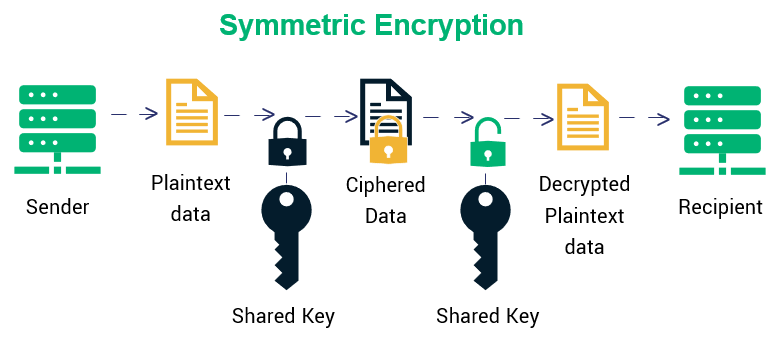
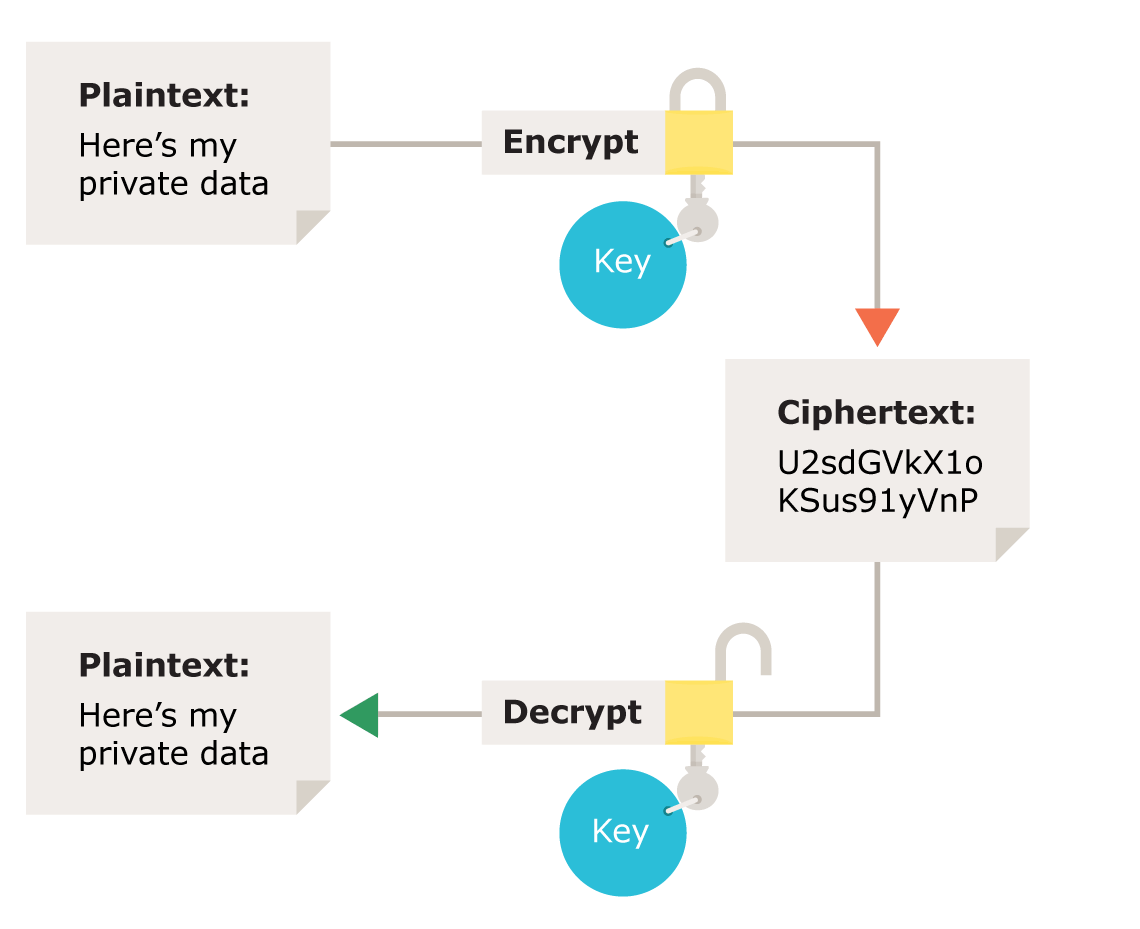
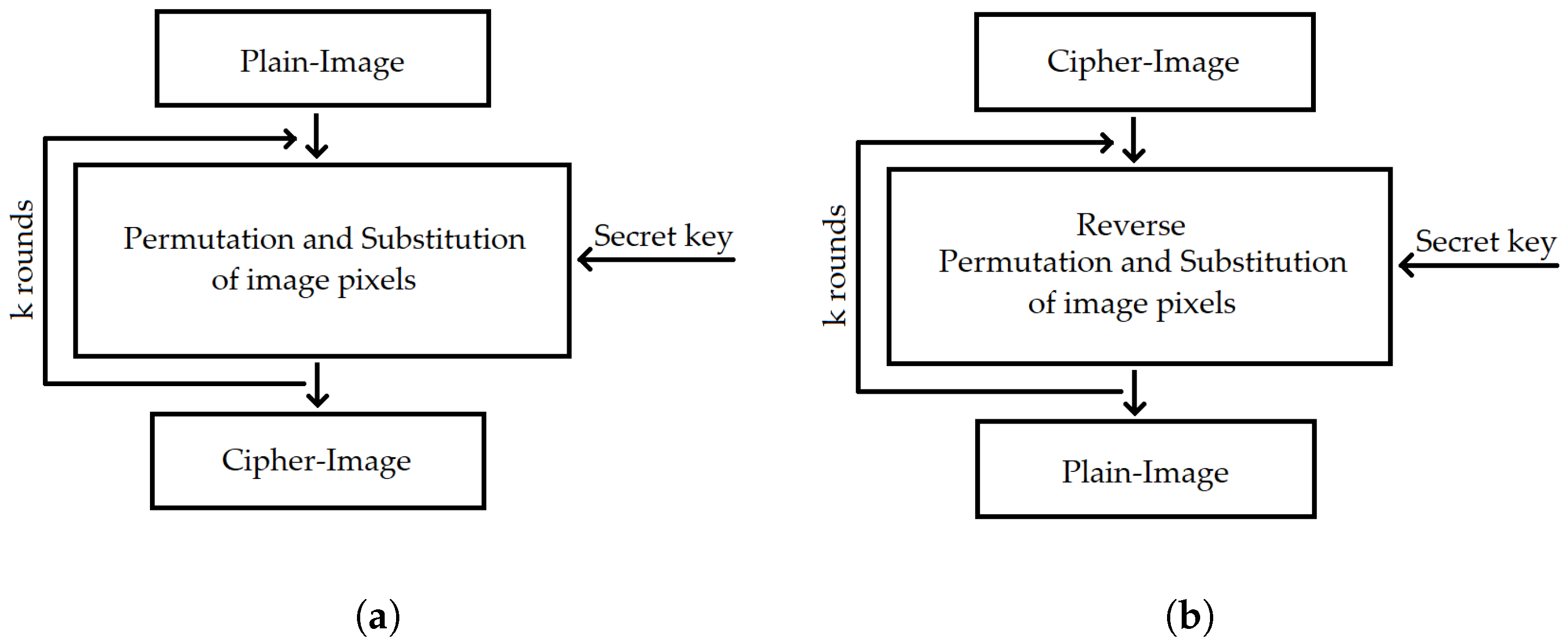
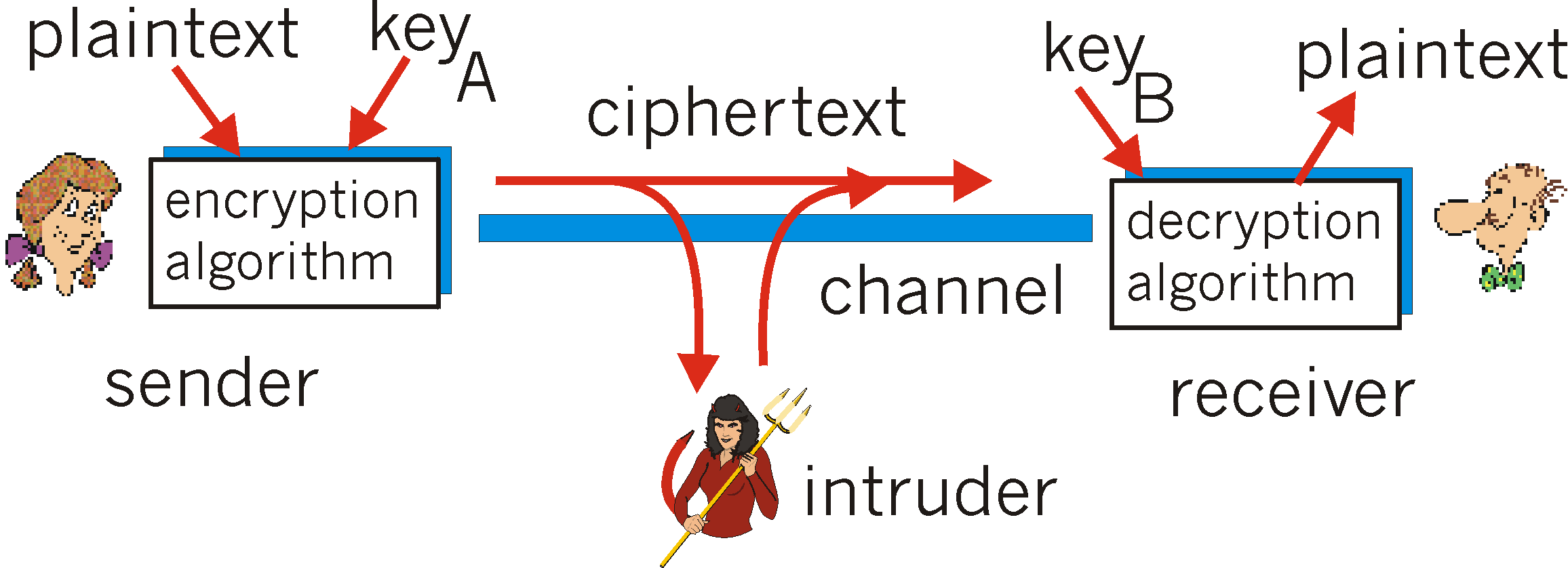
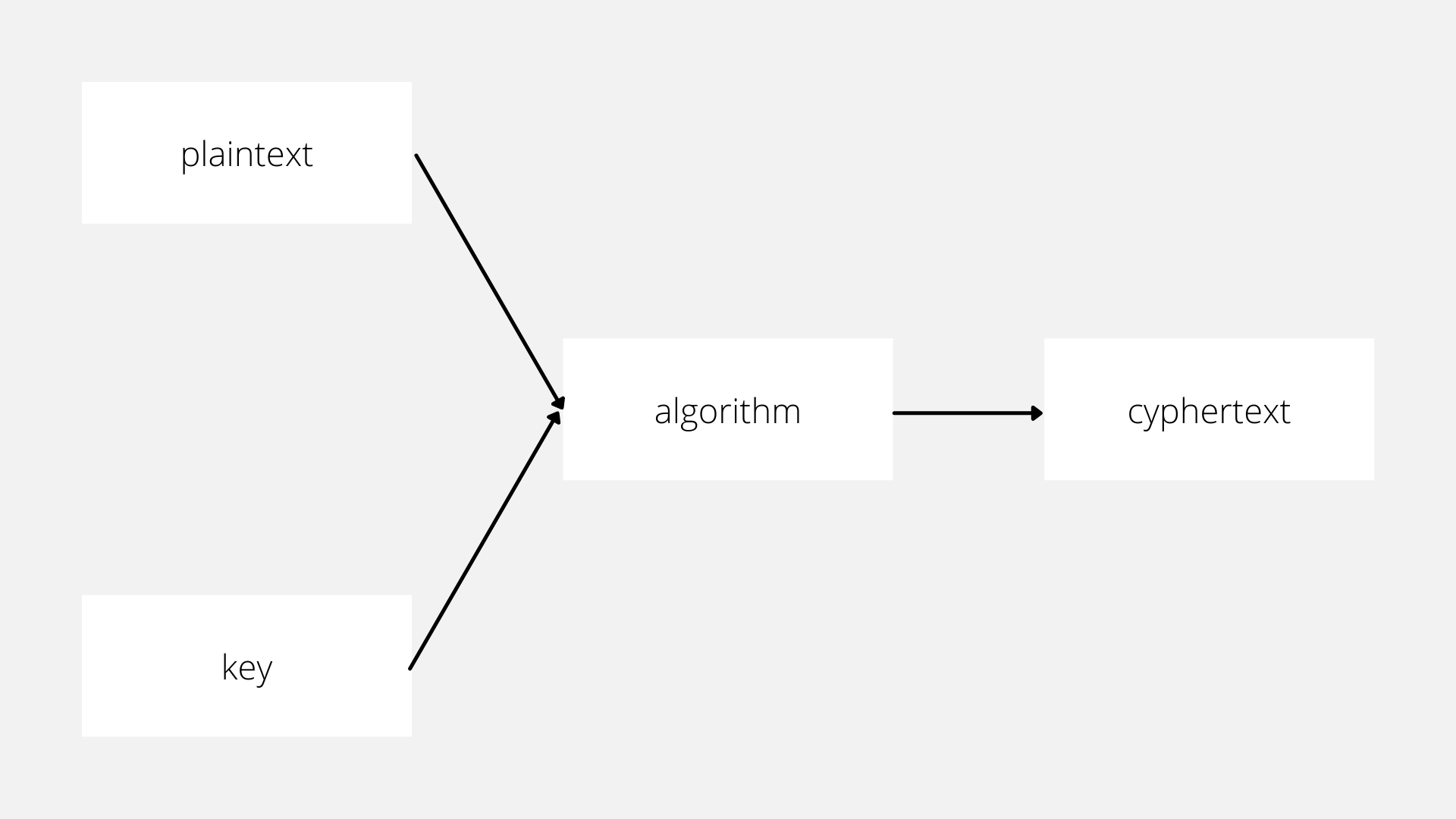
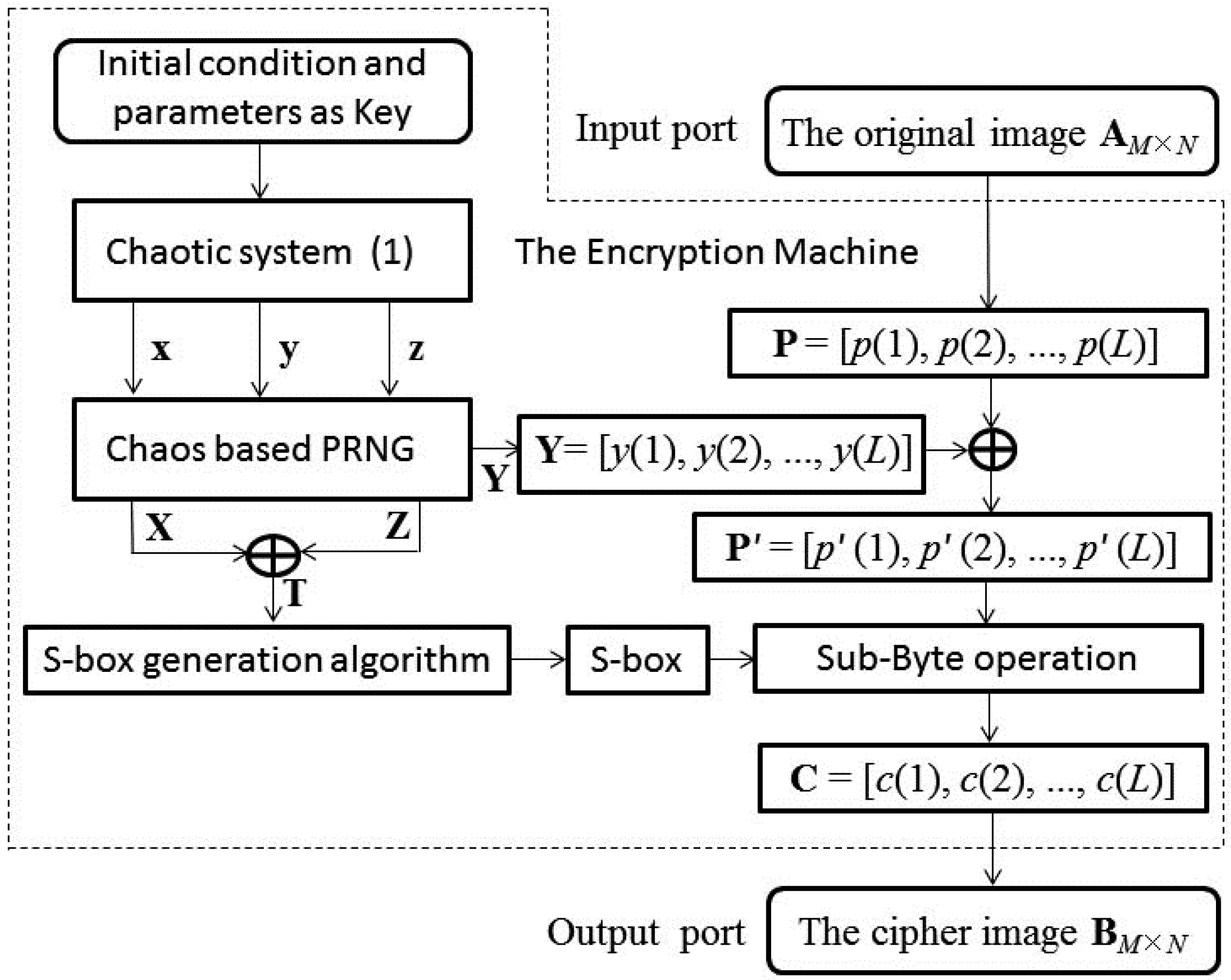
Decryption Flowchart Algorithm In Cryptography
Explore the fascinating world of Decryption Flowchart Algorithm In Cryptography through our stunning gallery of vast arrays of photographs. featuring exceptional examples of artistic, creative, and design. suitable for various professional and personal projects. Browse our premium Decryption Flowchart Algorithm In Cryptography gallery featuring professionally curated photographs. Suitable for various applications including web design, social media, personal projects, and digital content creation All Decryption Flowchart Algorithm In Cryptography images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Discover the perfect Decryption Flowchart Algorithm In Cryptography images to enhance your visual communication needs. Comprehensive tagging systems facilitate quick discovery of relevant Decryption Flowchart Algorithm In Cryptography content. Time-saving browsing features help users locate ideal Decryption Flowchart Algorithm In Cryptography images quickly. Each image in our Decryption Flowchart Algorithm In Cryptography gallery undergoes rigorous quality assessment before inclusion. Cost-effective licensing makes professional Decryption Flowchart Algorithm In Cryptography photography accessible to all budgets. The Decryption Flowchart Algorithm In Cryptography archive serves professionals, educators, and creatives across diverse industries. The Decryption Flowchart Algorithm In Cryptography collection represents years of careful curation and professional standards. Regular updates keep the Decryption Flowchart Algorithm In Cryptography collection current with contemporary trends and styles.




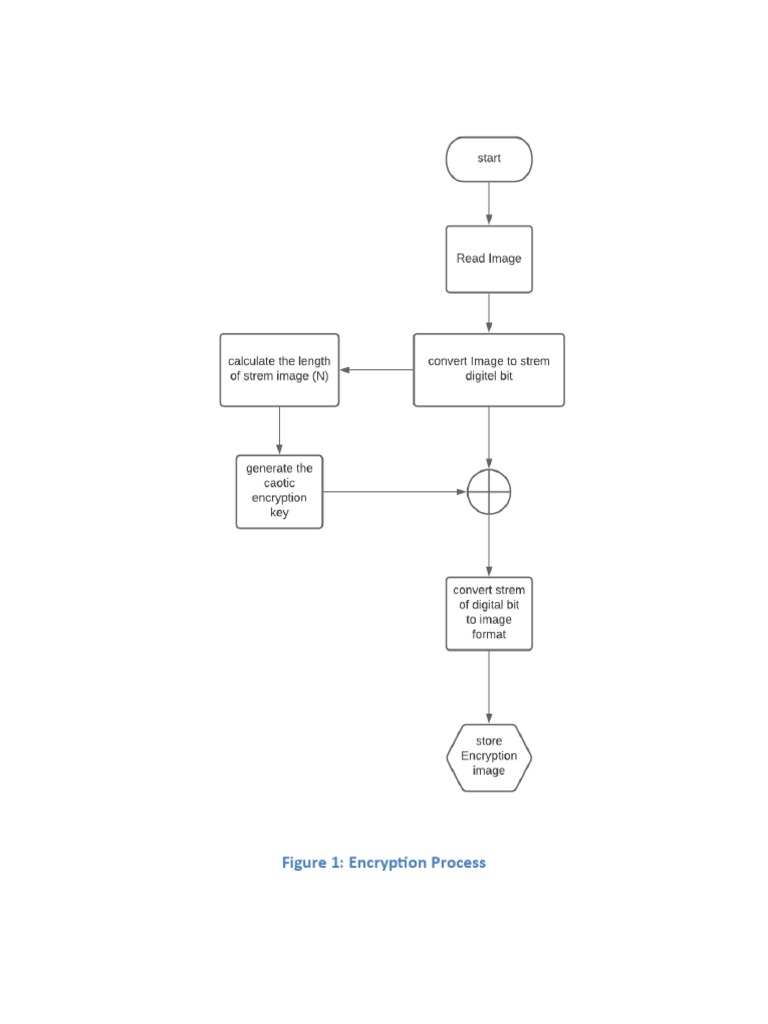
![Flowchart of 3DES encryption and decryption algorithm [40]. | Download ...](https://www.researchgate.net/publication/322276861/figure/fig4/AS:581599354130436@1515675499256/Flowchart-of-3DES-encryption-and-decryption-algorithm-40.png)


















































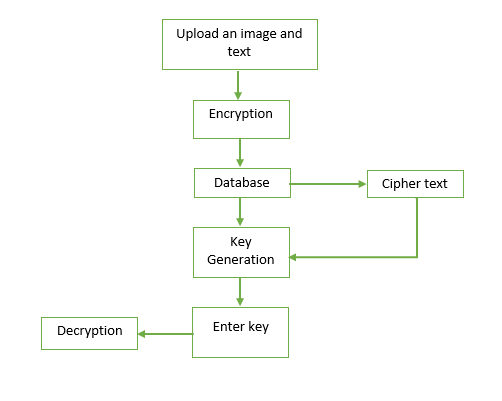
















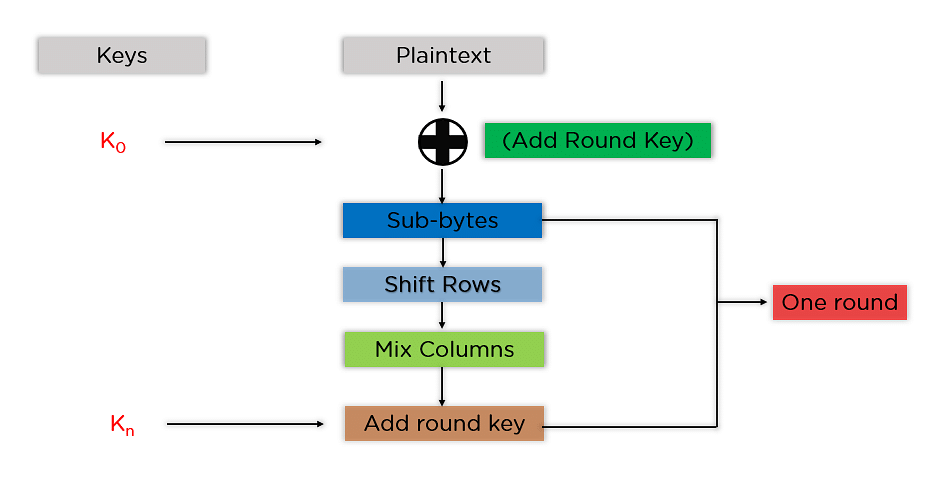





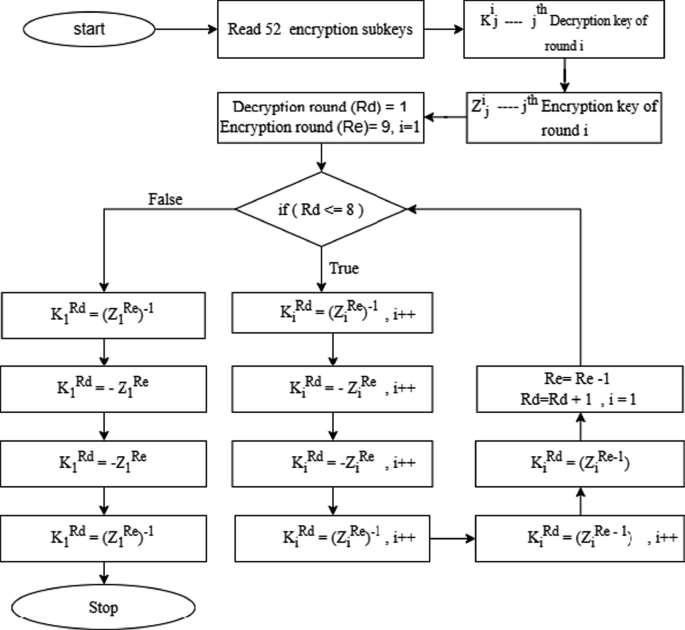









.png)

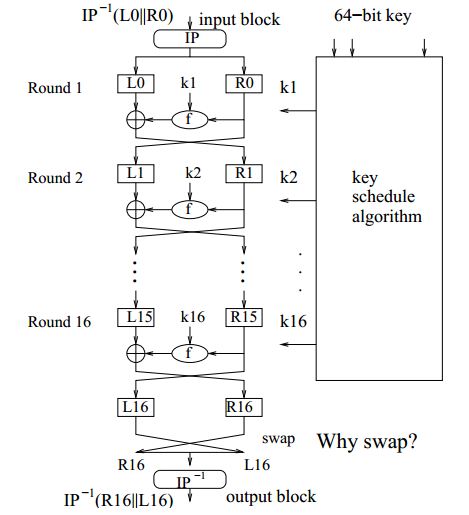



![[Case Study: Latrodectus] Analyzing and Implementing String Decryption ...](https://0x0d4y.blog/wp-content/uploads/2024/05/Diagrama-em-branco1.jpeg)