Computer Scanning Forgery
Study the characteristics of Computer Scanning Forgery using our comprehensive set of comprehensive galleries of learning images. facilitating comprehension through clear visual examples and detailed documentation. making complex concepts accessible through visual learning. Browse our premium Computer Scanning Forgery gallery featuring professionally curated photographs. Excellent for educational materials, academic research, teaching resources, and learning activities All Computer Scanning Forgery images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Our Computer Scanning Forgery images support learning objectives across diverse educational environments. Regular updates keep the Computer Scanning Forgery collection current with contemporary trends and styles. Advanced search capabilities make finding the perfect Computer Scanning Forgery image effortless and efficient. Reliable customer support ensures smooth experience throughout the Computer Scanning Forgery selection process. The Computer Scanning Forgery collection represents years of careful curation and professional standards. Comprehensive tagging systems facilitate quick discovery of relevant Computer Scanning Forgery content. Whether for commercial projects or personal use, our Computer Scanning Forgery collection delivers consistent excellence. The Computer Scanning Forgery archive serves professionals, educators, and creatives across diverse industries. Instant download capabilities enable immediate access to chosen Computer Scanning Forgery images.




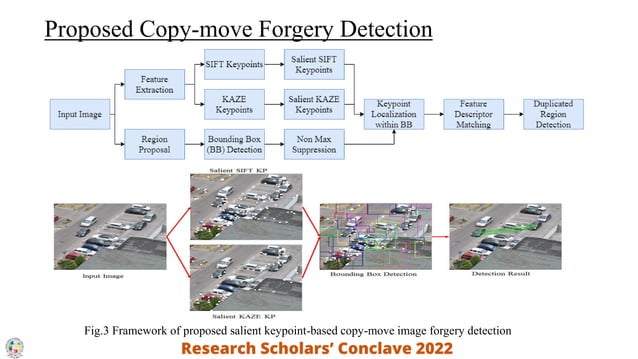




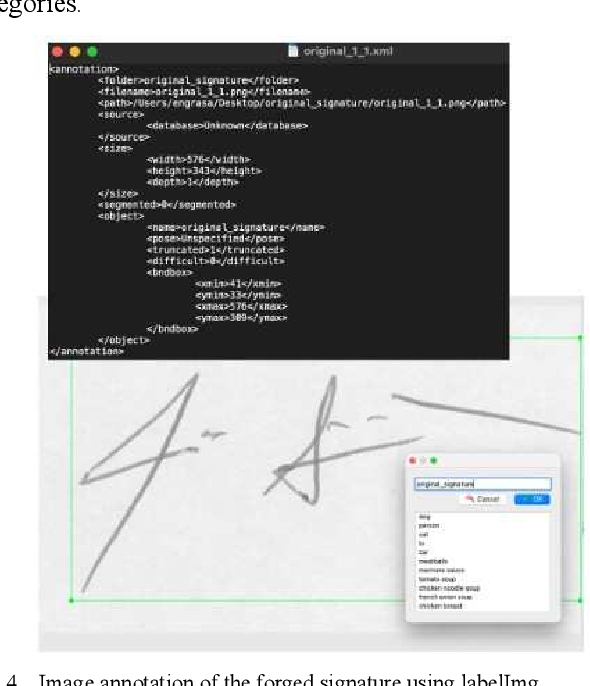











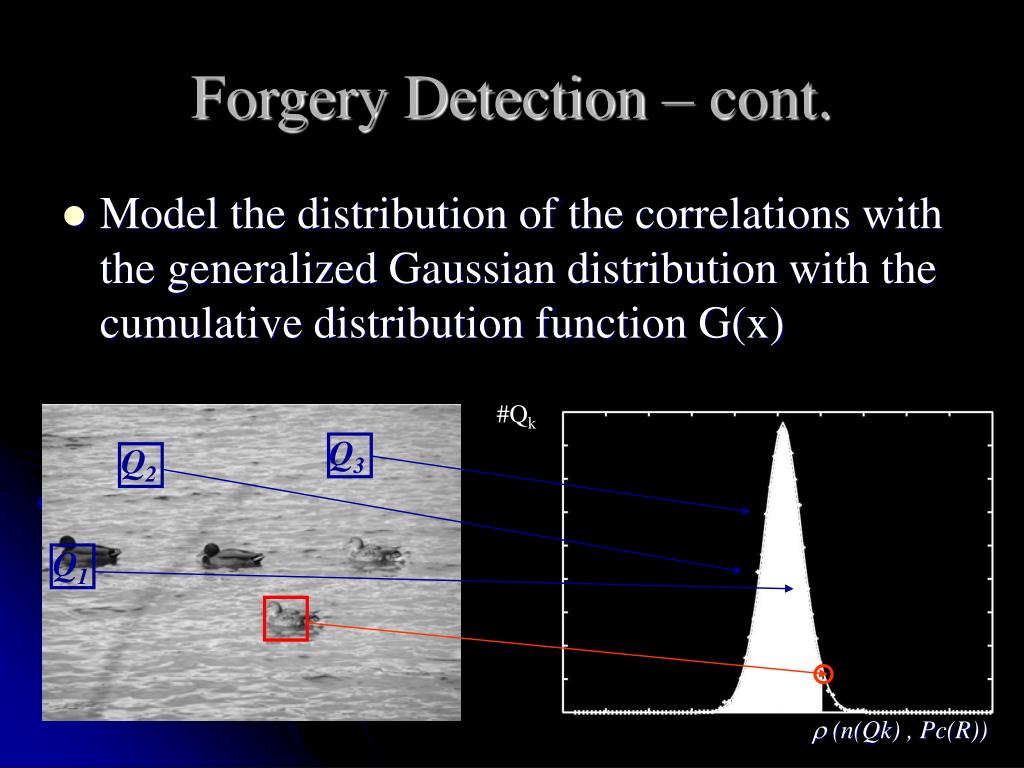
![Forgery detection techniques [2] | Download Scientific Diagram](https://www.researchgate.net/publication/365013597/figure/fig1/AS:11431281094278155@1667444042339/Forgery-detection-techniques-2.png)






![Types of digital image forgery techniques [15] | Download Scientific ...](https://www.researchgate.net/profile/Neeta-Sharma-7/publication/345943128/figure/fig1/AS:958501866205187@1605536061570/Types-of-digital-image-forgery-techniques-15_Q320.jpg)






![Forgery detection techniques [2] | Download Scientific Diagram](https://www.researchgate.net/publication/365013597/figure/fig1/AS:11431281094278155@1667444042339/Forgery-detection-techniques-2_Q320.jpg)



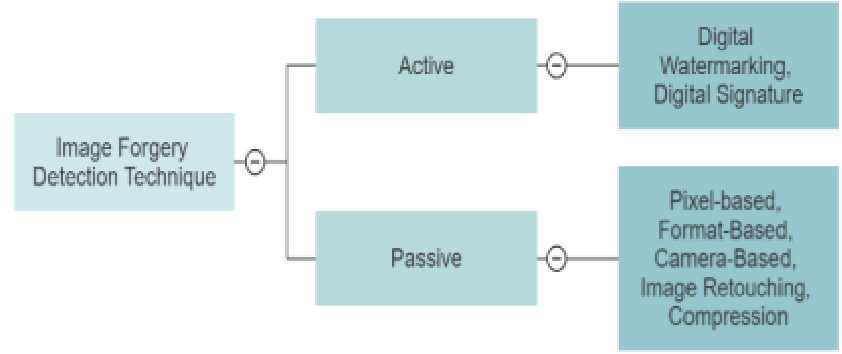
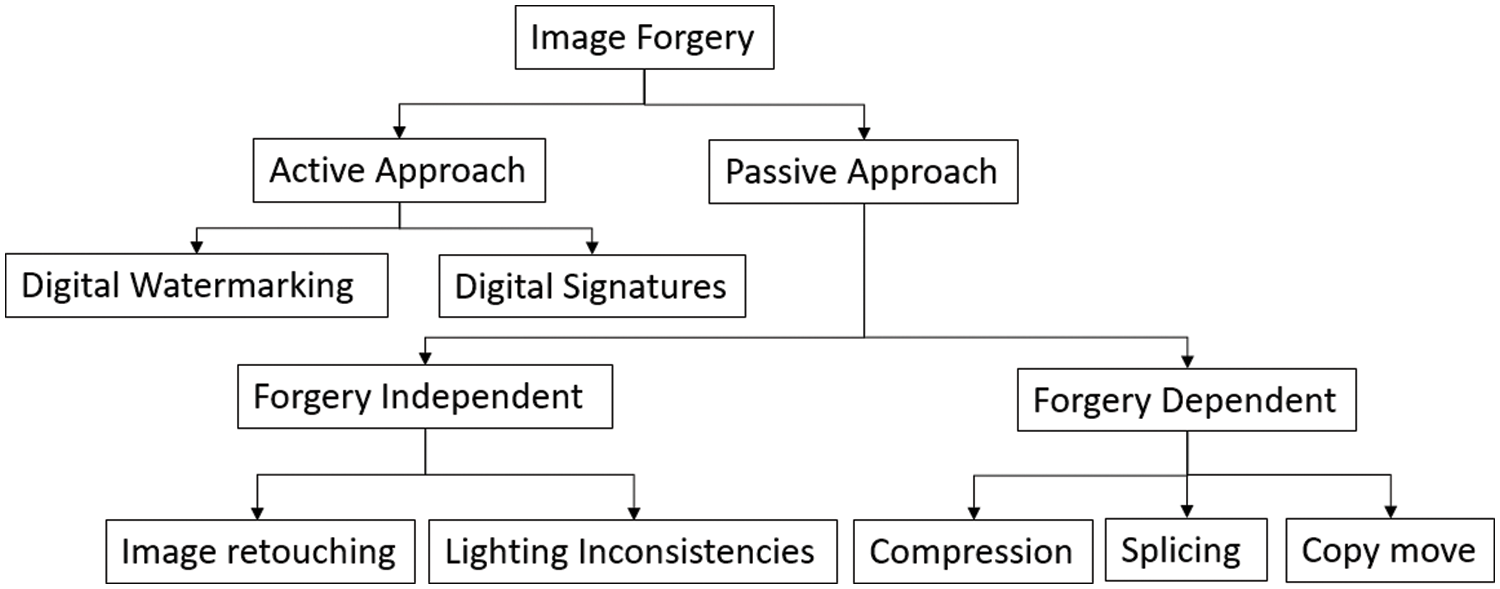
![Classification of image forgery [3]. | Download Scientific Diagram](https://www.researchgate.net/profile/Sudarshan-Nelatury/publication/327022702/figure/download/fig1/AS:659594753884160@1534271052251/Classification-of-image-forgery-3.png)









































(174F386C4FBF29DFDFDE344A729E85E3).jpg)








/GettyImages-820926684-5c7747ebc45847708ac311b709bdc1f2.jpg)