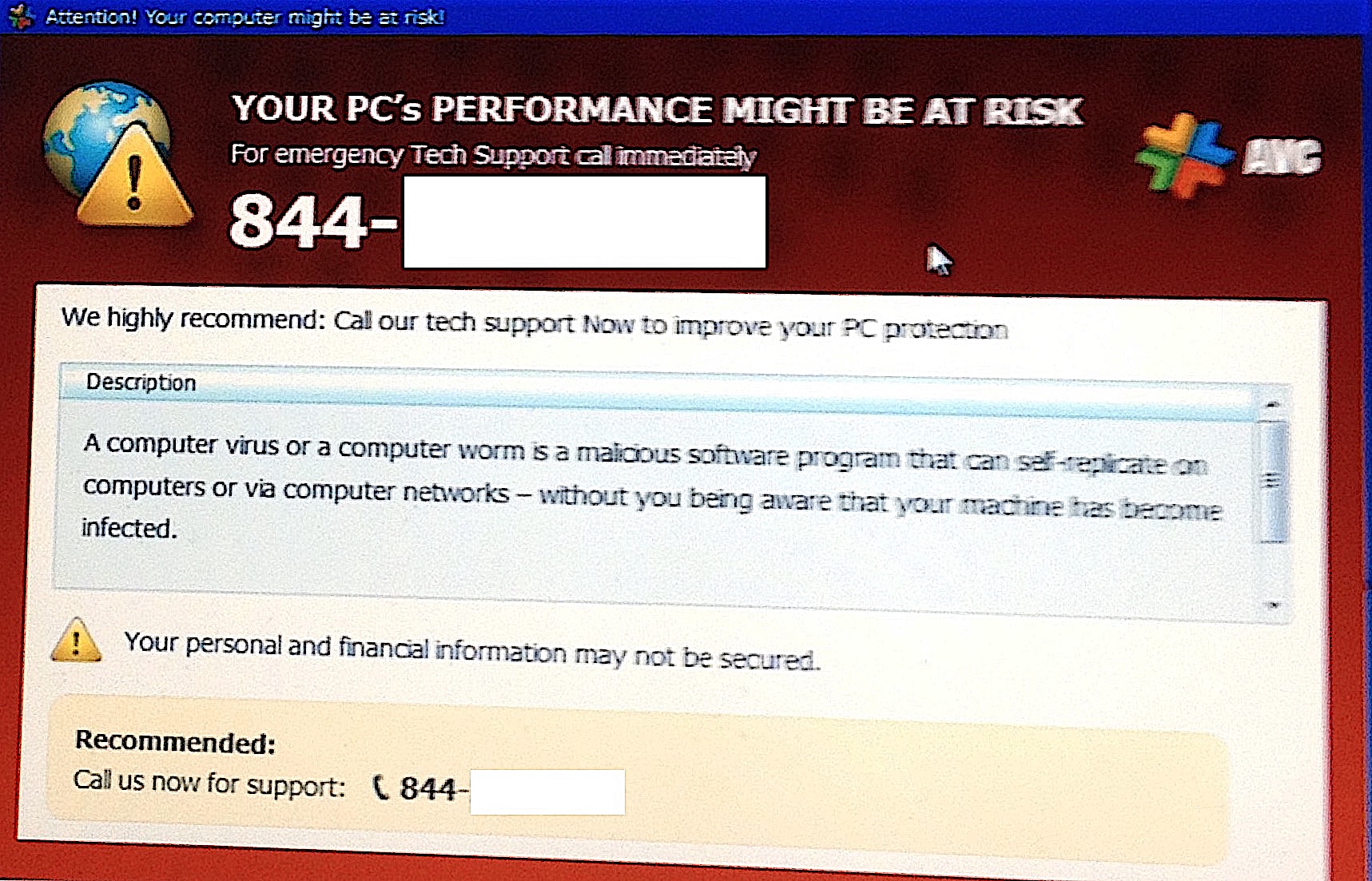
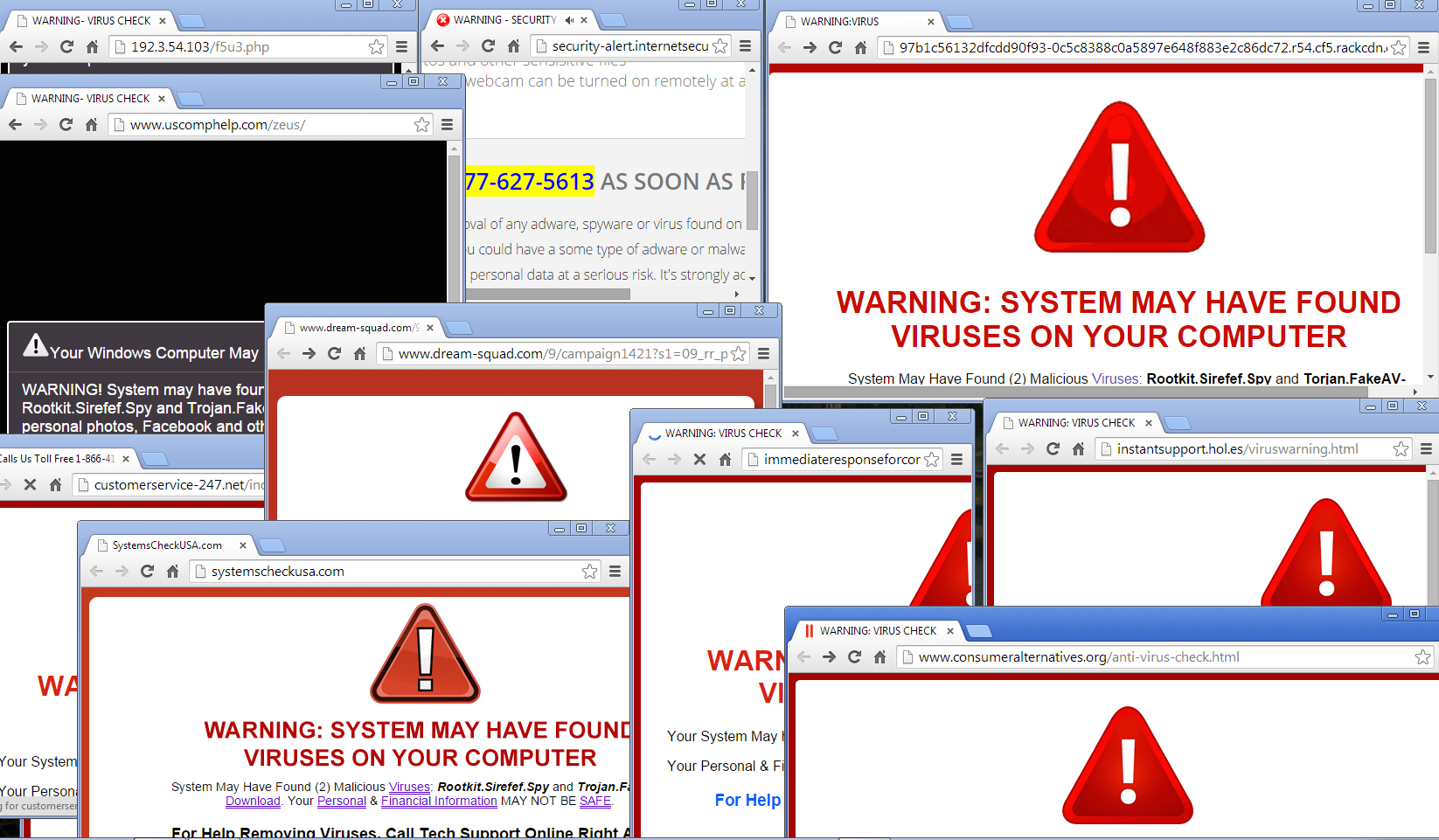
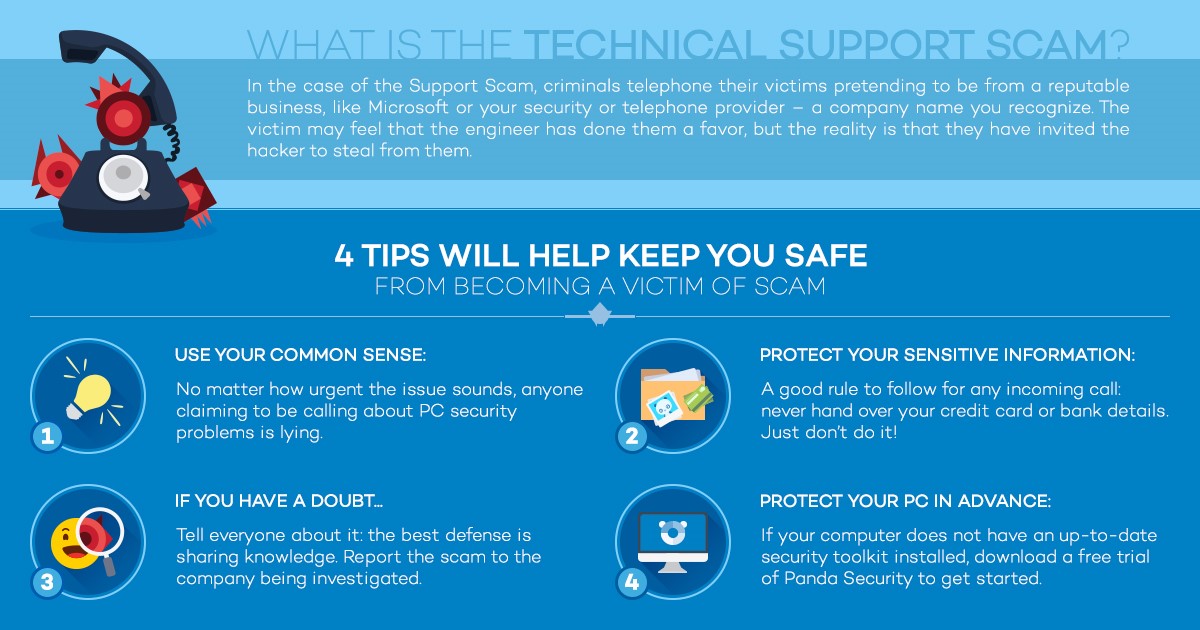
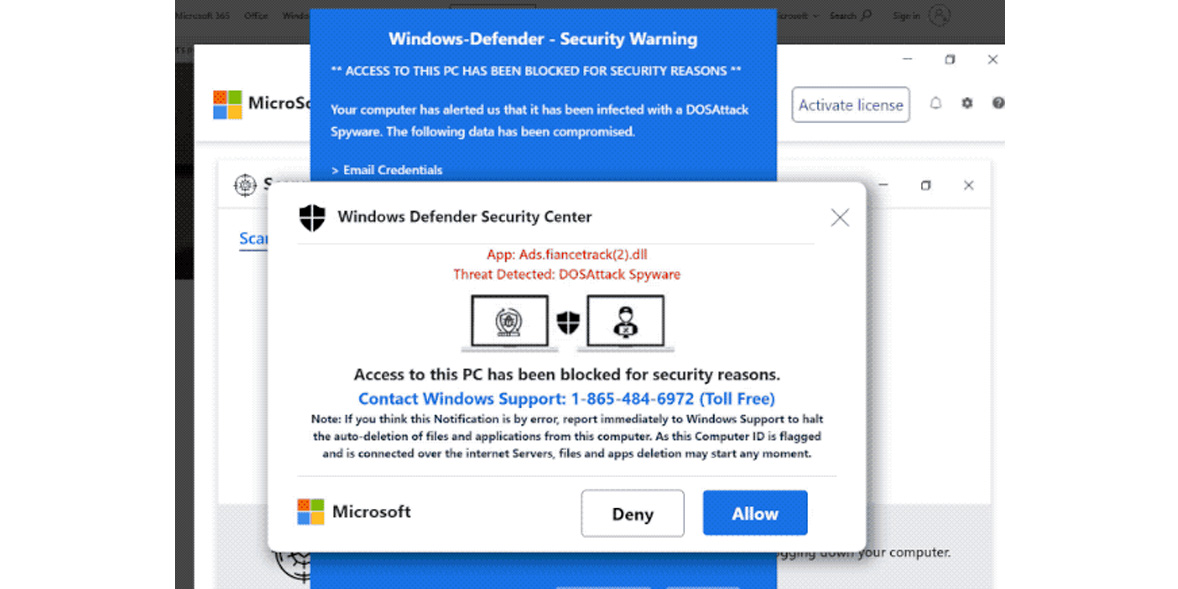
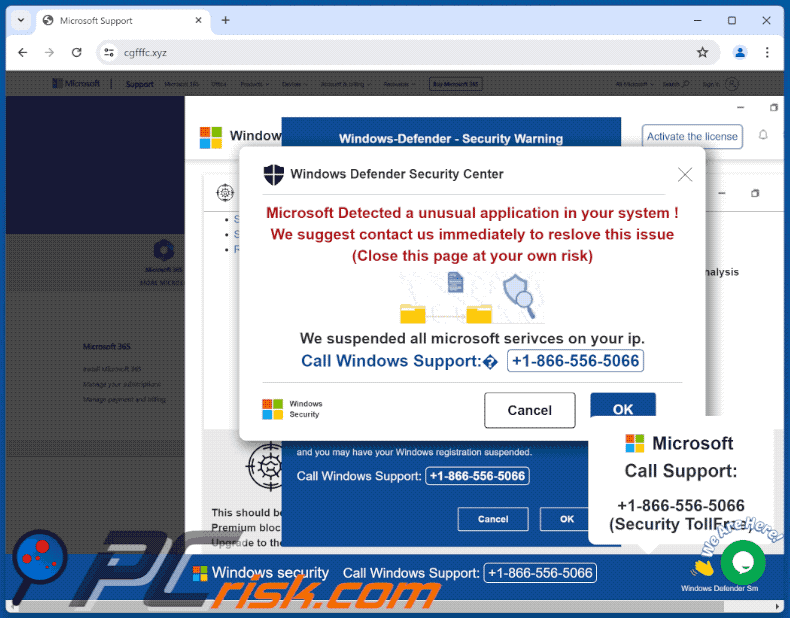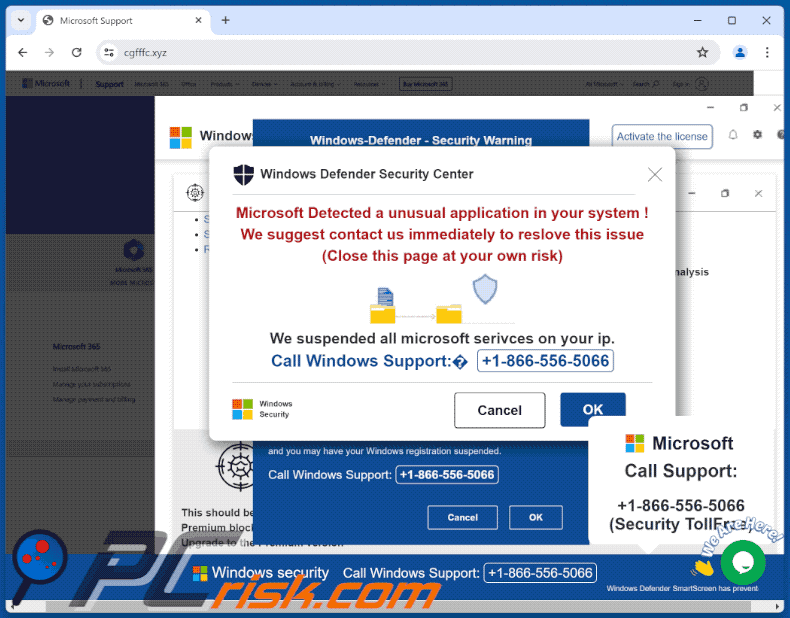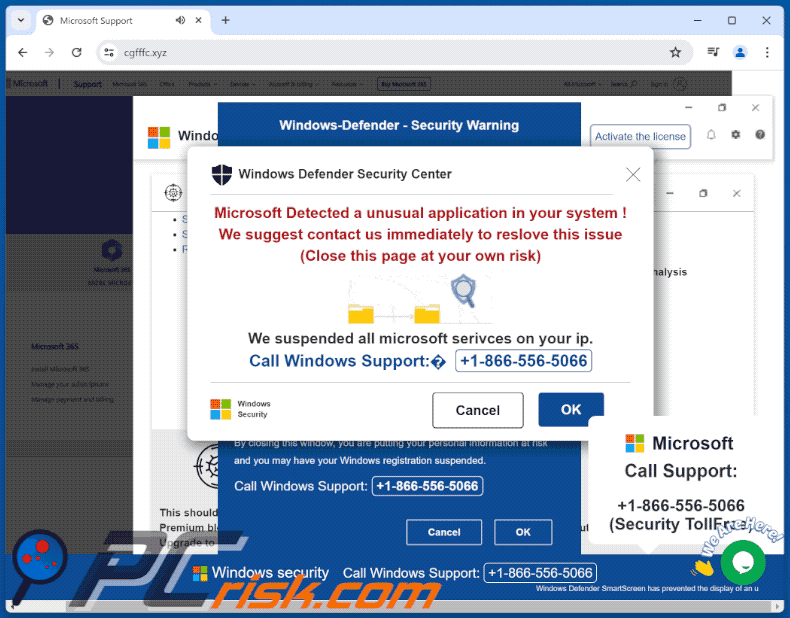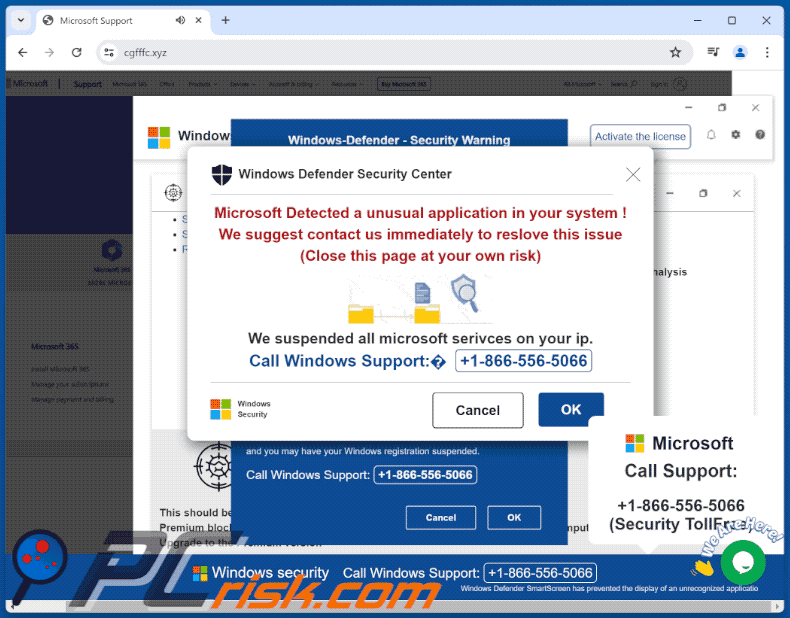
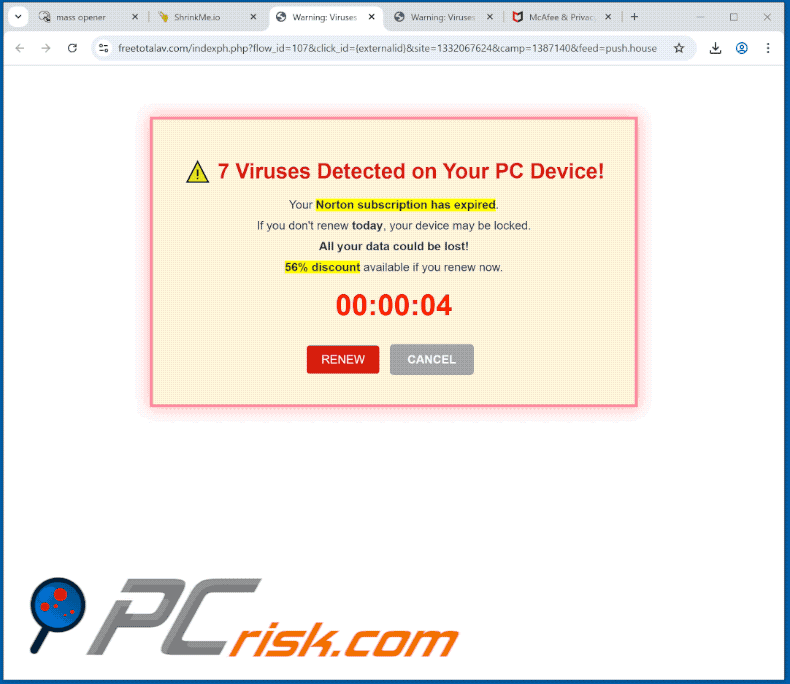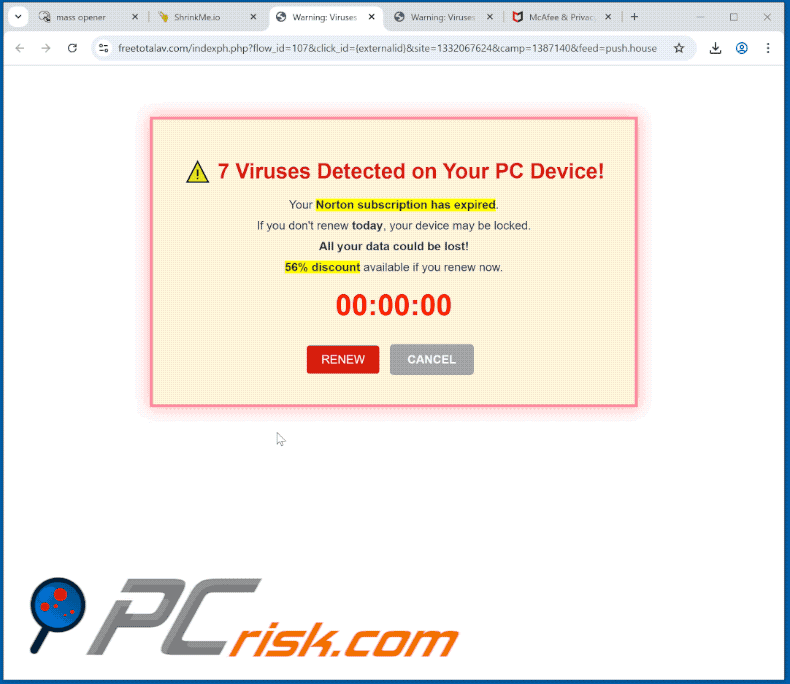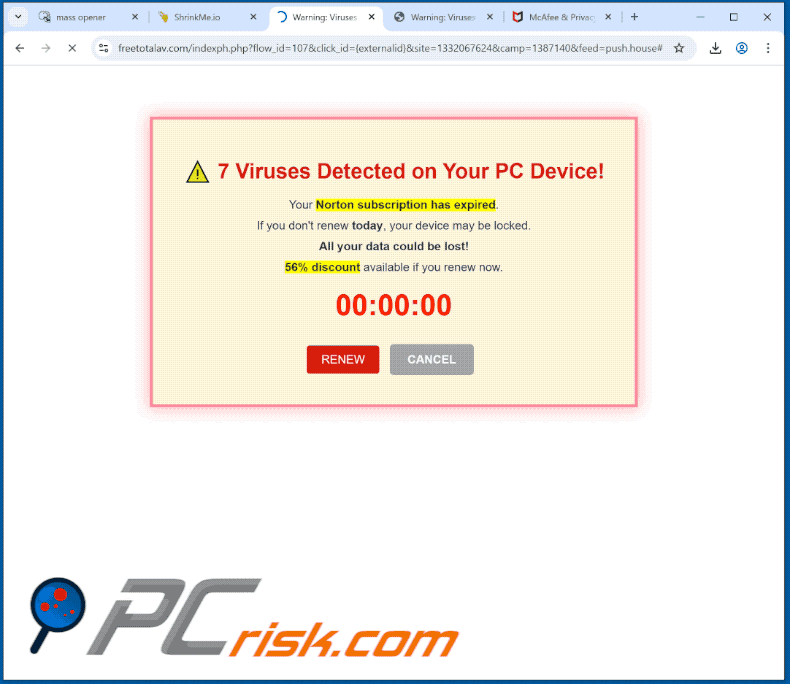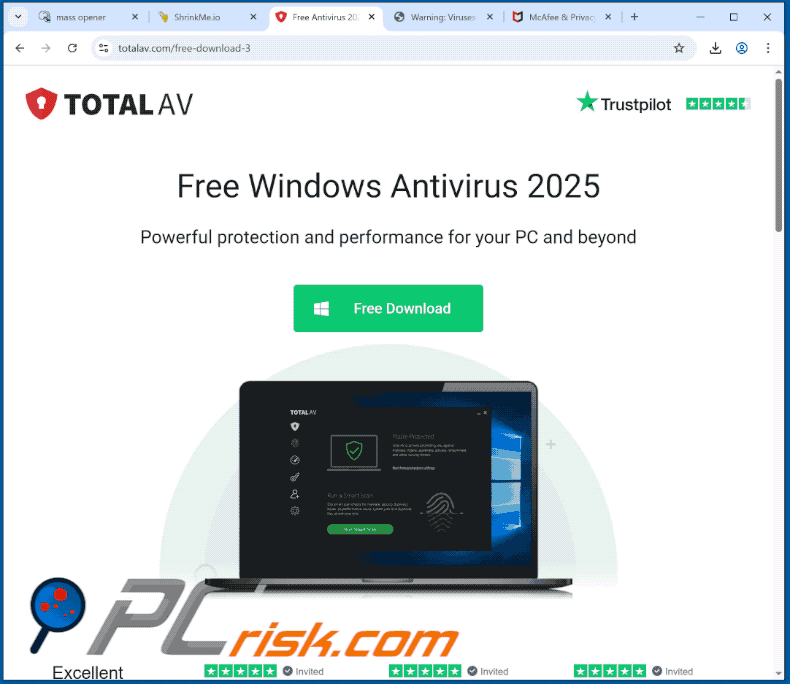
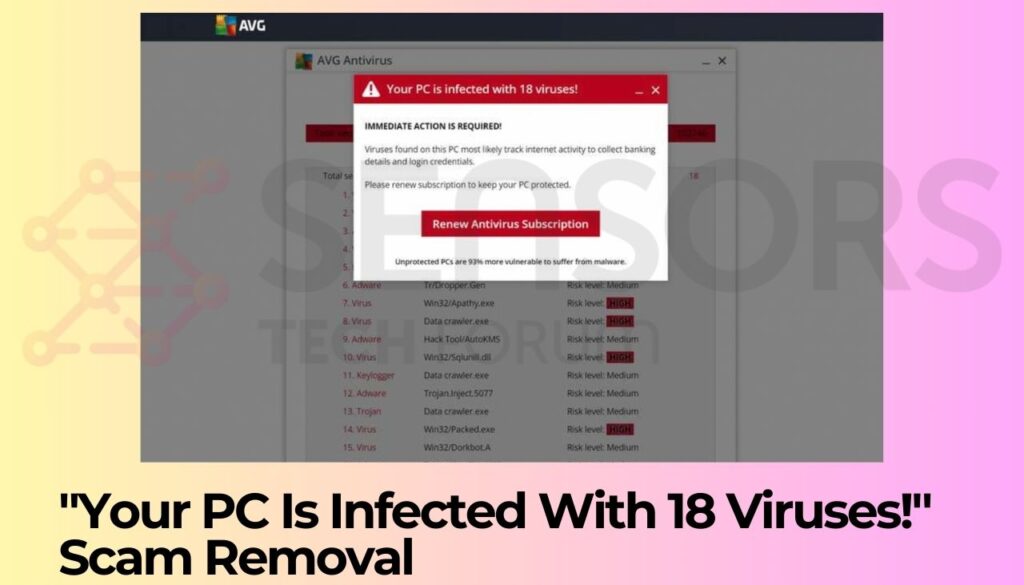
Computer Exploring A Scam
Drive innovation through extensive collections of industry-focused Computer Exploring A Scam photographs. documenting production methods of technology, digital, and software. perfect for industrial documentation and training. Our Computer Exploring A Scam collection features high-quality images with excellent detail and clarity. Suitable for various applications including web design, social media, personal projects, and digital content creation All Computer Exploring A Scam images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Our Computer Exploring A Scam gallery offers diverse visual resources to bring your ideas to life. Reliable customer support ensures smooth experience throughout the Computer Exploring A Scam selection process. Our Computer Exploring A Scam database continuously expands with fresh, relevant content from skilled photographers. Comprehensive tagging systems facilitate quick discovery of relevant Computer Exploring A Scam content. Instant download capabilities enable immediate access to chosen Computer Exploring A Scam images. The Computer Exploring A Scam archive serves professionals, educators, and creatives across diverse industries. Each image in our Computer Exploring A Scam gallery undergoes rigorous quality assessment before inclusion. Multiple resolution options ensure optimal performance across different platforms and applications. Whether for commercial projects or personal use, our Computer Exploring A Scam collection delivers consistent excellence.














































.png?sfvrsn=25a57d8_1)




/hacker-phishing-computer-infection-673354480-5bd73ab646e0fb0026911245-3b0789029a034a609e146223016a6f53.jpg)