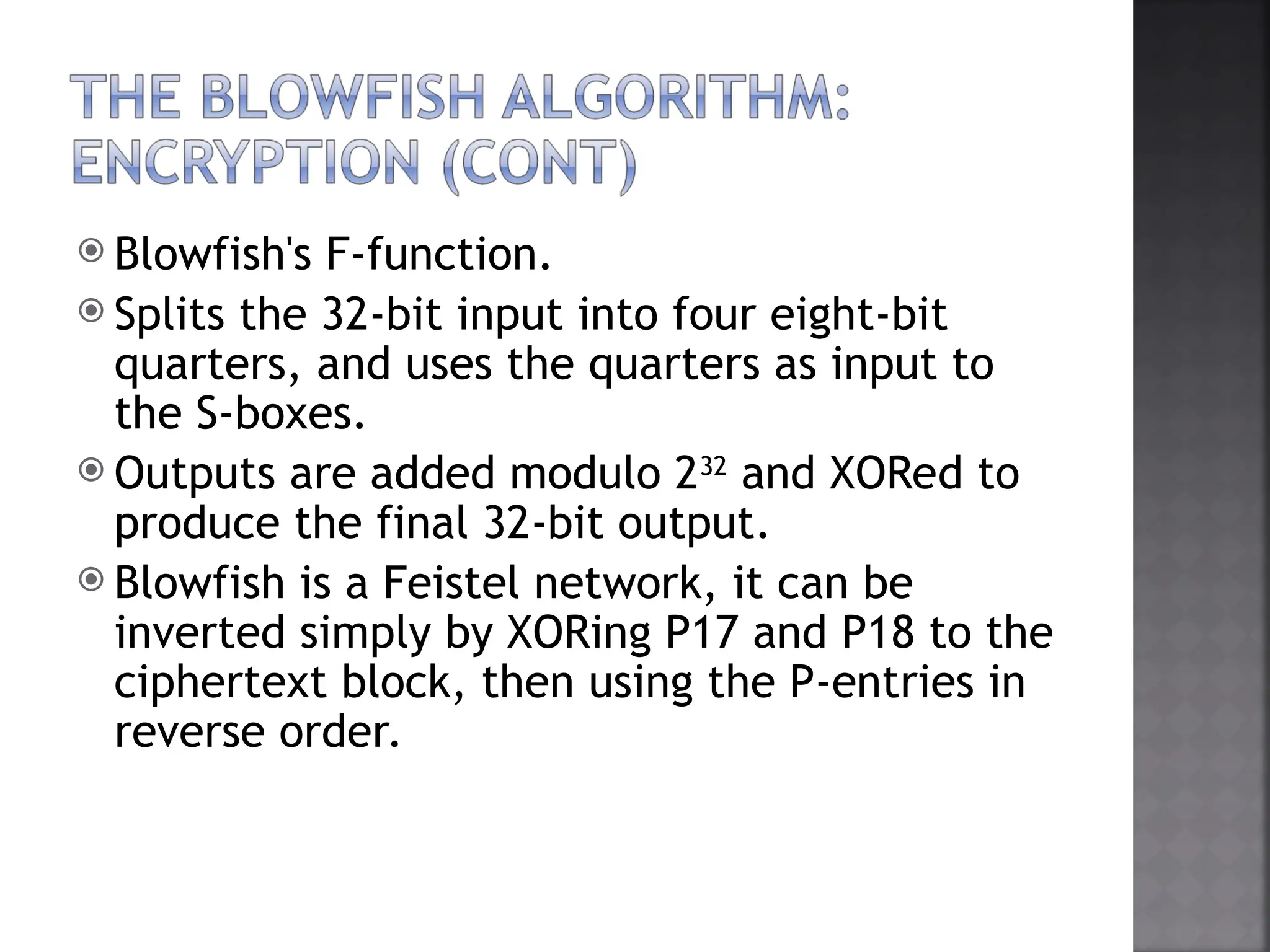
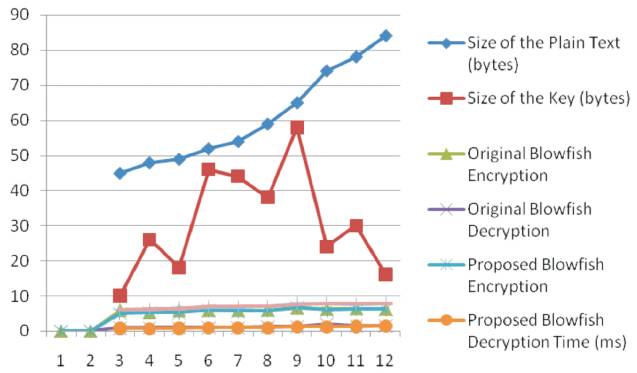
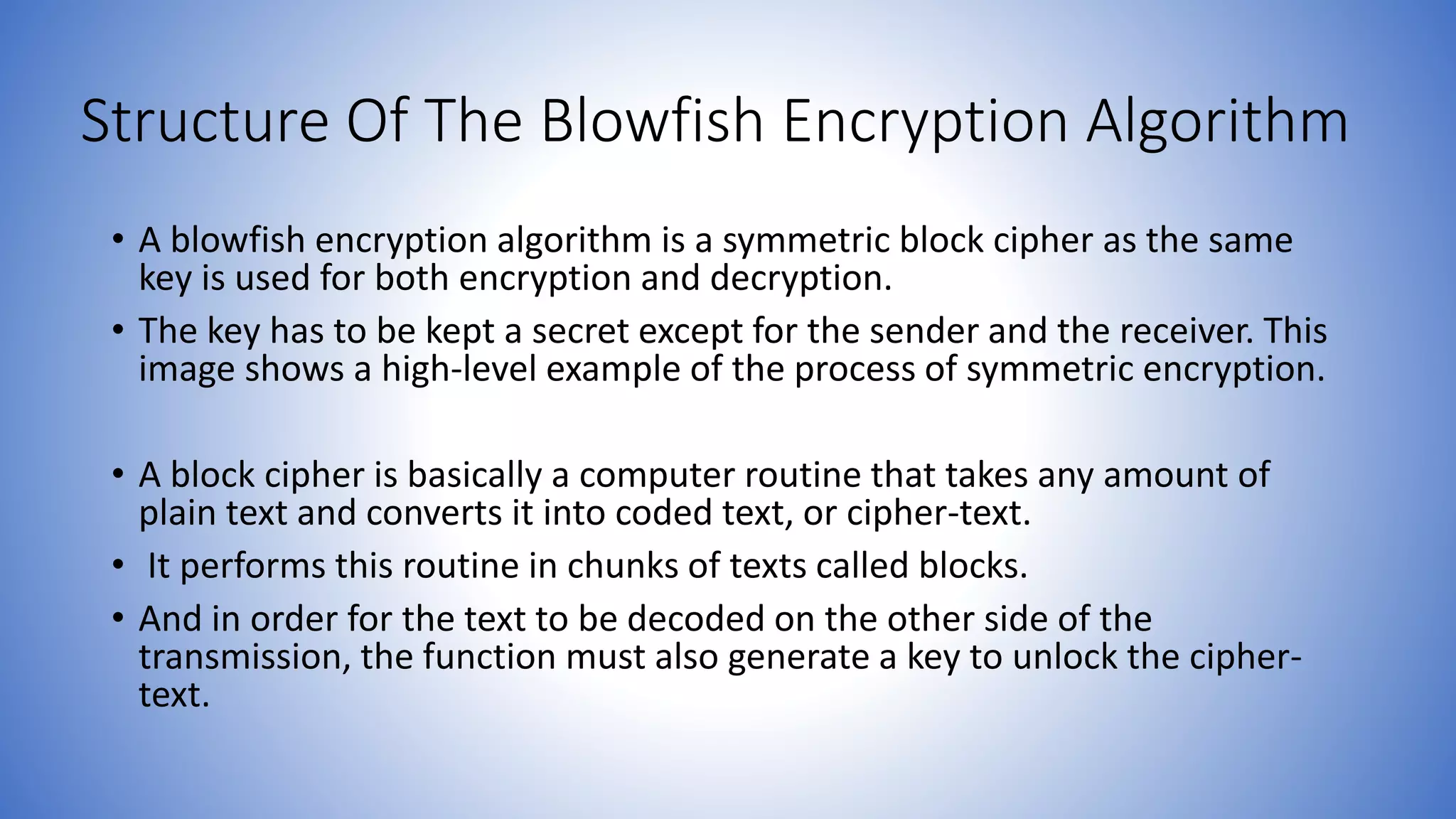
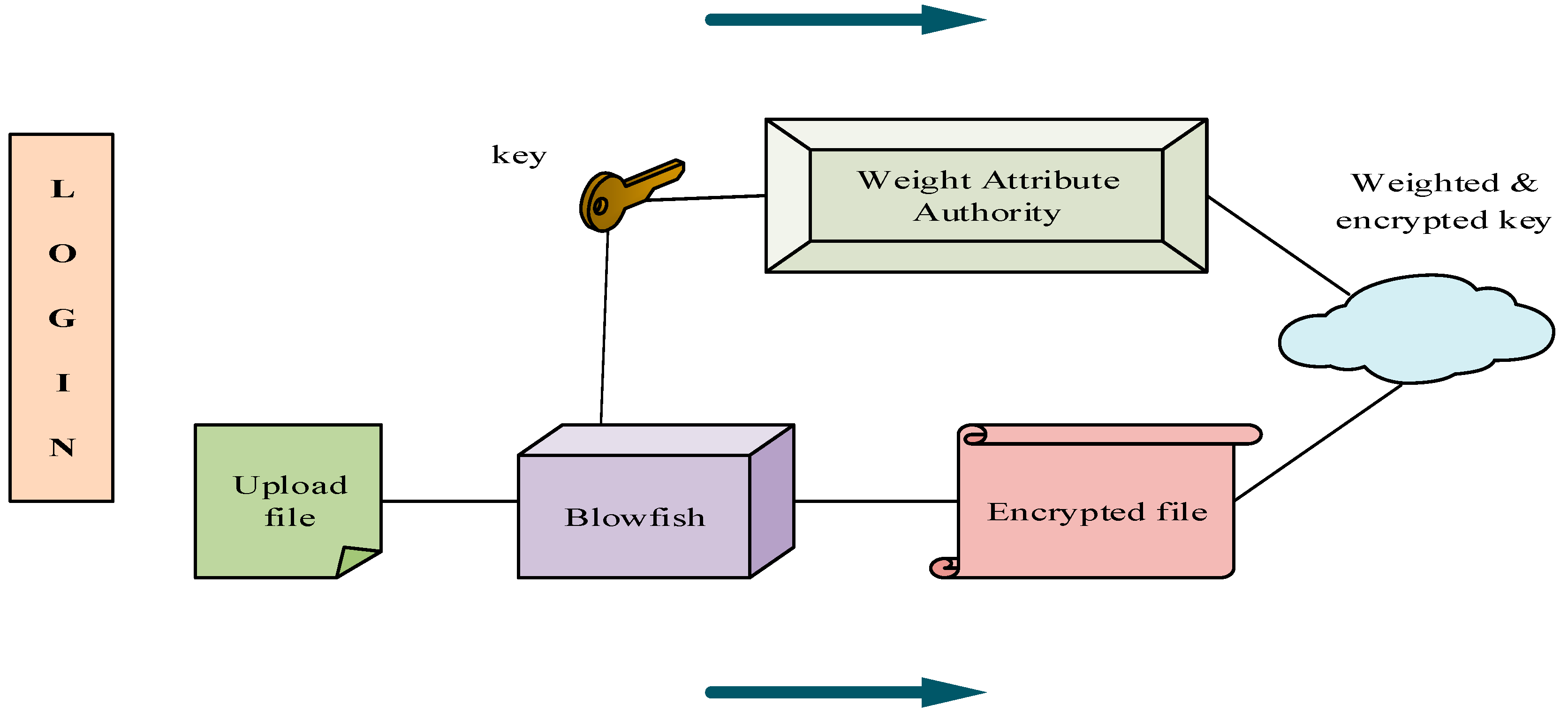
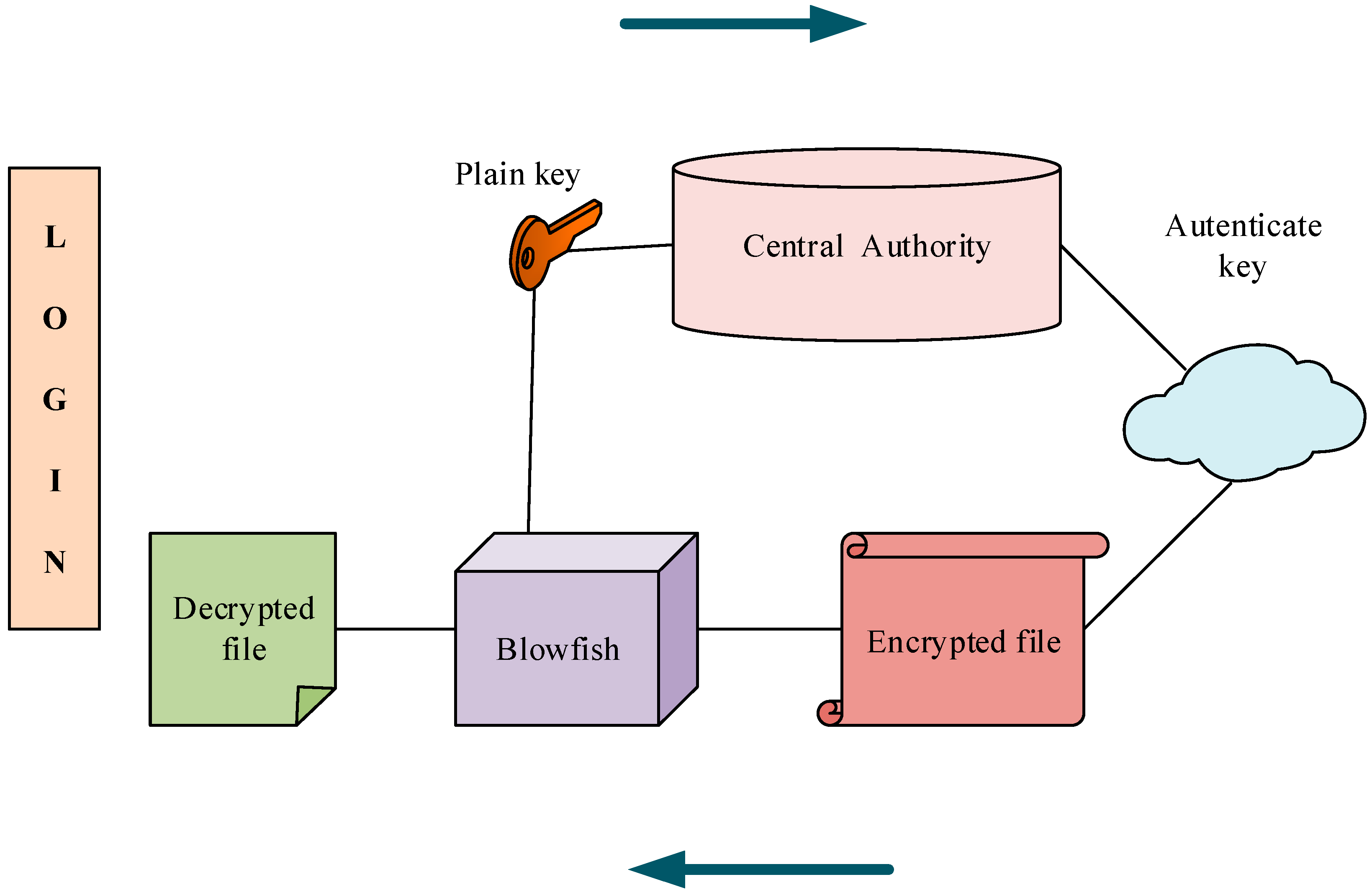
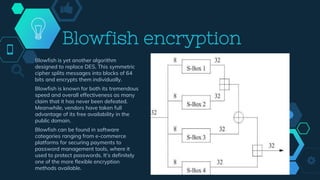
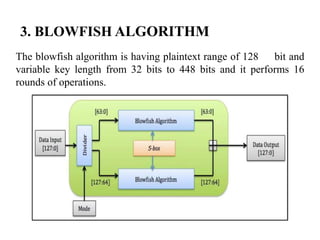
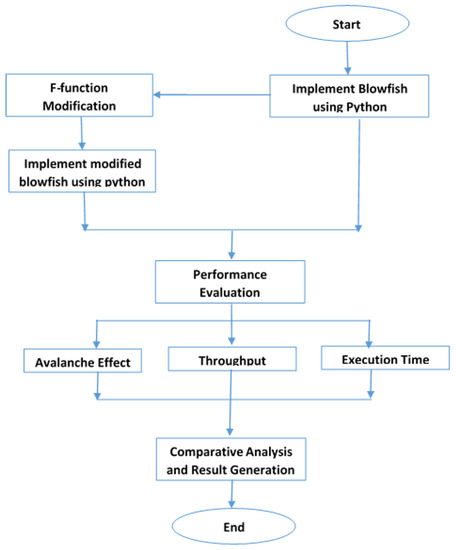
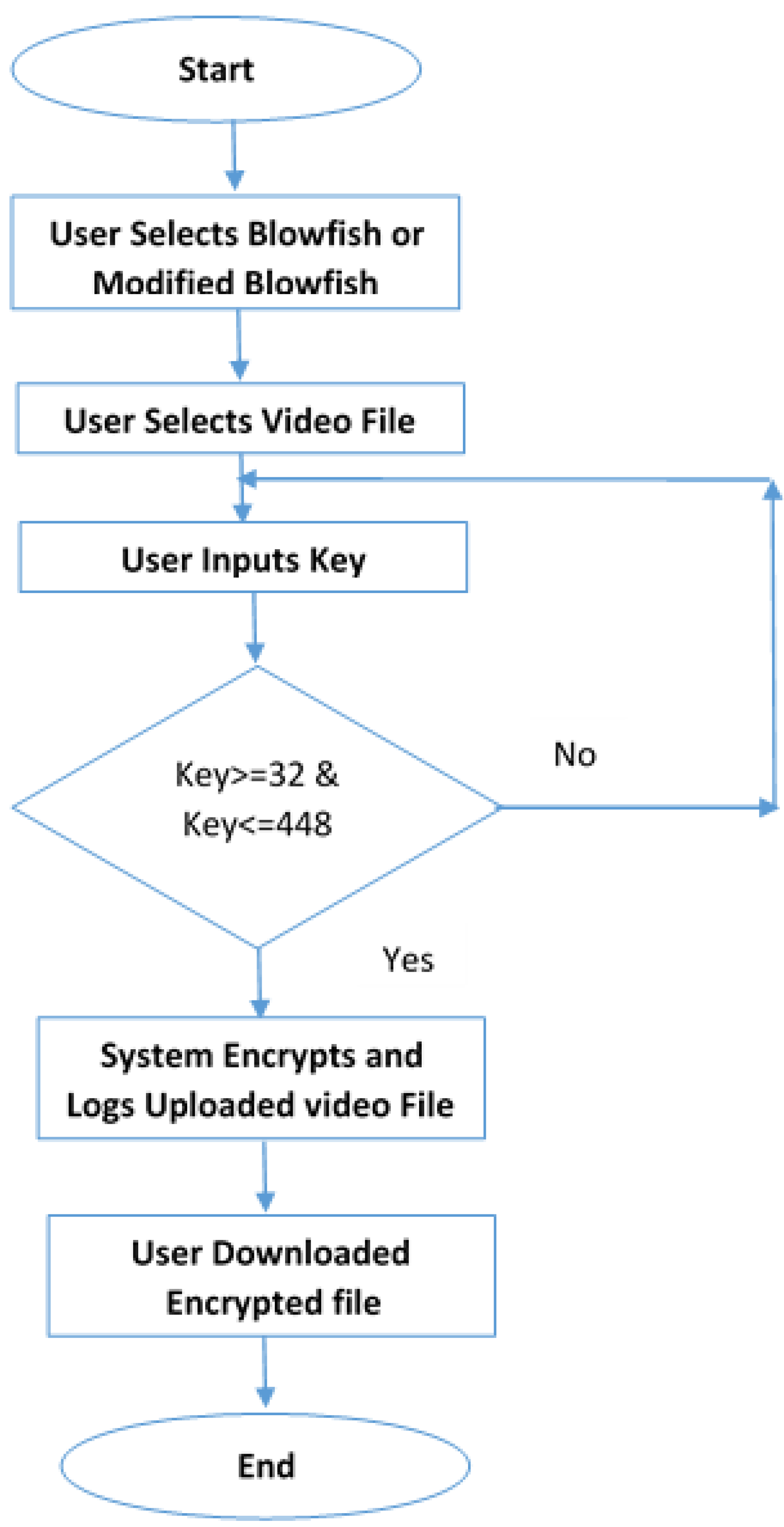
Encryption Process In Blowfish Algorithm
Explore the educational aspects of Encryption Process In Blowfish Algorithm through substantial collections of informative visual resources. designed to support various learning styles and educational approaches. making complex concepts accessible through visual learning. Each Encryption Process In Blowfish Algorithm image is carefully selected for superior visual impact and professional quality. Excellent for educational materials, academic research, teaching resources, and learning activities All Encryption Process In Blowfish Algorithm images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. The Encryption Process In Blowfish Algorithm collection serves as a valuable educational resource for teachers and students. Diverse style options within the Encryption Process In Blowfish Algorithm collection suit various aesthetic preferences. Multiple resolution options ensure optimal performance across different platforms and applications. Comprehensive tagging systems facilitate quick discovery of relevant Encryption Process In Blowfish Algorithm content. Our Encryption Process In Blowfish Algorithm database continuously expands with fresh, relevant content from skilled photographers. The Encryption Process In Blowfish Algorithm archive serves professionals, educators, and creatives across diverse industries. Professional licensing options accommodate both commercial and educational usage requirements. Cost-effective licensing makes professional Encryption Process In Blowfish Algorithm photography accessible to all budgets.







![Blowfish encryption algorithm [12–15, 17, 21]. | Download Scientific ...](https://www.researchgate.net/publication/350655579/figure/fig12/AS:1080288960610396@1634572367573/Blowfish-encryption-algorithm-12-15-17-21.jpg)


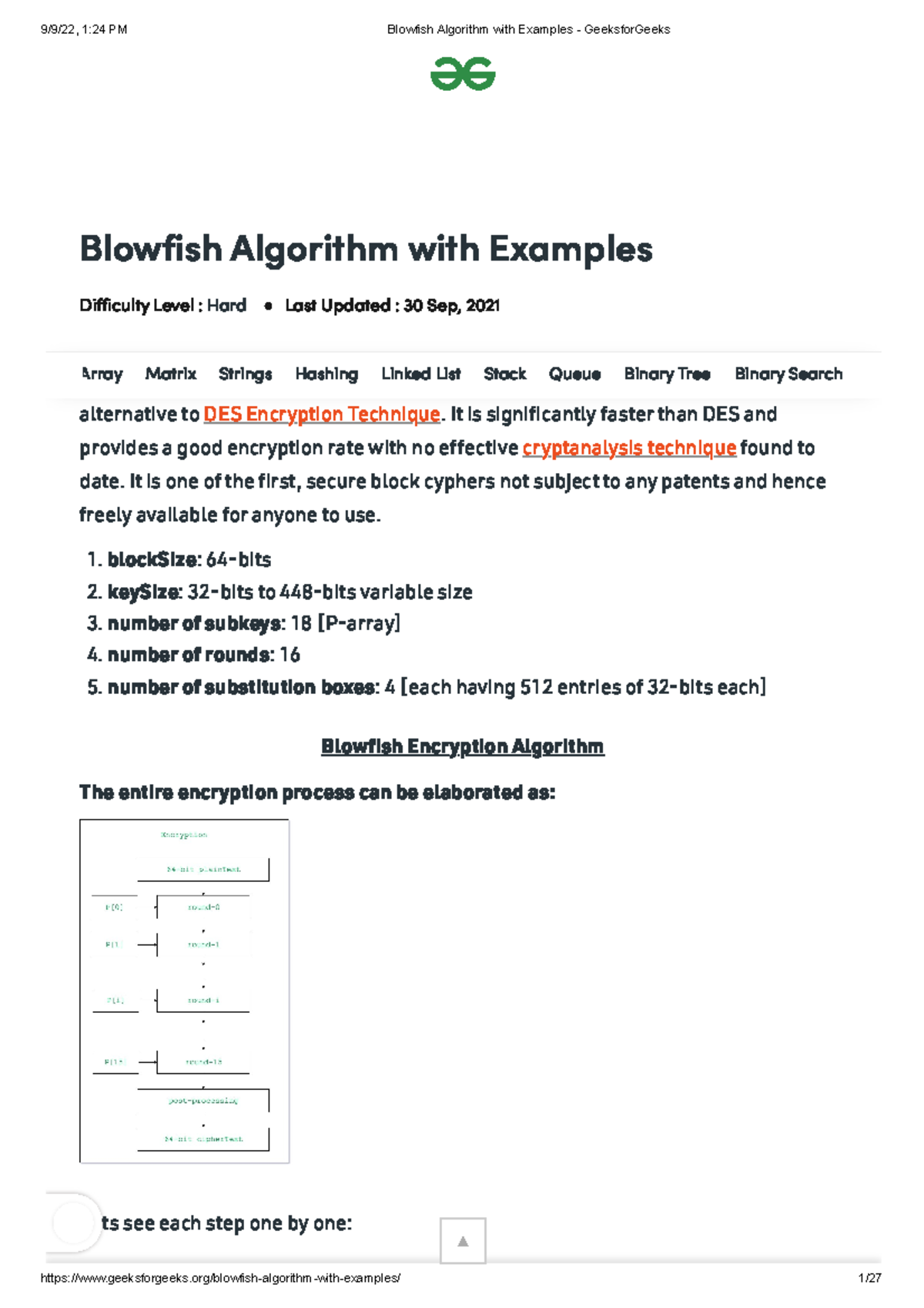

![Blowfish encryption algorithm [10]. | Download Scientific Diagram](https://www.researchgate.net/publication/345326563/figure/fig2/AS:963464793178141@1606719315413/Proposed-model_Q640.jpg)


![Blowfish encryption algorithm [10]. | Download Scientific Diagram](https://www.researchgate.net/publication/345326563/figure/fig3/AS:963464793161756@1606719315697/Block-healthnet-architecture_Q640.jpg)

![Blowfish encryption algorithm [10]. | Download Scientific Diagram](https://www.researchgate.net/profile/Farah-Hemeida/publication/336921734/figure/fig4/AS:820049786990594@1572526513563/Block-diagram-of-the-proposed-scheme_Q320.jpg)
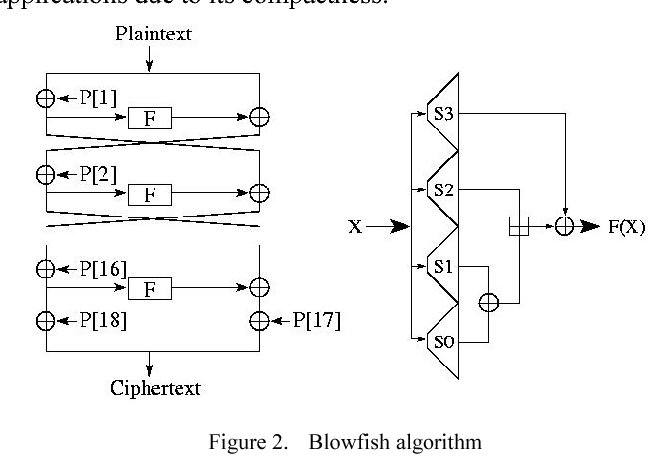




















![Encryption in blowfish algorithm[7]. | Download Scientific Diagram](https://www.researchgate.net/publication/350417078/figure/fig3/AS:1043773178007554@1625866326973/Encryption-in-blowfish-algorithm7.png)