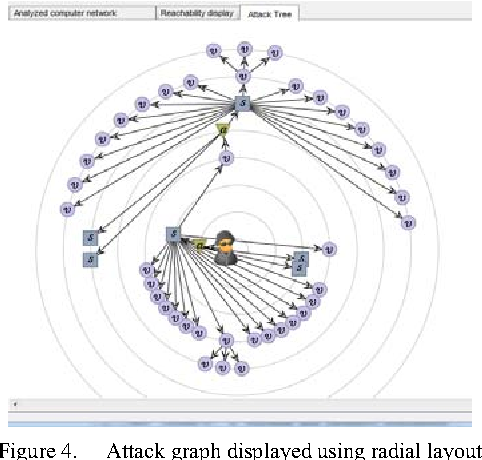
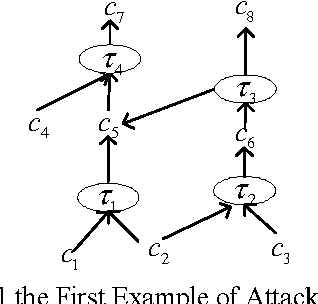
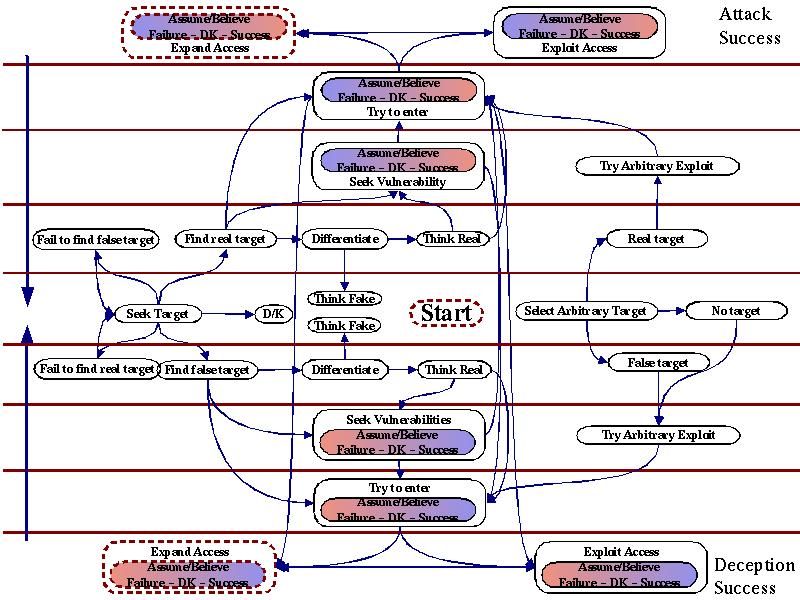
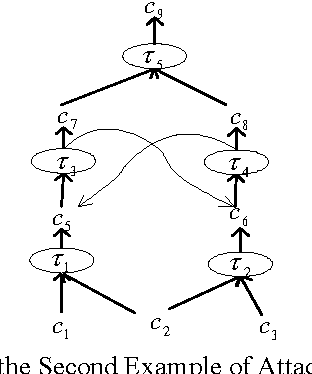
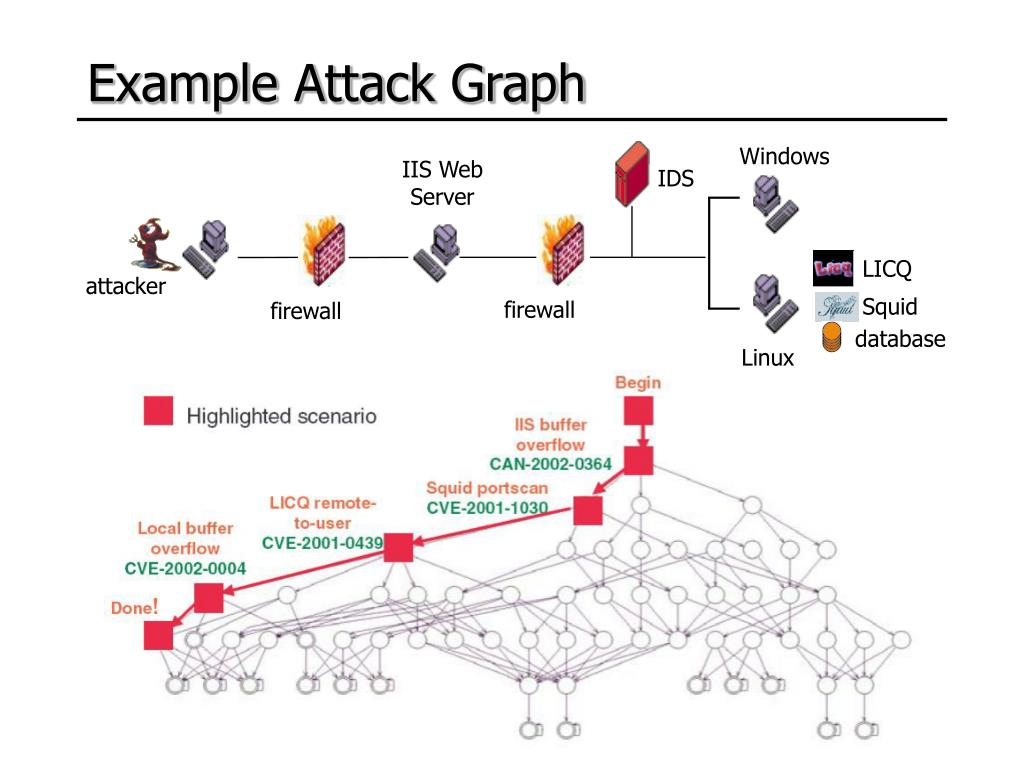
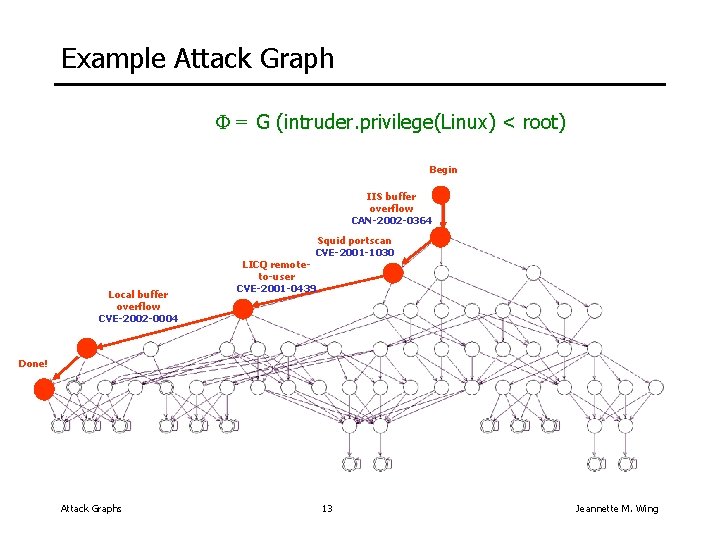
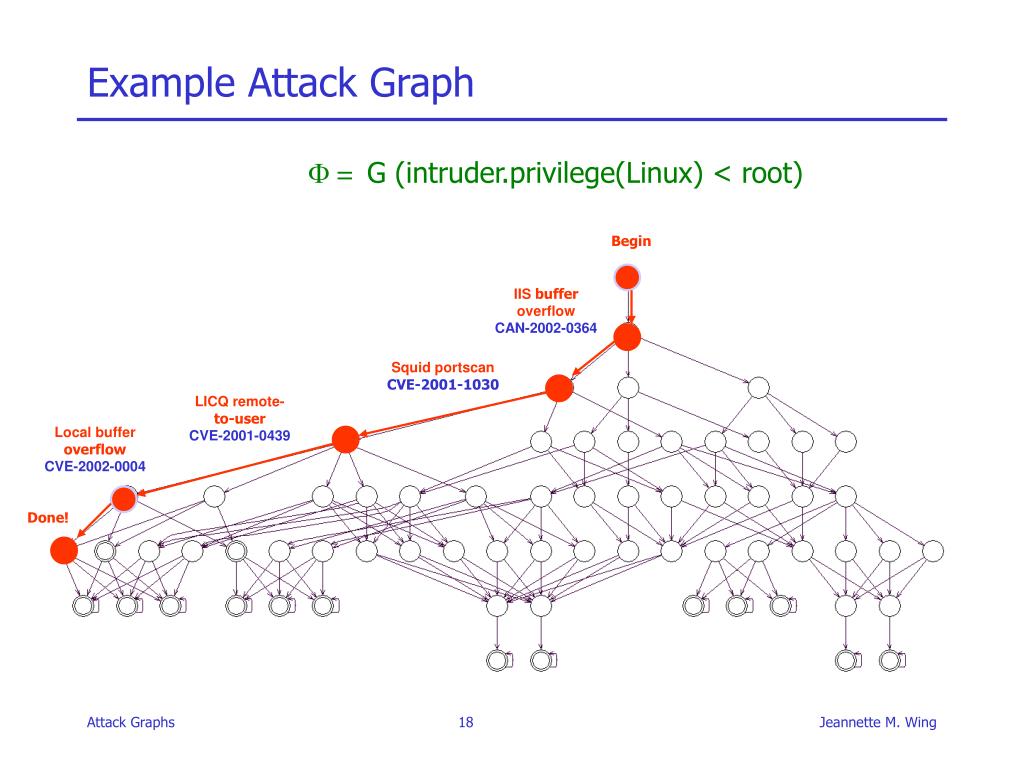
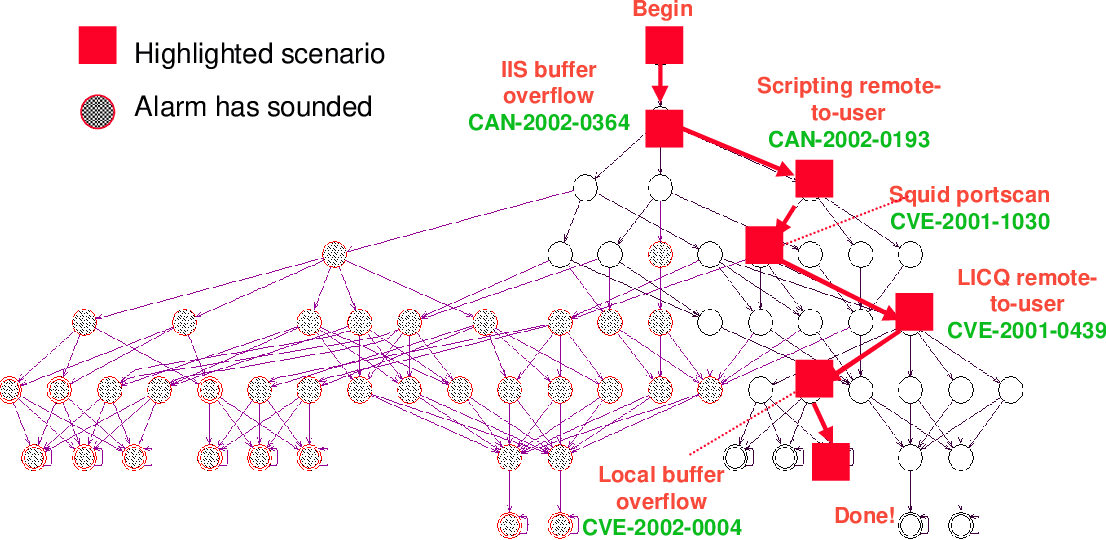
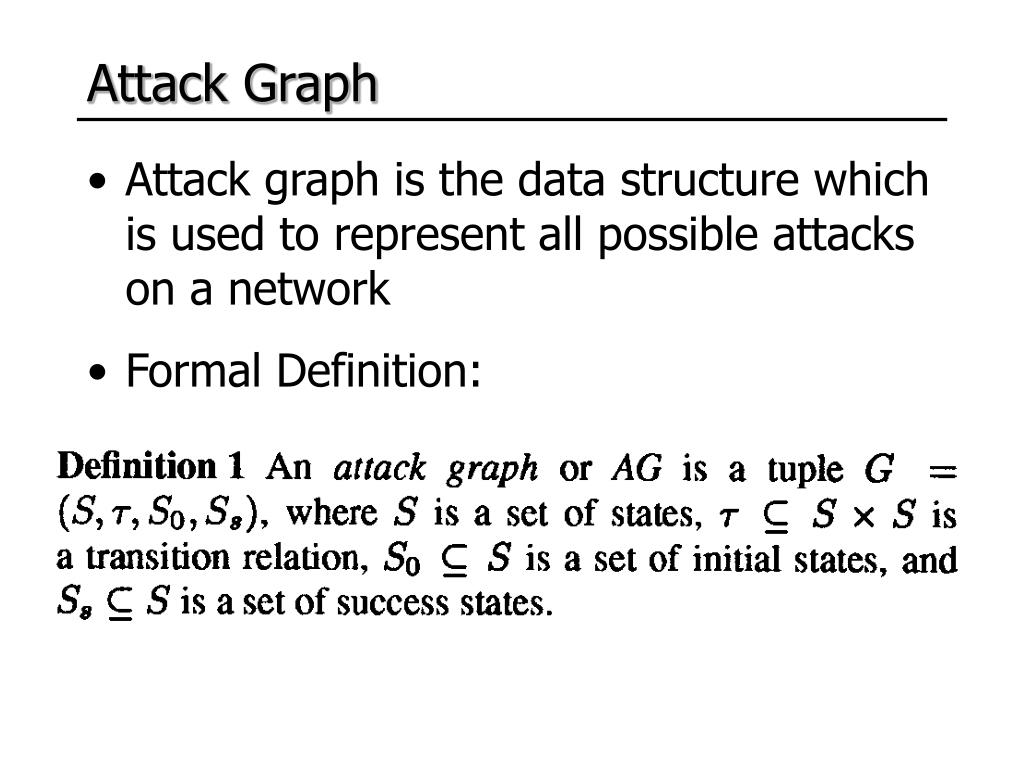
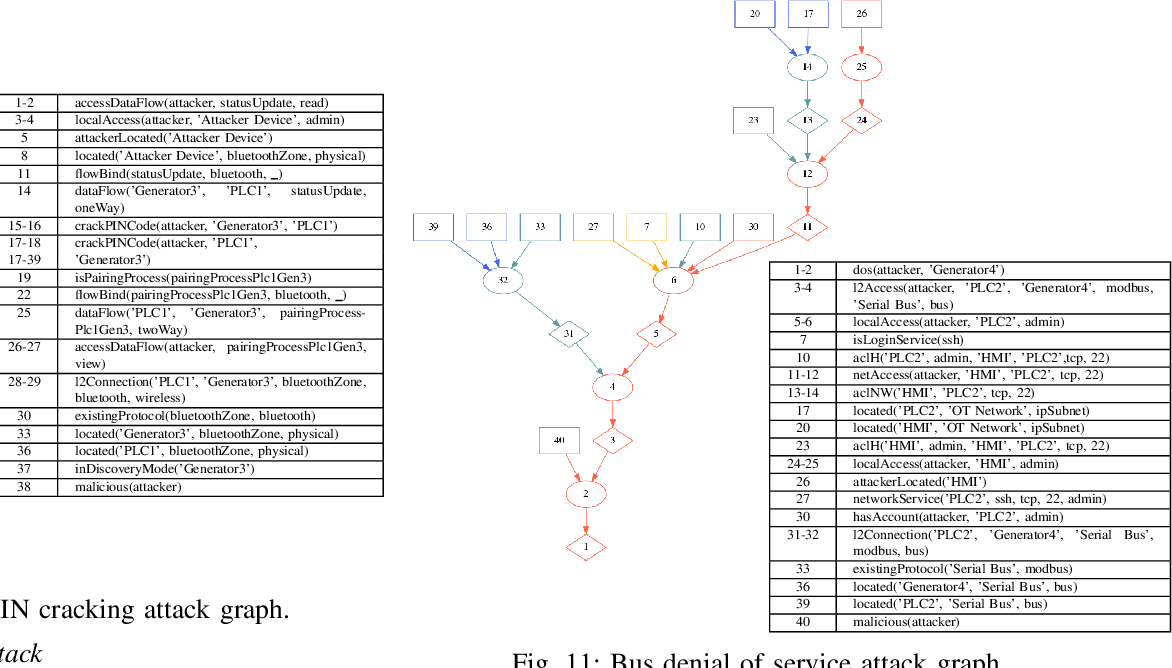
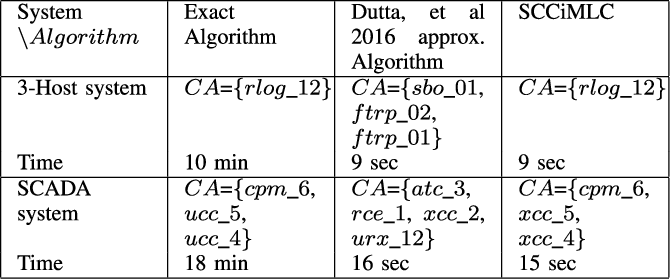
Attack Graph Computer Science
Discover traditional Attack Graph Computer Science with our collection of vast arrays of classic photographs. preserving the heritage of technology, digital, and software. designed to preserve cultural significance. Our Attack Graph Computer Science collection features high-quality images with excellent detail and clarity. Suitable for various applications including web design, social media, personal projects, and digital content creation All Attack Graph Computer Science images are available in high resolution with professional-grade quality, optimized for both digital and print applications, and include comprehensive metadata for easy organization and usage. Explore the versatility of our Attack Graph Computer Science collection for various creative and professional projects. Multiple resolution options ensure optimal performance across different platforms and applications. The Attack Graph Computer Science archive serves professionals, educators, and creatives across diverse industries. Professional licensing options accommodate both commercial and educational usage requirements. Time-saving browsing features help users locate ideal Attack Graph Computer Science images quickly. Instant download capabilities enable immediate access to chosen Attack Graph Computer Science images. Regular updates keep the Attack Graph Computer Science collection current with contemporary trends and styles. Diverse style options within the Attack Graph Computer Science collection suit various aesthetic preferences. Comprehensive tagging systems facilitate quick discovery of relevant Attack Graph Computer Science content.





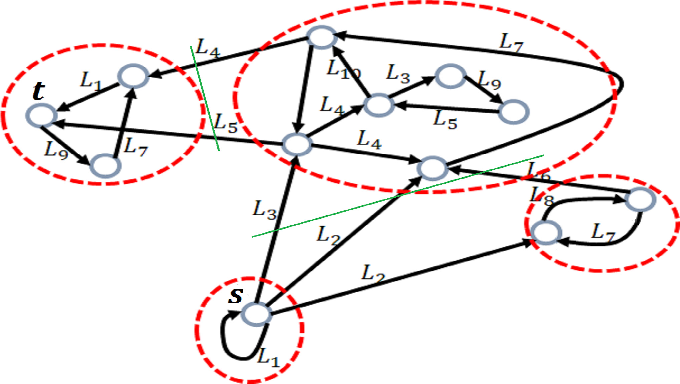
![An Attack Graph Sample [19]. | Download Scientific Diagram](https://www.researchgate.net/profile/Zaid-Alaaraji/publication/352020993/figure/fig2/AS:1029858750627840@1622548868164/Attack-Graph-uses-20_Q320.jpg)





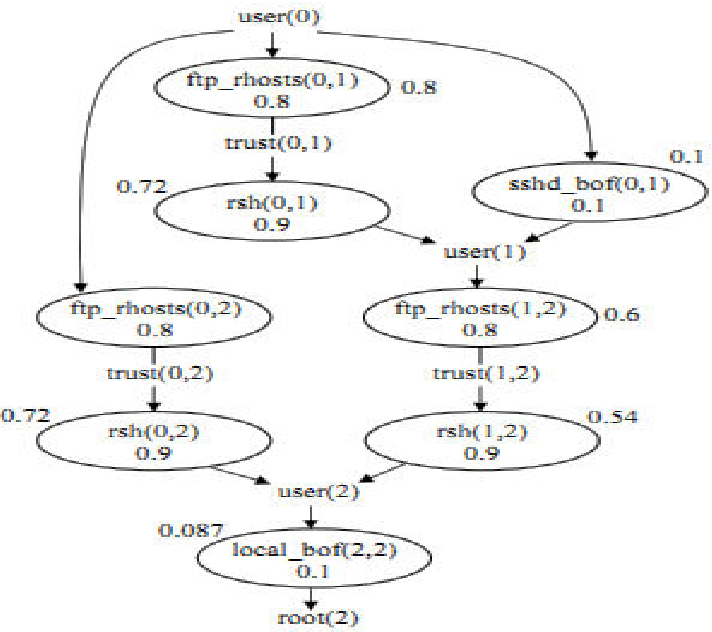



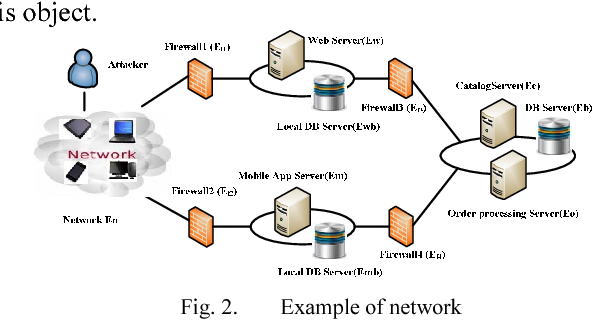
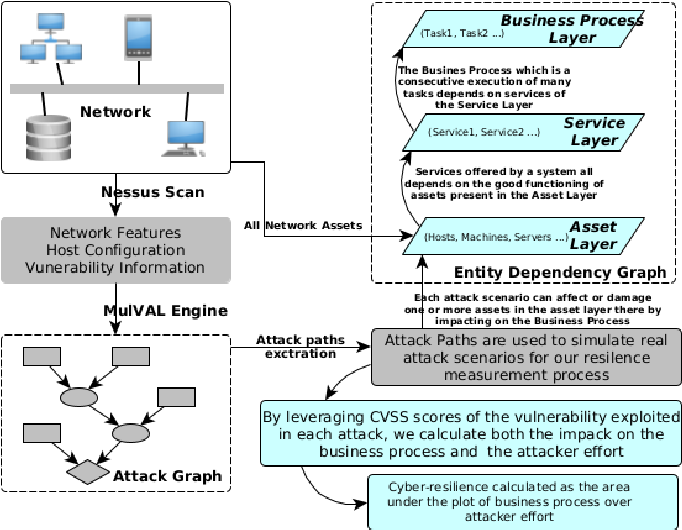

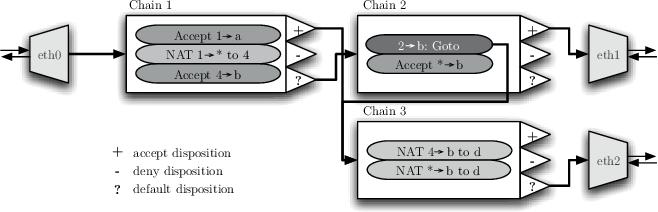
![Attack Graph uses [20]. | Download Scientific Diagram](https://mavink.com/images/loadingwhitetransparent.gif)
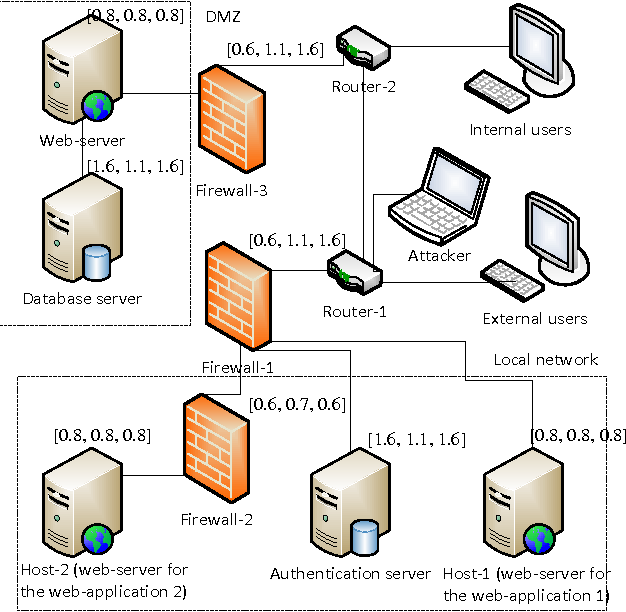
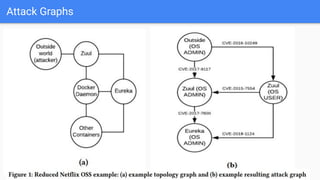
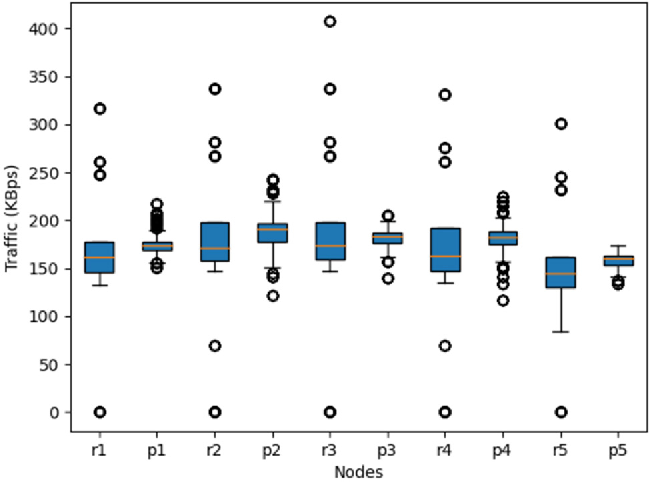

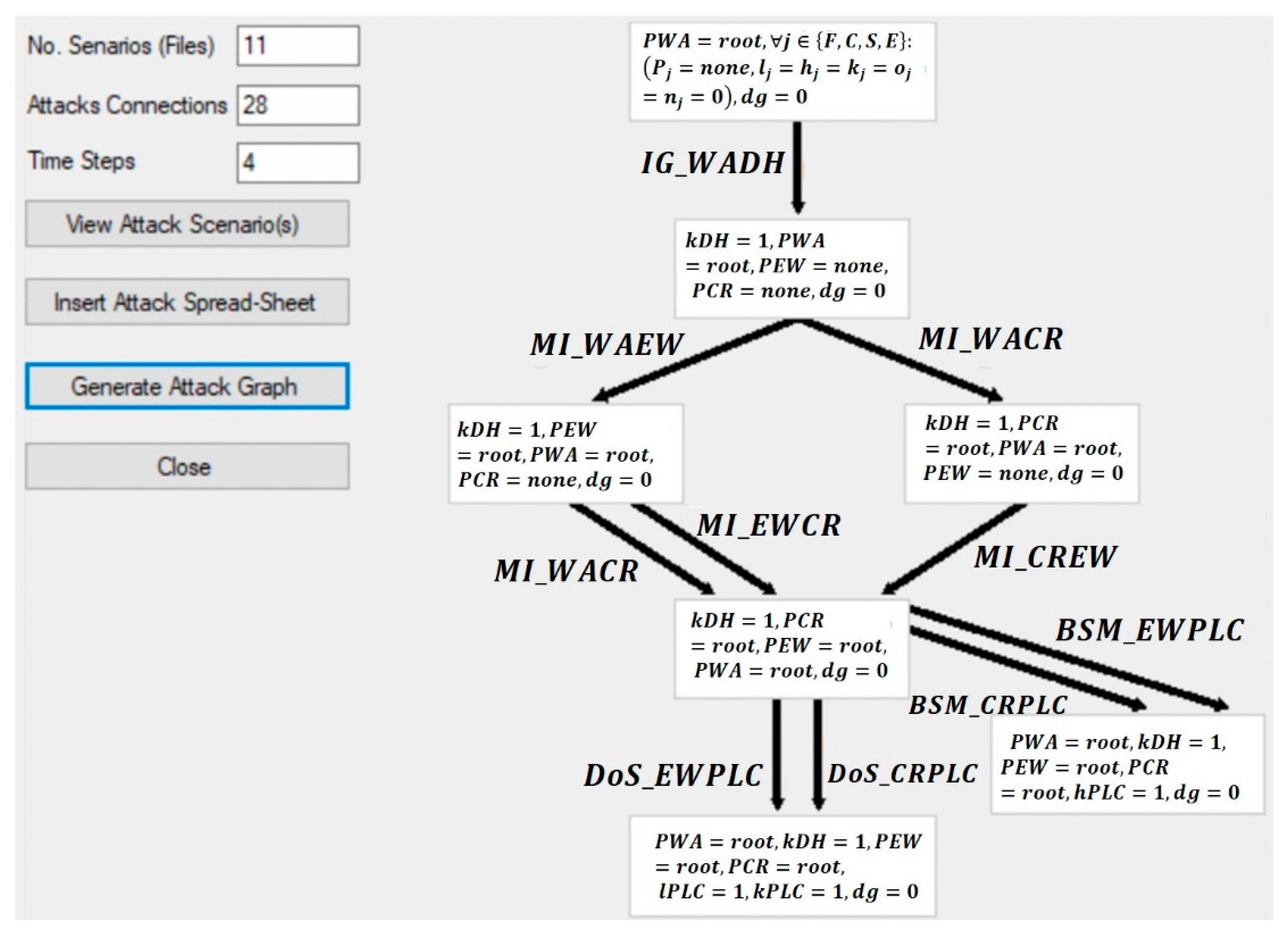
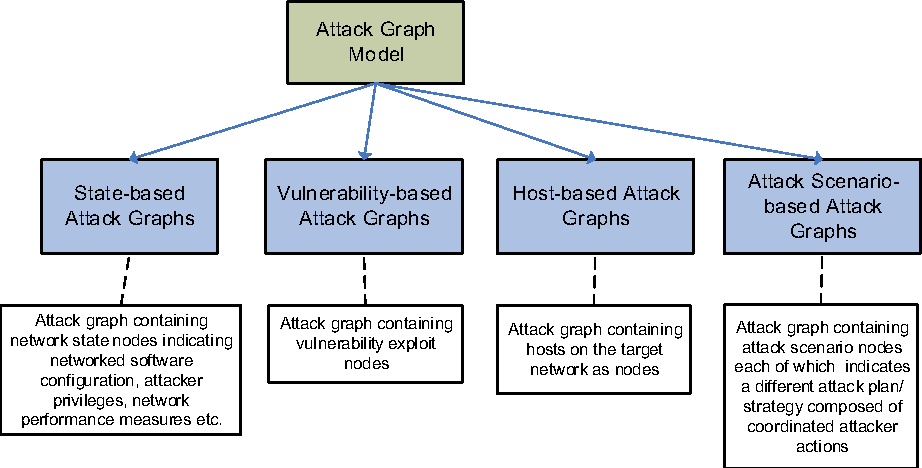
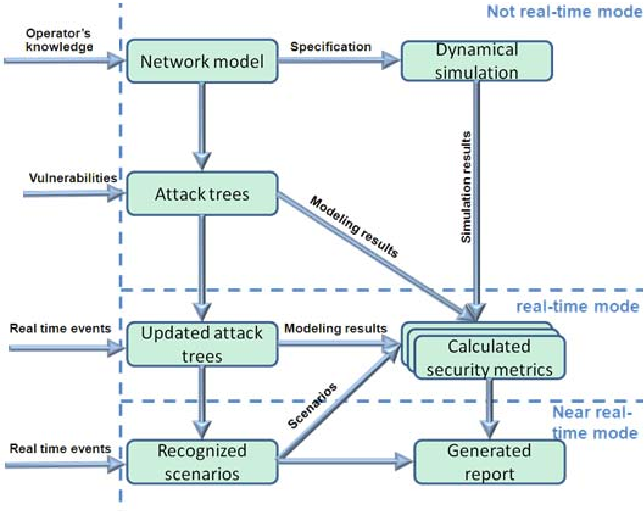
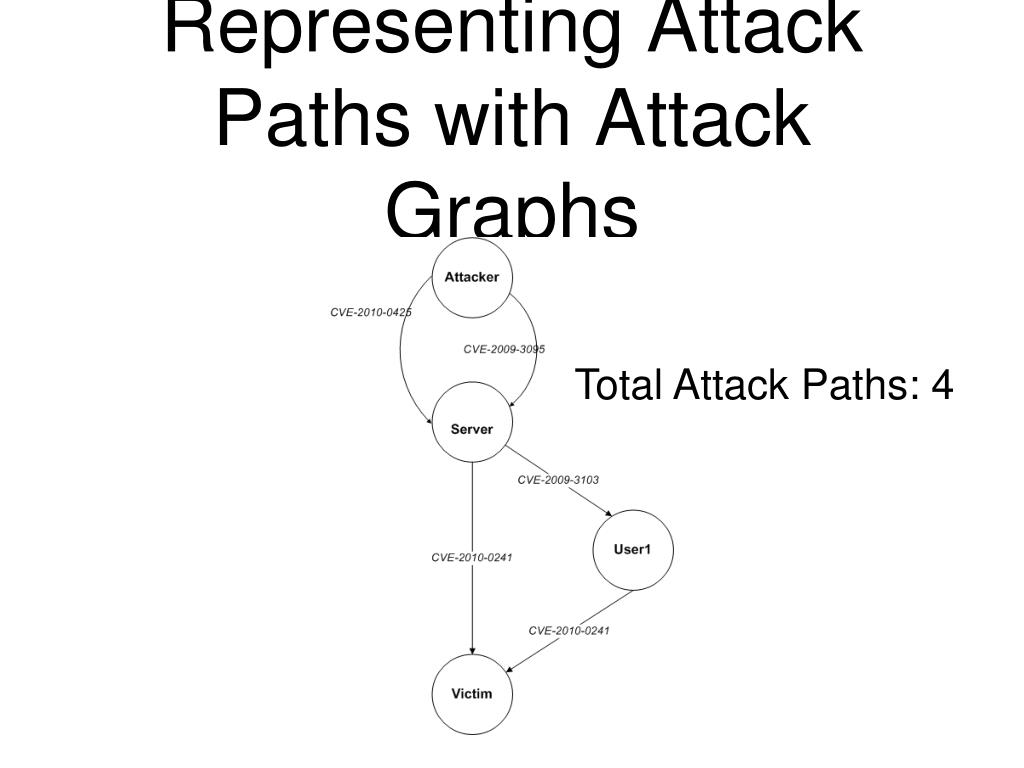
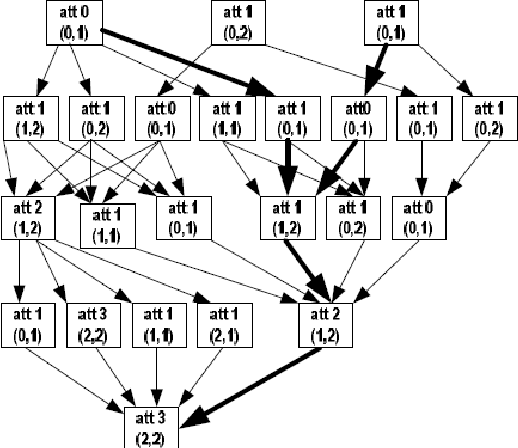
![Attack graph showing a successful attack for user1 from [11] | Download ...](https://www.researchgate.net/publication/337305621/figure/fig8/AS:862250944446464@1582588053146/Attack-graph-showing-a-successful-attack-for-user1-from-11.png)










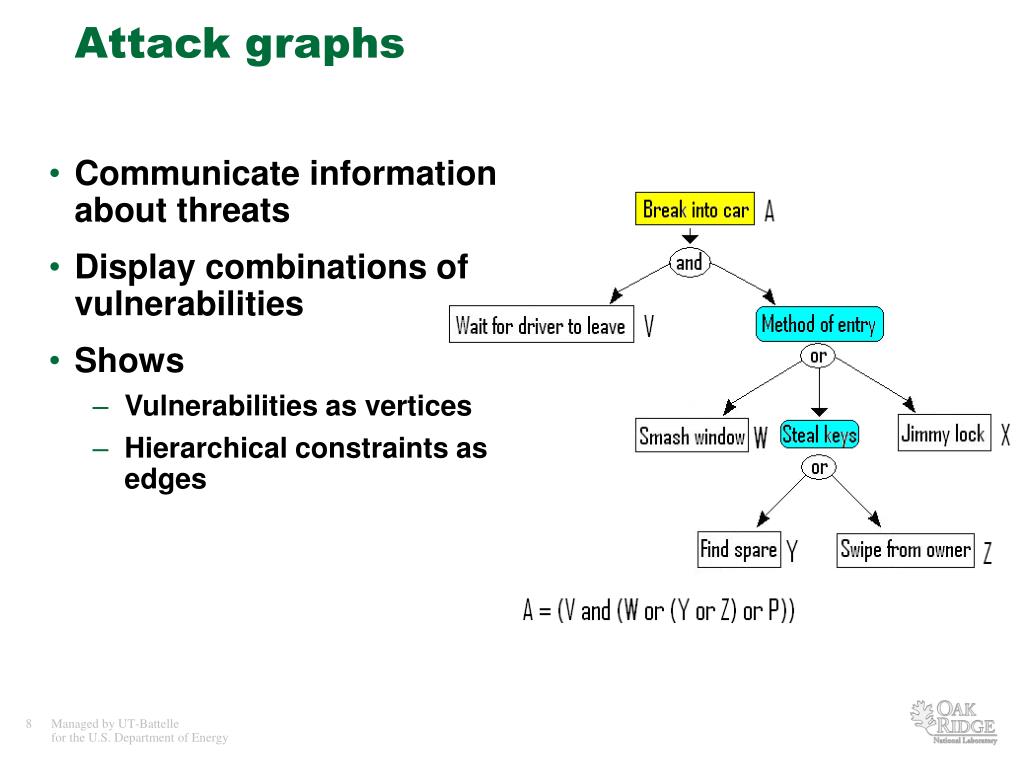
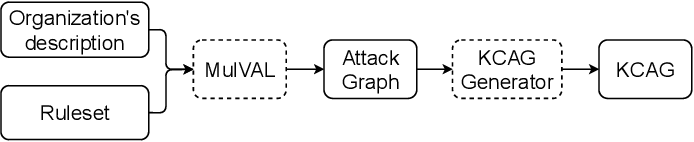





![Activity-attack graph [25] | Download Scientific Diagram](https://www.researchgate.net/profile/Ali-Dehghantanha/publication/330071595/figure/fig3/AS:743357785579521@1554241715898/Activity-attack-graph-25.png)



-p-2000.png)