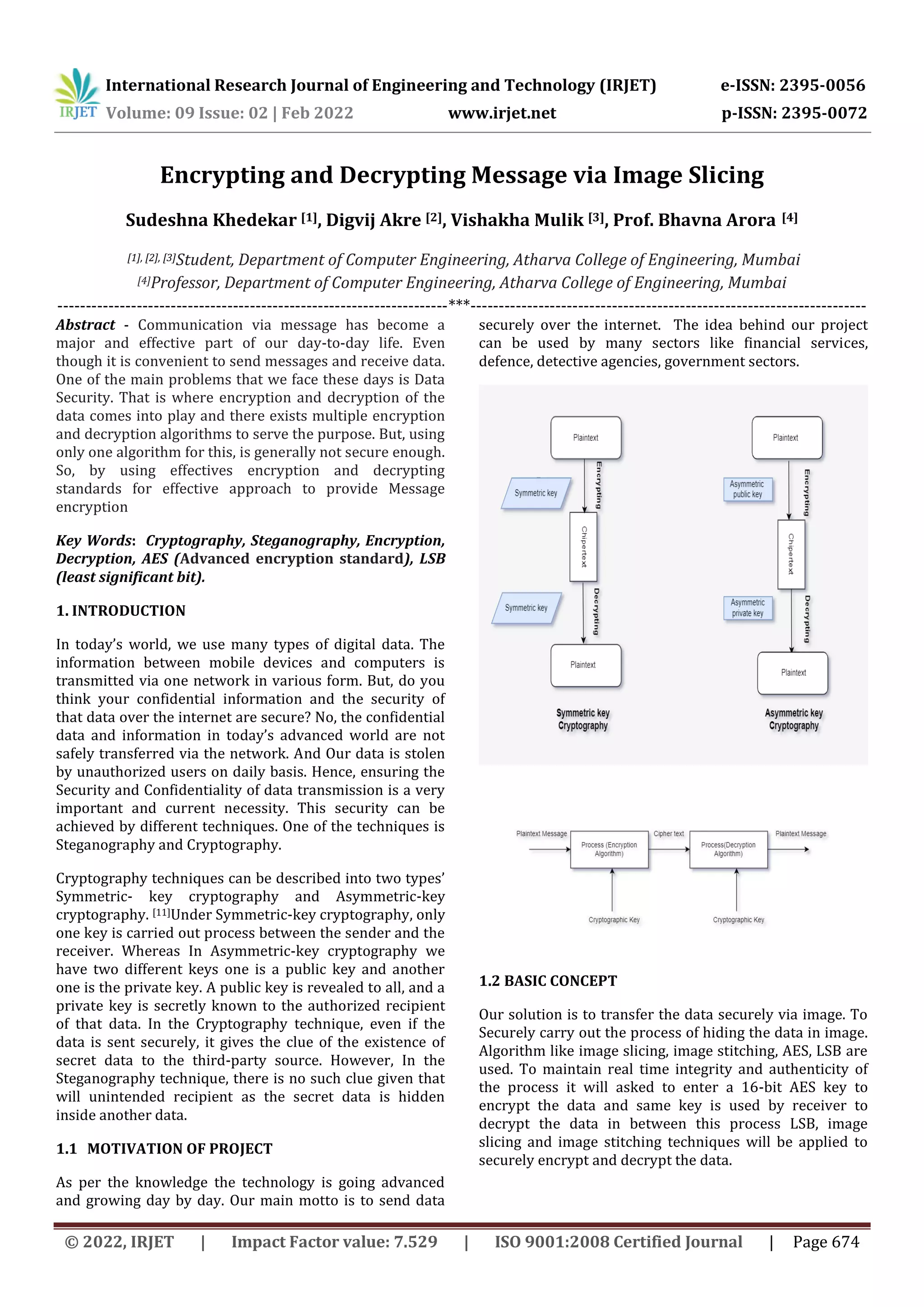
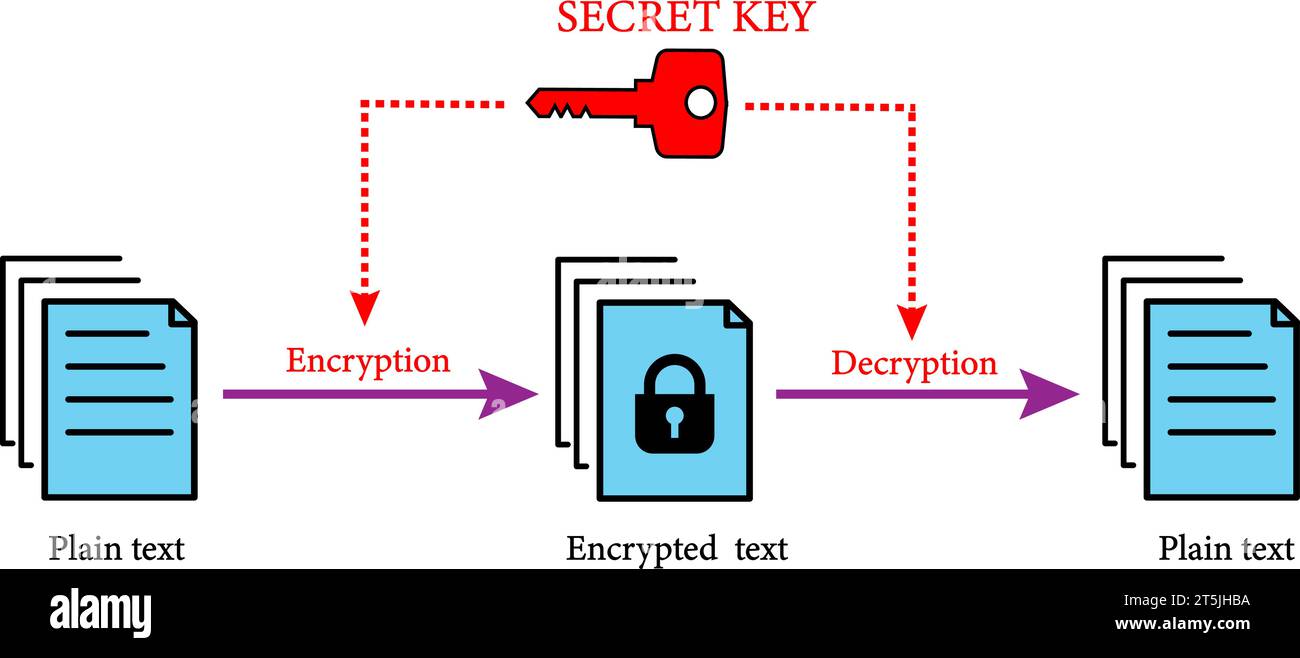
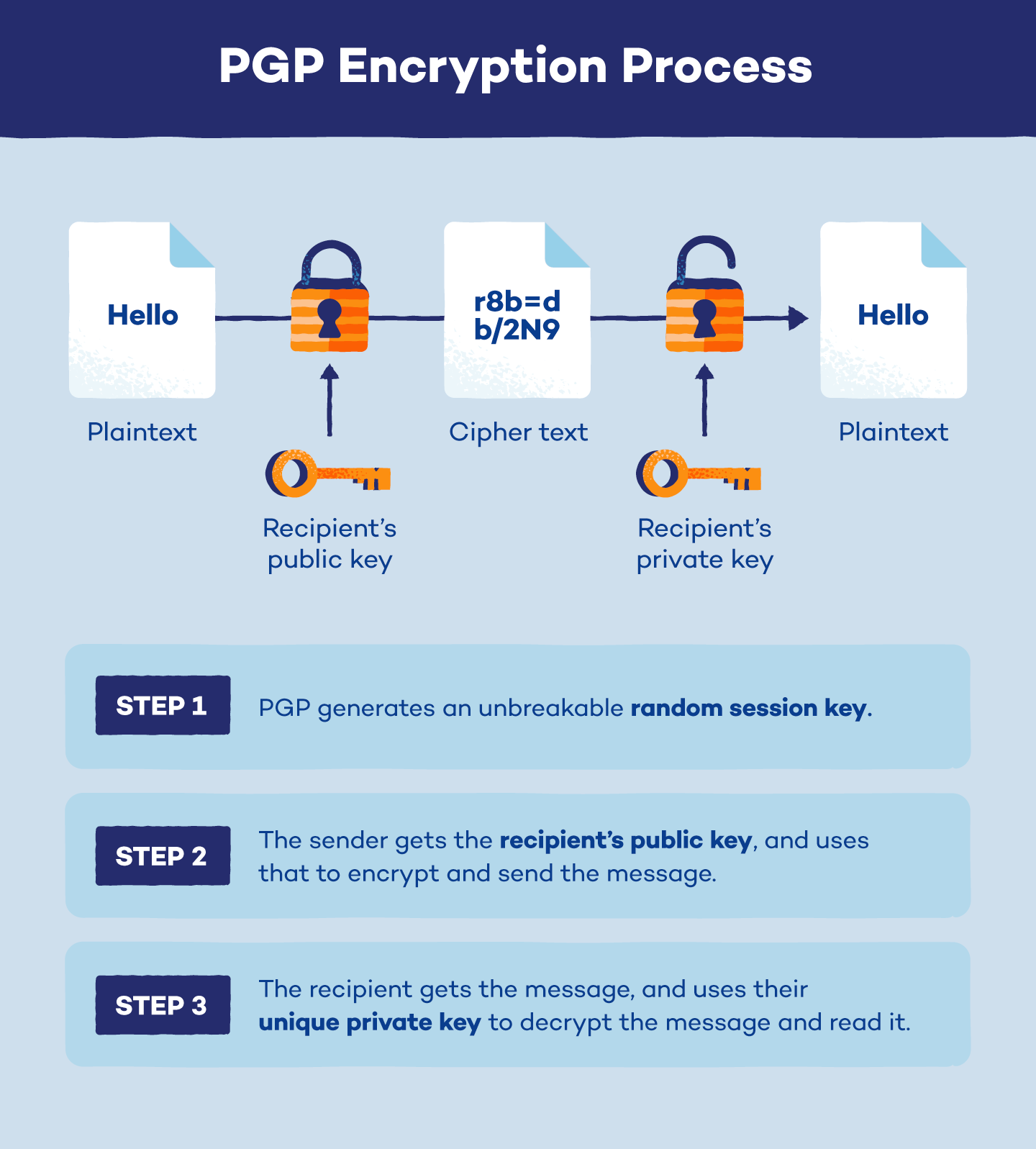
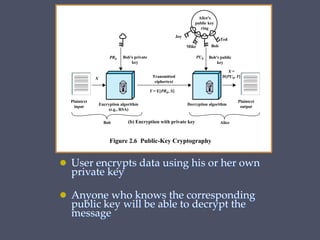
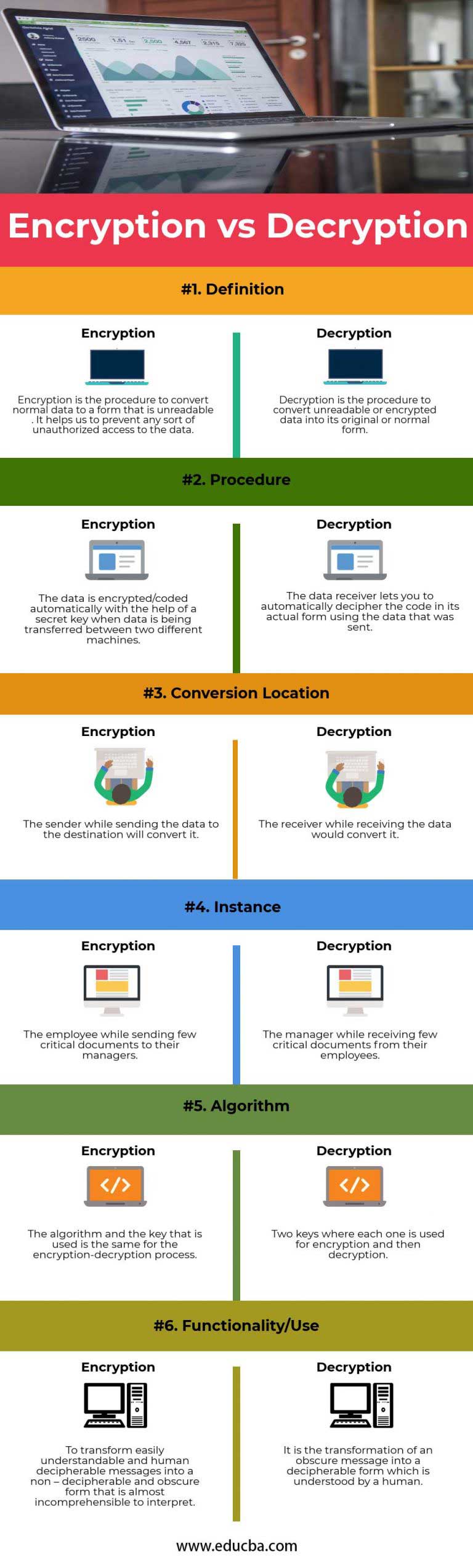
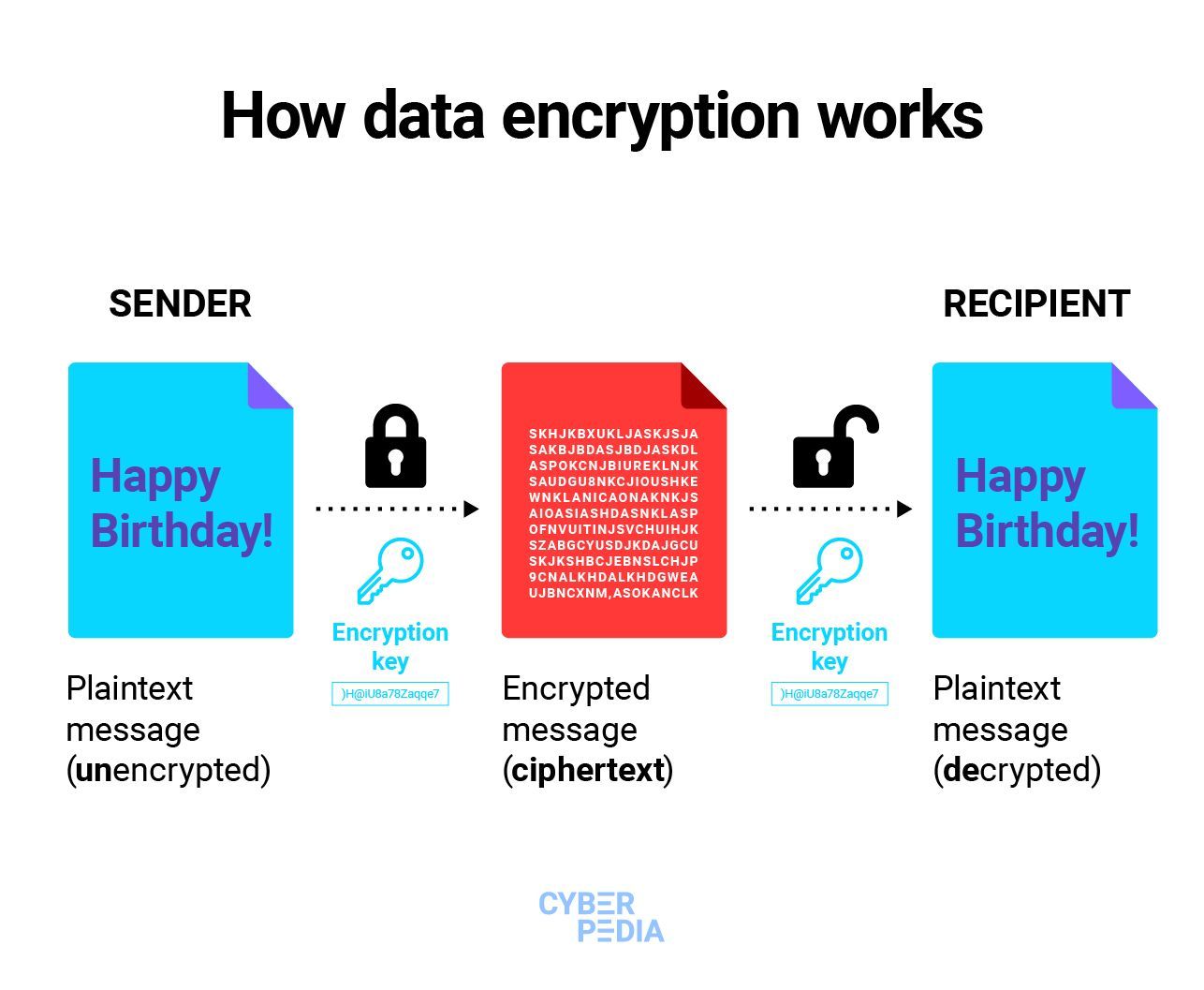
Encryption/decryption Using Our Own Messages
Collection of Encryption/decryption Using Our Own Messages featuring substantial collections of high-quality images. featuring exceptional examples of photography, images, and pictures. perfect for creative professionals and enthusiasts. Discover high-resolution Encryption/decryption Using Our Own Messages images optimized for various applications. Suitable for various applications including web design, social media, personal projects, and digital content creation All Encryption/decryption Using Our Own Messages images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Explore the versatility of our Encryption/decryption Using Our Own Messages collection for various creative and professional projects. Our Encryption/decryption Using Our Own Messages database continuously expands with fresh, relevant content from skilled photographers. Time-saving browsing features help users locate ideal Encryption/decryption Using Our Own Messages images quickly. Regular updates keep the Encryption/decryption Using Our Own Messages collection current with contemporary trends and styles. Reliable customer support ensures smooth experience throughout the Encryption/decryption Using Our Own Messages selection process. Advanced search capabilities make finding the perfect Encryption/decryption Using Our Own Messages image effortless and efficient. Diverse style options within the Encryption/decryption Using Our Own Messages collection suit various aesthetic preferences.







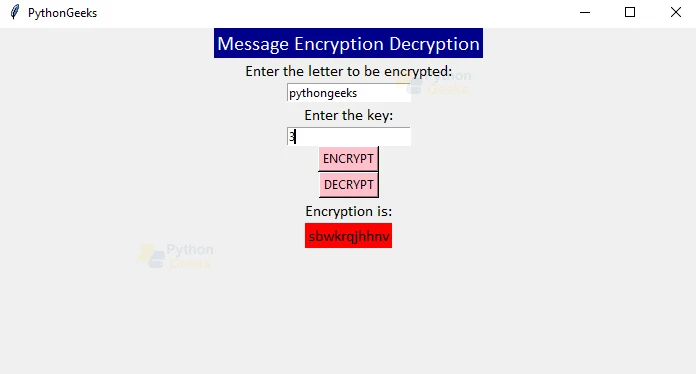
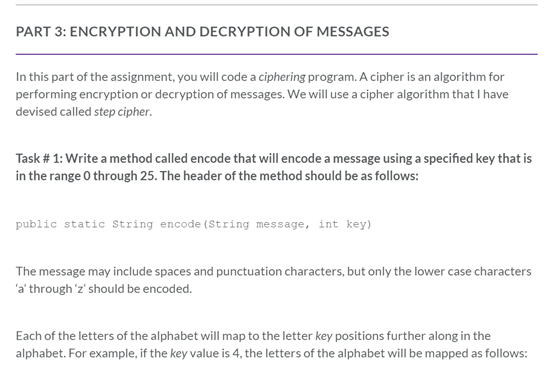
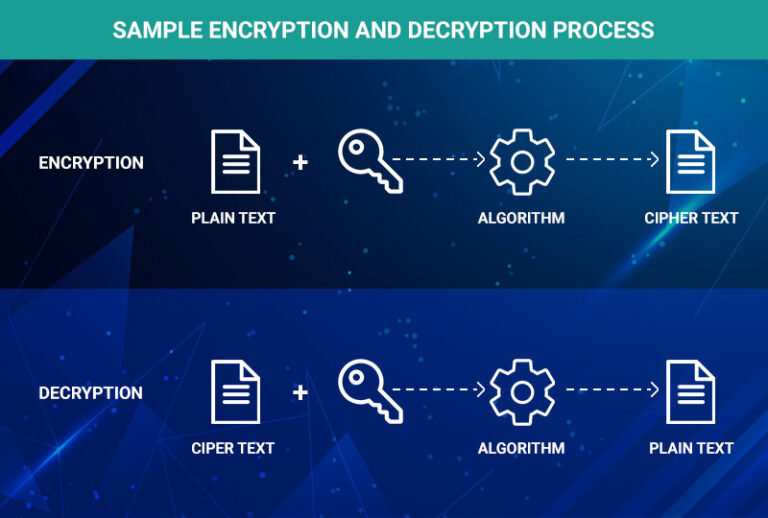


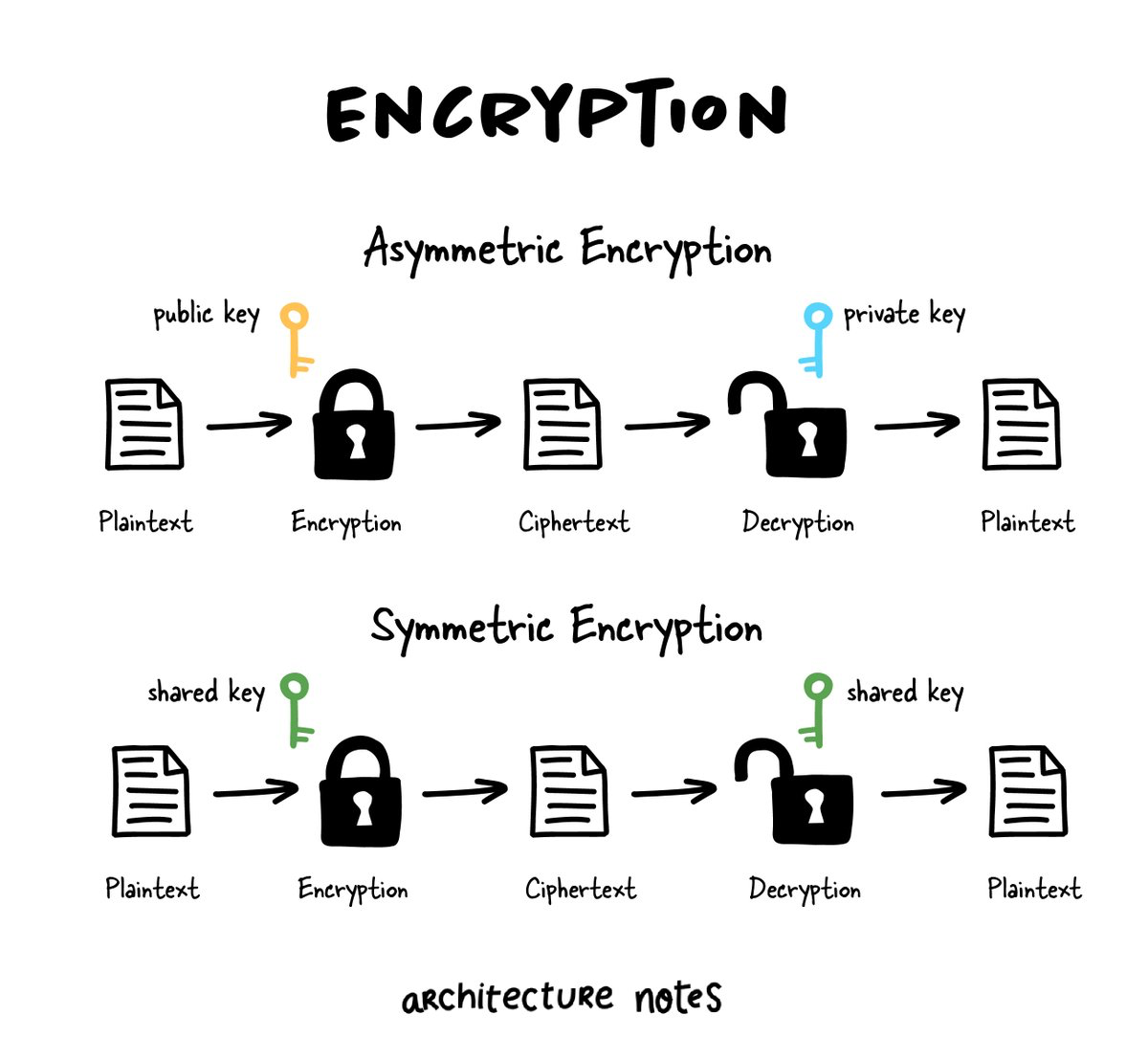




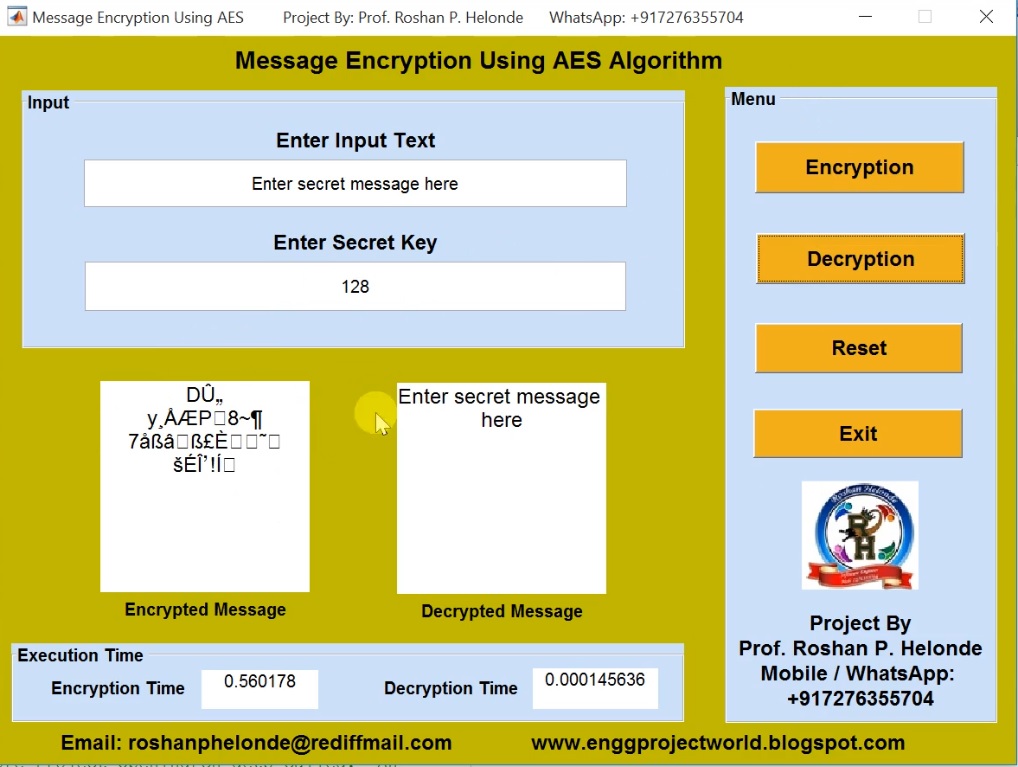
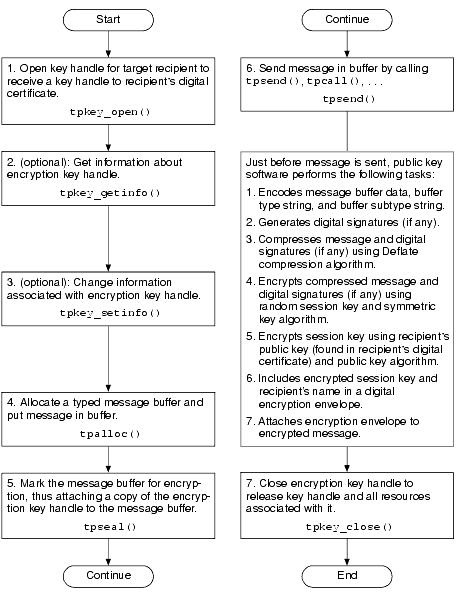

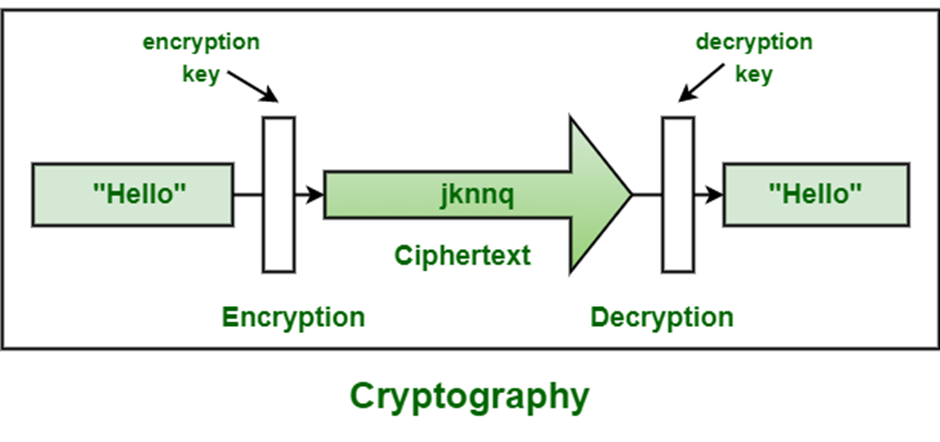
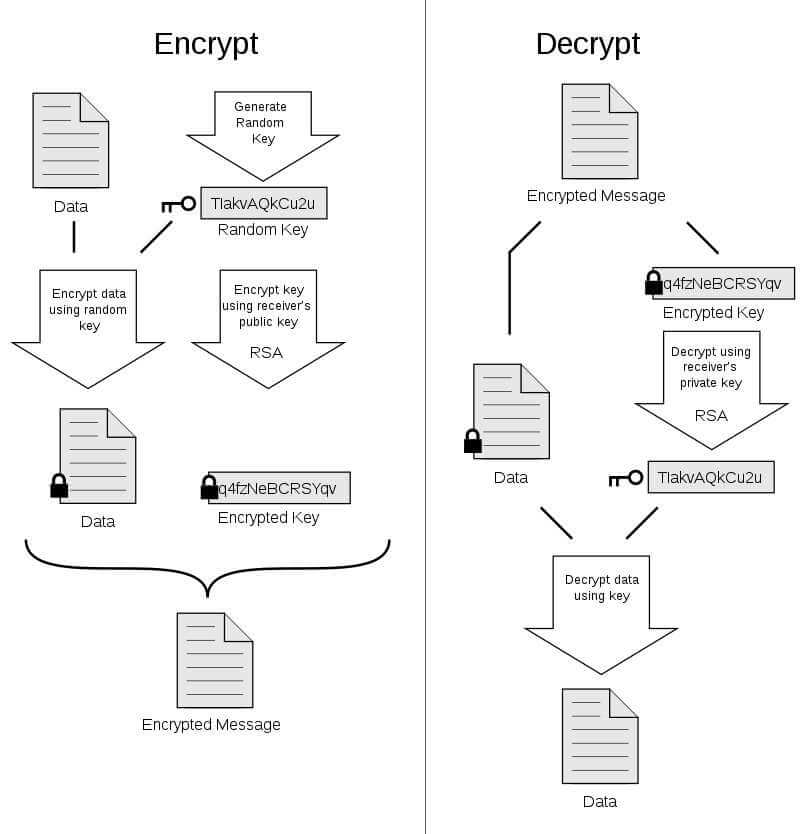
![Introduction to Encryption [Part 01] : Understanding the Basics - Codimite](https://codimite.flywheelstaging.com/wp-content/uploads/diagram-1.webp)
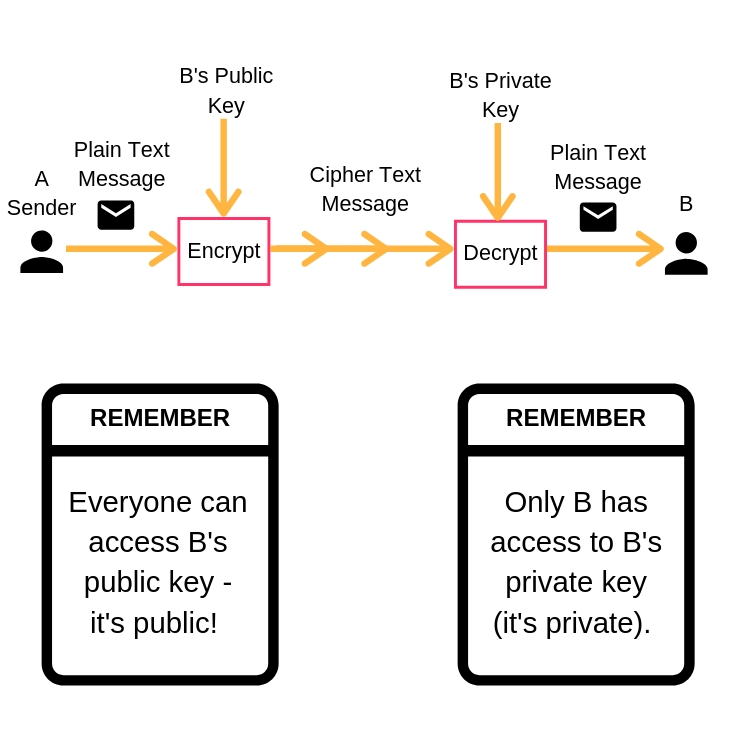







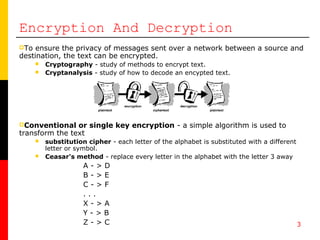

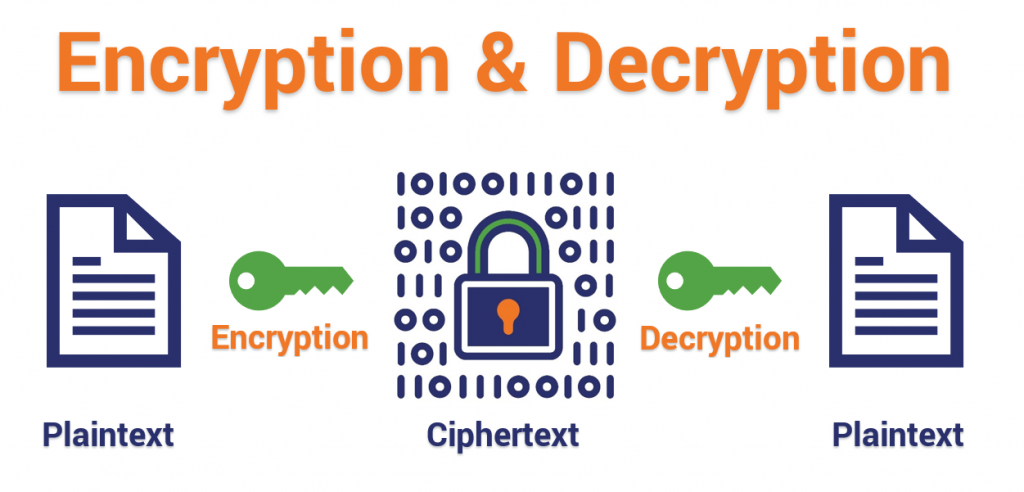

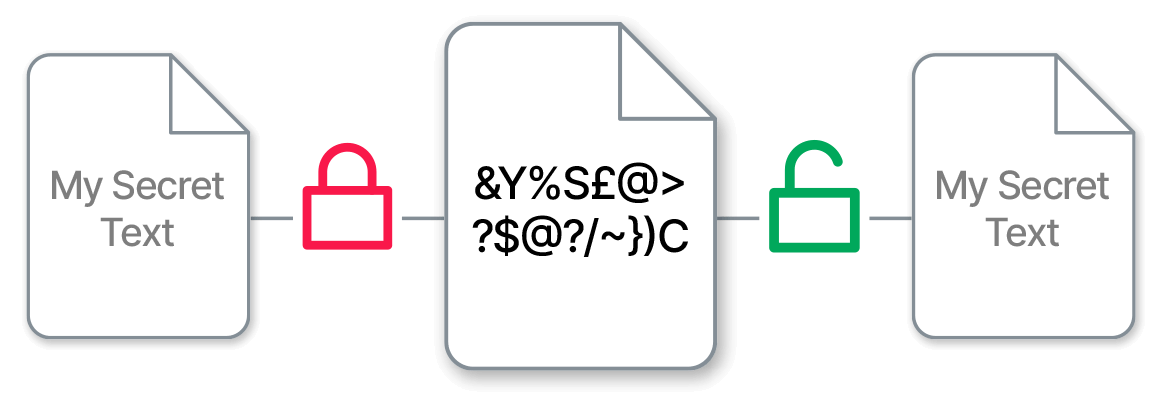
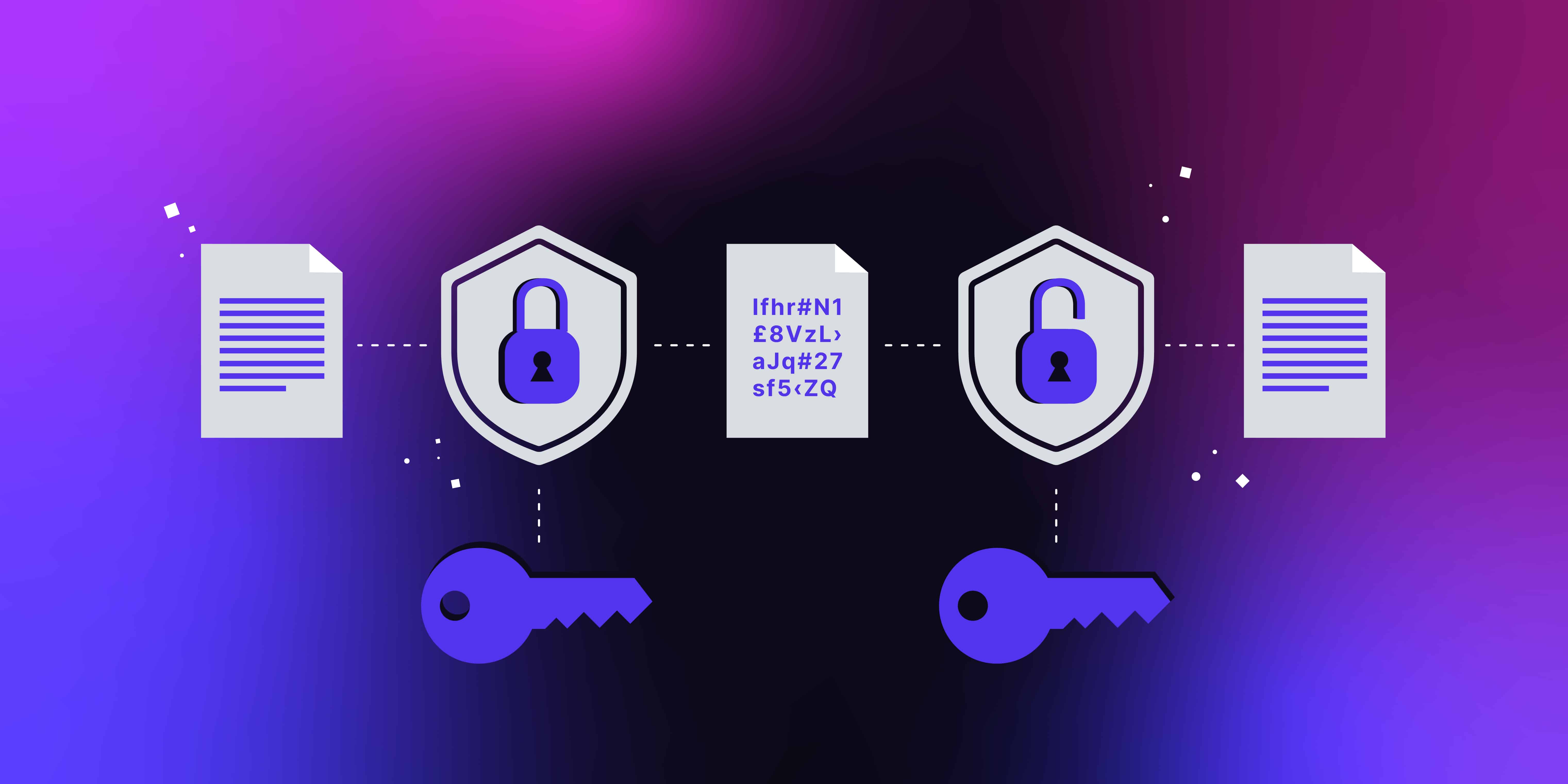
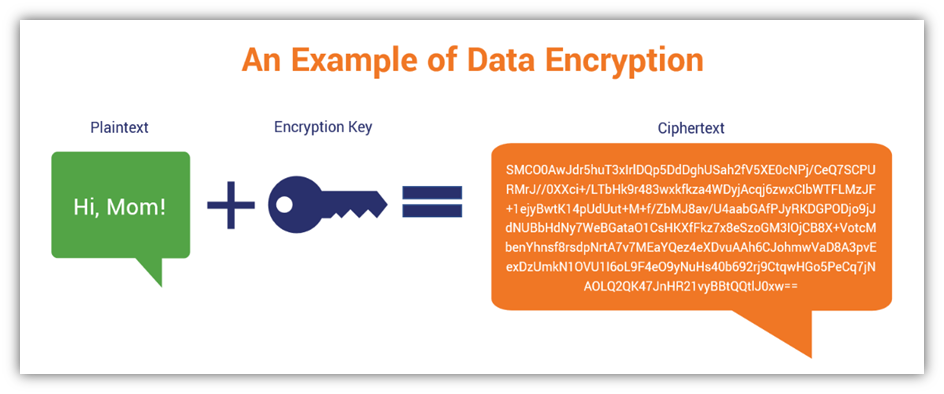
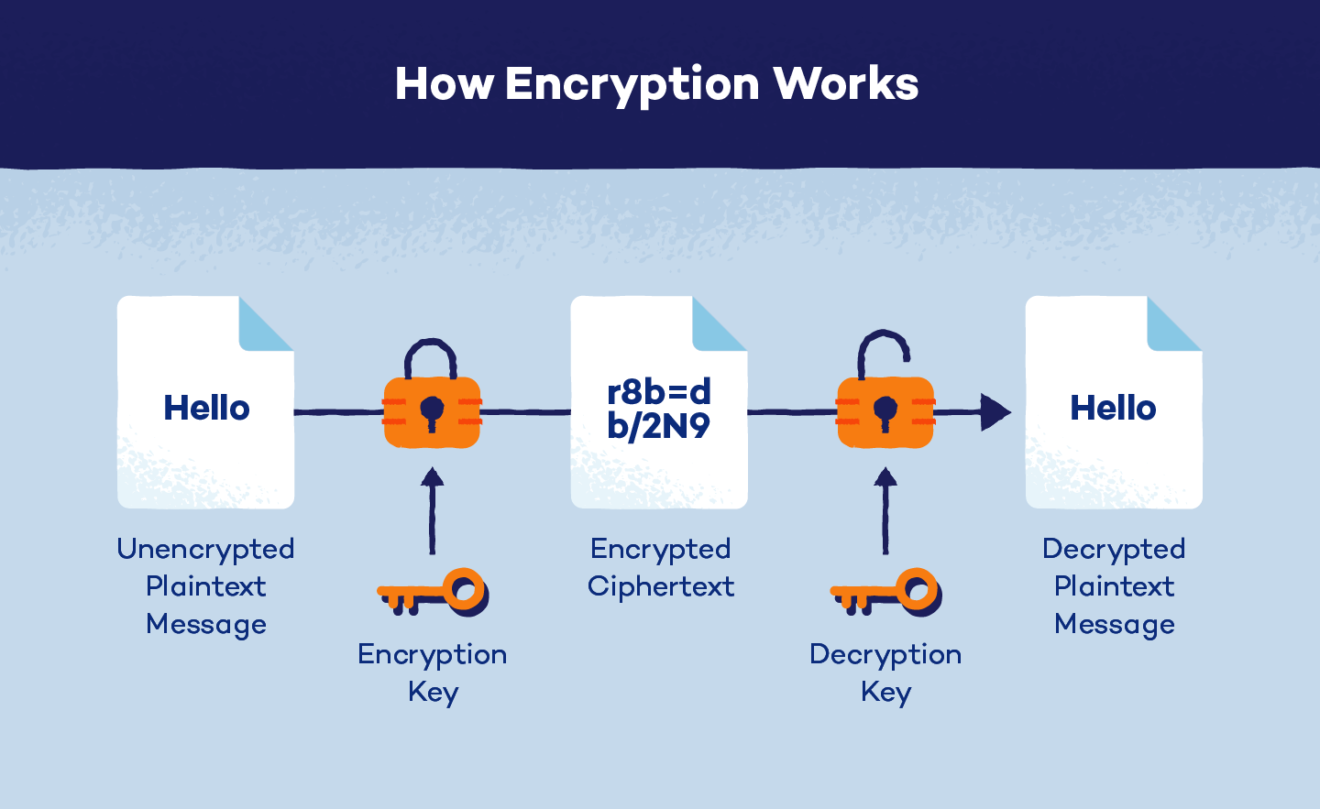

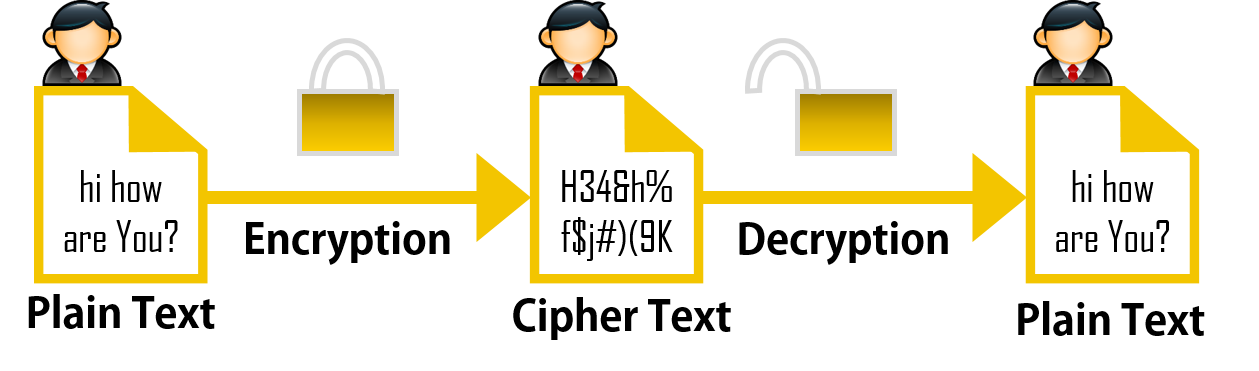

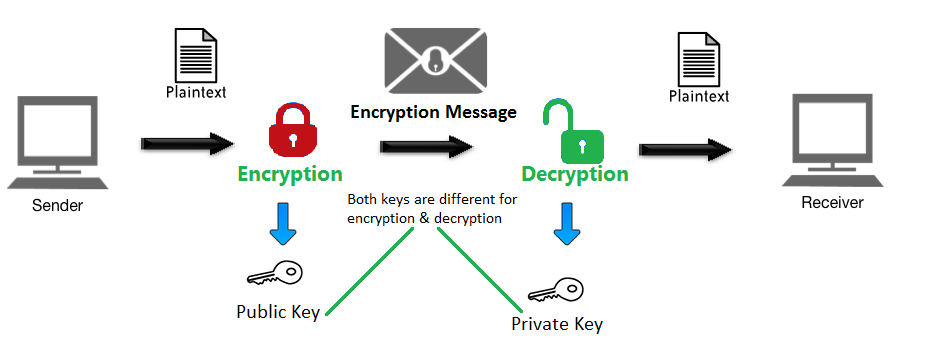







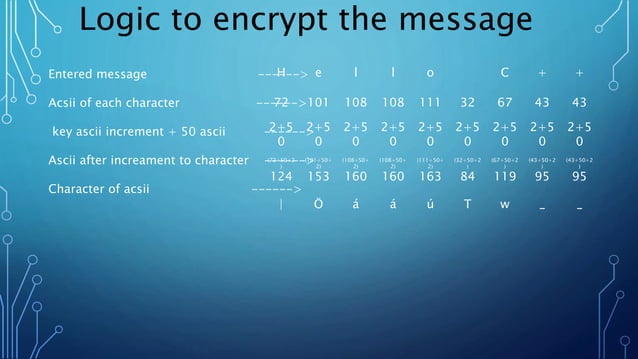
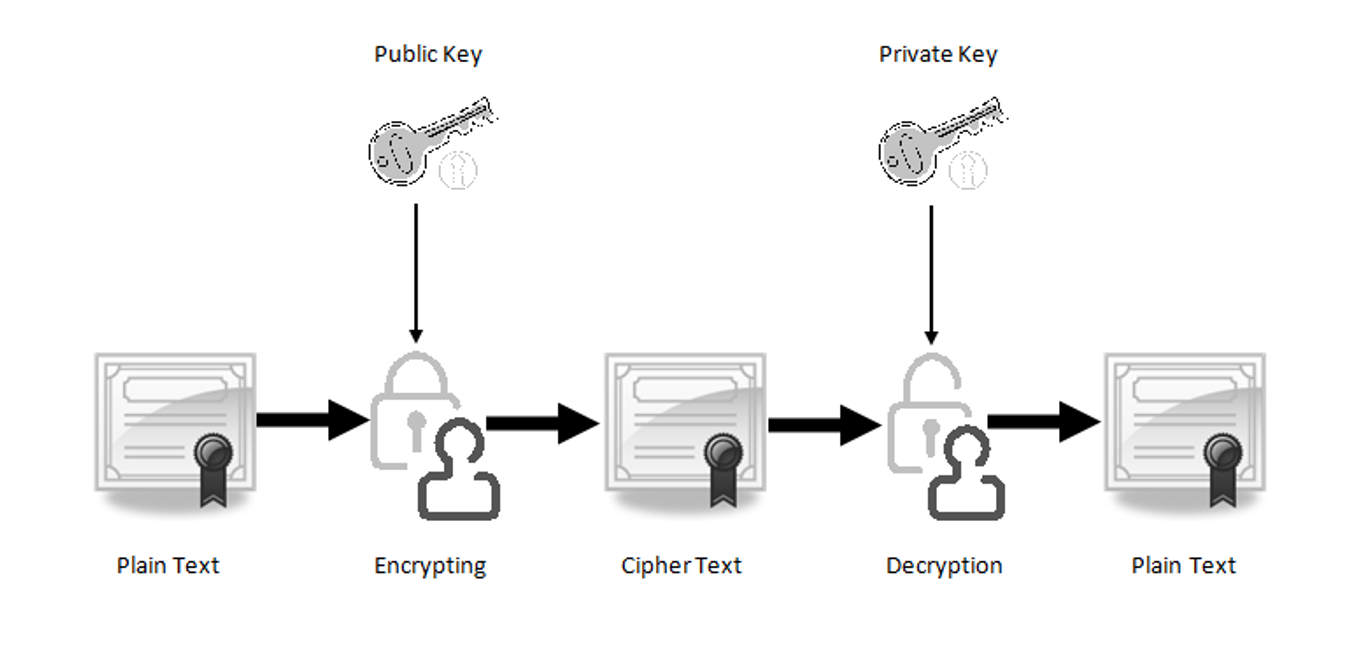
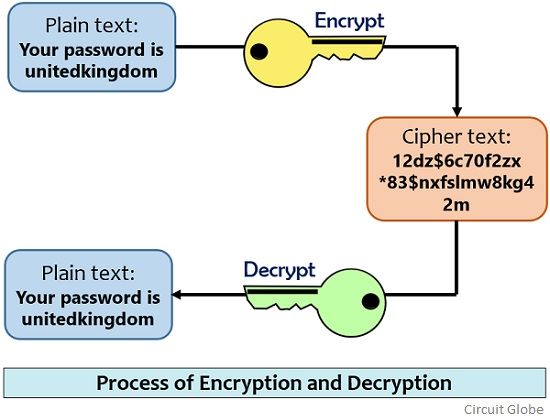
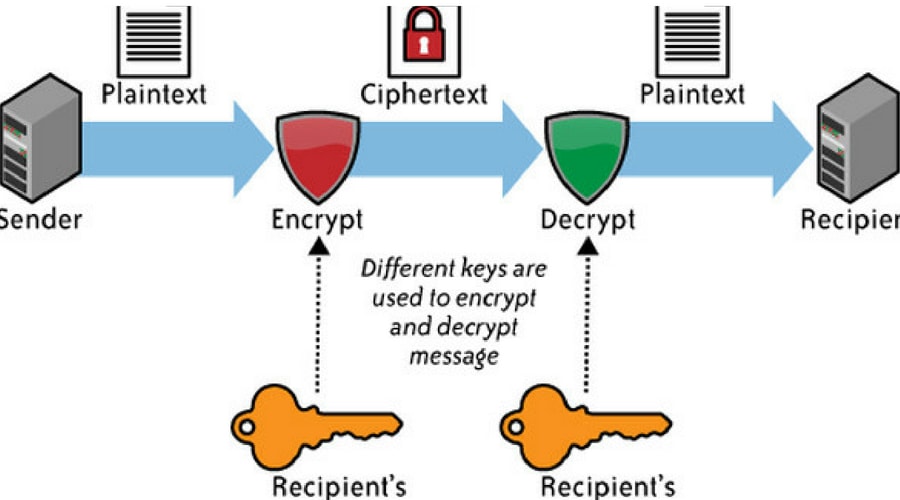
+to+perform+the+encryption+and+decryption.+Encryption+algorithms+can+be+divided+into+two+groups:+symmetric+and+asymmetric%2C+which+differ+in+the+way+the+encryption+keys+are+used..jpg)

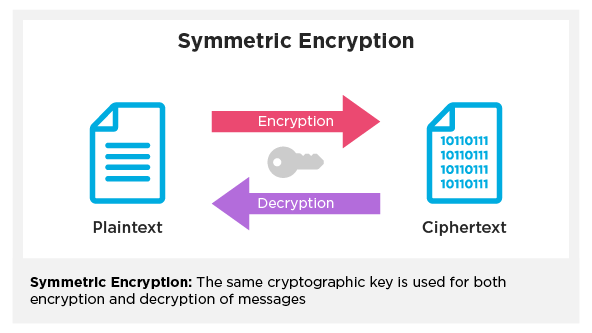




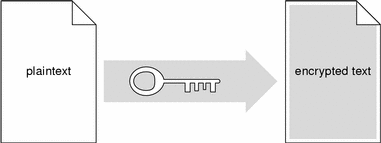
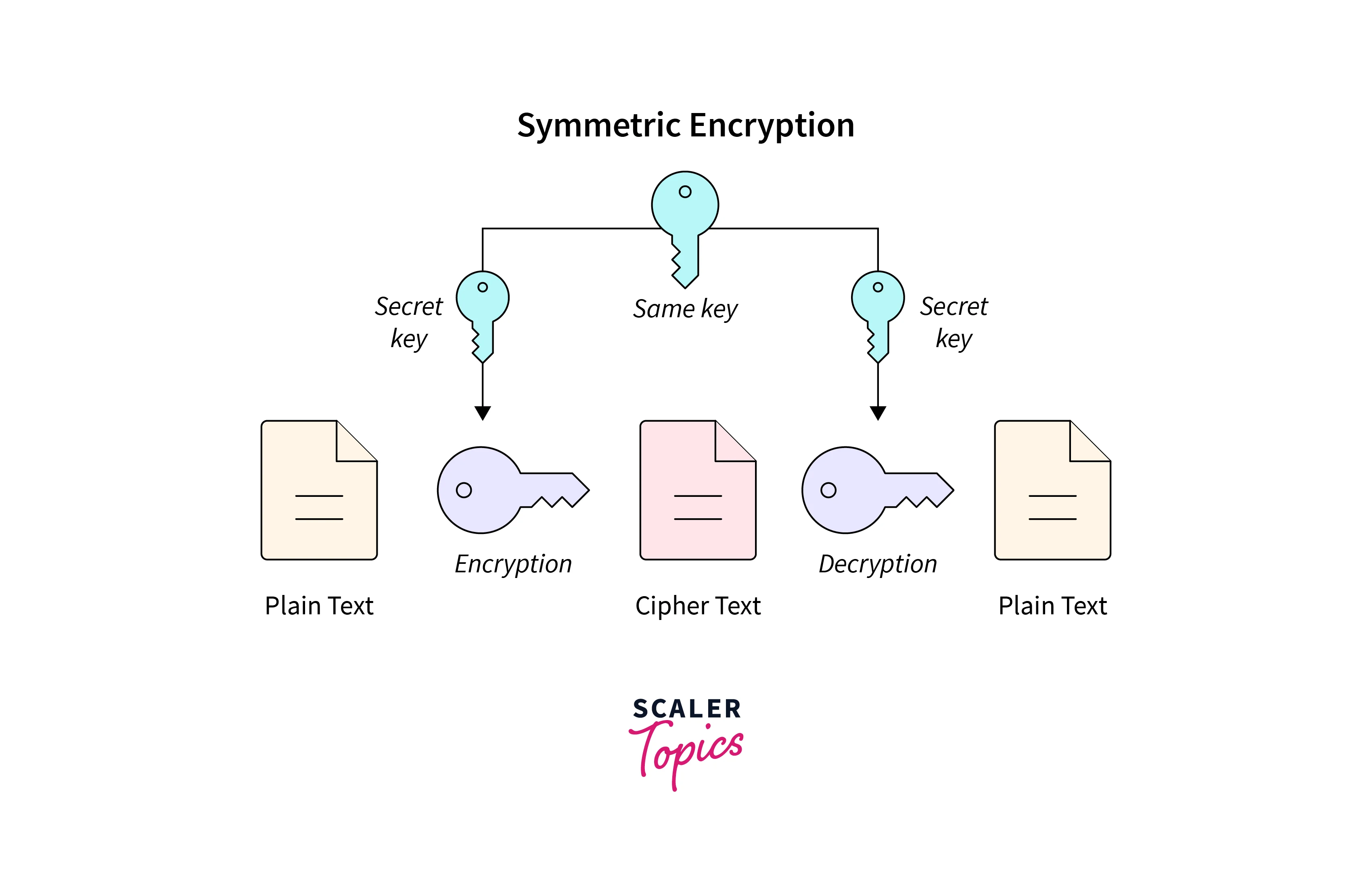
.jpg)





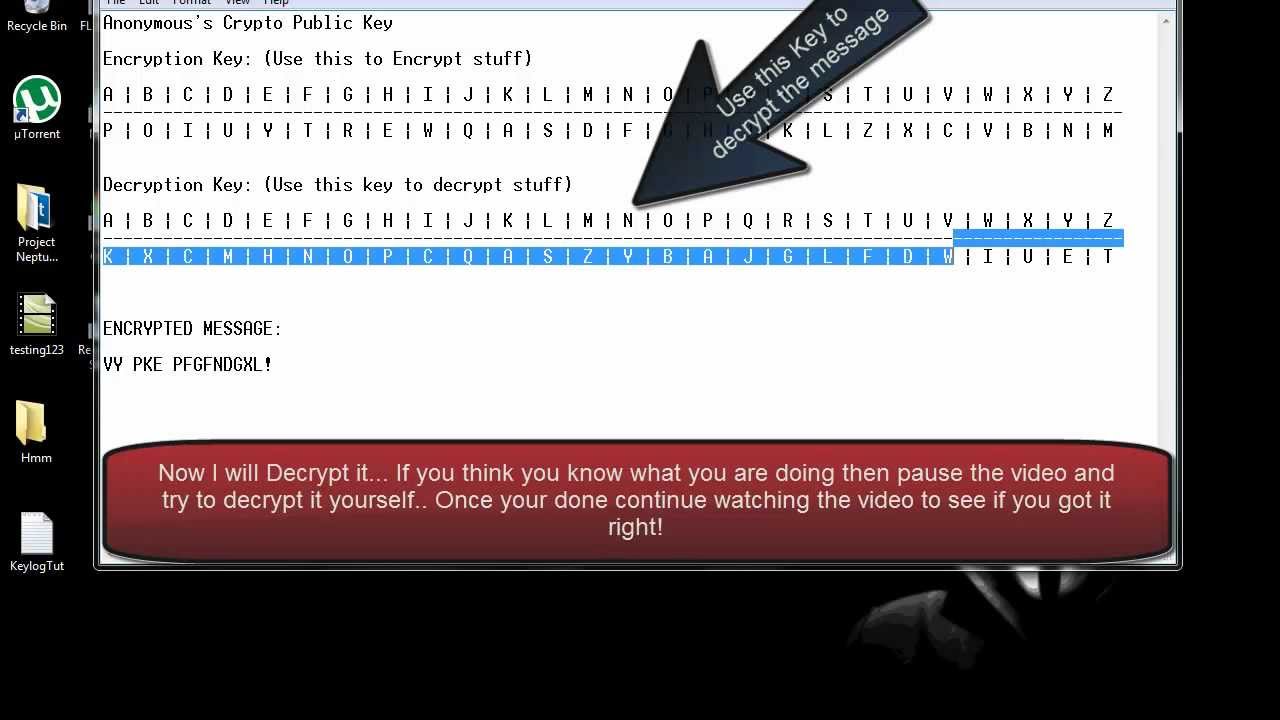


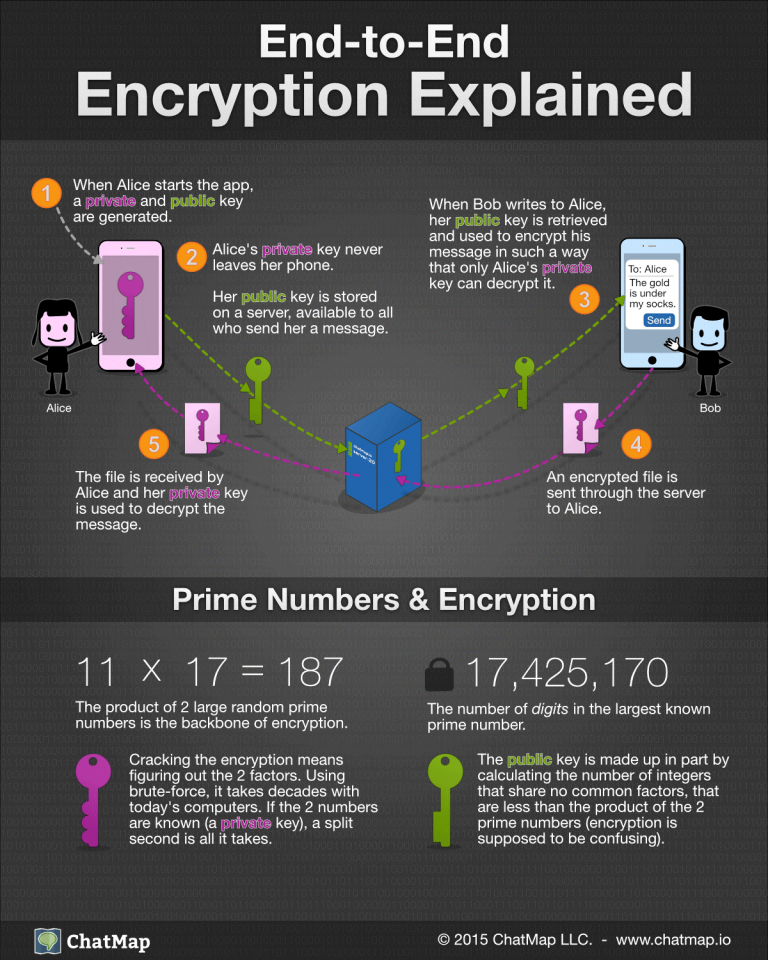
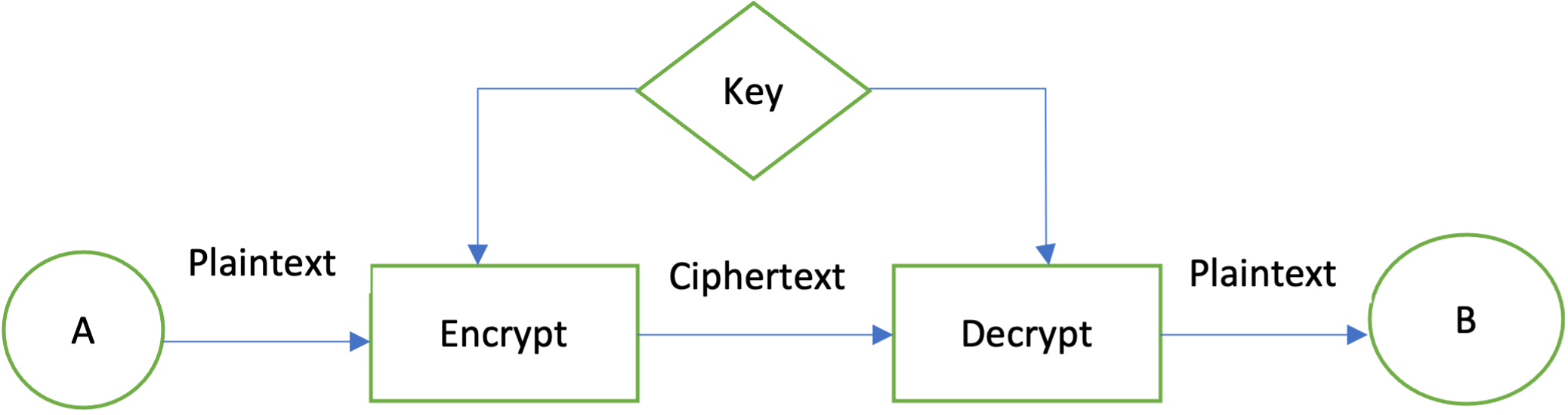
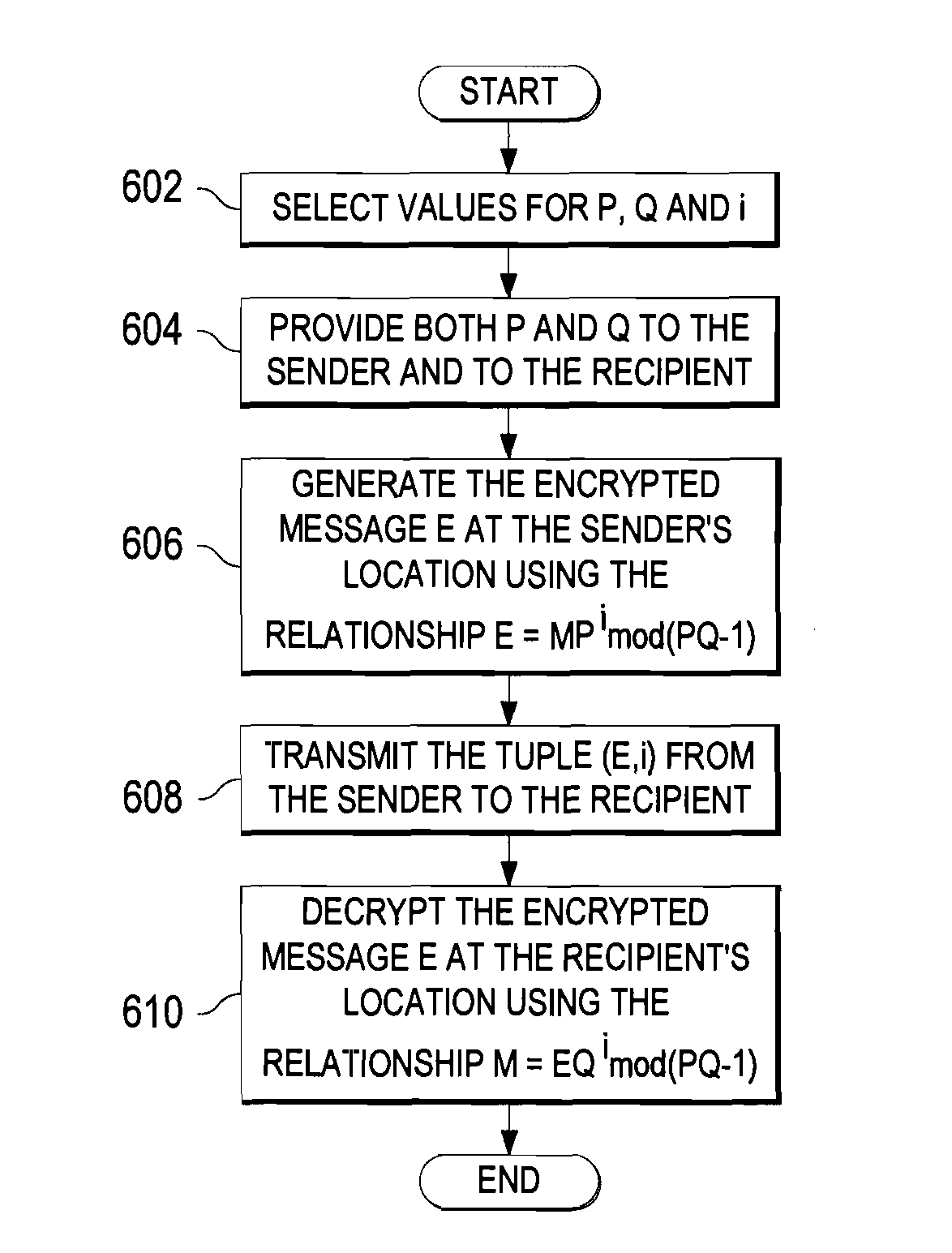
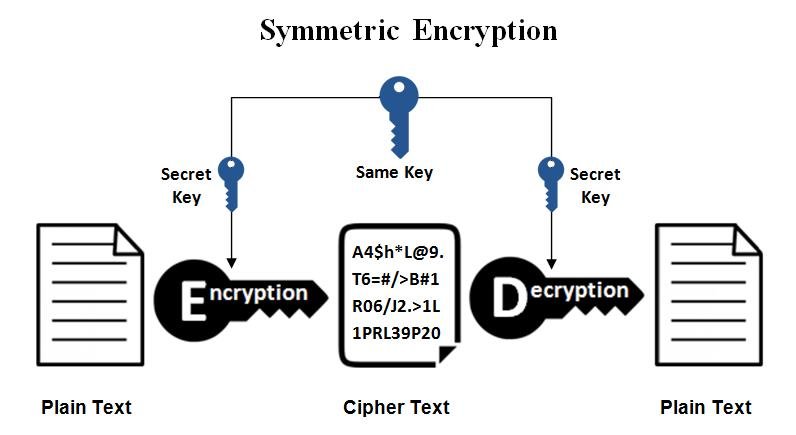
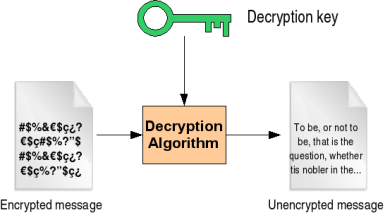
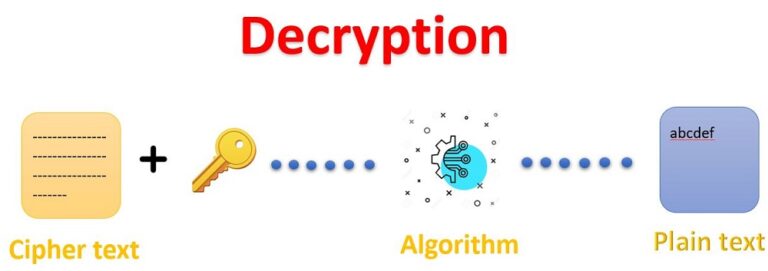
![[Chapter 6] 6.2 What Is Encryption?](https://web.deu.edu.tr/doc/oreily/networking/puis/figs/puis_0601.gif)