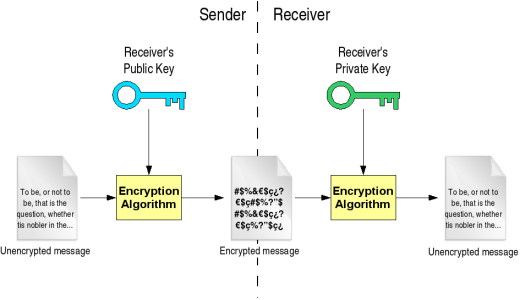
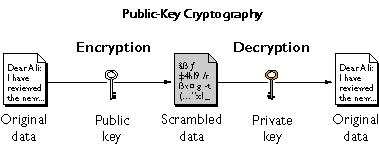
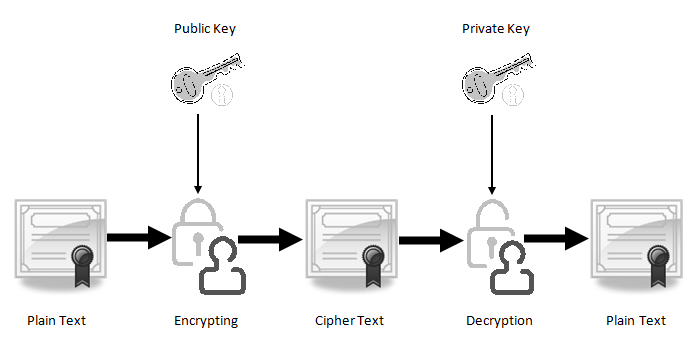
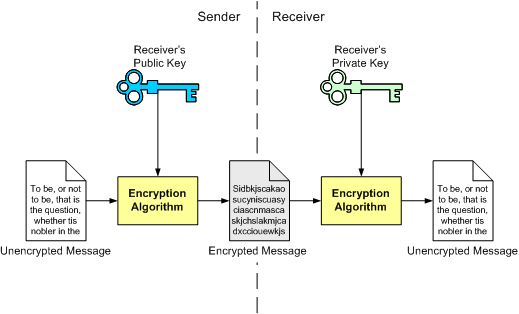
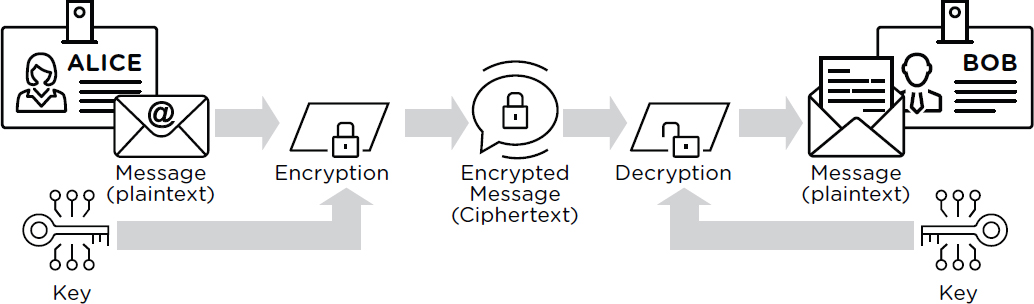
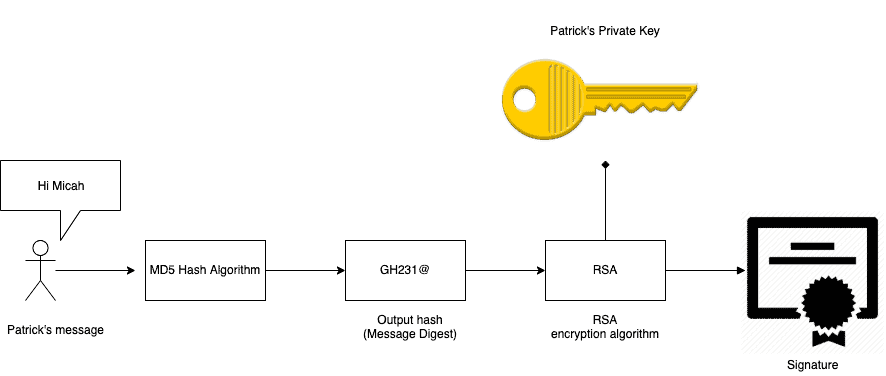
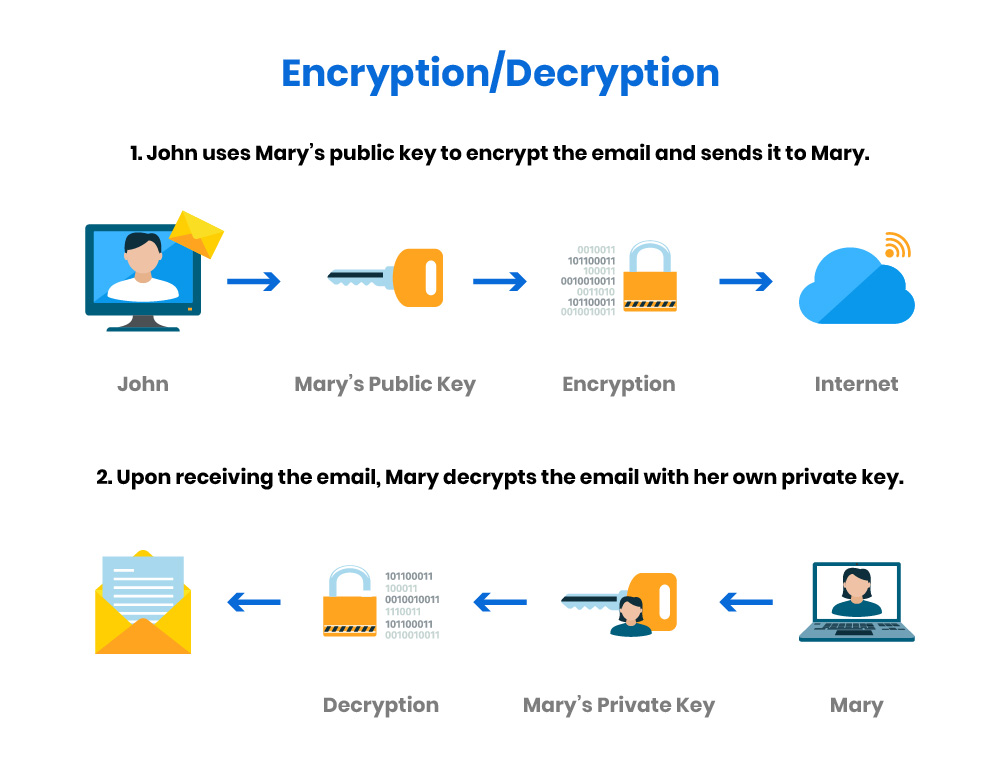
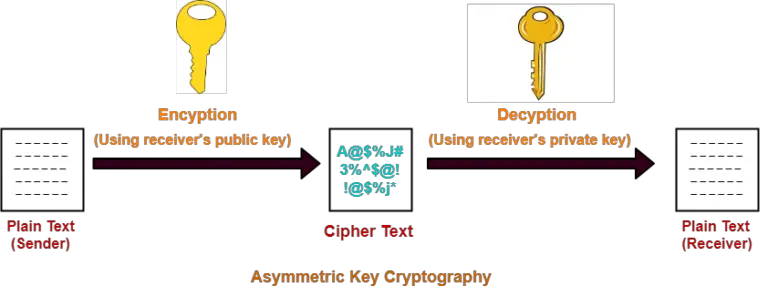
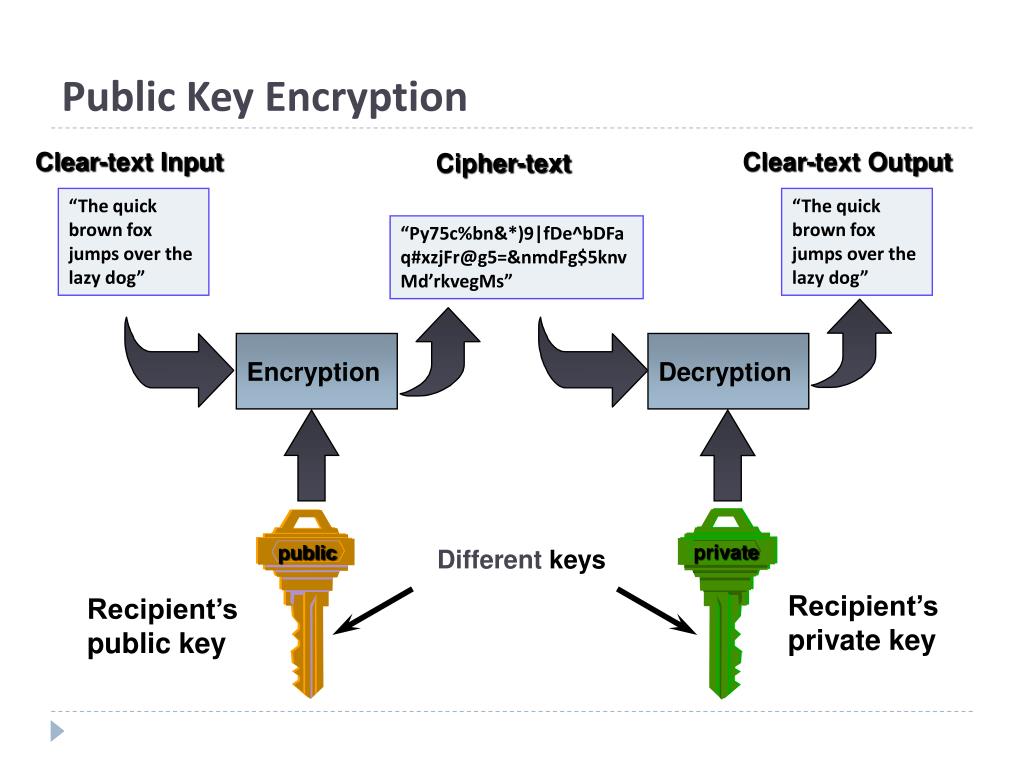
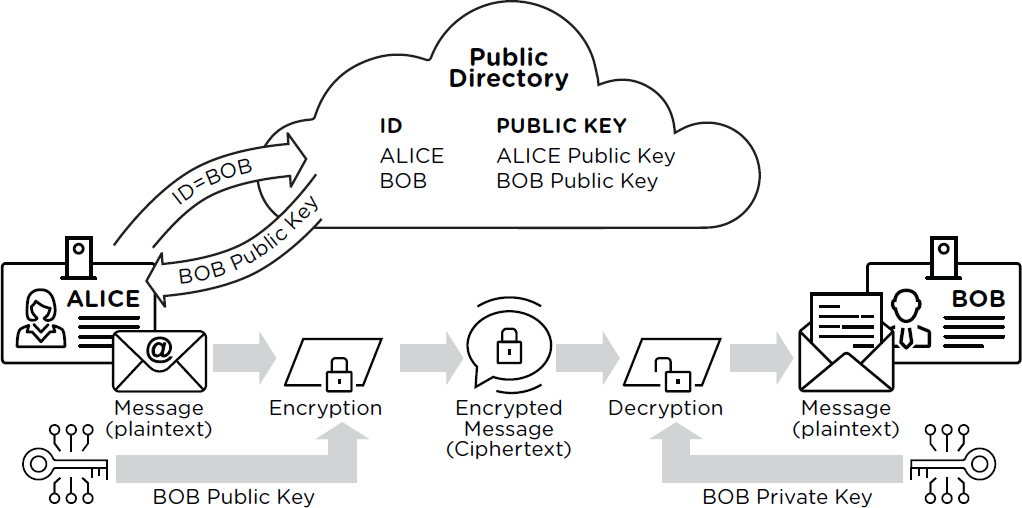
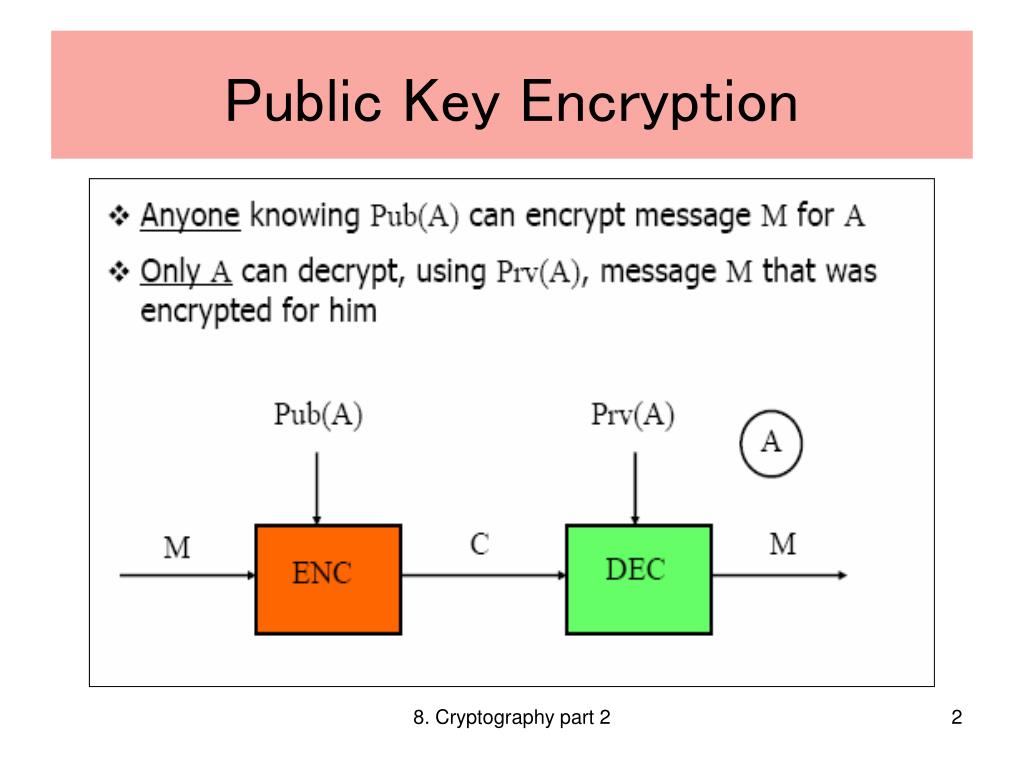
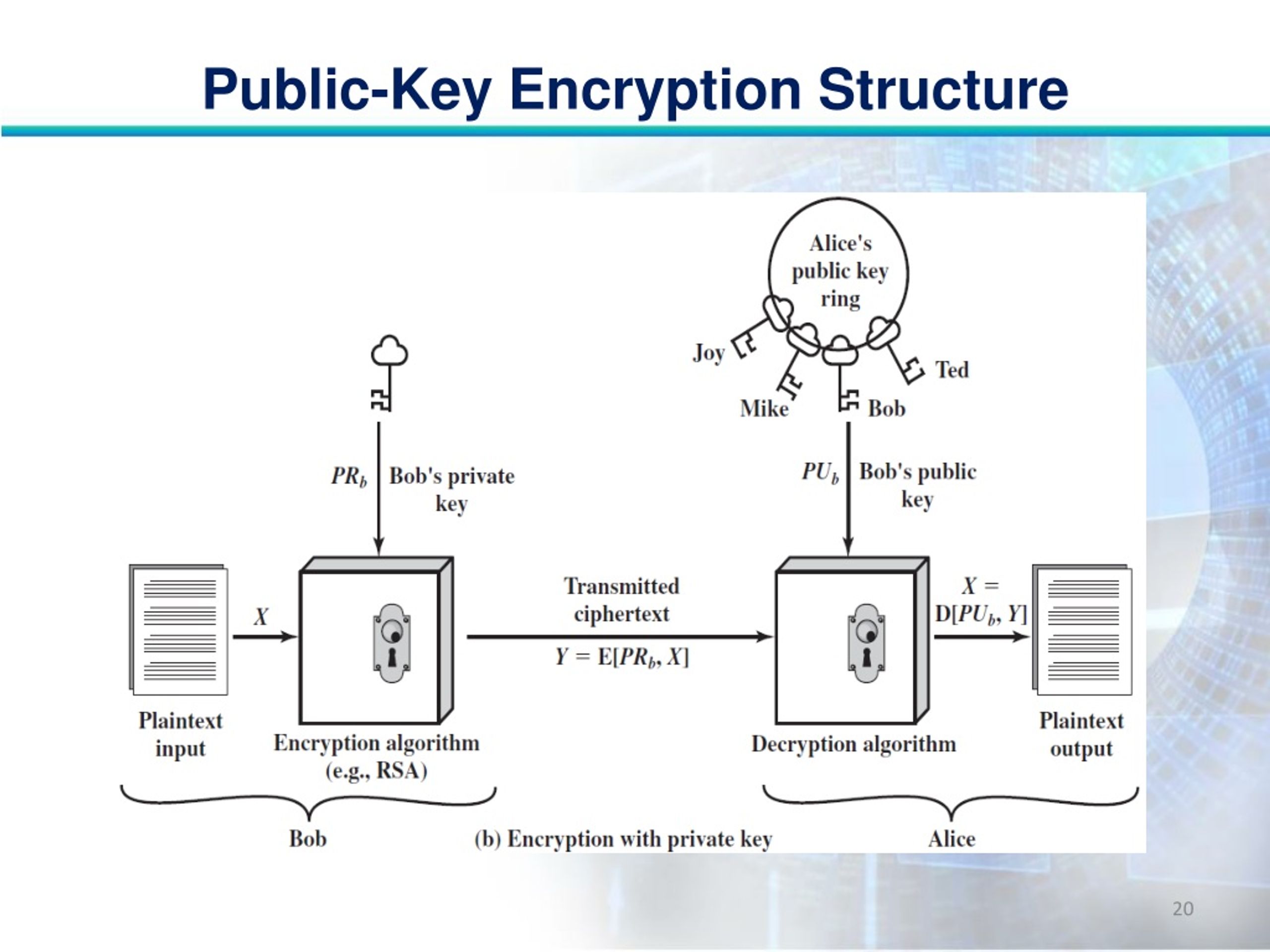
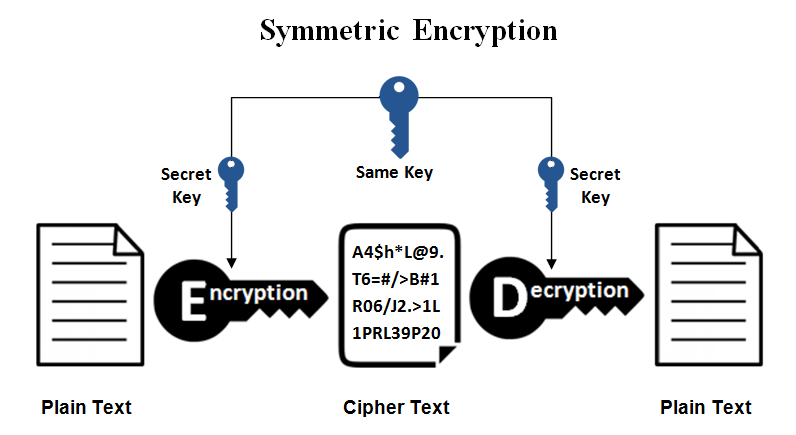
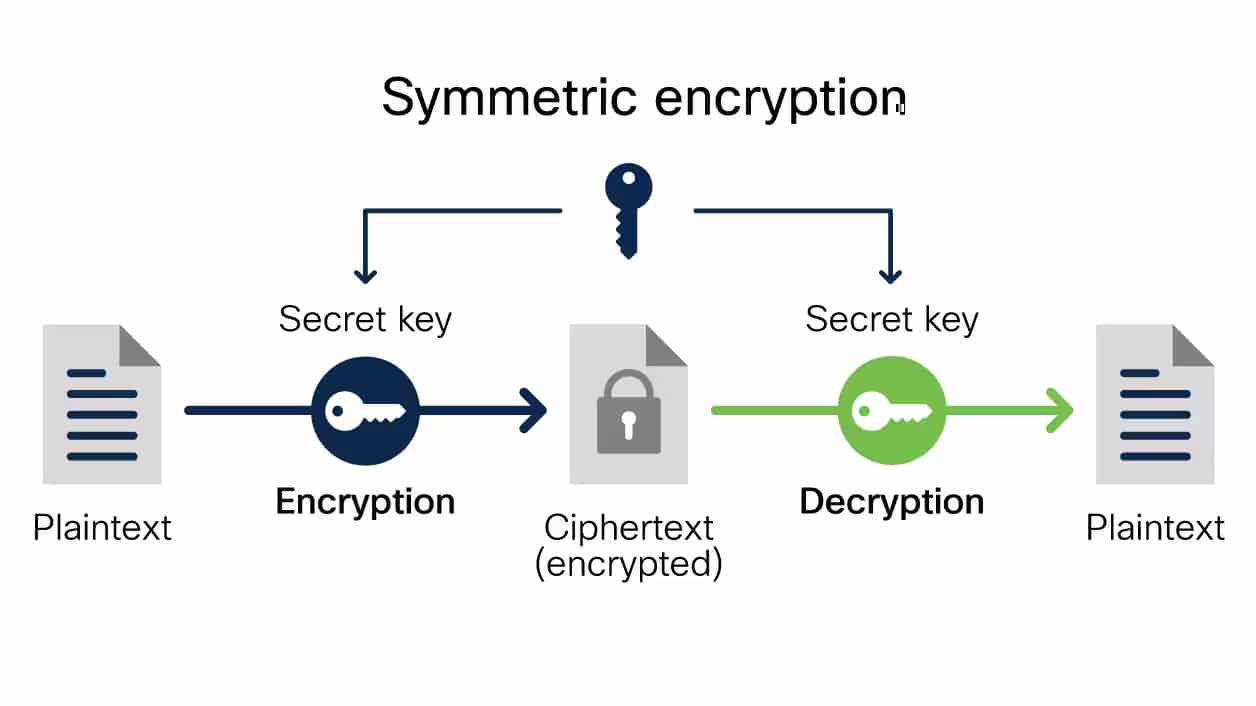
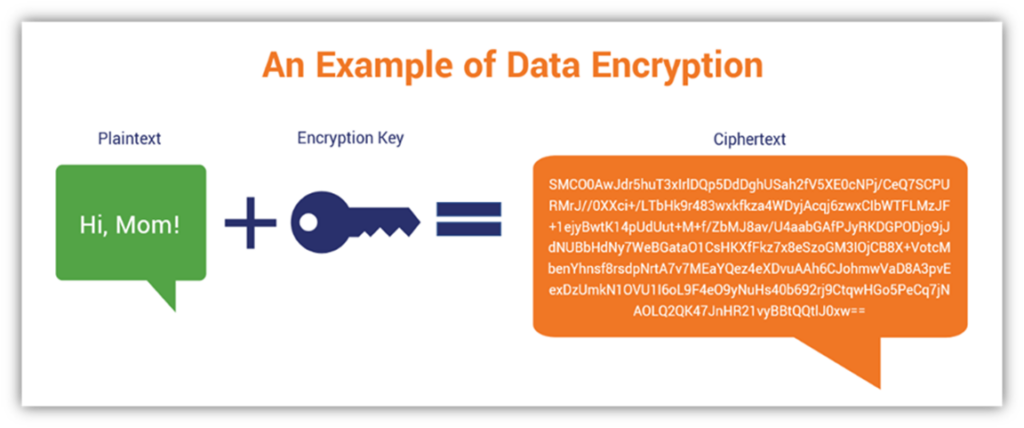
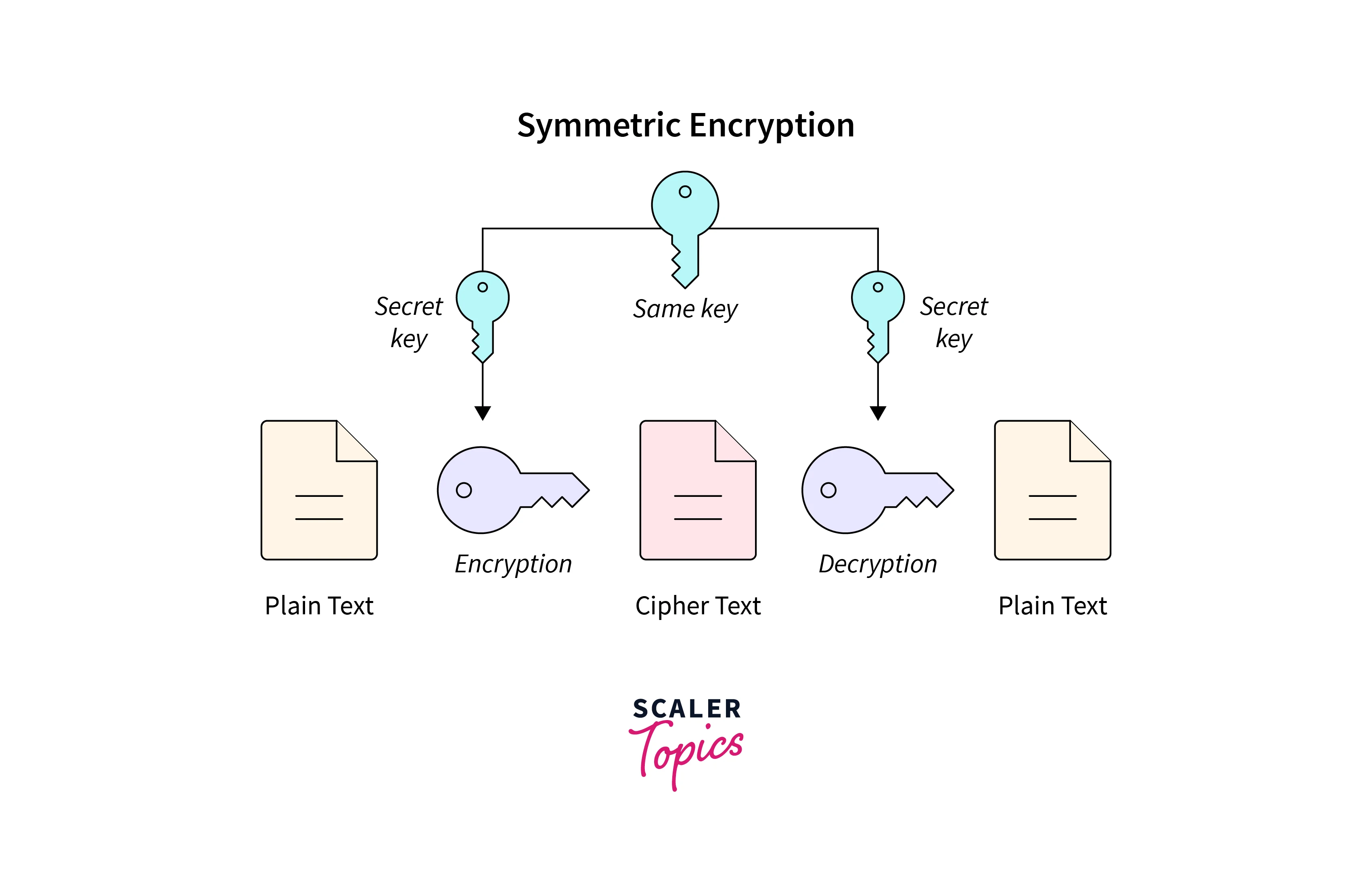
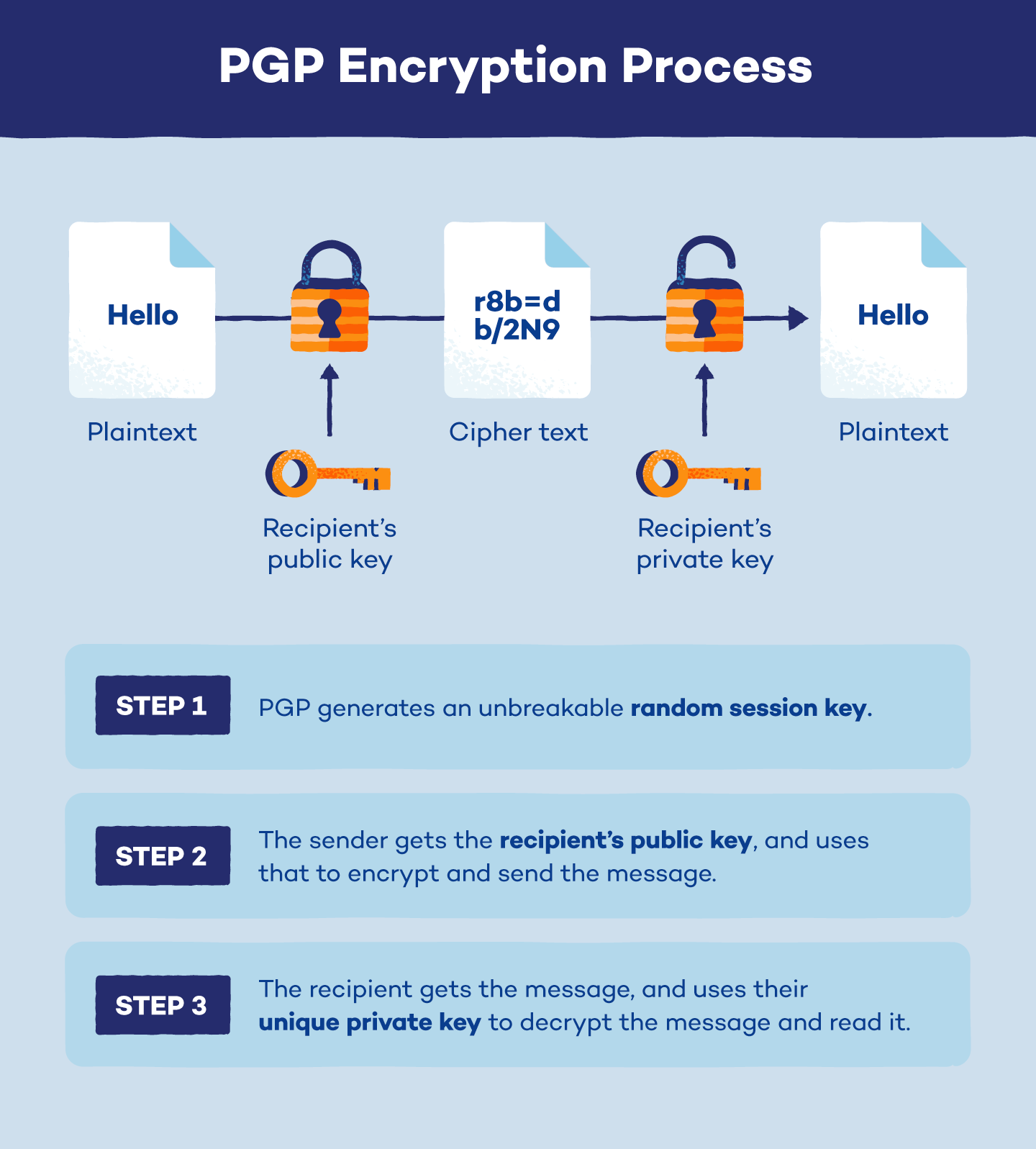
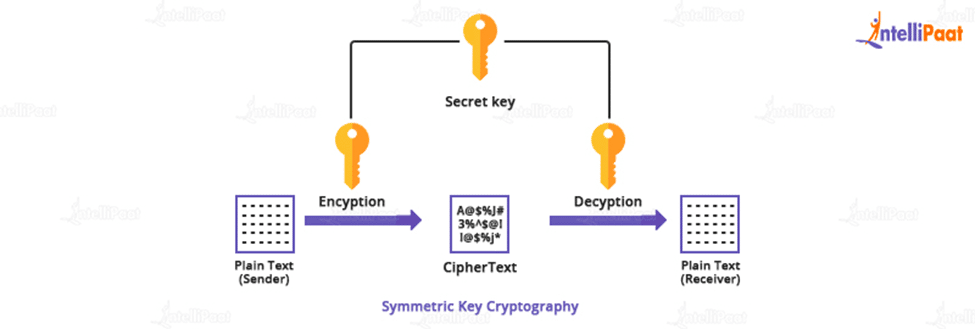
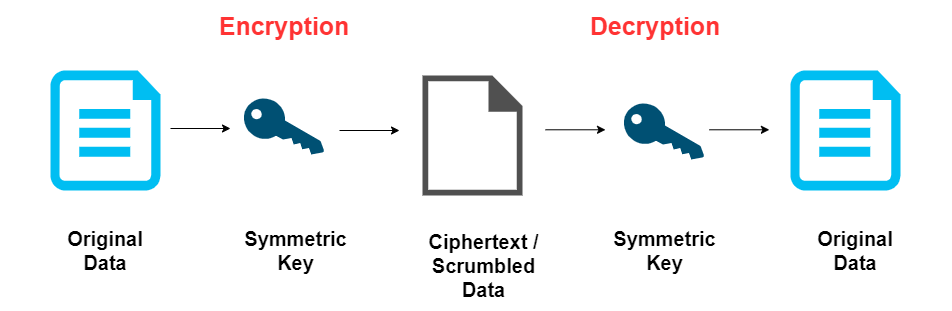
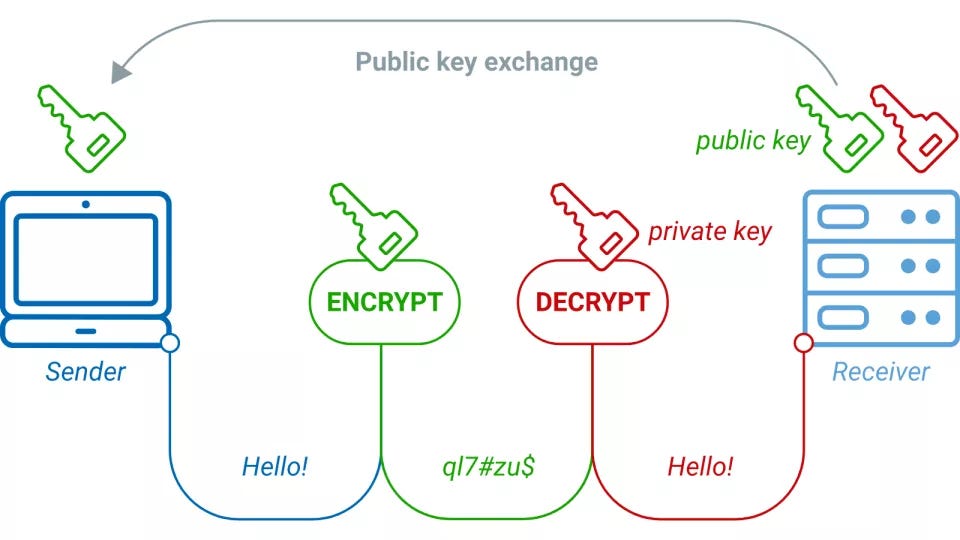
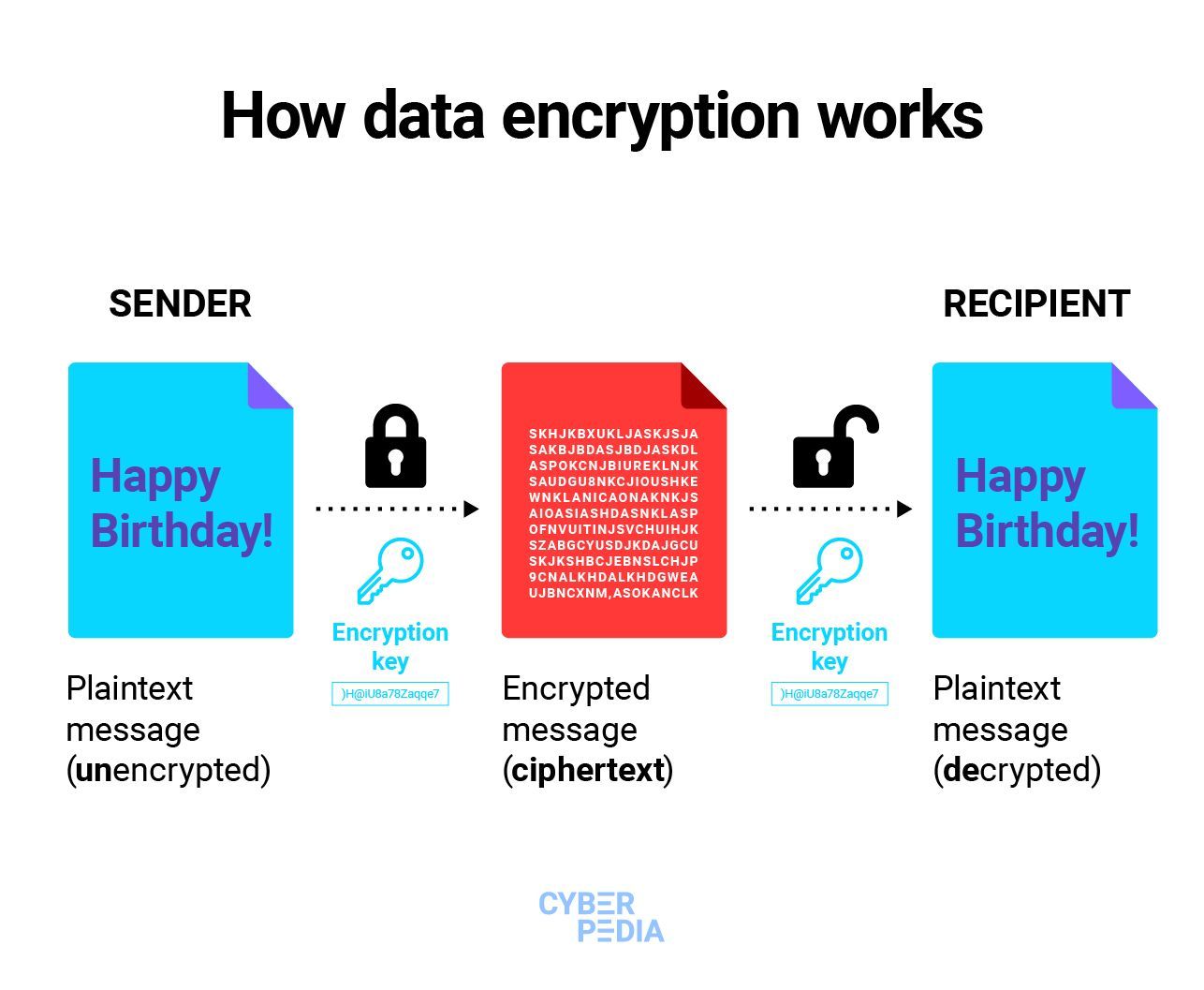
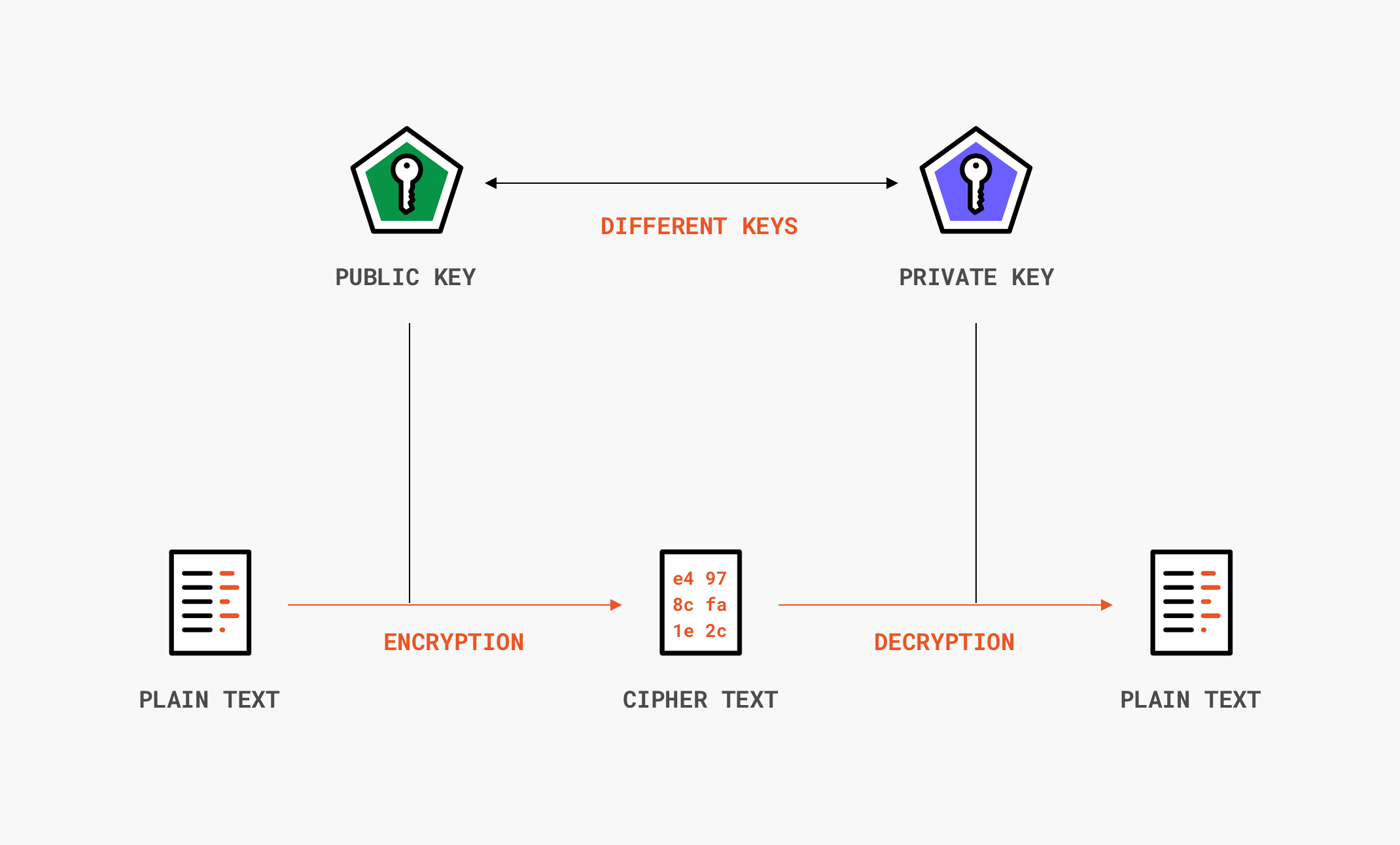
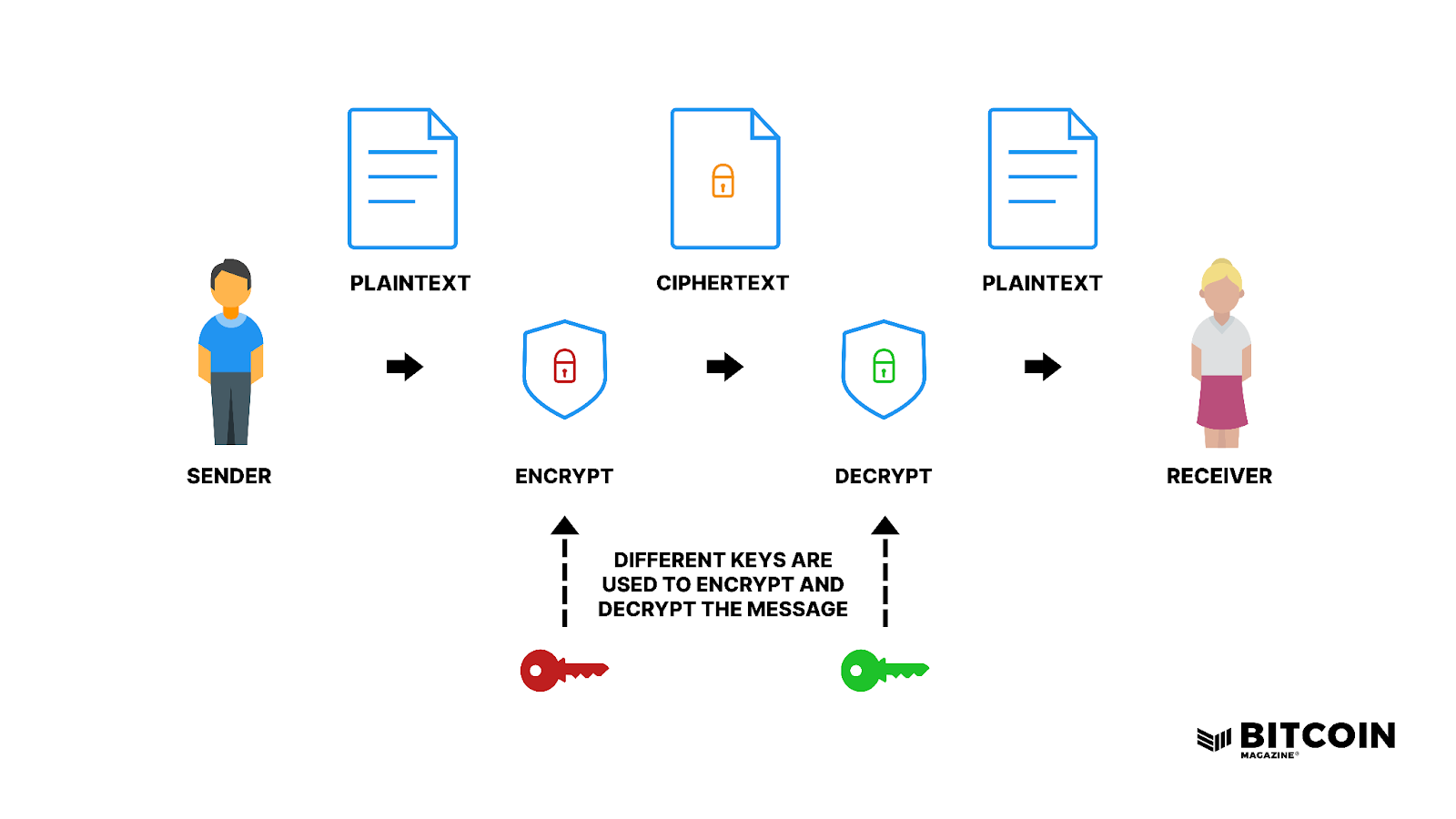
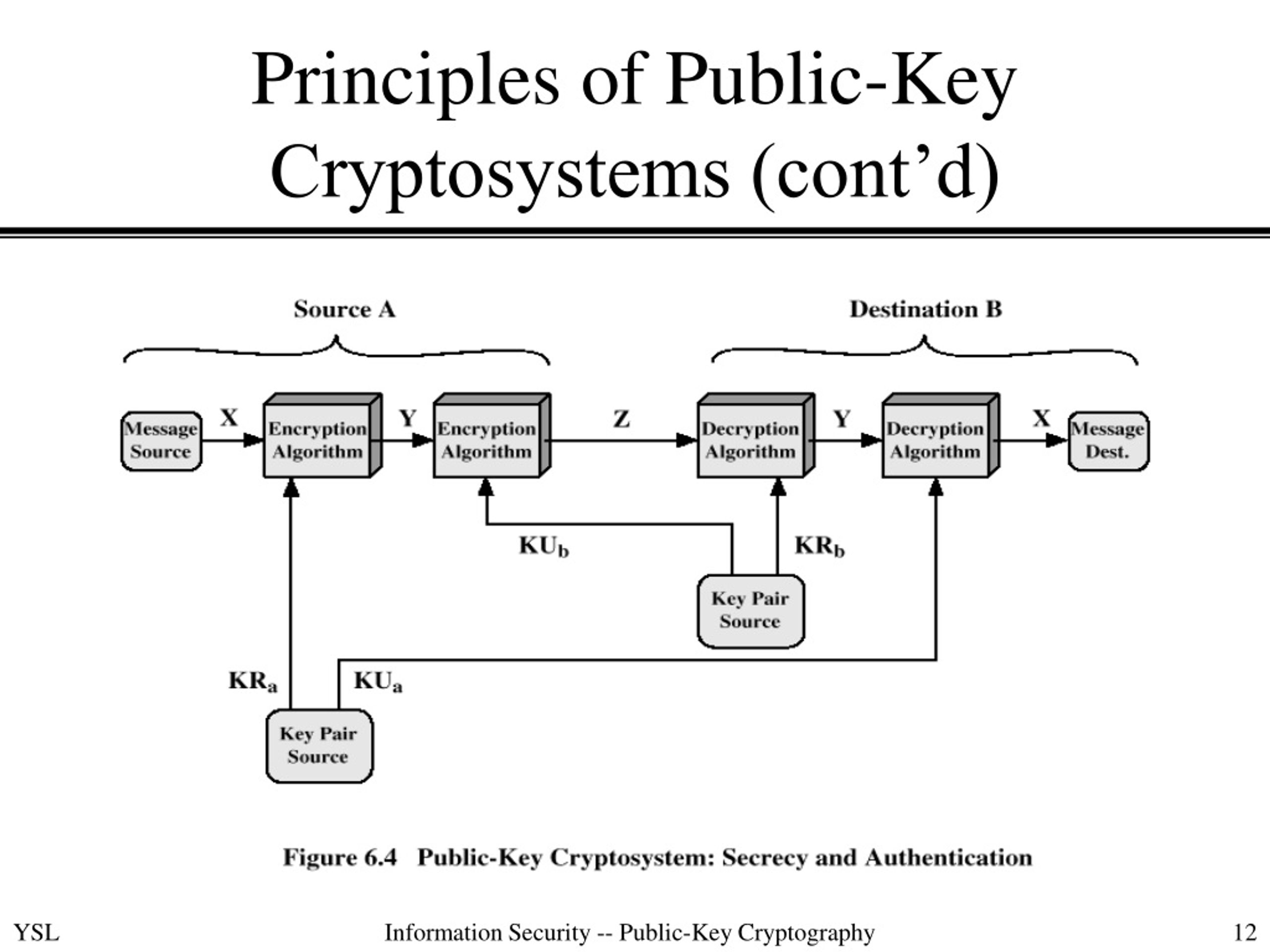
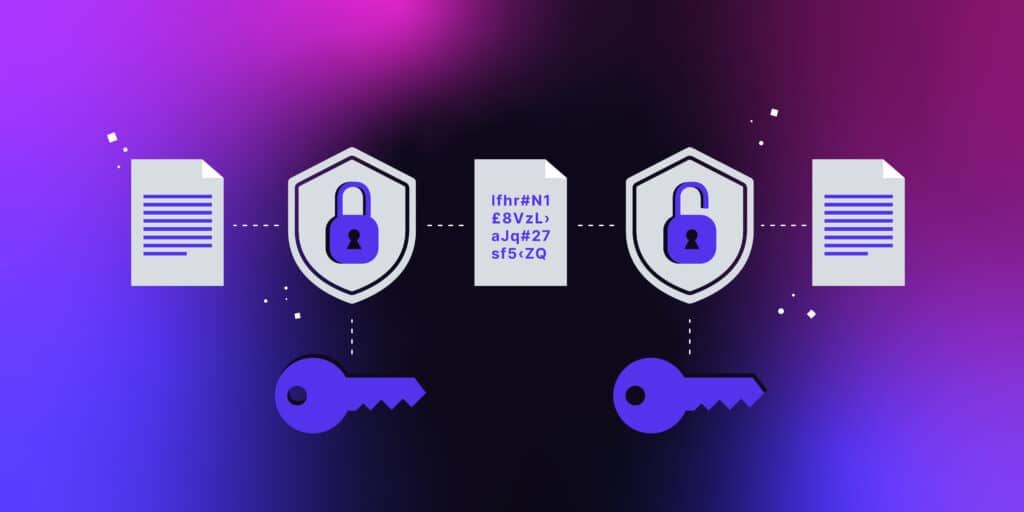
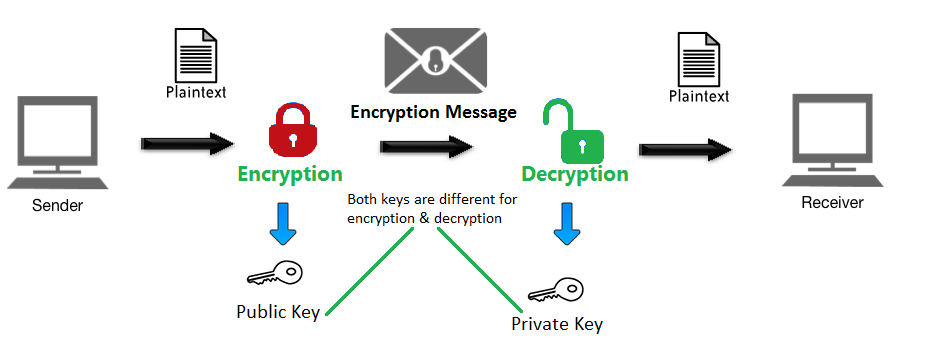
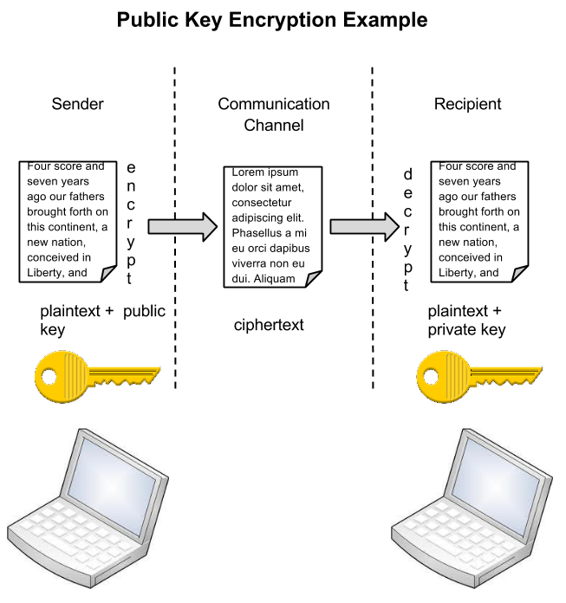
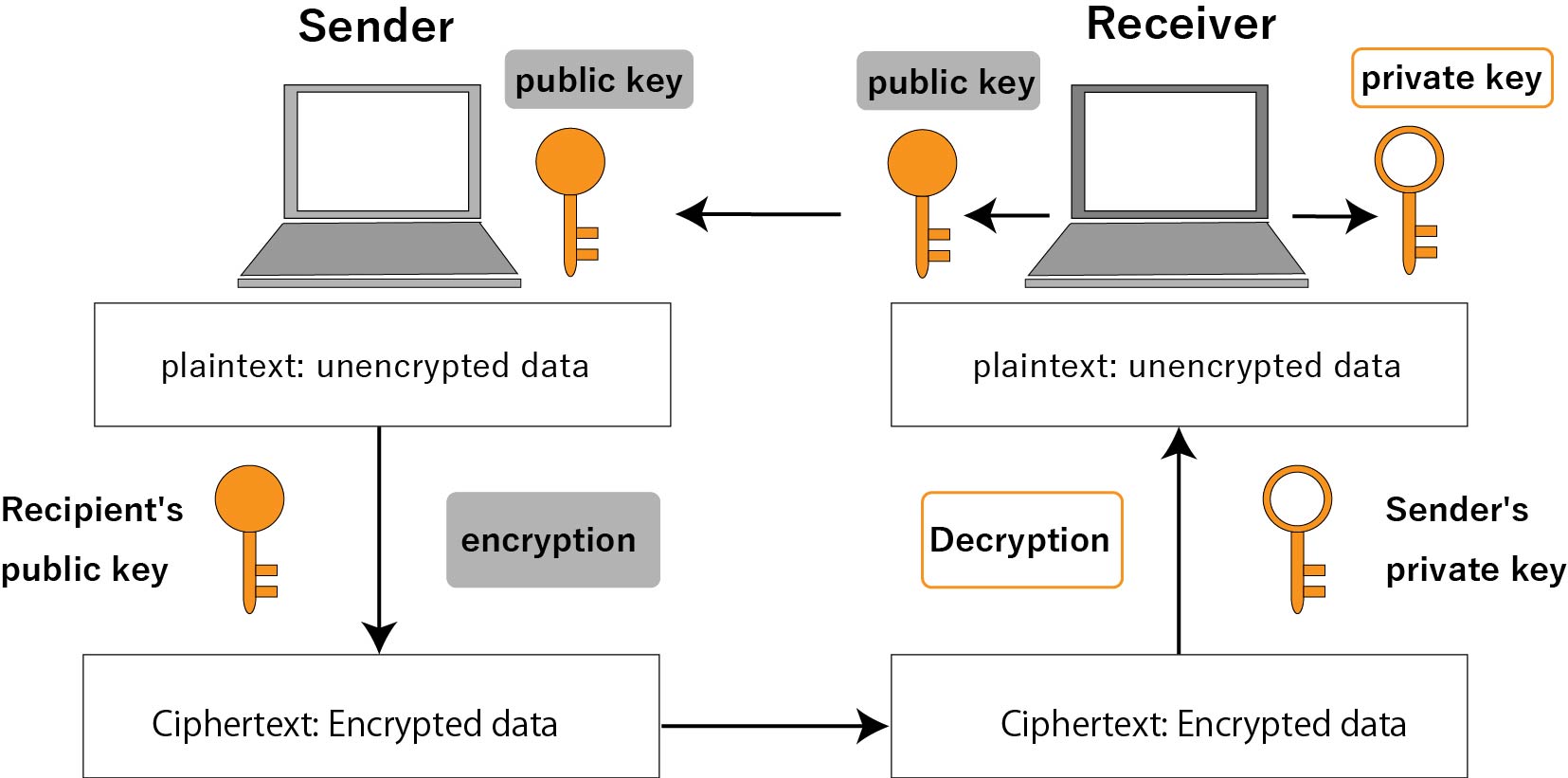
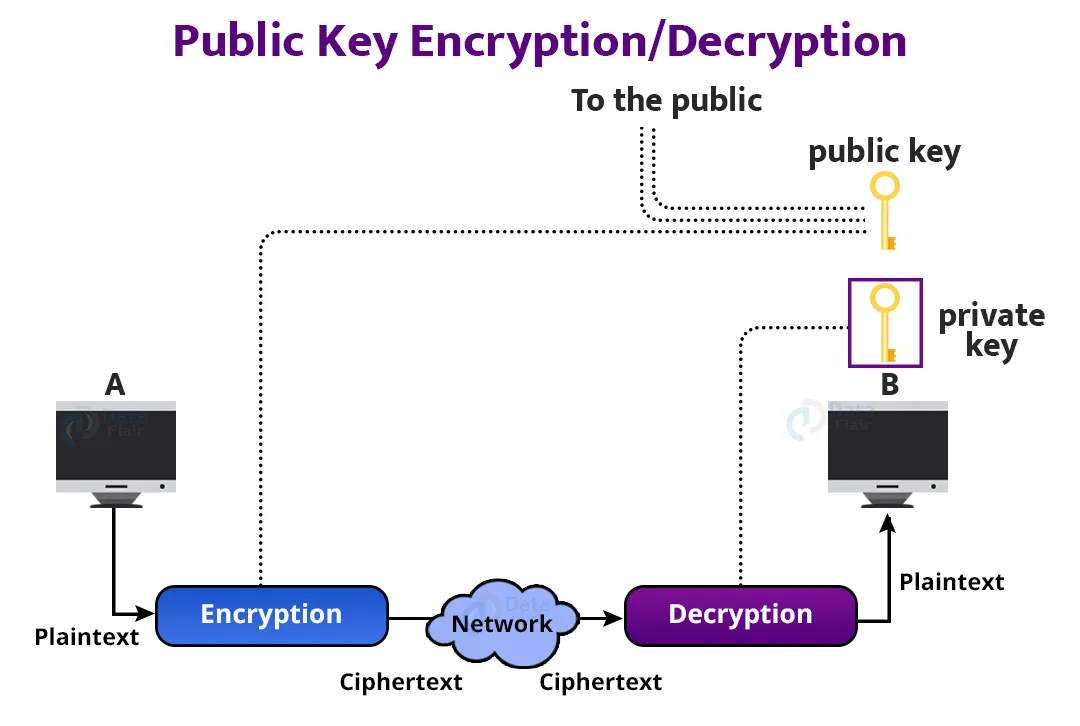
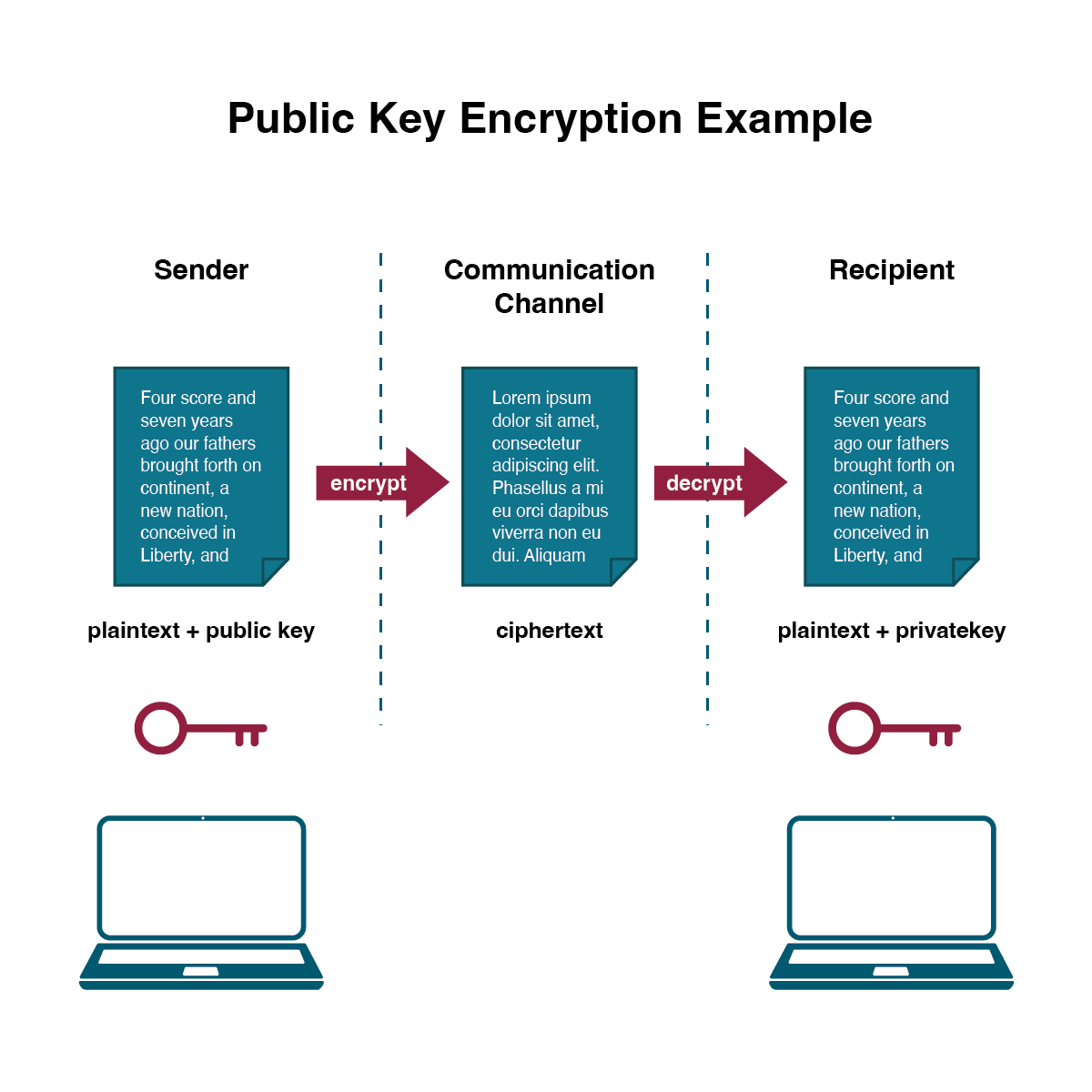
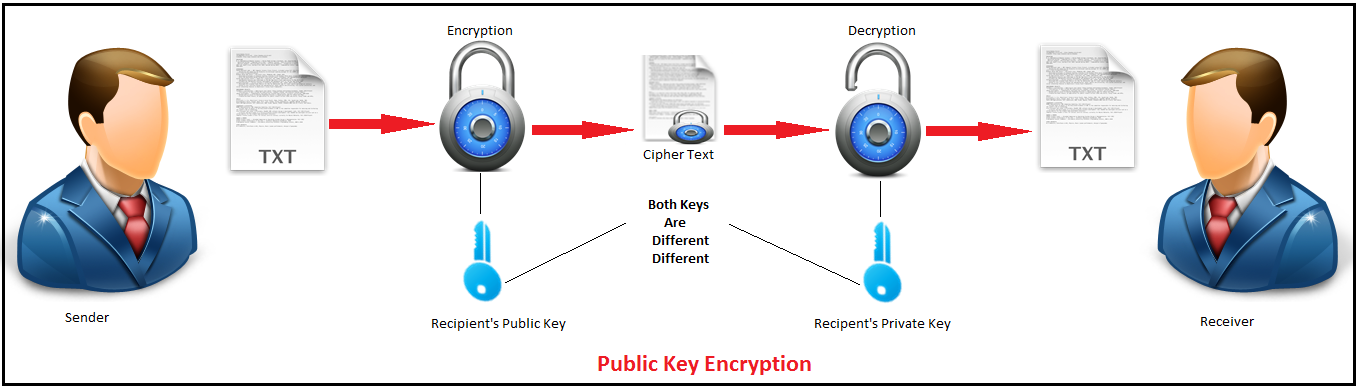
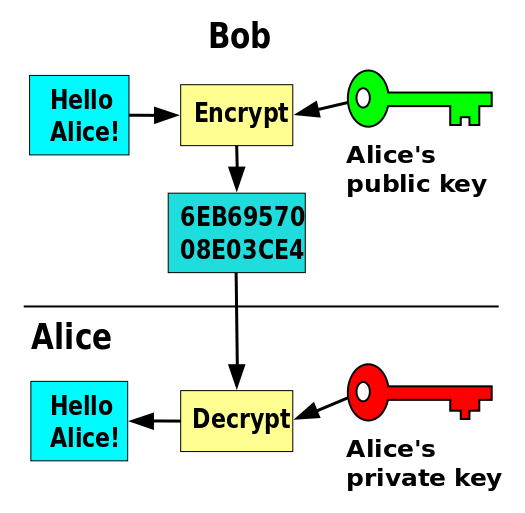
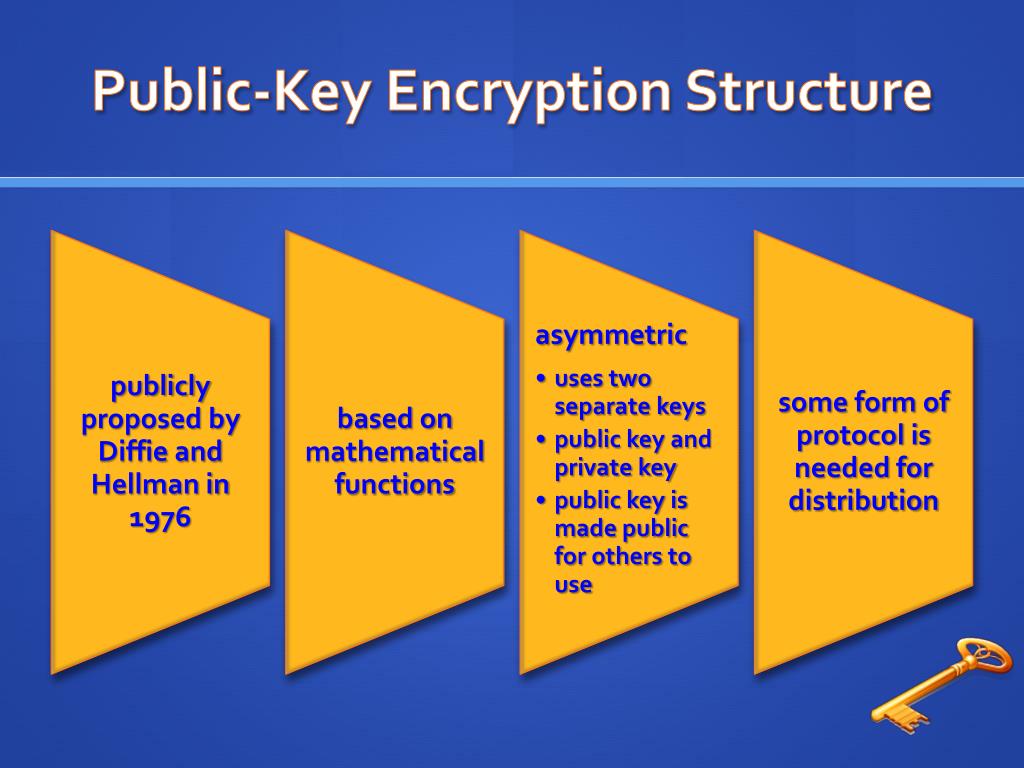
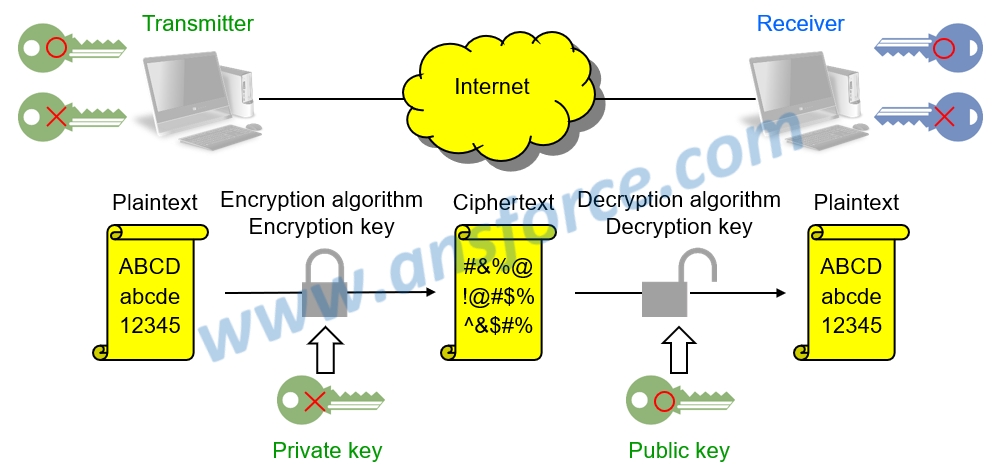
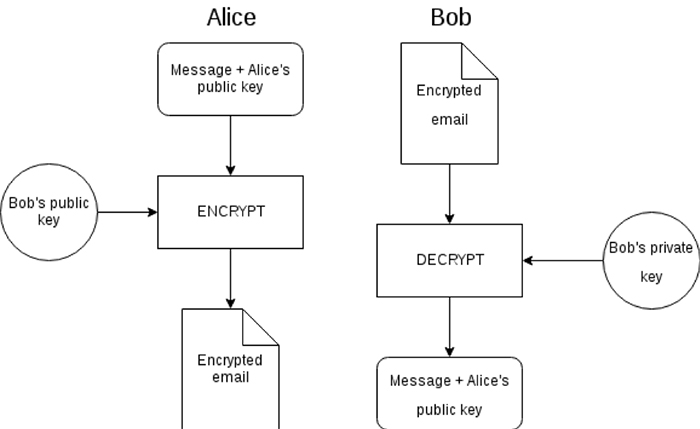
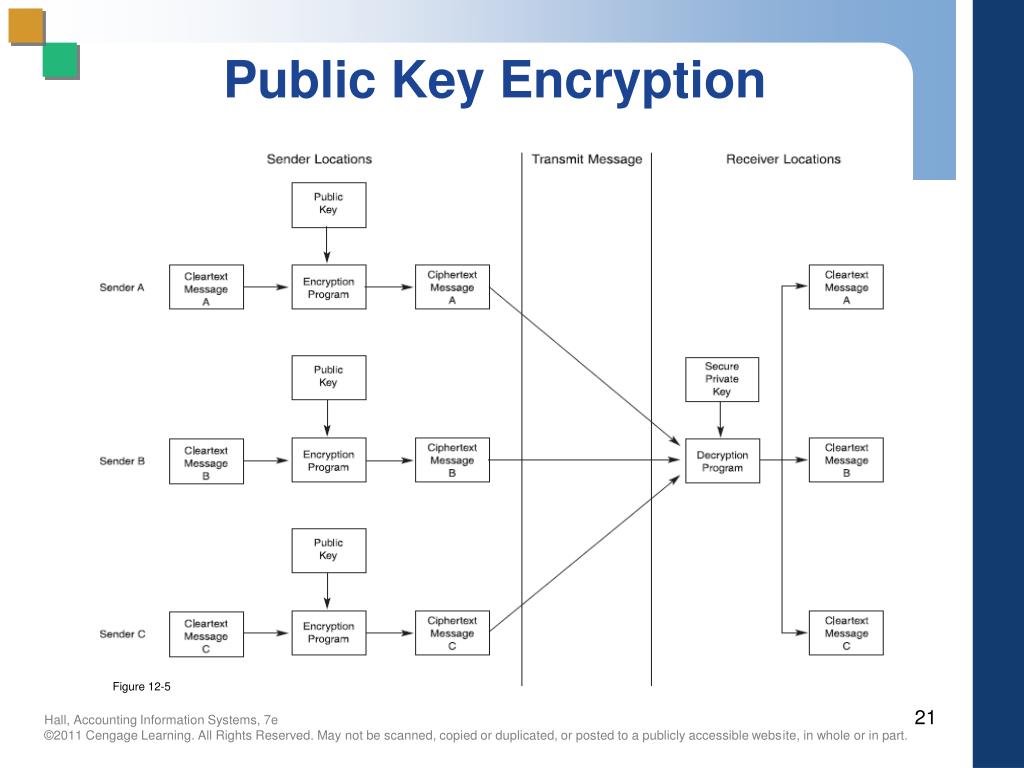
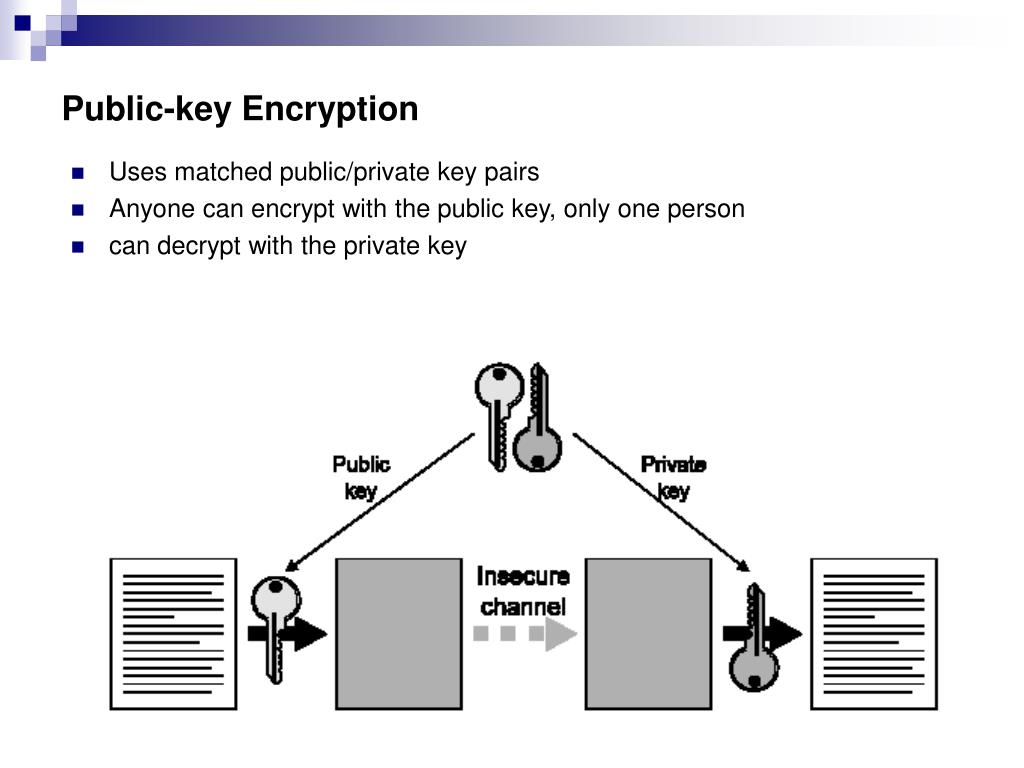
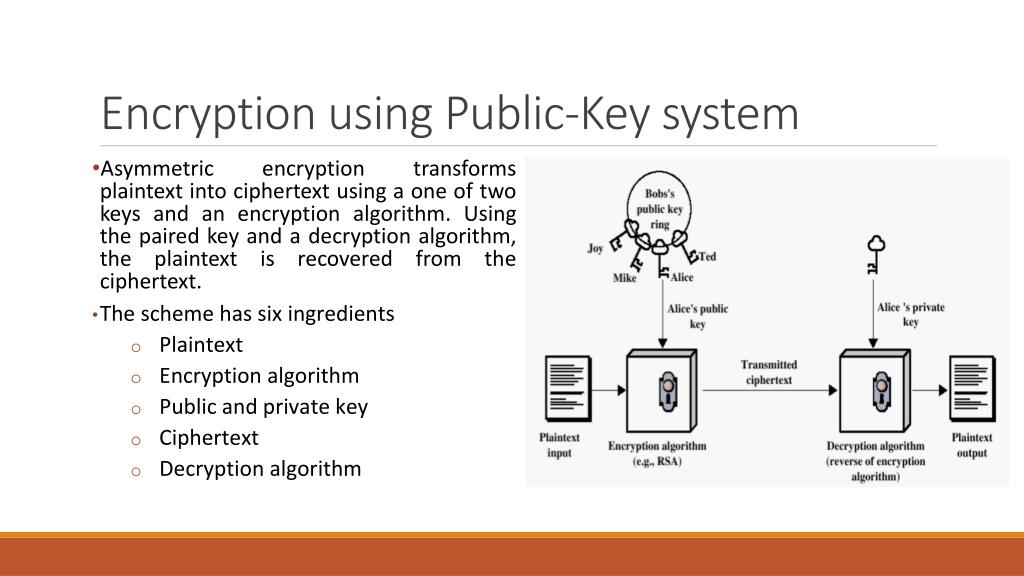
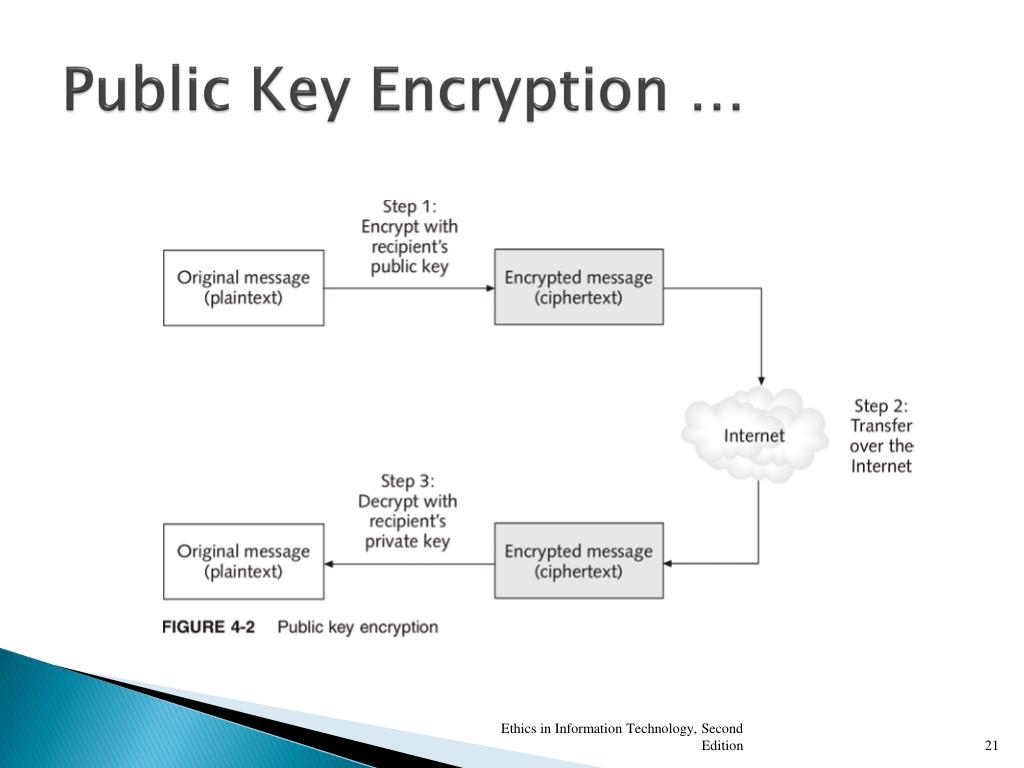
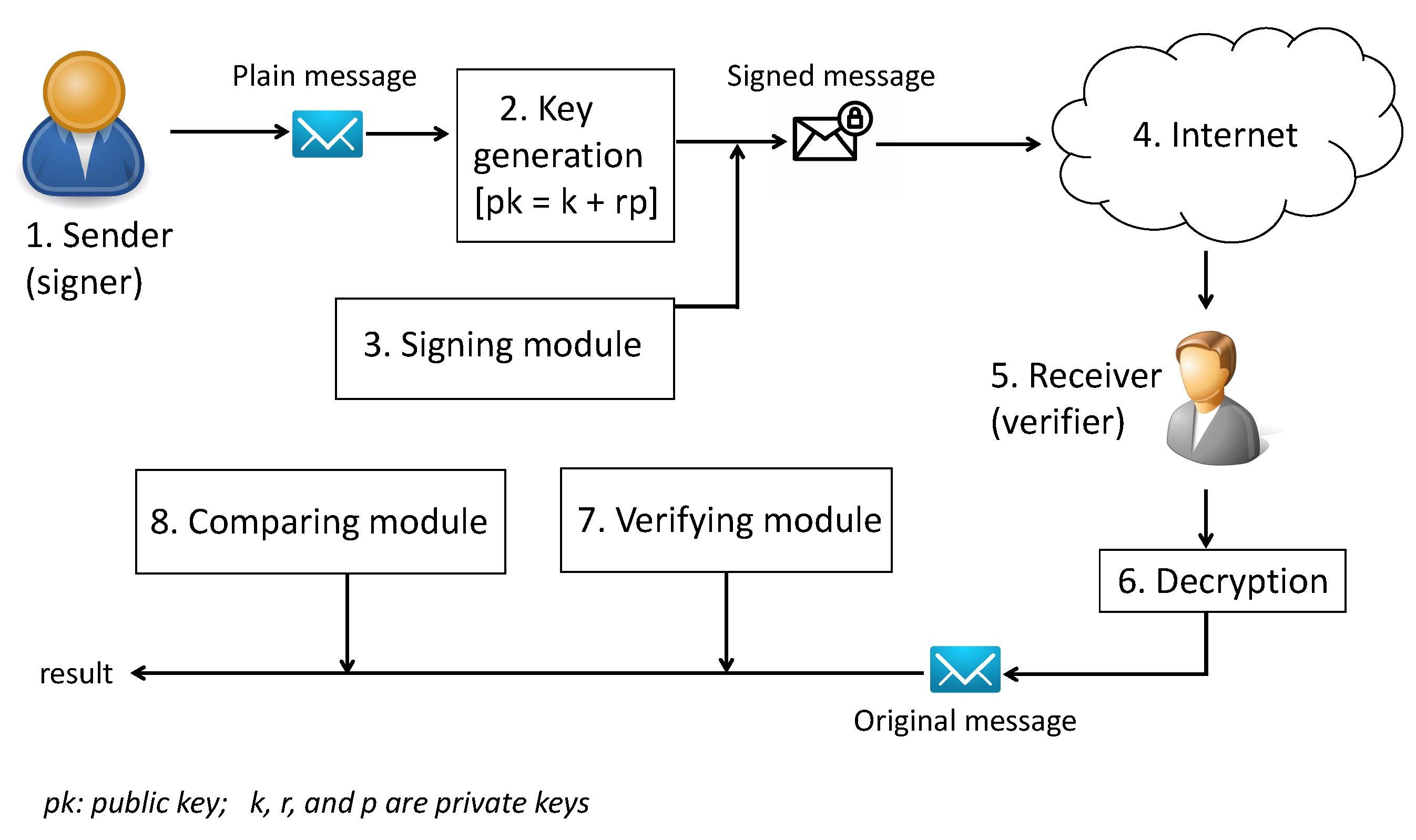
Diagram The Process Of Public Key Encryption When Transmitting Data
Explore the educational aspects of Diagram The Process Of Public Key Encryption When Transmitting Data through extensive collections of informative visual resources. facilitating comprehension through clear visual examples and detailed documentation. encouraging critical thinking and analytical skill development. Each Diagram The Process Of Public Key Encryption When Transmitting Data image is carefully selected for superior visual impact and professional quality. Excellent for educational materials, academic research, teaching resources, and learning activities All Diagram The Process Of Public Key Encryption When Transmitting Data images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. The Diagram The Process Of Public Key Encryption When Transmitting Data collection serves as a valuable educational resource for teachers and students. Regular updates keep the Diagram The Process Of Public Key Encryption When Transmitting Data collection current with contemporary trends and styles. Reliable customer support ensures smooth experience throughout the Diagram The Process Of Public Key Encryption When Transmitting Data selection process. Cost-effective licensing makes professional Diagram The Process Of Public Key Encryption When Transmitting Data photography accessible to all budgets. Professional licensing options accommodate both commercial and educational usage requirements. The Diagram The Process Of Public Key Encryption When Transmitting Data collection represents years of careful curation and professional standards.



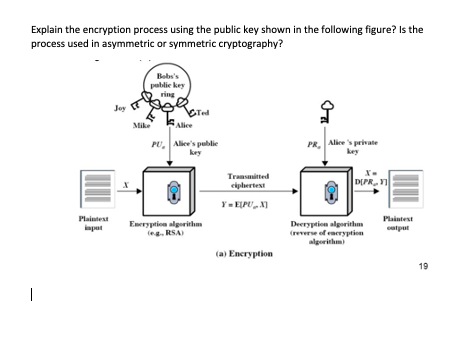







![How Public Key Encryption Works [13]. | Download Scientific Diagram](https://www.researchgate.net/publication/362363523/figure/fig1/AS:11431281095890432@1668051792415/How-Public-Key-Encryption-Works-13_Q640.jpg)




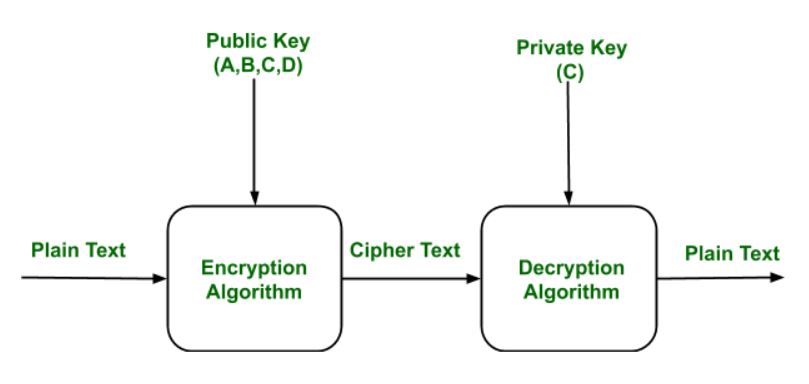




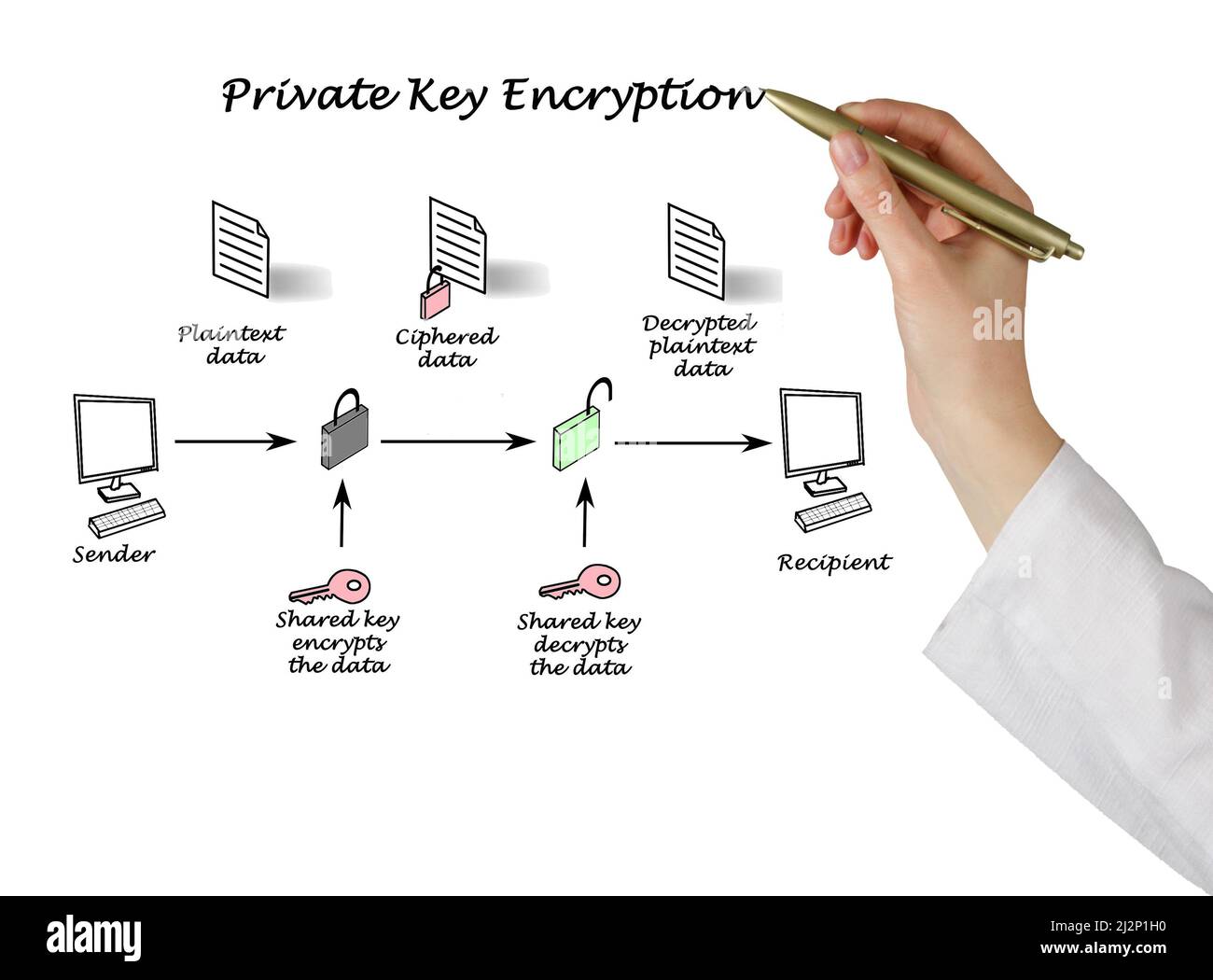







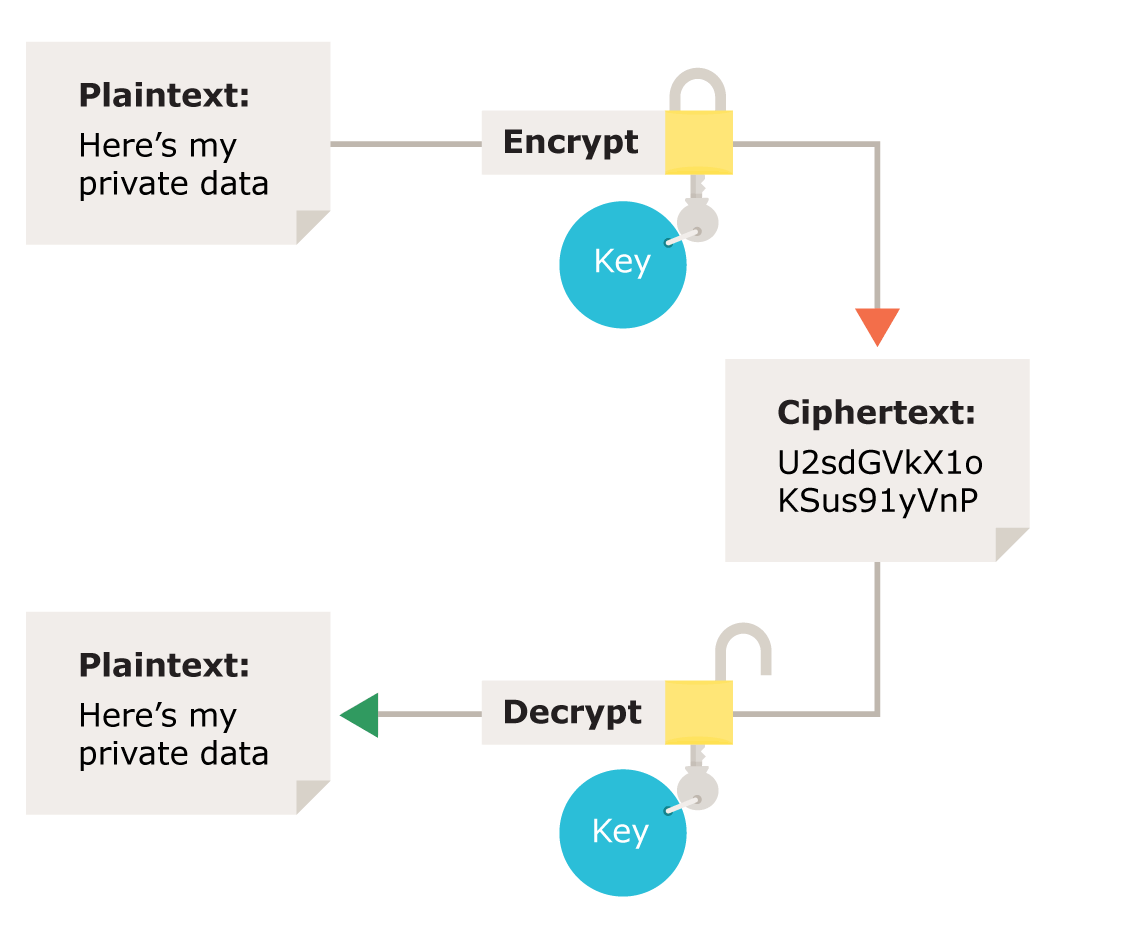


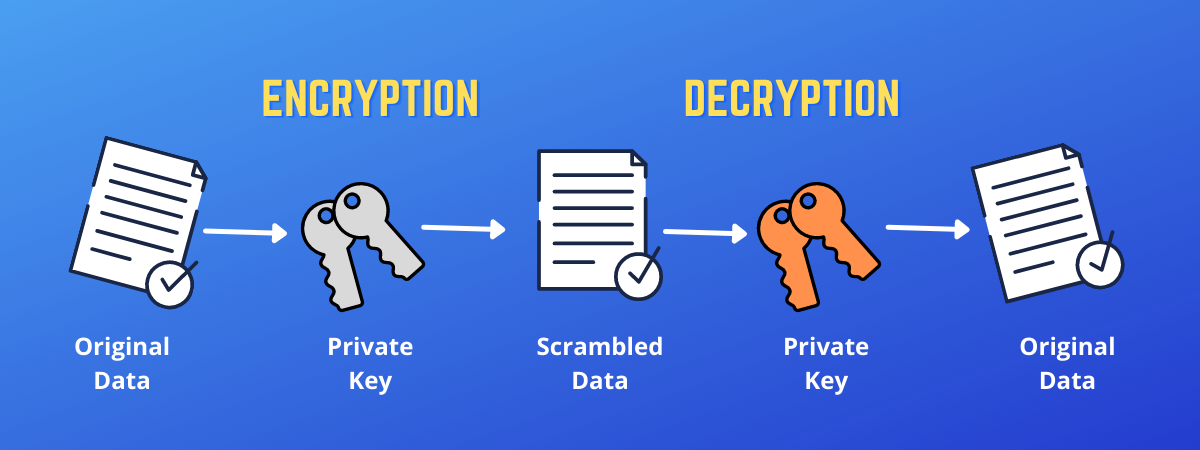


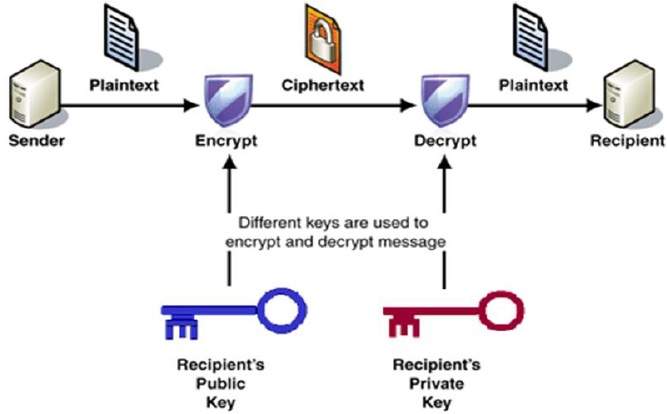
![Public-Key Encryption [5]. | Download Scientific Diagram](https://www.researchgate.net/profile/Md-Bhuiyan-40/publication/266228471/figure/fig1/AS:669382430711816@1536604616227/Figure-1-Public-Key-Encryption-5_Q320.jpg)
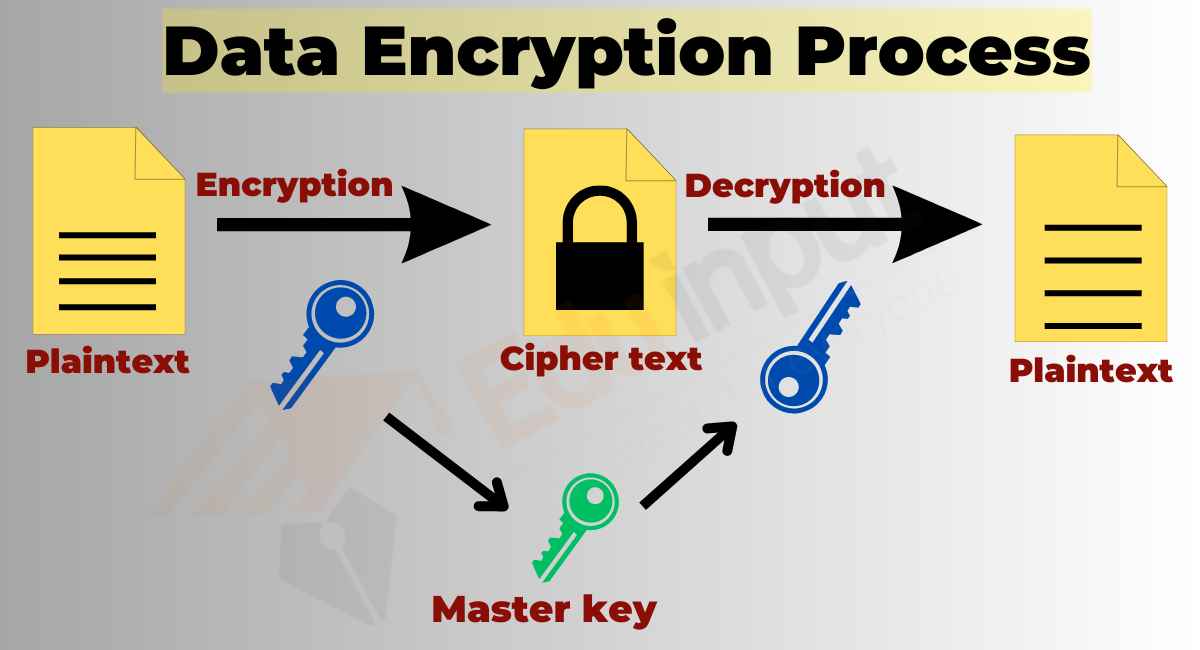
![Public-key encryption [71] | Download Scientific Diagram](https://www.researchgate.net/profile/Albena-Bogoeva/publication/333145193/figure/fig2/AS:785948375785474@1564396103786/Public-key-encryption-71_Q320.jpg)